Integration with DUO MFA
Before You Start
Overview
In this article, you’ll learn how to integrate DUO with an Acreto Ecosystem.
This process involves the following steps:
Prerequisites
To integrate Acreto with DUO, you will need the following:
- Active Acreto Ecosystem
- DUO account - use the existing one or create a new one (you may use the free trial option).
- A physical or virtual host for DUO Authentication Proxy - t’s not recommended to install the Duo Authentication Proxy on the same Windows server that acts as your Active Directory domain or Network Policy Server (NPS) role. This may create conflicts between the Duo service and your pre-existing services.
- Existing Identity provider with LDAP functionality. For example, the free LDAP JumpCloud will be used.
The Purpose of DUO Integration
A DUO integration allows your Acreto Ecosystem to utilize the user credentials stored in your LDAP Identity Provider to connect to the Ecosystem using Acreto TLS Client with additional Multi-Factor Authentication made by the DUO application, phone, or SMS.
It uses DUO Authentication Proxy as the “Man in the middle” that additionally secures the login procedure for Acreto users.
The solution uses an LDAP connection from Acreto to DUO and from DUO to Identity Provider LDAP.
How To
Configuration of DUO
To configure your DUO to work with Acreto, please:
- Log in to the DUO admin panel.
- From the left menu choose the Applications option.
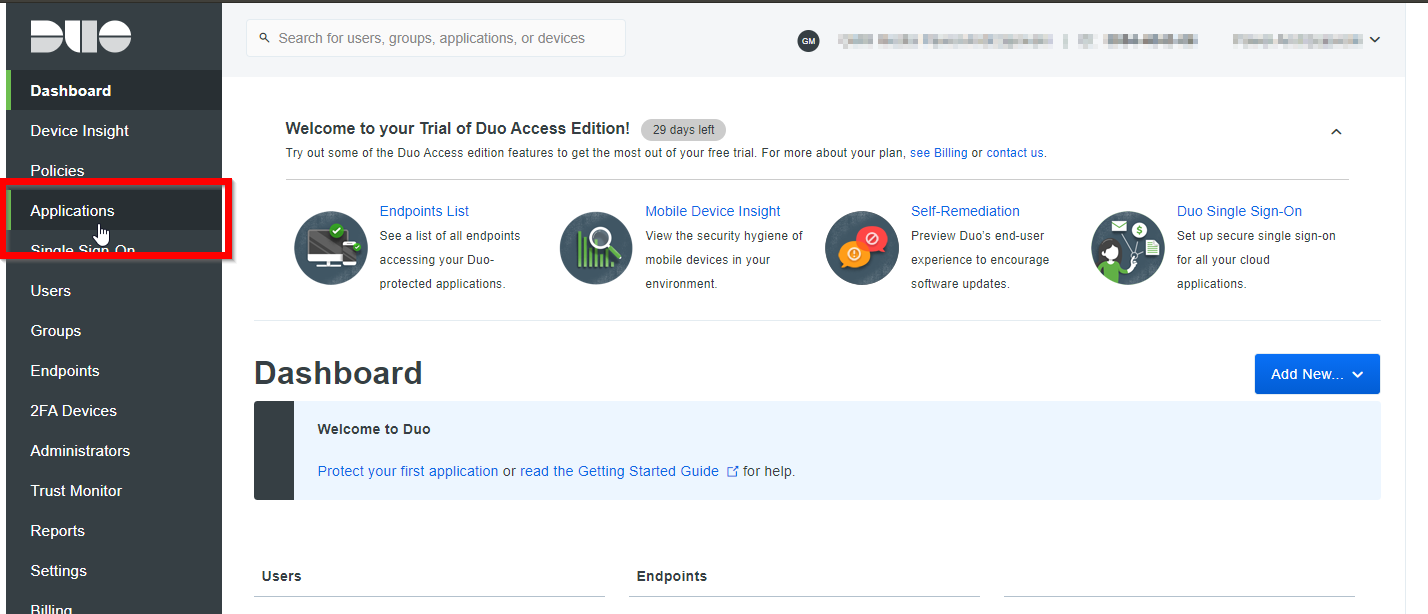

- Use the search option, and type LDAP. The list of apps should be filtered to only one position LDAP Proxy.
- Click on the Protect button for the LDAP Proxy option.
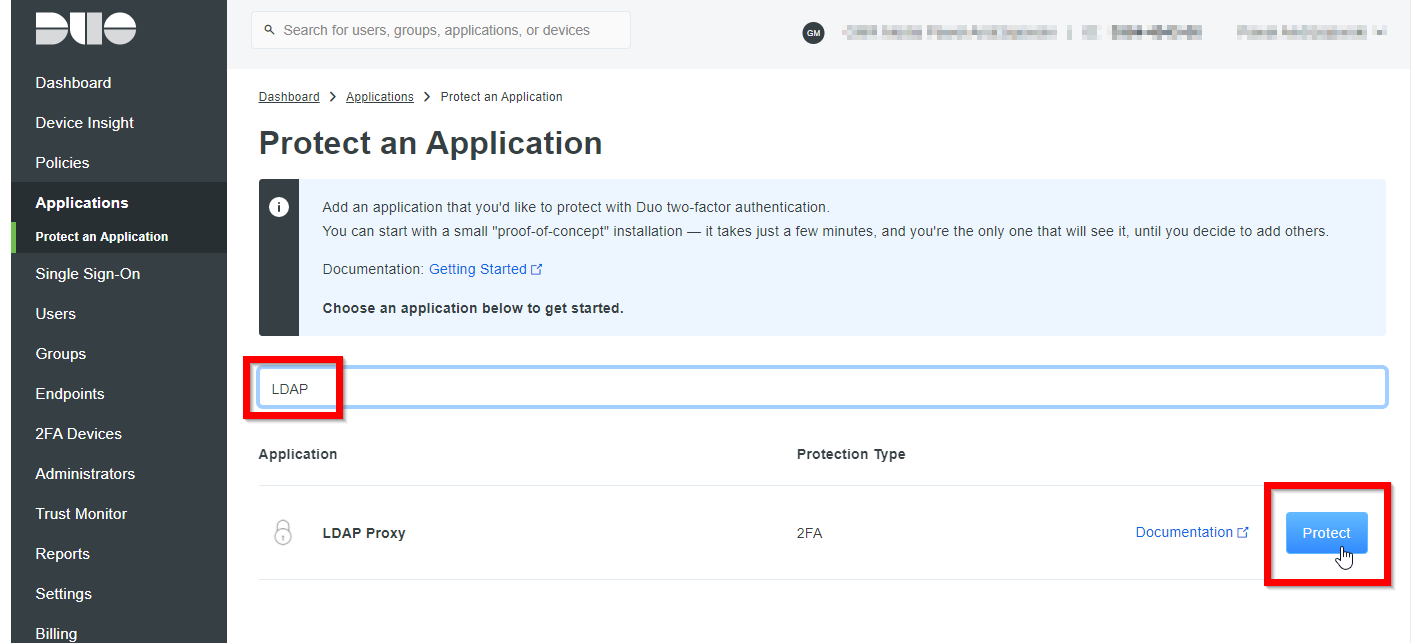

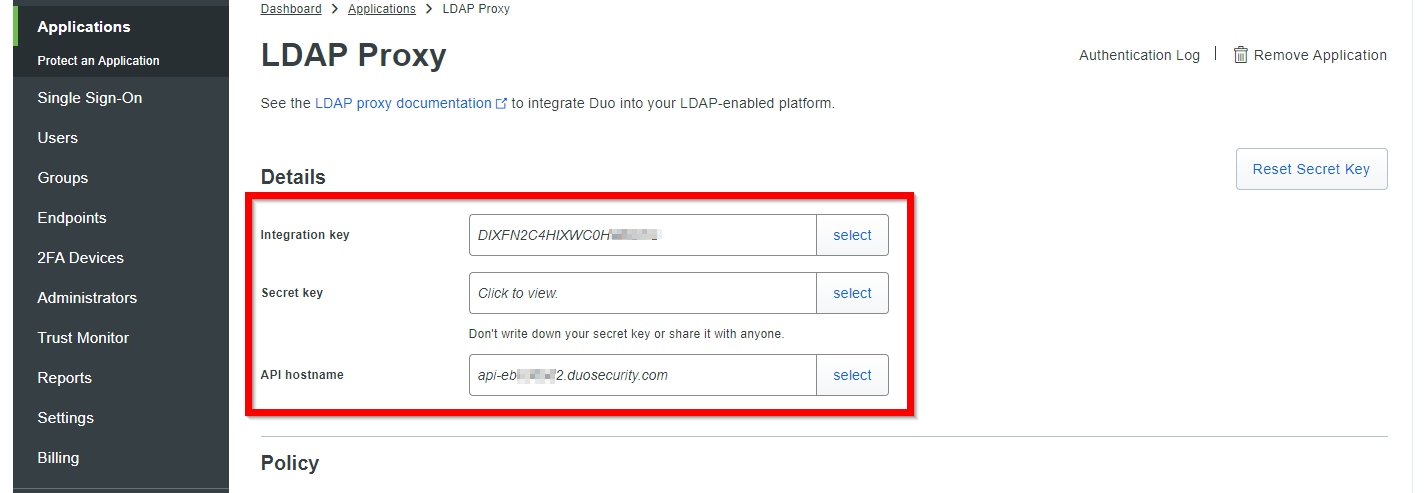
- On top of the LDAP Proxy configuration screen, you will get three essential values that need to be noted: Integration key, Secret key, and API hostname.

- After scrolling the screen, you will see additional settings. Fill the Name field with its value, which will be displayed for users on the authorization screen.
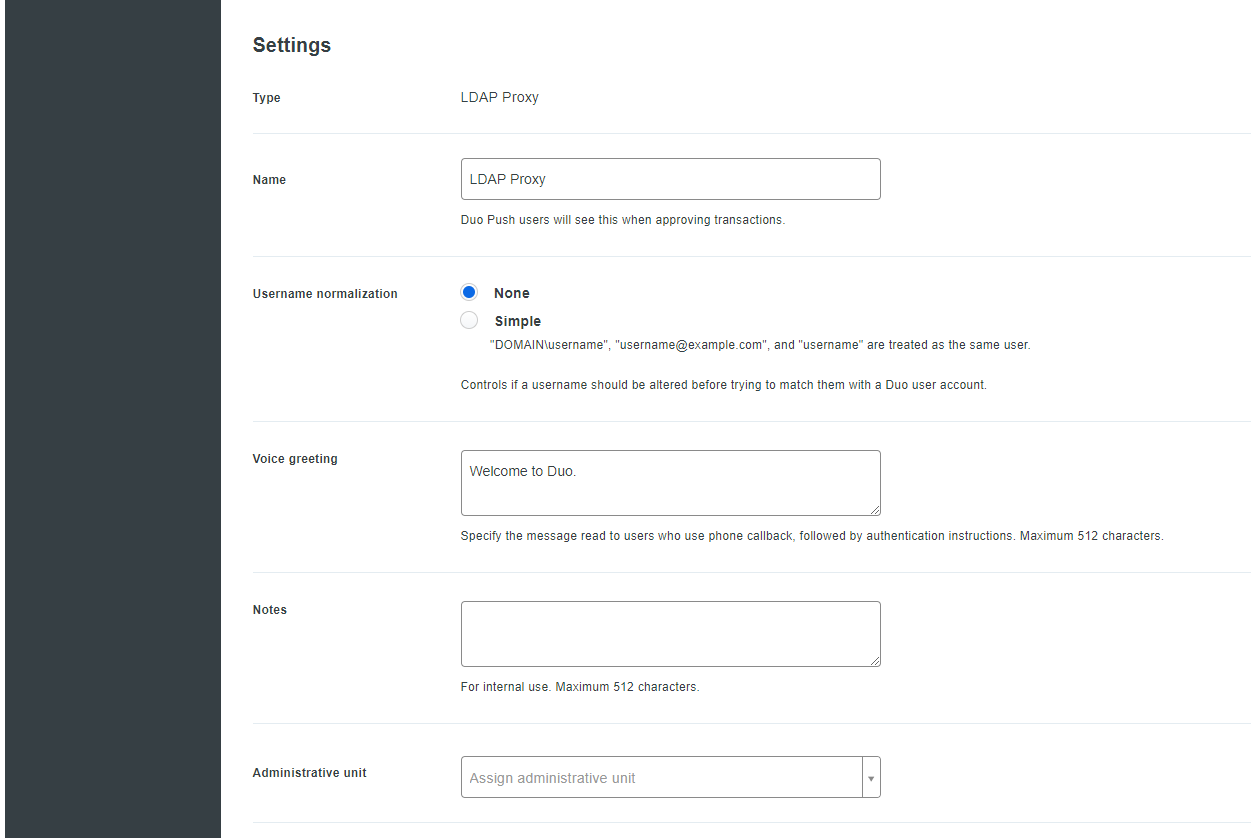

- Scroll to the bottom of the screen and click on the Save button.
Install the Duo Authentication Proxy
To install the Duo Authentication Proxy, you will need the host with Windows. The procedure for the Linux host may be found on the official DUO documentation.
- Log in to your Windows machine.
- Download the latest version of DUO Proxy for Windows
https://dl.duosecurity.com/duoauthproxy-latest.exe - Run the downloaded installer as a User with administrator privileges and install the proxy.
- When the installation is done, configure the proxy by editing the file:
C:\Program Files\Duo Security Authentication Proxy\conf\authproxy.cfg - Fill in the
ad_clientsection to configure LDAP/ActiveDirectory connection:- host - The IP/hostname of LDAP/ActiveDirectory service.
- service_account_username - The username of a domain account that has permission to bind to your directory and perform searches. We recommend creating a service account that has read-only access.
- service_account_password - The password corresponding to service_account_username.
- search_dn - The LDAP distinguished name (DN) of an Active Directory container or organizational unit (OU) containing all of the users you wish to permit to log in. For example
search_dn=DC=example,DC=com
- Fill the
ldap_server_autosection to configure DUO Authentication Proxy as the LDAP server:- ikey - Your integration key that you did get in the DUO configuration step.
- skey - Your secret key that you did get in the DUO configuration step
- api_host - Your API hostname (i.e. api-XXXXXXXX.duosecurity.com) that you did get in the DUO configuration step
- client - The mechanism that the Authentication Proxy should use to perform primary authentication. This should correspond with a “client” section elsewhere in the config file. In this case, when only one client is configured, use the
ad_clientWarningad_client - Use Active Directory for primary authentication. Make sure you have a [ad_client] section configured. Neither [radius_client] nor [duo_only_client] are valid for use with [ldap_server_auto]. This parameter is optional if you only have one “ad_client” section. If you have multiple, each “server” section should specify which “client” to use.
- Make sure the config file is similar to following:
[ad_client] host=ldap.jumpcloud.com service_account_username=xxxxxx service_account_password=xxxxxxxxxxxx search_dn=ou=Users,o=xxxxxxxxxxxxxxxx,dc=jumpcloud,dc=com auth_type=plain bind_dn=uid=search,ou=Users,o=xxxxxxxxxxxxxxxx,dc=jumpcloud,dc=com [ldap_server_auto] ikey=DIxxxxxxxxxxxxxxxxxx skey=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx api_host=api-xxxxxx.duosecurity.com failmode=safe client=ad_client port=1812 ; comment if you want to use the default LDAP port failmode=safe ssl_key_path=ldap_server.key ssl_cert_path=ldap_server.pem - Save and close the configuration file.
- Start the DUO Authentication Proxy
/opt/duoauthproxy/bin/authproxyctl start - Ensure that DUO Authentication Proxy is running
/opt/duoauthproxy/bin/authproxyctl status
Configure Identity provider in WEDGE
Configure Wedge to use DUO Authentication Proxy as the Identity Provider. If you want to know more about IdP, read this article.
- Log in to Acreto WEDGE
- From the left menu, choose Objects > Identity Providers
- Click on the Add new + button.
- Fill the form with proper values:
- Name - the representative name of the Idp - e.g., DUO LDAP
- Description - infromative description of IDP - e.g. DUO Authentication Proxy
- Identity Provider Type - choose LDAP
- Host - set the LDAP server to the IP address or hostname of your Duo authentication proxy
- Port - set the LDAP server port to 636 to secure the connection with SSL.
- Username - the name of the user that has been used for the DUO Authentication Proxy configuration.
- Password - the same password that has been used for the DUO Authentication Proxy configuration.
- User Base DN - Proper DN config.
- Save & commit
Summary
Thanks to Acreto and Multi-Factor Authentication, the administrator can force users to use multi-factor logging, increasing the organization’s security level.