Linux - Manual IPsec Configuration
Prerequisites
- Ubuntu 18.04 or newer installed on your device
- Ecosystem set up with proper security policies
Create Gateway for IPsec
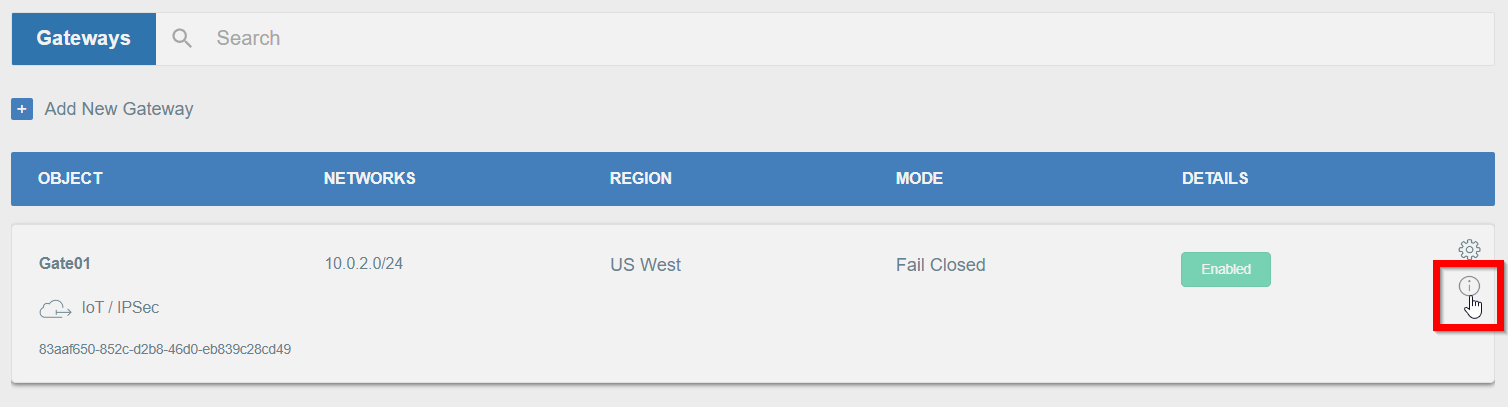
If you didn’t do it yet, you need to create a new Gateway device on the Acreto platform.
-
Log in to the Acreto platform at wedge.acreto.net
-
Select your ecosystem and go to Objects using the left menu.
-
Click Add new Object and select Gateway.
-
Fill at least:
-
Name: - the name of IPSec connection, needs to be compatible with Strongswan connection name requirements (basically, only letters and numbers)
-
Category: IoT
-
Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted)
-
Local Networks: - your local network addresses that should be routed through this gateway
Note: To simplify testing, add IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow testing connectivity from the gateway through Acreto using ping, traceroute, and similar tools.
-
-
Save the created Gateway by pressing Add.
-
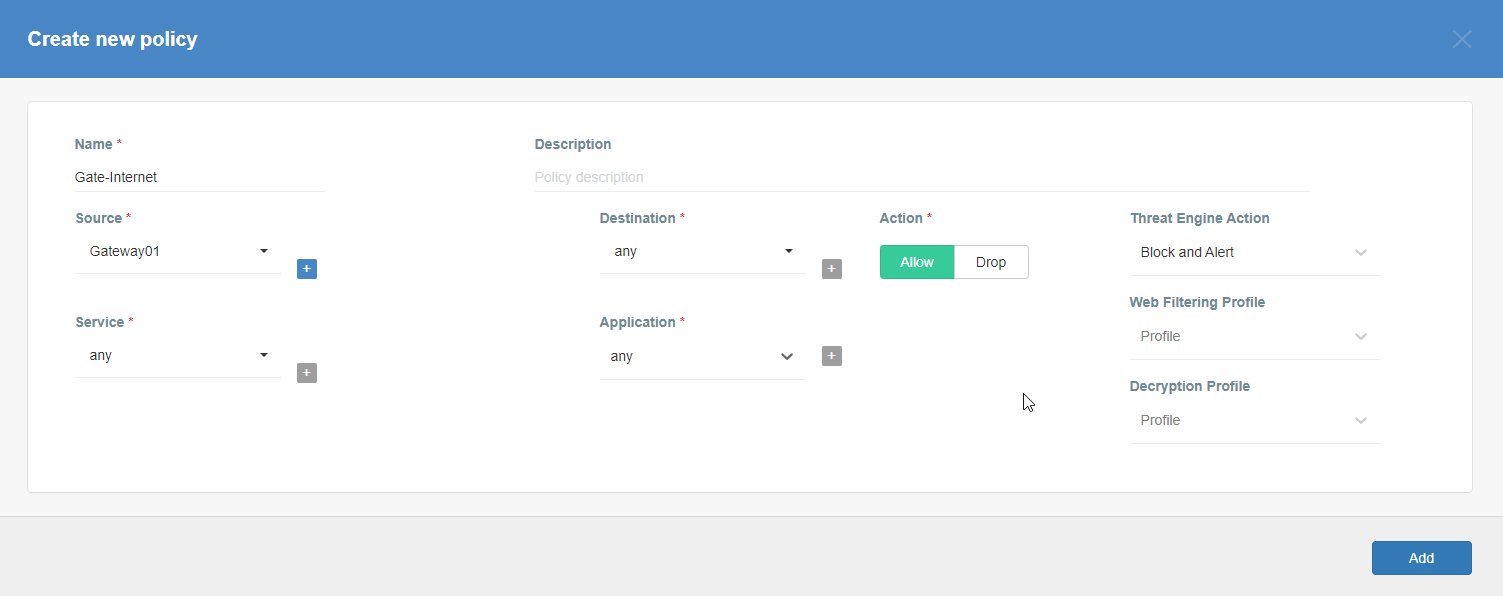
Add security policy that will allow communication from the Gateway device to the Internet.

-
Commit pending changes (top of the screen)
Note: to successfully test your connectivity, you also need to create a security policy that will allow traffic going through your device.
Generate Strongswan config files
-
Log in to the Acreto platform at wedge.acreto.net
-
Select your ecosystem and go to Objects using the left menu
-
Open the gateway object which you want to use by clicking on its “Info” button.
-
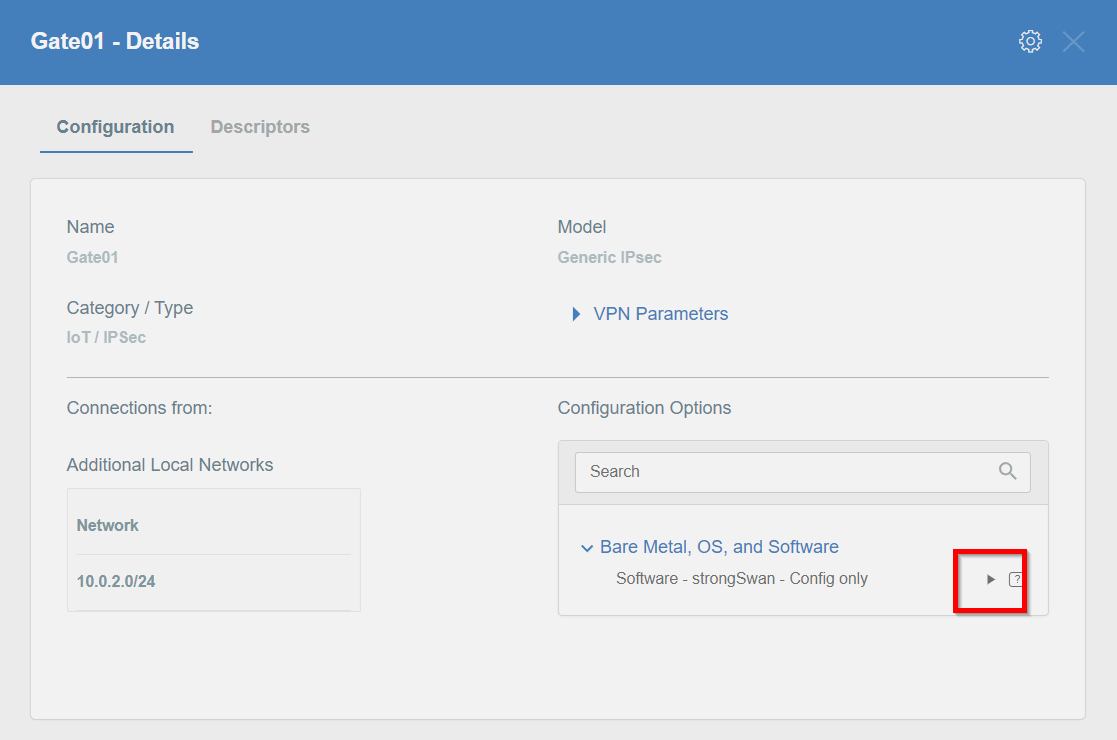
Download Strongswan configuration using Configuration Options > Software Clients with Config
-
Download Strongswan configuration to your device.
Install dependencies on the device
-
Log in to your device.
-
Set up time/date server, to do that use the following command:
sudo timedatectl set-ntp on ntpdate -s ntp.ubuntu.com -
Install required packages:
sudo apt-get update
sudo apt-get install -y --no-install-recommends \
apt-utils \
ifupdown2 \
inetutils-ping \
strongswan \
kmod \
openssl \
libstrongswan-standard-pluginsApply configuration files
-
Log in to your device.
-
Unzip downloaded config file and copy respective files to their location:
unzip -x 10b6c4d8-0e9a-f5c7-c4c9-7edd6a6493ed.zip sudo cp -r etc/* /etc -
Ensure the files are in proper location
/etc/ipsec.d/[connection uuid].conf/etc/ipsec.d/leftifupdown.sh/etc/ipsec.secrets
Enable gateway mode (optional)
To work in gateway mode, you need to configure IPsec to use VTI devices.
Modify /etc/strongswan.d/charon.conf - leave all on defaults except for the
following:
install_routes = no
install_virtual_ip = no
ignore_routing_tables = 220Modify connection file /etc/ipsec.d/*.conf to enable VTI support -
uncomment mark and leftupdown options:
# uncomment this line for policy routing configuration
mark=105
# uncomment this line for policy routing configuration
leftupdown=/etc/ipsec-leftupdown.shDetermine connection name as defined in ipsec configuration:
CONN=`grep '^conn .*' /etc/ipsec.d/*.conf|cut -d' ' -f2`; echo $CONNCreate a routing file that will contain (remote) networks which should be routed through the Acreto platform - by default, it would be a default gateway:
cat > /etc/ipsec.d/$CONN.route << EOF
0.0.0.0/0
EOFEnable IP forwarding
echo net.ipv4.ip_forward=1 > /etc/sysctl.d/10_ac_ip_forward.conf
systemctl restart systemd-sysctlConfigure connection autostart
sed -i'' -e s/auto=route/auto=start/ /etc/ipsec.d/*.confStart IPSec
-
Restart ipsec service with following command:
ipsec restart -
Wait approximately 10 seconds, and check status of ipsec:
ipsec statusall -
If the connection did not start, try to take it up manually:
CONN=`grep '^conn .*' /etc/ipsec.d/*.conf|cut -d' ' -f2`; echo $CONN ipsec up $CONNIt should display information useful for debugging purposes.
-
Ensure everything works fine with:
ipsec statusall ip address show ip route show Check if you have Internet access enabled. -
Check if you have Internet access enabled.
Validation
Ensure that traffic goes through our platform (with traceroute, mtr,). Verify with the command below
Tunnel verification command
mtr 8.8.8.8Expected output after successful tunnel creation
Host Loss% Snt Last Avg Best Wrst StDev
1. 100.65.0.30 0.0% 9 225.1 225.1 224.6 225.8 0.3
2. 100.65.0.1 0.0% 8 225.9 227.5 225.7 237.1 3.9
3. ???
4. nyk-b2-link.telia.net 0.0% 8 226.0 226.9 226.0 228.3 0.7
5. 72.14.218.254 0.0% 8 227.1 227.8 226.4 230.4 1.2
6. 108.170.248.97 0.0% 8 227.1 227.2 226.8 227.9 0.4
7. 108.170.227.211 0.0% 8 226.5 226.9 226.0 227.7 0.6
8. dns.google 0.0% 8 226.7 227.6 226.7 229.2 0.8