Create first security policy
Overview
In the previous step, you configured and connected your first Thing to your Ecosystem. Now, you need to create a security policy.
A security policy is a set of rules that manages network traffic in an Ecosystem. These policies allow you to decide what traffic should be allowed, inspected, or blocked.
Acreto follows a Zero-Trust approach. This means that all network traffic is blocked by default.
Security policy: Allow all
To allow communications to flow through an Ecosystem, you must define a set of security policies. Without a matching security policy, the traffic is blocked.
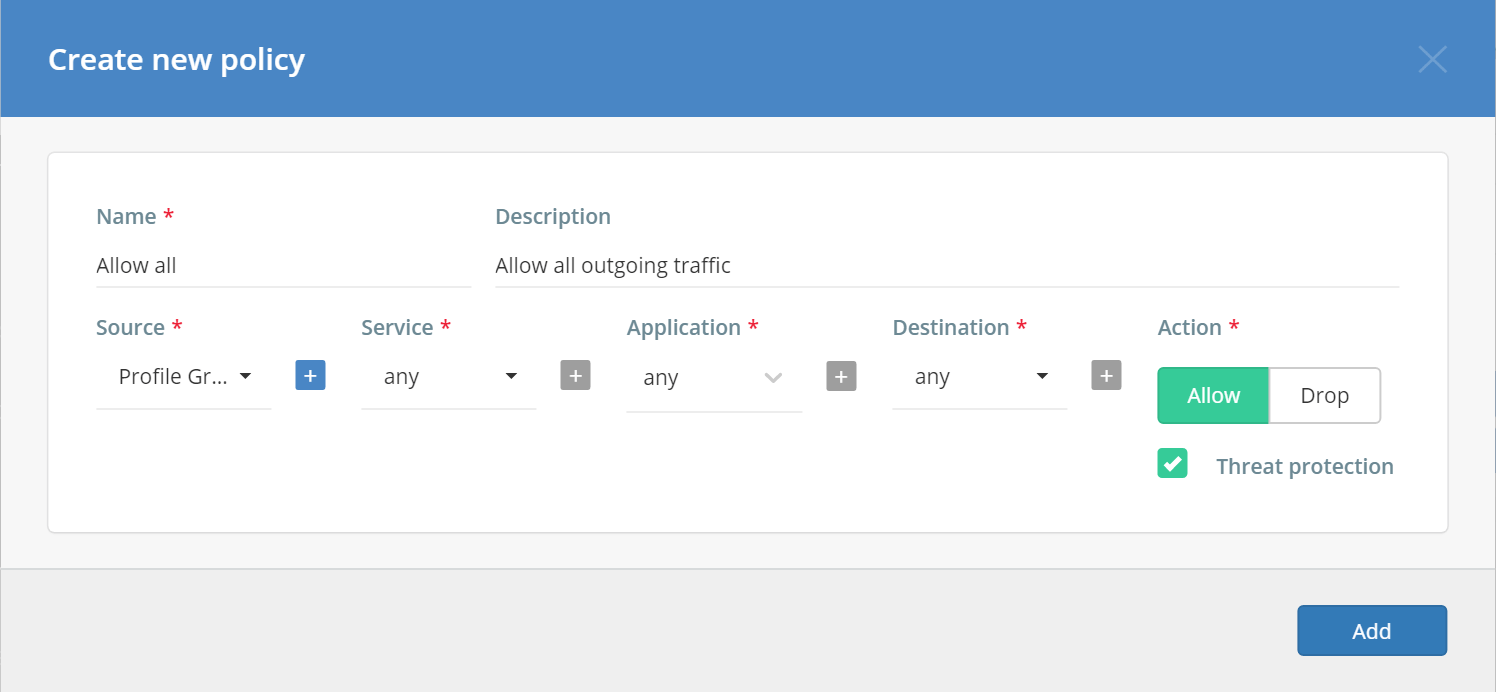
For testing purposes, we’ll guide you through the creation of an Allow all traffic security policy. To do this, you will complete an Add New Policy form as shown below.
Complete the form by entering the correct values:
- Name - use a descriptive name so that others in your organization will know what this policy is for; in this case, Allow all.
- Description – add a short description of the policy; in this case, Allow all outgoing traffic.
- Source - choose the source where the traffic will come from; in this case, select your profile group.
- Service - select a protocol (like TCP, UDP, ICMP) and destination port of the traffic; in this case, Any.
- Application - choose the applications for which the policy applies; in this case, Any.
- Destination - choose a target where the traffic should be directed; in this case, Any.
- Action - allow/drop traffic when the conditions have been met; in this case, Allow.
- Threat protection - decide whether you want to enable threat protection for the traffic; in this case, Marked.
- Click on the Add button to save the configuration.
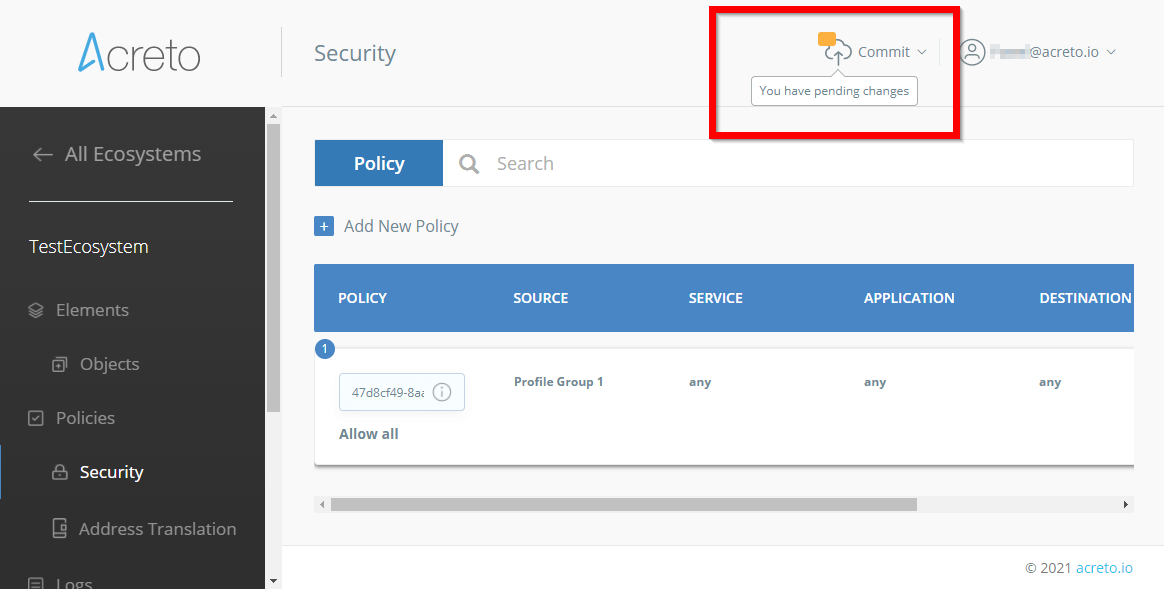
- Once the new security policy has been added and is visible on the list, you must Commit your changes.
Before saving, the form should look like the image below :
Your changes will not be applied until you Commit them!
Now, any Thing in a selected Profile group (Source) should be able to securely connect to any destination.
Security Policy: Block Facebook Using Application Control
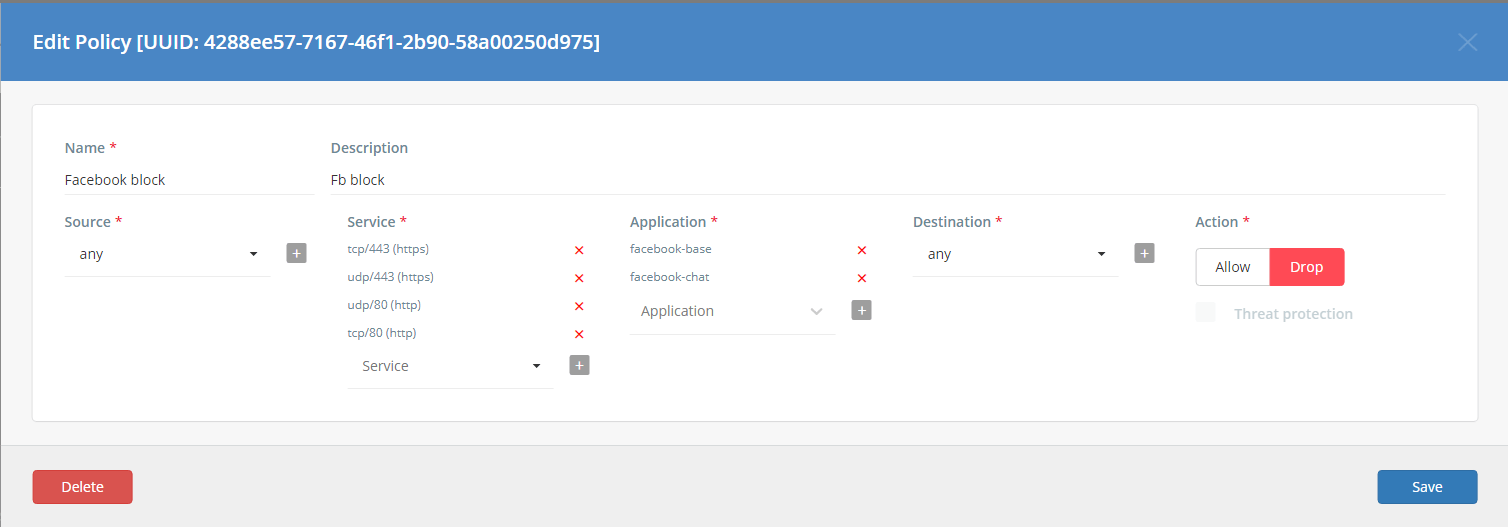
If you want to block Facebook from accessing your Ecosystem users, you should use the Application Control security policy. To create such a policy, fill out the Add New Policy form as shown below.
- Name - use a descriptive name so that others in your organization will know what this policy is for; in this case, “Block facebook.com.”
- Description – create a short description of the policy; in this case, Block all facebook.com traffic.
- Source - choose the source from where the traffic will come; in this case, Any.
- Service - select the protocol (TCP, UDP, ICMP) and destination port of the traffic; in this case, Any.
- Application - choose the application(s) for which the policy applies; in this case, facebook-base and facebook-chat.
- Destination – select a target where the traffic should go; in this case, Any.
- Action - allow/drop traffic when the conditions have been met; in this case, Drop.
Click the Add button to save the configuration.
Once the new security policy has been added and is visible on the list, you must Commit your changes.
Your changes will not be applied until you commit them!
After committing your settings, any Facebook traffic now coming through the Ecosystem should be blocked.