OKTA
This feature is currently in Beta.
Introduction
In this article, you’ll learn how to integrate OKTA with an Acreto Ecosystem. The OKTA integration allows your Acreto Ecosystem to utilize the user credentials managed by OKTA to connect to the Ecosystem using Acreto TLS Client.
It uses the LDAPS (LDAP Secure) protocol and the OKTA LDAP Interface which can be deployed on the OKTA account.
How To
Step 1: Enable OKTA LDAP Interface
To configure your OKTA account, you need to enable the OKTA LDAP Interface. Please go through the following procedures:
- Enable OKTA LDAP Interface
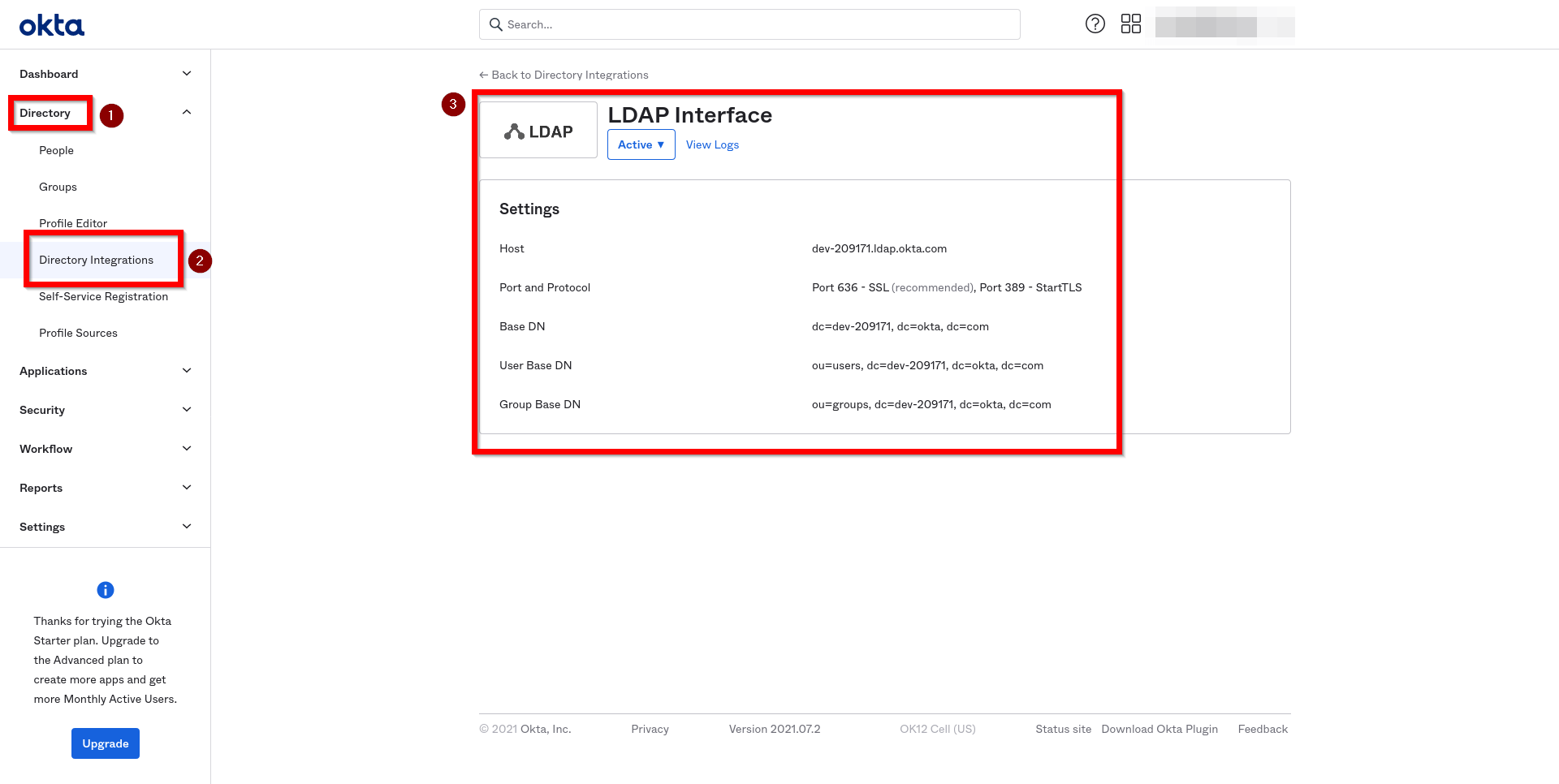
- Read OKTA LDAP configuration details:
- Create OKTA Third-Party Administrator account with read-only administrator role. This administrator account will be used by Acreto Ecosystem to authenticate with OKTA.
Ensure that created Third-Party Administrator account will not be challenged with OKTA Multifactor Authentication for requests originating from your Ecosystem IP addresses. You also need to whitelist the following addresses on your server section of the Identity Provider creation page in step 2.
Step 2: Configuration of Acreto Ecosystem
-
Add New Identity Provider
To add a new Identity Provider:
- Select Objects and Identity Providers from the left menu.
- Click on “Add New”.
- Fill in the following information:
- Name and Description
- Host, User Base DN, Group Base DN - as provided on OKTA LDAP Interface settings screen
- Username and Password - credentials of the OKTA Third-Party Administrator account created in step 1
- Save your changes.
-
Create Security Policy to allow traffic sent by your users
When you create a new Identity Provider, a new Profile Group is created with a name containing Identity Provider name, for example:
Identity Provider LDAP001 (fa45). By default, all users authenticated with this Identity Provider are assigned to that Profile Group.To allow traffic from your users using that Identity Provider, select this Profile Group in the Source field of Security Policy. For detailed instructions on creating a Security Policy, see Create first security policy.
-
Commit your changes
Step 3: Testing
To test the integration:
- Generate Onboarding Portal Link
- Open generated Onboarding Portal Link and follow the instructions
- Connect to your ecosystem providing username and password managed by OKTA
To get more information about end-user onboarding experience, see onboarding documentation
Next steps
- Customize your security policies
- Define mappings of LDAP groups to Identity Provider groups
- Send invitations to your users
Summary
Thanks to Acreto and OKTA Identity Provider Integration, users can connect to an Acreto Ecosystem with the same credentials utilized for other internal resources on their network domain.
See also
- OKTA documentation:Set up and manage the LDAP Interface