Active Directory - Azure
Before You Start
Overview
In this article, you’ll learn how to integrate your Azure Active Directory with an Acreto Ecosystem. This process involves the following steps:
- Configuration of Azure AD
- Configuration of Acreto Ecosystem
- Providing an Onboarding Portal link to users
This feature is currently in beta mode.
Prerequisities
In order to integrate Acreto with Azure Active Directory, you will need:
- Active Acreto Ecosystem
- Azure Active Directory - Active Subscription is needed - but basic features are free
- Azure Active Directory Domain Services - Active Subscription is needed - ~$109.50/month/set
The Purpose of Azure Active Directory Integration
An Azure Active Directory integration allows your Acreto Ecosystem to utilize the user credentials stored in your Active Directory to connect to the Ecosystem using Acreto TLS Client.
It uses the LDAPS (LDAP Secure) protocol and the Domain Services which can be deployed on the Azure account to sync with AD passwords.
The LDAPS protocol is used to establish communication between the Acreto Ecosystem and the Azure Active Directory.
Administrators integrate with a Lightweight Directory Access Protocol (LDAP) directory to streamline the user login process and to automate administrative tasks, such as creating users and assigning roles. An LDAP integration allows the system to use it’s existing LDAP server as the master source of user data.
Typically, AD integration is also part of a single sign-on implementation.
How Does it Work?
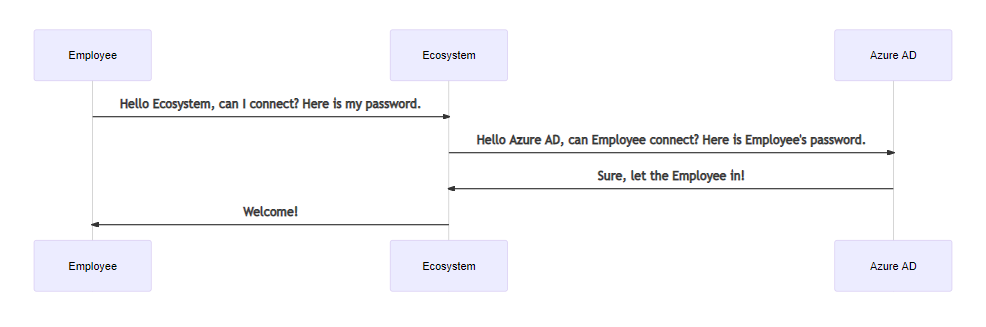
The integration uses the LDAP service account credentials to retrieve the user’s distinguished name (DN) from the LDAP server. Given the user’s DN value, the integration then reconnects with LDAP using the user’s DN and password.
In the diagram below, you can see the communication flow between some Employee (trying to connect to the Ecosystem using Acreto TLS Client), Acreto Ecosystem and Azure AD.
The integration never stores LDAP passwords on the Ecosystem.
The integration uses a read-only connection that never writes to the Azure Active Directory. The integration only queries for information.
How To
Configuration of Azure Active Directory
To configure your Azure Active Directory to work with Acreto, please:
- Configure secure LDAP for an Azure Active Directory Domain Services managed domain
- Enable password synchronization in Azure Active Directory Domain Services
- If you followed the first tutorial and don’t use on-premises AD the synchronization (between your Azure AD and Azure AD Domain Services) will be enabled by default. However it is needed to reset the password of all current users. It can be done by expiring all the current passwords, or resetting them manually from the Azure AD Users View.
Configuration of Acreto Ecosystem
1.Log in to New or Existing Ecosystem
-
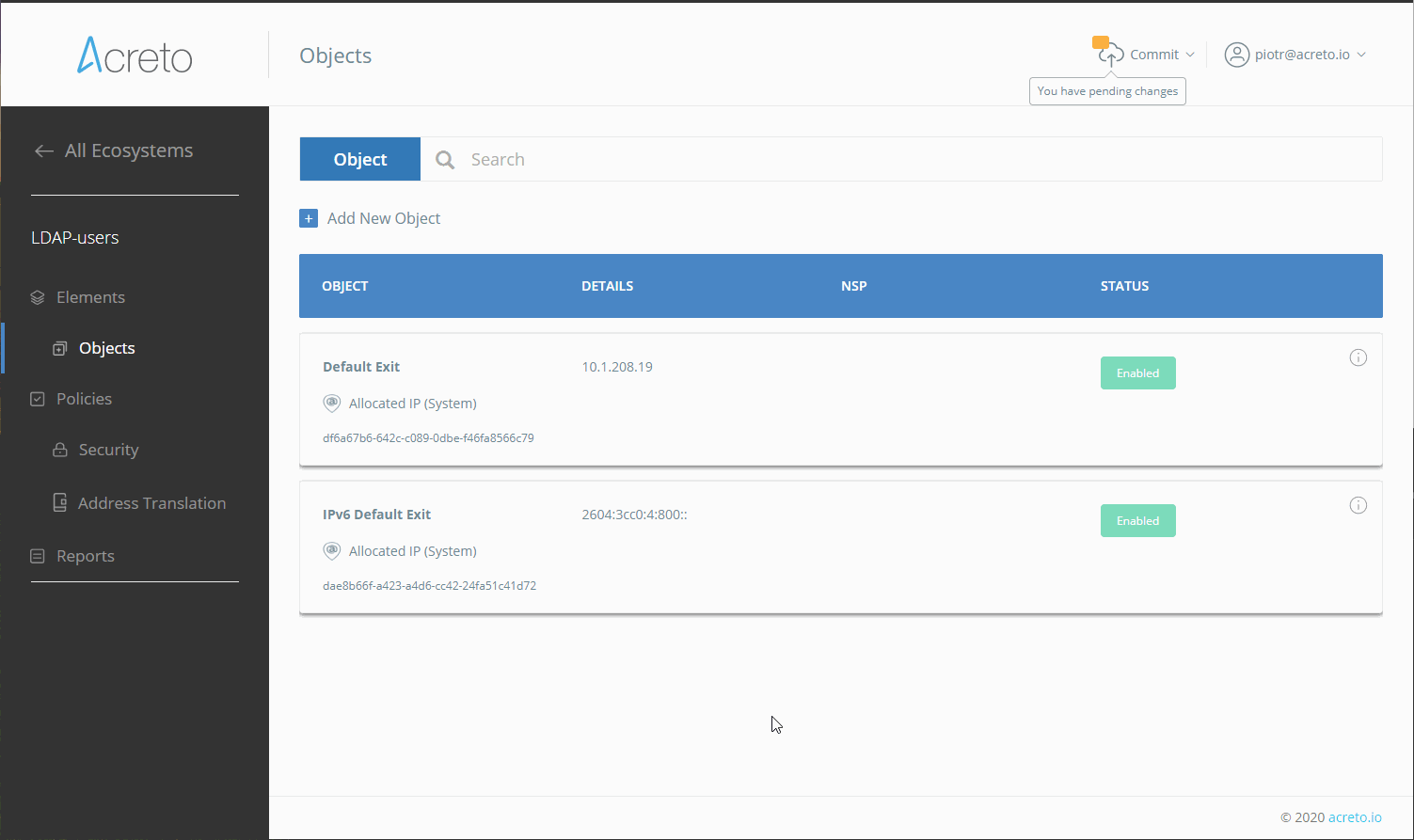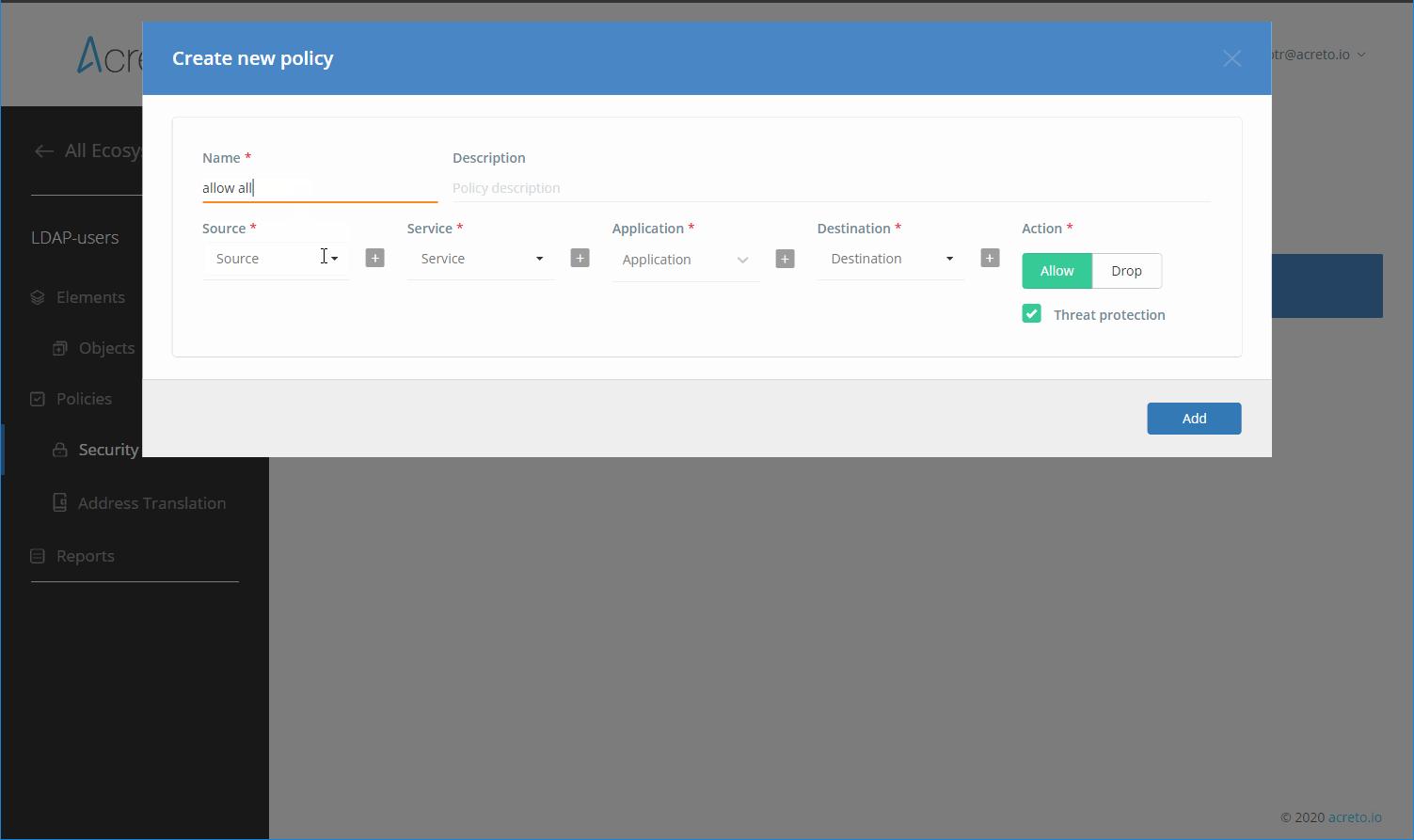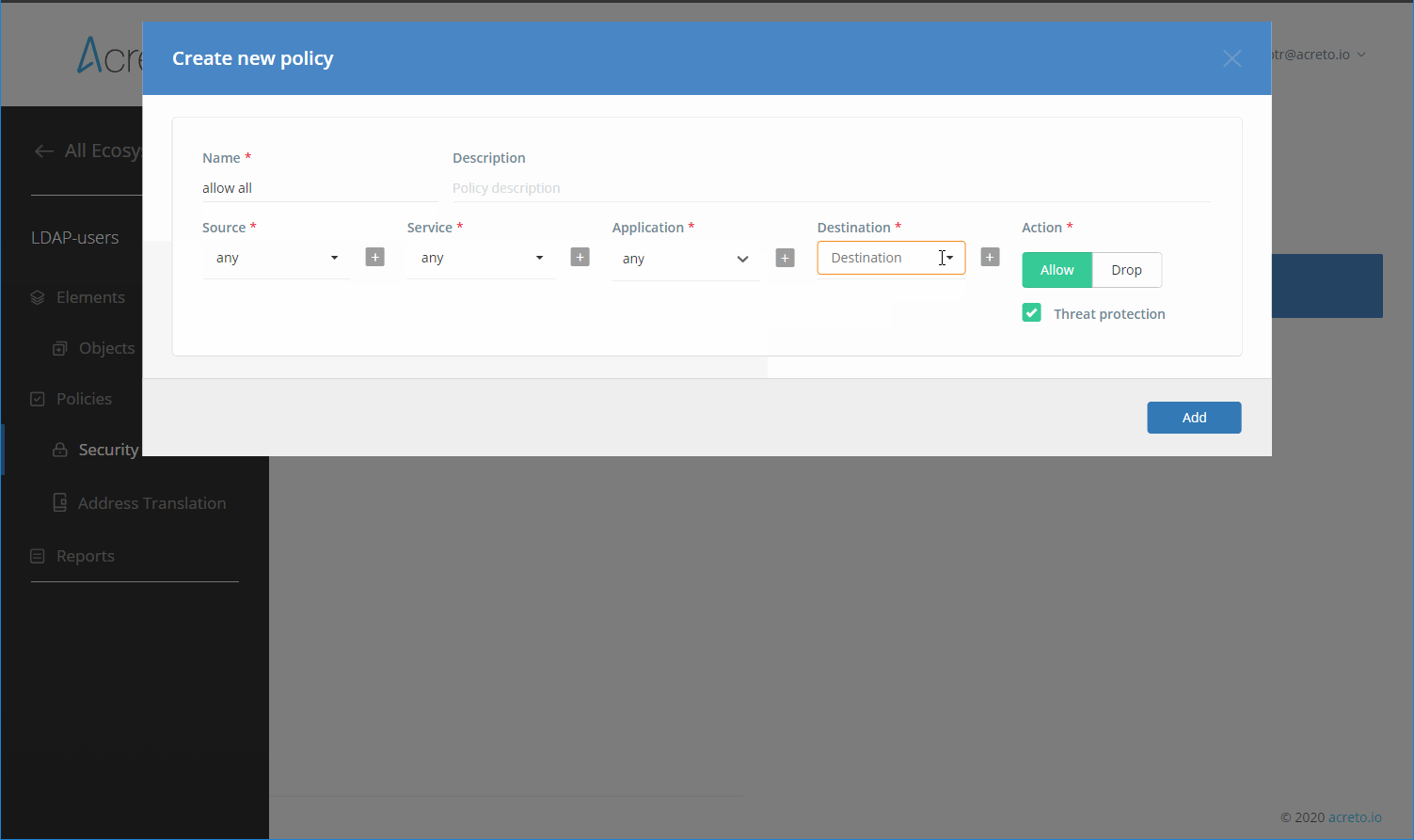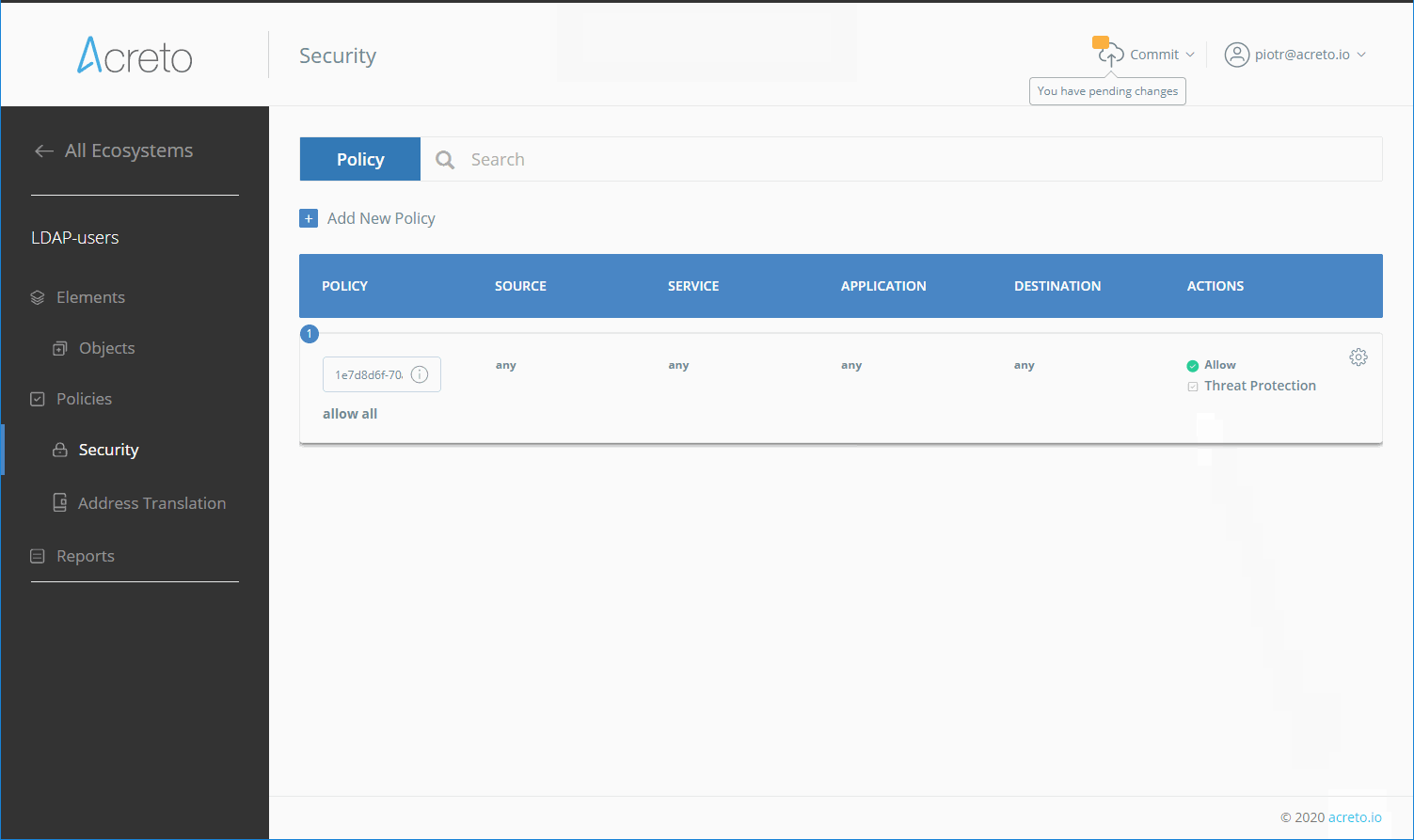
Create Security Policy
Create a Security Policy that allows users to connect through your Identity Provider to reach all destinations.
WarningIn beta mode, all users authenticated using Identity Providers belong to default profile group Profile Group 1. This will change in future versions.
To simplify the initial configuration, we will create a policy that allows all traffic to be passed through the Ecosystem.
InfoYou should customize the Security Policy to fit your needs once the Identity Provider setup is complete. It should be configured to limit access to network resources for each group (Profile Group).
-
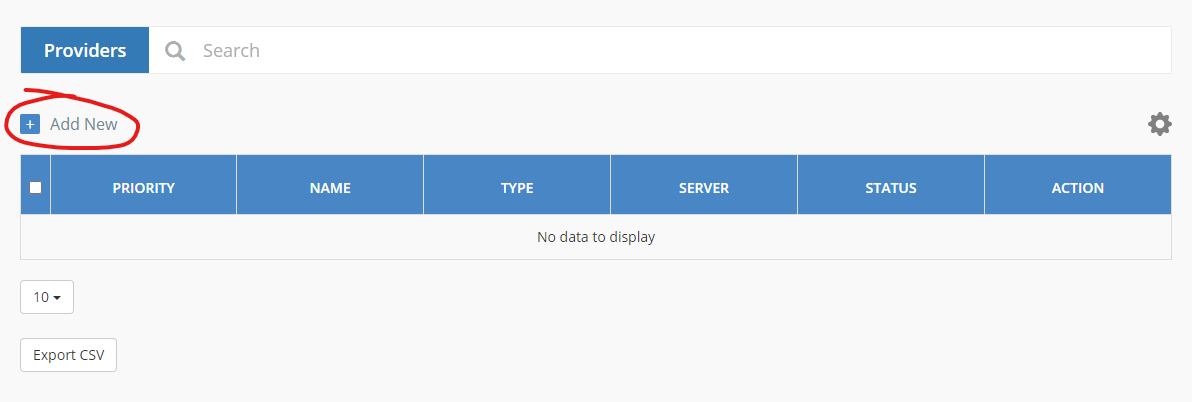
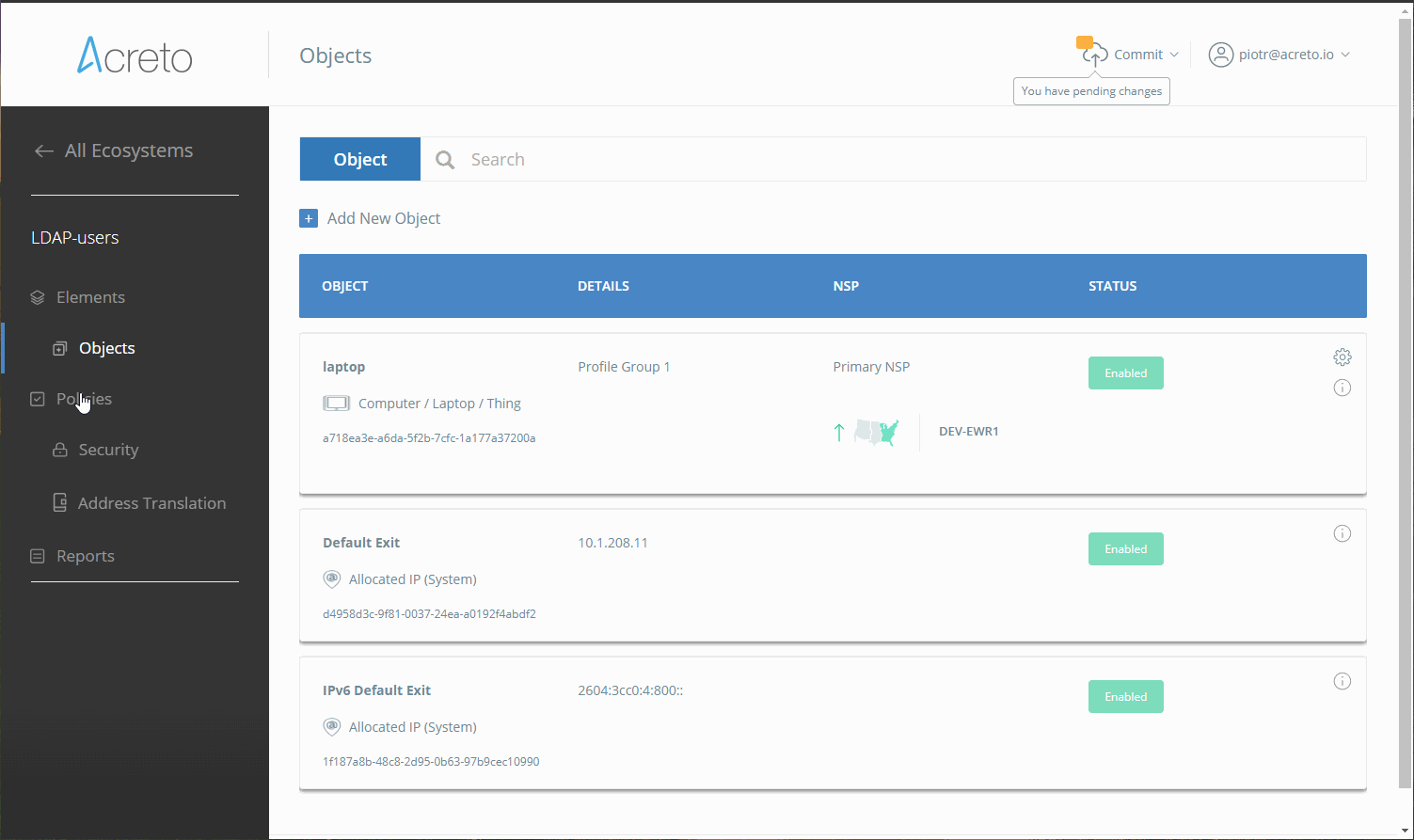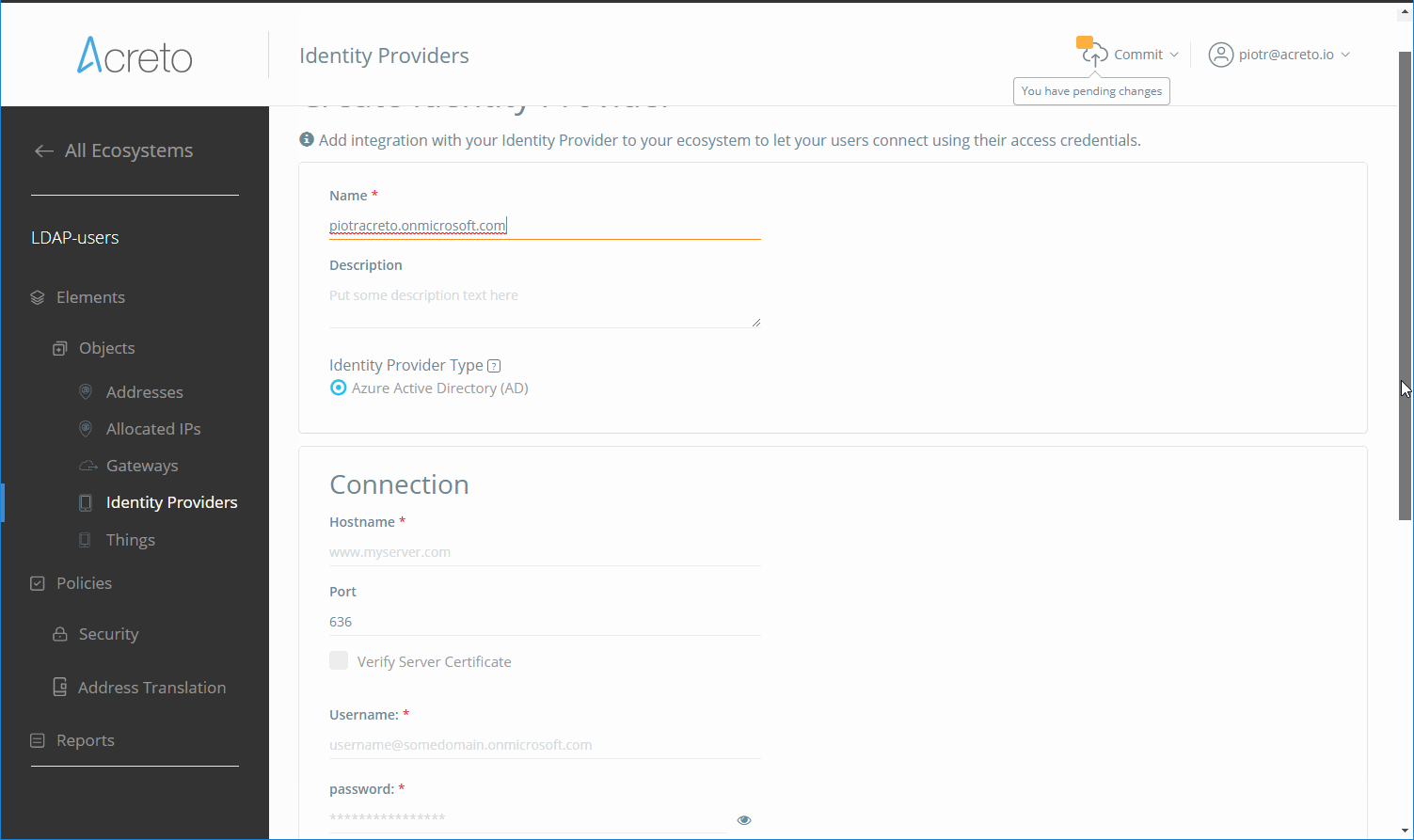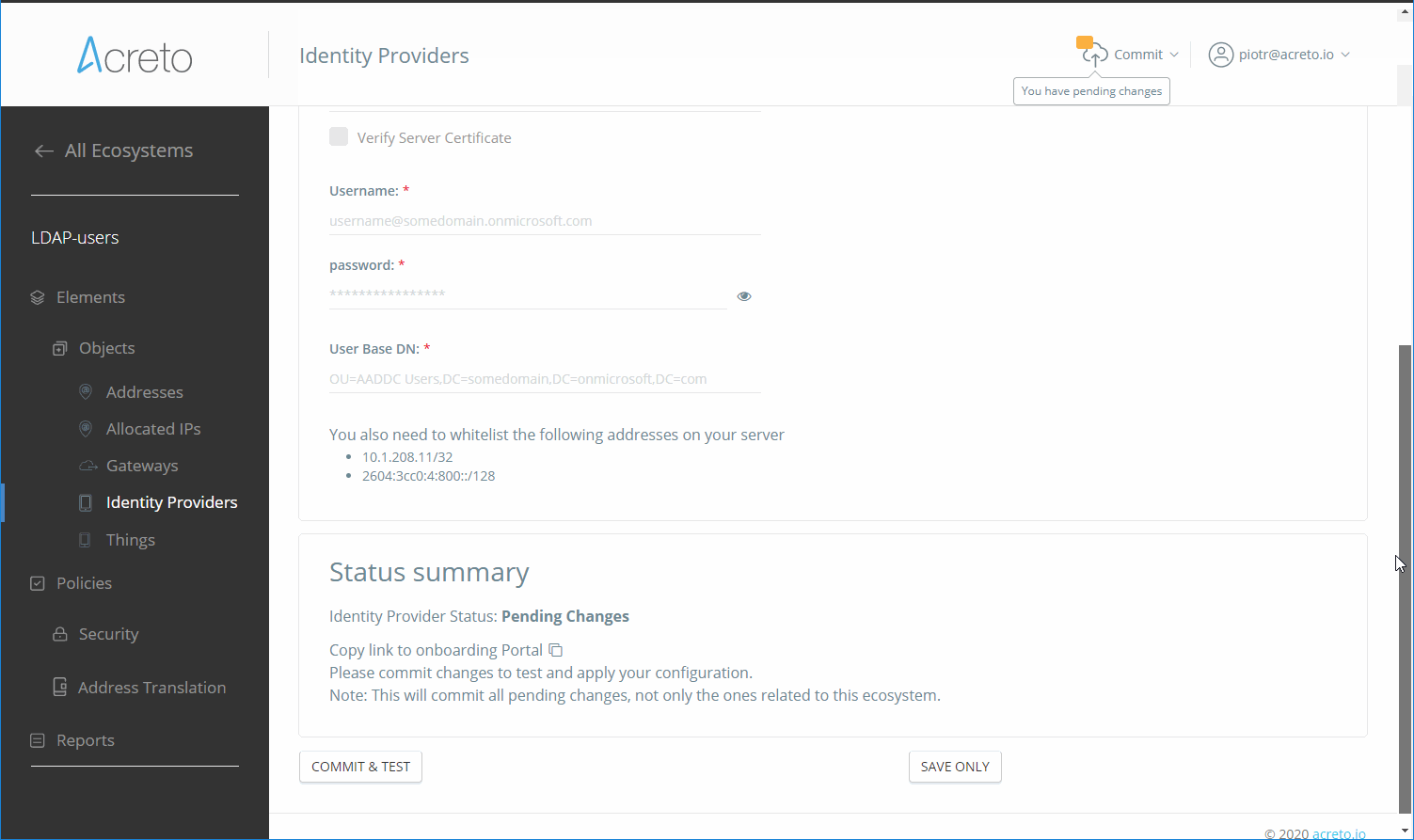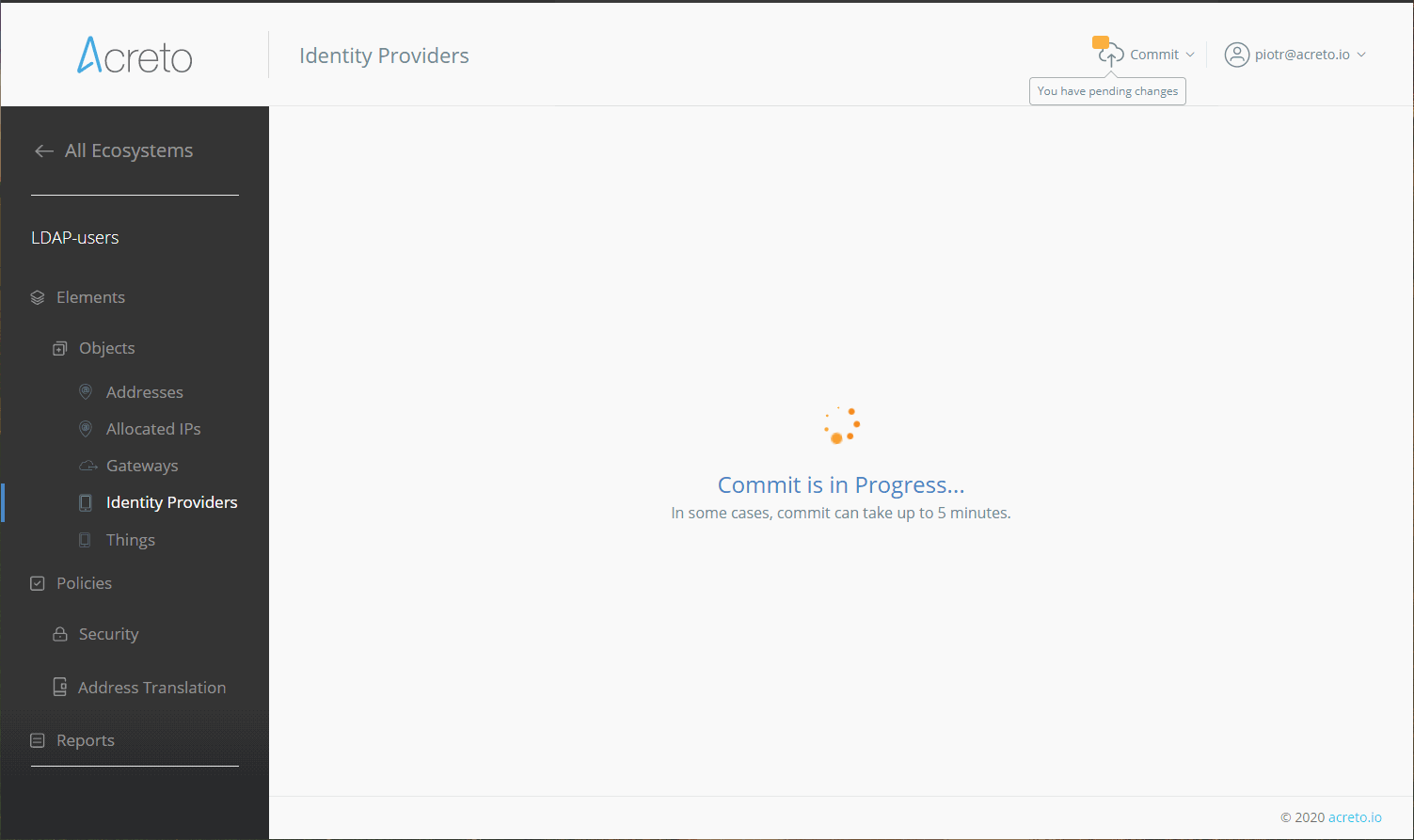
Add New Identity Provider
To add a new Identity Provider, select Objects and Identity Providers from the left menu and then click on “Add New”.
-
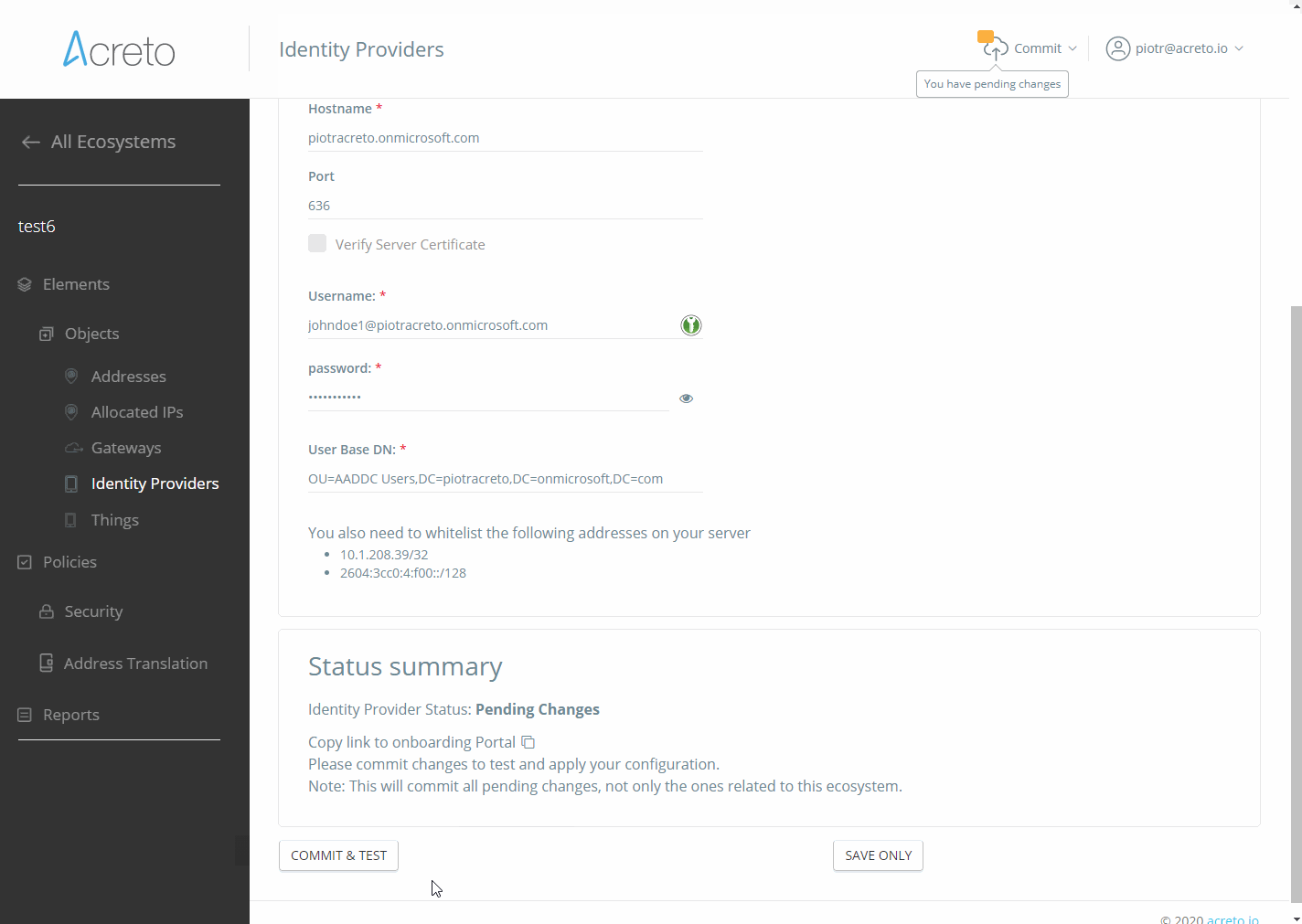
Fill the form with proper values:
- Name - descriptive name for this IdP
- Description - description of the IdP
- Identity Provider Type - in case of AD config choose one of two available options
- Host - domian or IP address of your AD server
- Port - 636
- Username - user that will be used to connection
- Password - password for the user account
- User Base DN - for Azure AD use
OU=AADDC Users, DC=somedomain, DC=onmicrosoft, DC=com, for On-premise Windows Server ADCN=Users, DC=SOMEDOMAIN, DC=com
Base DN and other values may be specific for your custom configuration. Check proper configuration in the AD control panel.
- Save and commit your changes
Provide Onboarding Portal Link to Your Users
To allow users, employees or team members VPN users to authenticate in OpenVPN using Azure AD credentials, Acreto offers unique and individual URLs for every Ecosystem portal called Onboarding Portal.
-
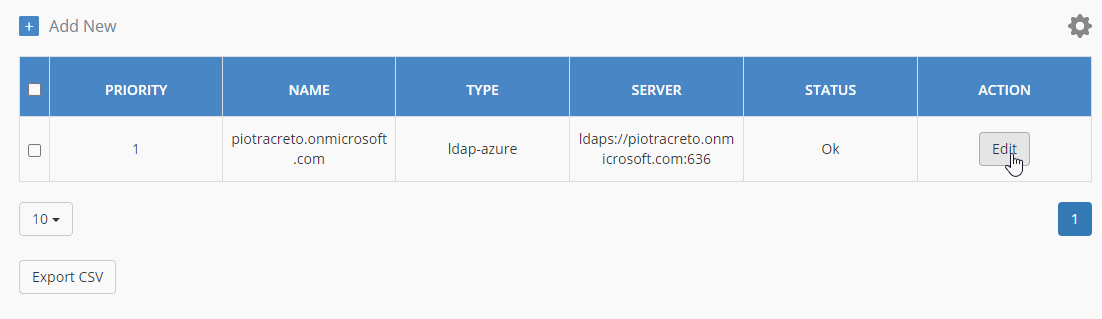
To access the unique URL to that portal, please click on Edit next to previously added IdP and scroll down.
-
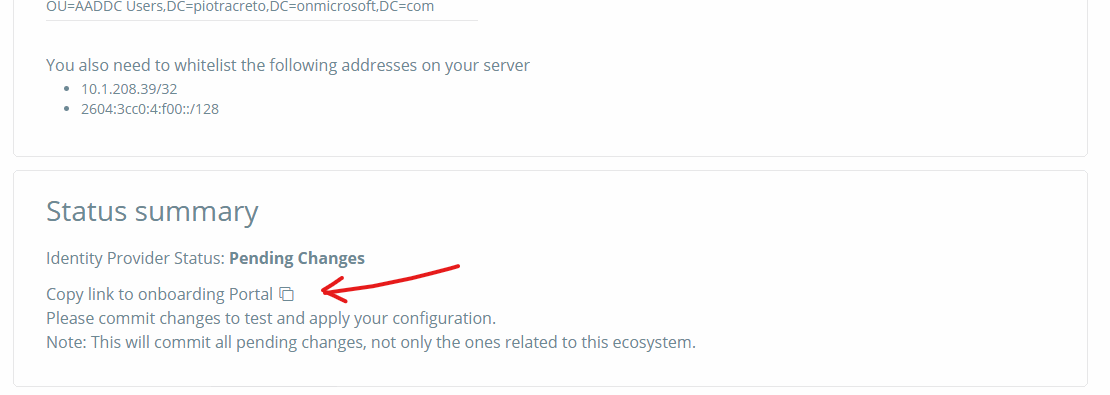
Then, click on the icon to copy the URL.
-
Now, provide the generated link to your users.
VPN User Experience
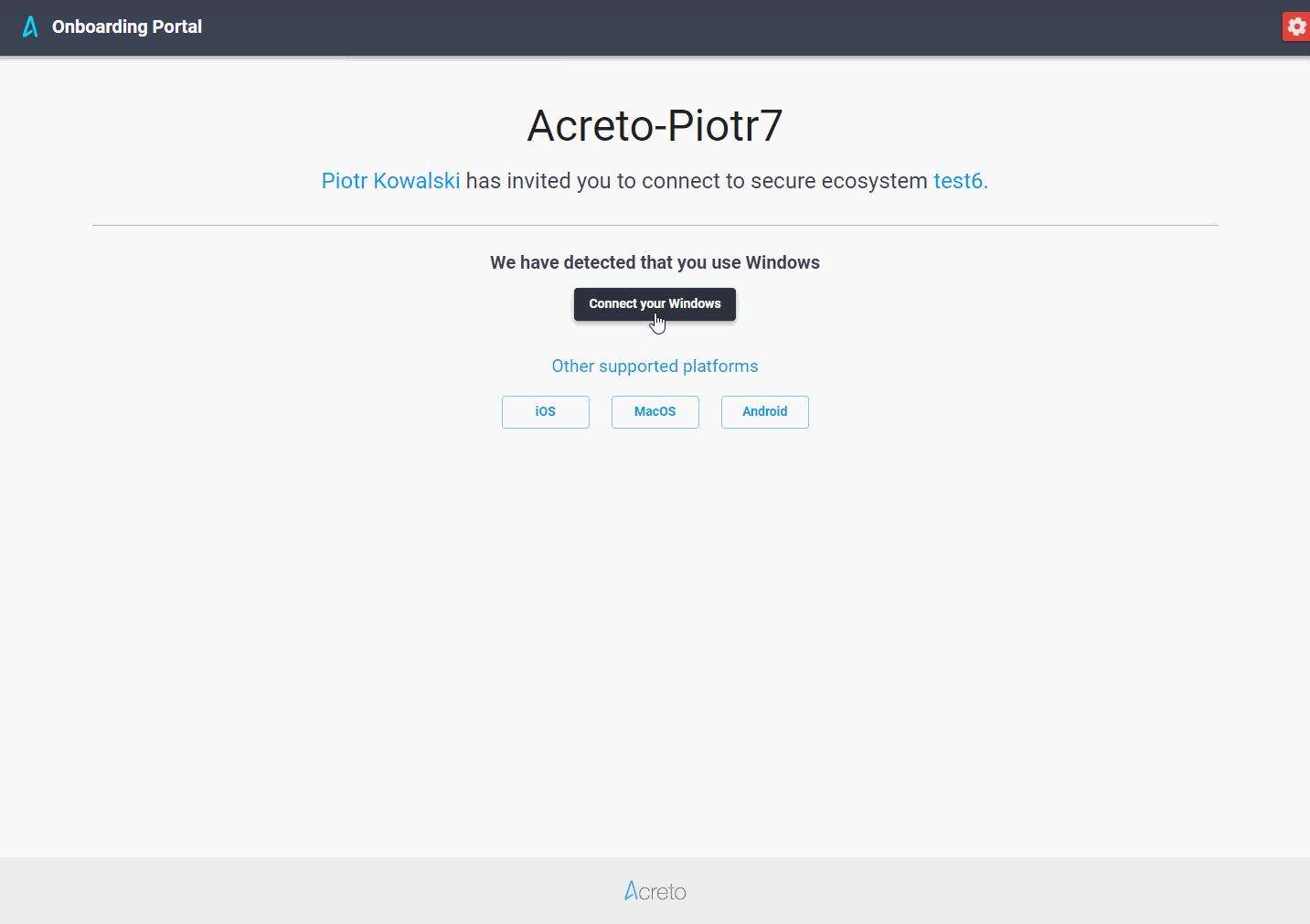
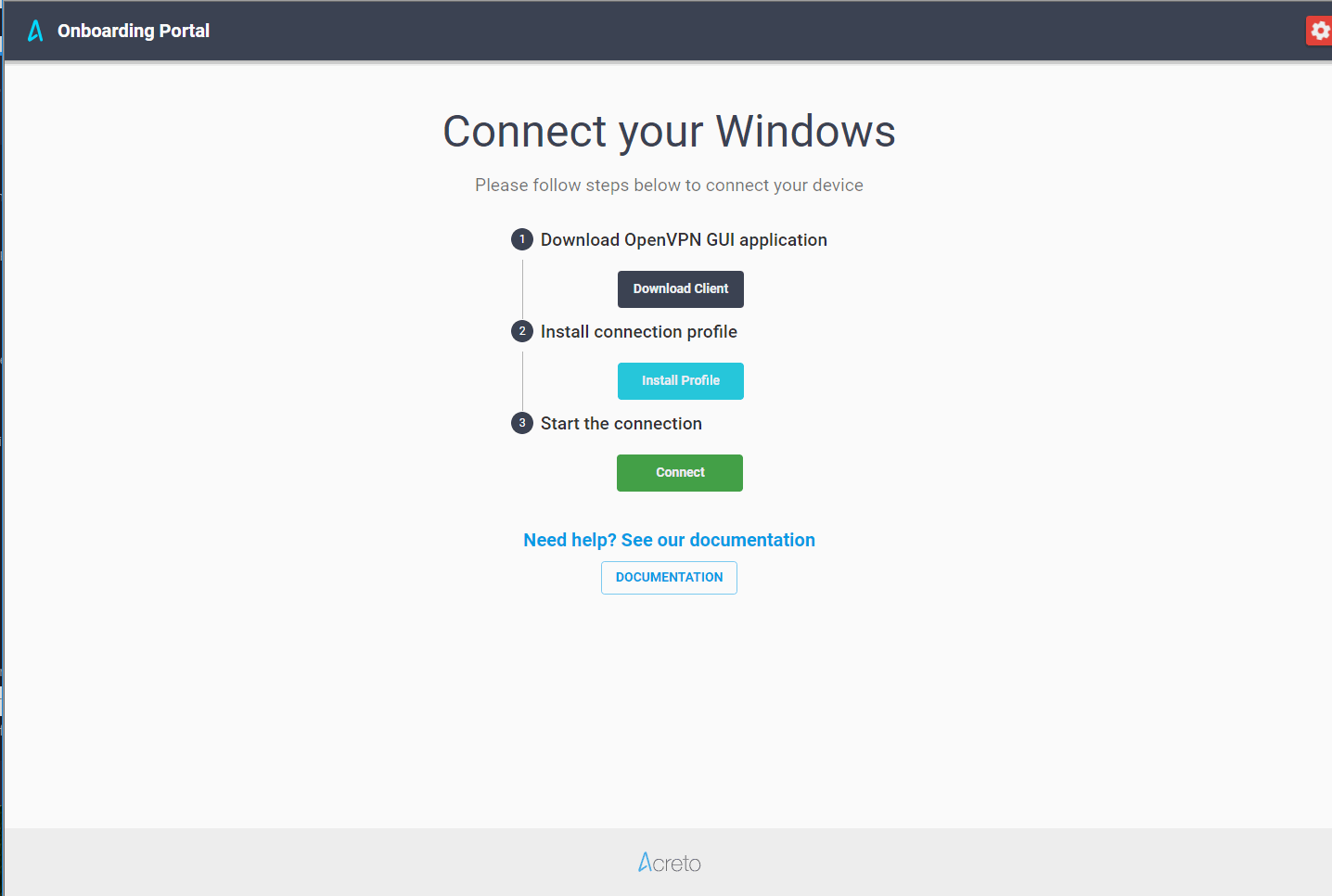
When the End User or Employee opens the Onboarding Portal, the Welcome Page will be presented.
The Ecosystem Admin should share this URL with the End Users, ask them to open it, and then follow instructions.
Frequently Asked Questions
-
Active Directory included into Office 365 subscription sufficient for the integration?
No, Office 365 subscription covers only the free Azure Active Directory.
You need Azure Active Directory Domain Services which is an additional subscription from Microsoft.
-
Why is it required to enable password synchronization in Azure Active Directory Domain Services?
Enable password synchronization in Azure Active Directory Domain Services - As documented on Microsoft article Tutorial: Configure secure LDAP for an Azure Active Directory Domain Services managed domain:
Users (and service accounts) can’t perform LDAP simple binds if you have disabled NTLM password hash synchronization on your managed domain.
Acreto uses LDAP simple binds, therefore NTLM password hash synchronization feature needs to be enabled.
If you followed the first tutorial and don’t use on-premises AD the synchronization (between your Azure AD and Azure AD Domain Services) will be enabled by default. However it is needed to reset the password of all current users. It can be done by expiring all the current passwords or resetting them manually from the Azure AD Users View.
Summary
Thanks to Acreto and Azure Active Directory Identity Provider Integration, users can connect to an Acreto Ecosystem with the same credentials utilized for other internal resources on their network domain.
Also, Acreto Ecosystem Admin(s) can re-use any existing password and security policies that are already in place. For example, the Active Directory may already have account lockout and password expiration policies.