Get started with popular use cases
Implementation examples
This chapter will show you how to secure your company and infrastructure with Acreto SASE.
This chapter will show you how to secure your company and infrastructure with Acreto SASE.
The shift to working from home and remote workforce has put never-before-seen stress on VPN solutions. The goal is to address the traditional bottlenecks of performance and upkeep of the hardware approach toward cloud-delivered security and connectivity. To accomplish this we will send all users to connect to benefit from the scale, availability, and security of Acreto SASE+Plus.
VPNs offer privacy but little else. Acreto SASE+ Plus replaces traditional VPNs with an offering that integrates connectivity, privacy, and security. It is globally available yet provides a local experience that is elegant, simple, and sustainable.
In this use case, we would like to show you how easy is to shift your company to be able to work from home. With help of small articles we will guide you thru this process with a “step-by-step” procedure for:
In this use case, we would like to show you how easy is to shift your company to be able to work from home. With help of small articles we will guide you thru this process with a “step-by-step” procedure for:
The first goal to achieve is to import users to Acreto so that they can start working inside the ecosystem. We need to create the Ecosystem, connect Identity Provider, and onboard users with their devices - all steps have been described below.
To complete this procedure you should:
In the context of our use case, we will use Microsoft Azure Active Directory with 10 Users and a sample Ecosystem.
To import and onboard Users:
We already imported and secured our users - they able to connect to the Ecosystem. To meet the assumptions of the “Work from Anywhere” idea, it is necessary to provide users with access to the data center and internal services. For this purpose, we will connect the data center with the Ecosystem.
To complete this procedure you should:
For maximum flexibility Acreto offers three options to connect your datacenters and applications
This checklist includes information to connect Acreto to your internal Datacenter for private application access
Acreto Virtual Gateway method behind datacenter Firewall:
This checklist includes information to connect Acreto to your internal Datacenter using the existing firewall/VPN gateway
Using the checklist above connect Acreto your Datacenters to Acreto via IPSEC (vGateway or existing HW). The below procedure shows how to do it using the Raspberry device as a vGateway.
It’s not the only method to reach the goal, other possibilities have been described here. As an alternative, you may use your existing branch office equipment such as your existing Cisco router, or existing firewall.
The following procedure is a summary of Linux - Automatic IPsec Configuration article - which you may want to ready if you want to know more.
To connect your Datacenter/Branch Office to Acreto:
192.168.200.1/24
1. Local Networks: - your local network addresses that should be routed through this gatewayTo simplify testing, add IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow testing connectivity from the gateway through Acreto using ping, traceroute, and similar tools.
To successfully test your connectivity, you also need to create a security policy that will allow traffic to go through your device.
To proceed with this step you should have at last one Gateway configured as vGateway in your Ecosystem. From the left menu choose Objects > Gateways to display the list of existing gateways.
To generate an image with the configuration for Raspberry Pi you need to:
To proceed with this step you need to have an image file generated by Acreto or URL to the image for your vGateway.
To install the image we need to proceed with flashing the SD card.
Download the write_image.sh script
Click on the button and save the script in your home directory:
Get write_image.shor open the terminal and download the script using the command:
wget https://kb.acreto.net/reference-material/downloads/write_image.shTake your SD card from your Raspberry device
Put your SD card into your computer
Use write_image.sh script to write the image to SD card
if you have an image file downloaded locally:
./write_image.sh image-file.zip /dev/sdbif you have want to use the URL of an image directly::
./write_image.sh https://aws1-vgateway-images.s3.amazonaws.com/vgateway-raspberry-pi4.s.nAH2xOL8HyJIK1g8v4HEsNCt.img.zip /dev/sdbwhere /dev/sdb is the location of your SD card
Once finished, plug the SD card into your device and log in as:
acretoacreto.ioChange your password after the first login
Test the network connectivity
IPsec status showing the tunnel status
ipsec statusallTraceroute to check if the traffic goes through Acreto Ecosystem
traceroute 8.8.8.8More information about checking the connectivity can be found under Connectivity Check article where a dedicated tool is available.
For better cotroll you may connect Acreto to your internal Syslog Collector - all logs from event will be transferred there.
Based on the logs, you can extend the network rules, for example, those that block excessive network traffic (Youtube) or the application that are time eaters (Facebook)
To complete this procedure you should:
In this article, you’ll learn how to integrate DUO with an Acreto Ecosystem.
This process involves the following steps:
To integrate Acreto with DUO, you will need the following:
A DUO integration allows your Acreto Ecosystem to utilize the user credentials stored in your LDAP Identity Provider to connect to the Ecosystem using Acreto TLS Client with additional Multi-Factor Authentication made by the DUO application, phone, or SMS.
It uses DUO Authentication Proxy as the “Man in the middle” that additionally secures the login procedure for Acreto users.
The solution uses an LDAP connection from Acreto to DUO and from DUO to Identity Provider LDAP.
To configure your DUO to work with Acreto, please:




To install the Duo Authentication Proxy, you will need the host with Windows. The procedure for the Linux host may be found on the official DUO documentation.
https://dl.duosecurity.com/duoauthproxy-latest.exeC:\Program Files\Duo Security Authentication Proxy\conf\authproxy.cfgad_client section to configure LDAP/ActiveDirectory connection:
search_dn=DC=example,DC=comldap_server_auto section to configure DUO Authentication Proxy as the LDAP server:
ad_client
ad_client - Use Active Directory for primary authentication. Make sure you have a [ad_client] section configured. Neither [radius_client] nor [duo_only_client] are valid for use with [ldap_server_auto]. This parameter is optional if you only have one “ad_client” section. If you have multiple, each “server” section should specify which “client” to use.
[ad_client]
host=ldap.jumpcloud.com
service_account_username=xxxxxx
service_account_password=xxxxxxxxxxxx
search_dn=ou=Users,o=xxxxxxxxxxxxxxxx,dc=jumpcloud,dc=com
auth_type=plain
bind_dn=uid=search,ou=Users,o=xxxxxxxxxxxxxxxx,dc=jumpcloud,dc=com
[ldap_server_auto]
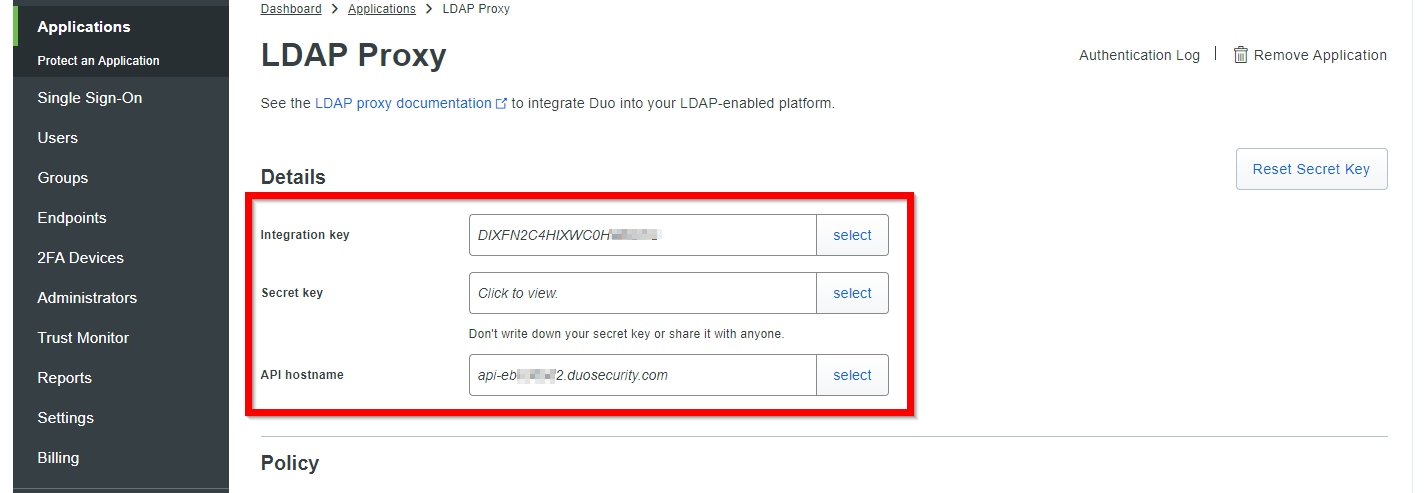
ikey=DIxxxxxxxxxxxxxxxxxx
skey=xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
api_host=api-xxxxxx.duosecurity.com
failmode=safe
client=ad_client
port=1812 ; comment if you want to use the default LDAP port
failmode=safe
ssl_key_path=ldap_server.key
ssl_cert_path=ldap_server.pem/opt/duoauthproxy/bin/authproxyctl start/opt/duoauthproxy/bin/authproxyctl statusConfigure Wedge to use DUO Authentication Proxy as the Identity Provider. If you want to know more about IdP, read this article.
Thanks to Acreto and Multi-Factor Authentication, the administrator can force users to use multi-factor logging, increasing the organization’s security level.
This document describes how to configure Reflection NAT. Reflection NAT is a mechanism that allows you to secure any Internet Site using the Acreto Platform. Technically, to achieve this, we need to:
You can find more about this technique on the Internet, for example at http://www.nycnetworkers.com/real-world/nat-reflectionnat-loopbacknat-hairpinning/
In this example, we will protect the website http://kb.acreto.net, hosted on a server with IP 52.216.94.210. In order to achieve this, we will do the following:
In your DNS server, create or change DNS record for secure.acreto.io to point to 104.193.146.129, for example:
secure IN A 104.193.146.129Note: In the future, we will use CNAME records instead of A records.
Note 2: For testing, you can put this name into your host’s file (/etc/hosts on Linux/Mac) instead:
104.193.146.129 secure.acreto.ioOn ACRETO web server, configure the firewall to allow traffic to TCP ports 80 and 443 from ACRETO Public IP, in our example - 104.193.146.129
Go to http://104.193.146.129 - you should see the ACRETO website