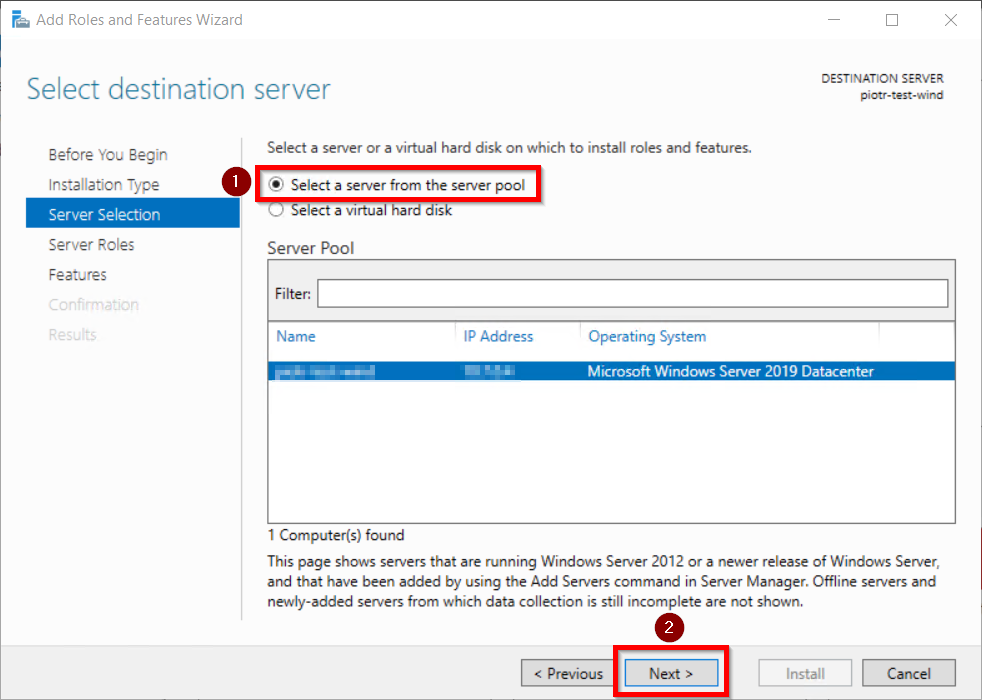
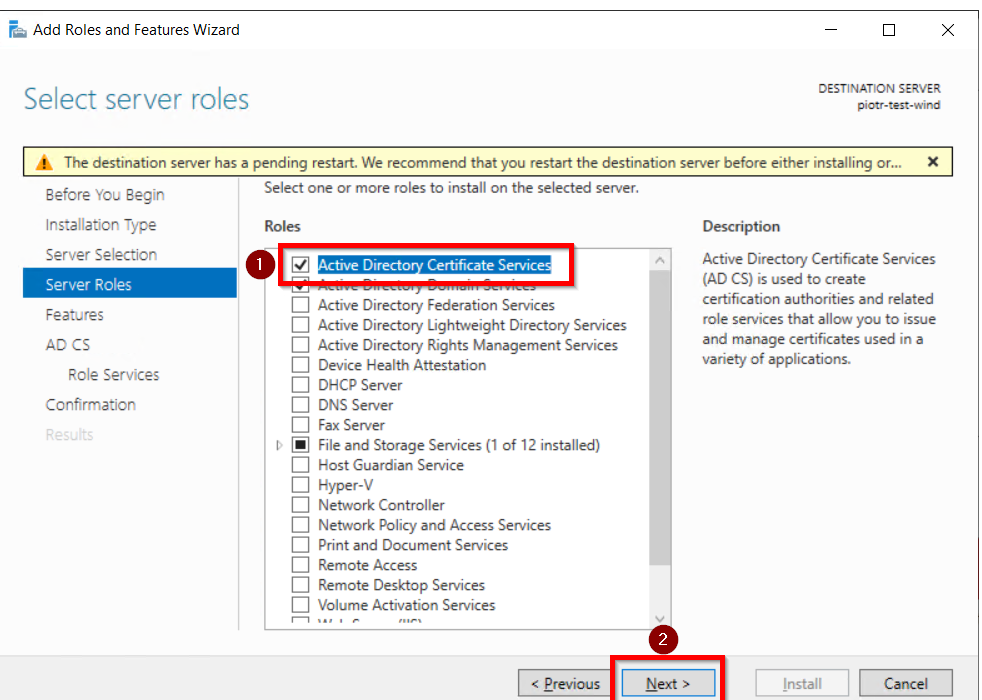
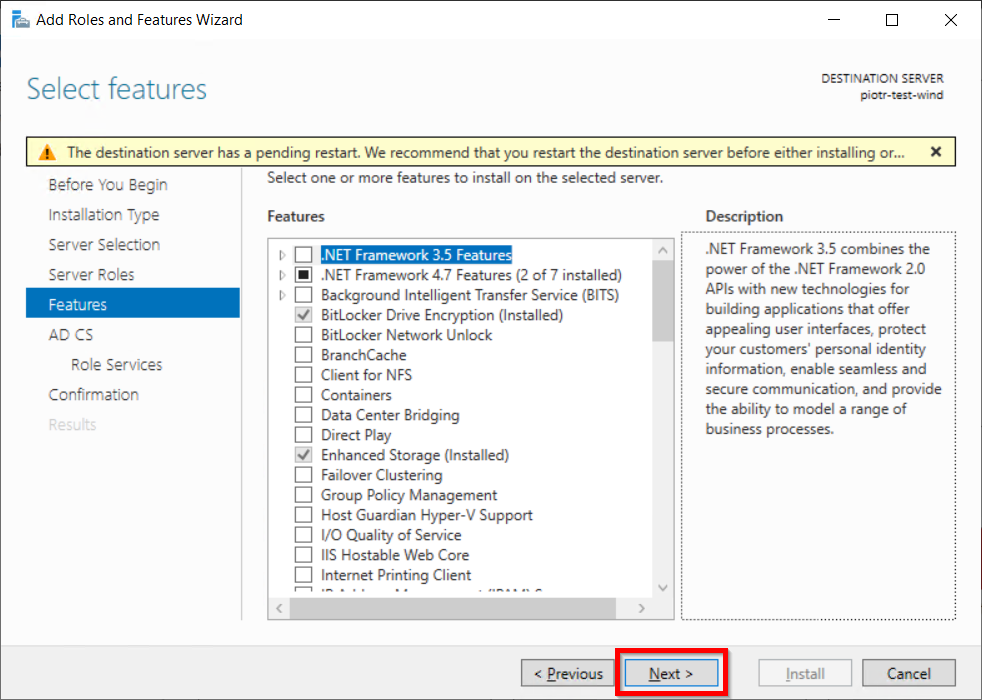
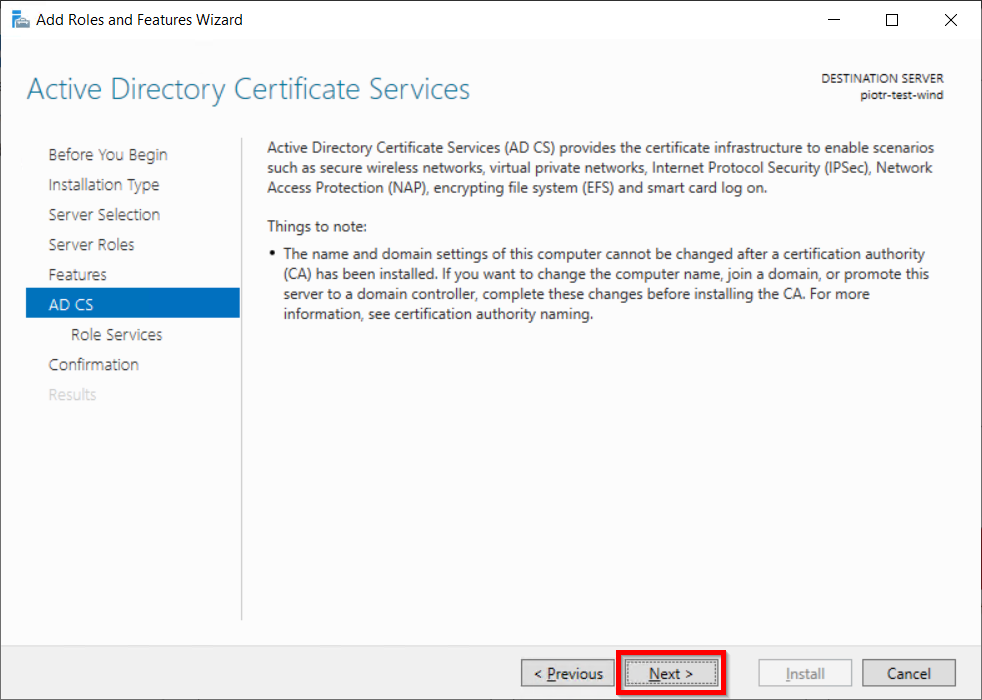
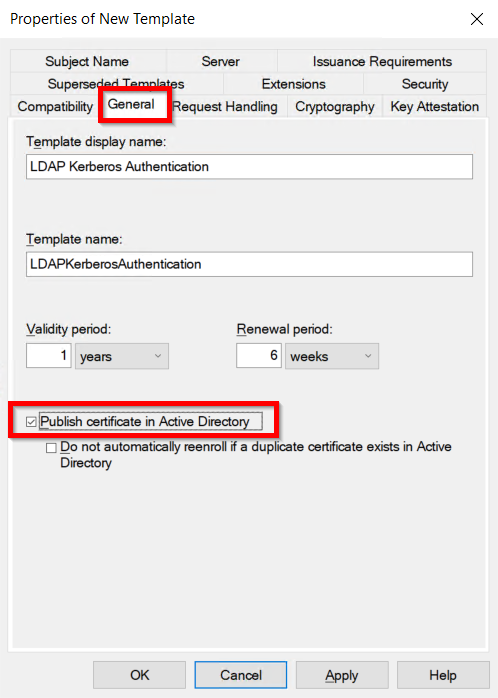
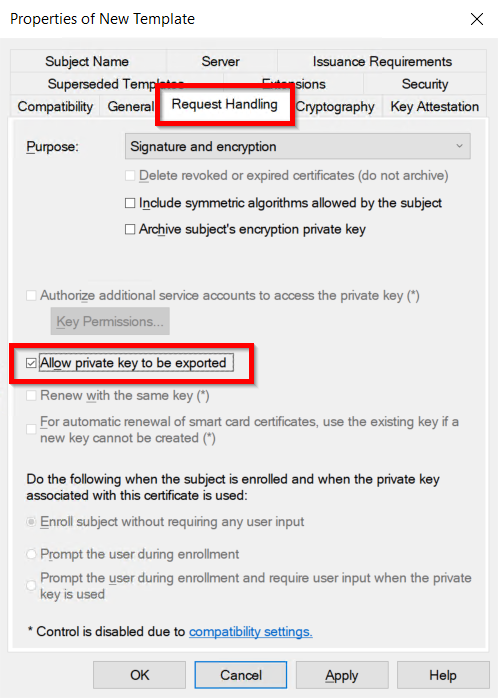
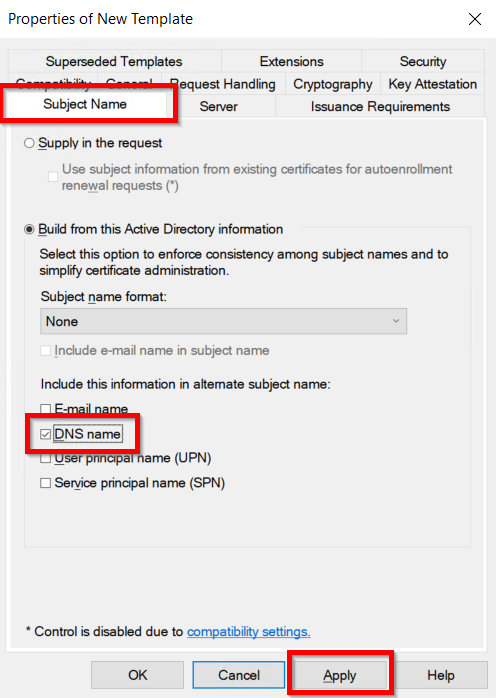
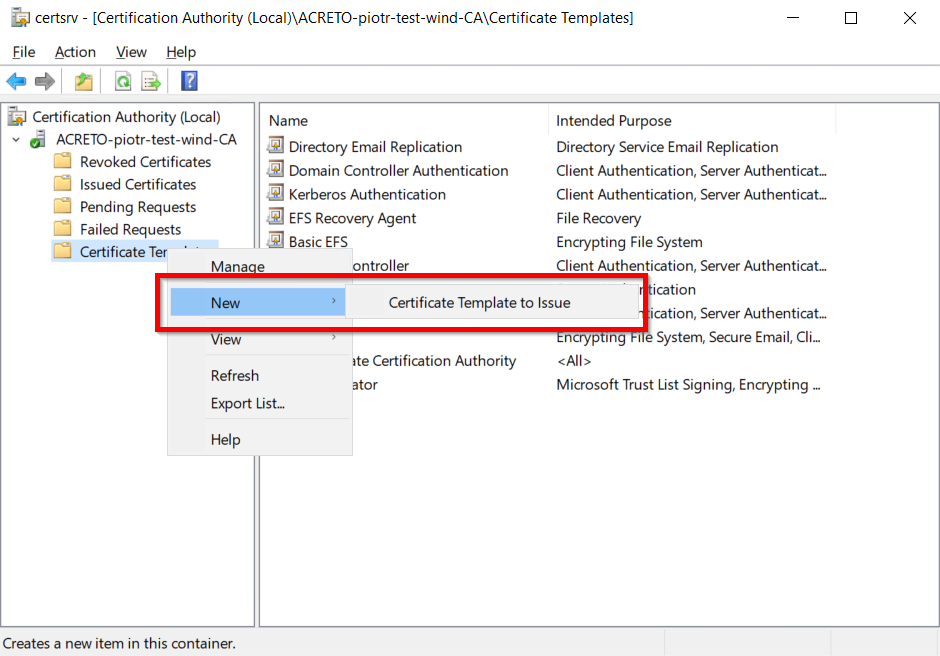
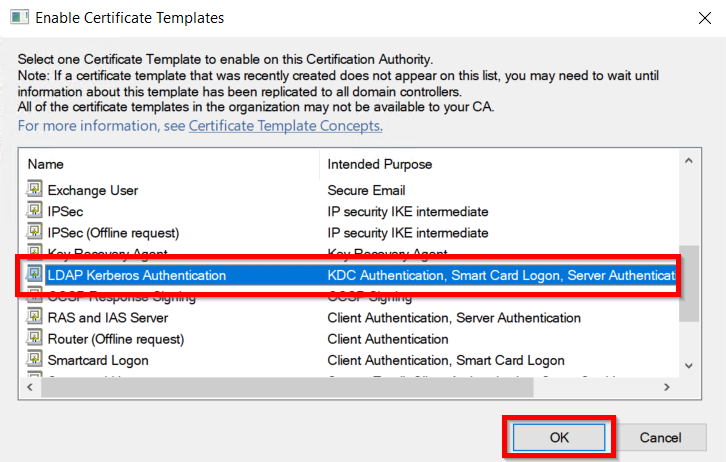
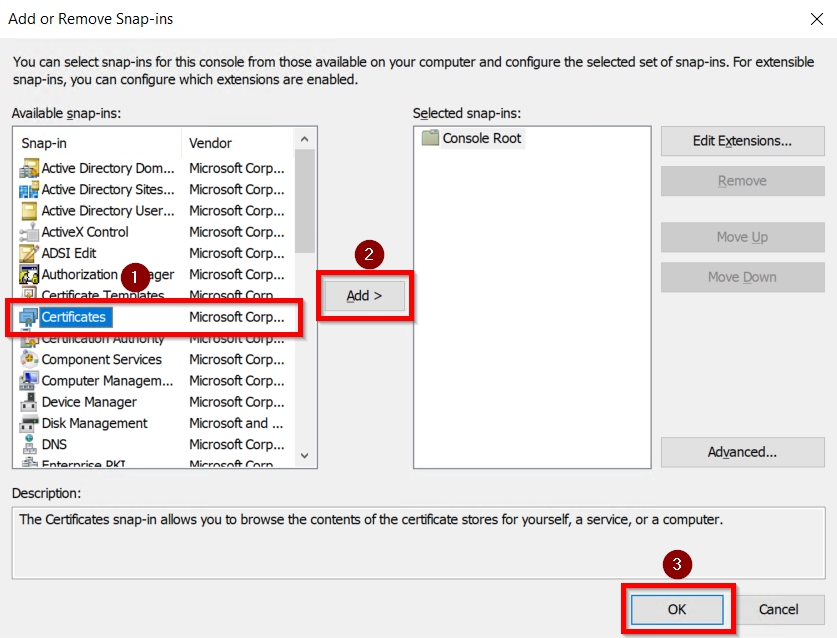
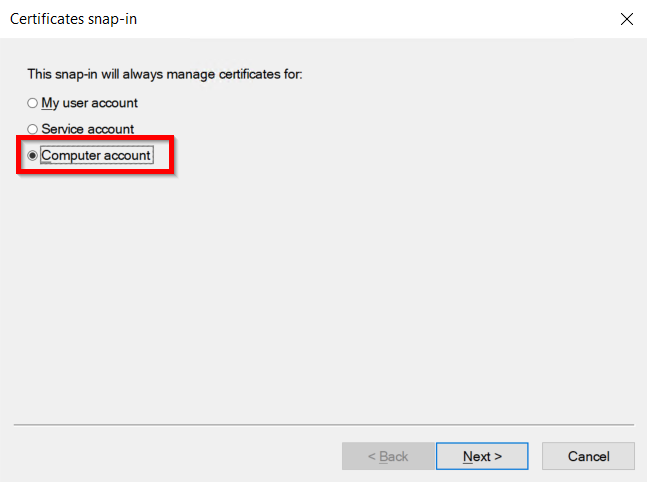
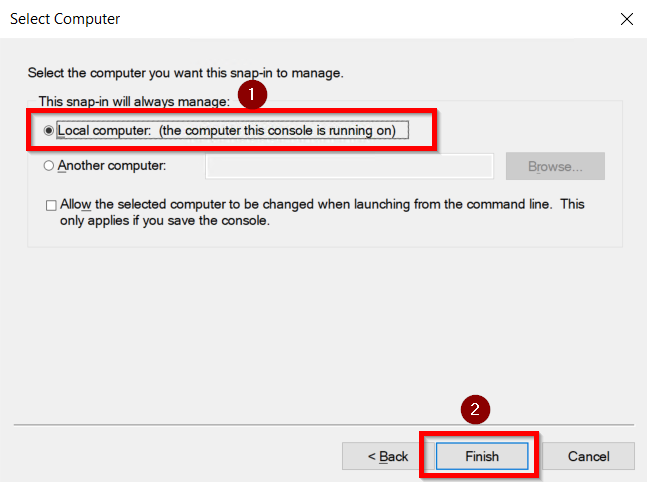
Identity Providers Overview
Overview
In this article, you will learn how Acreto integrates with Identity Providers (like Active Directory or OKTA) to authenticate your users.
Definitions
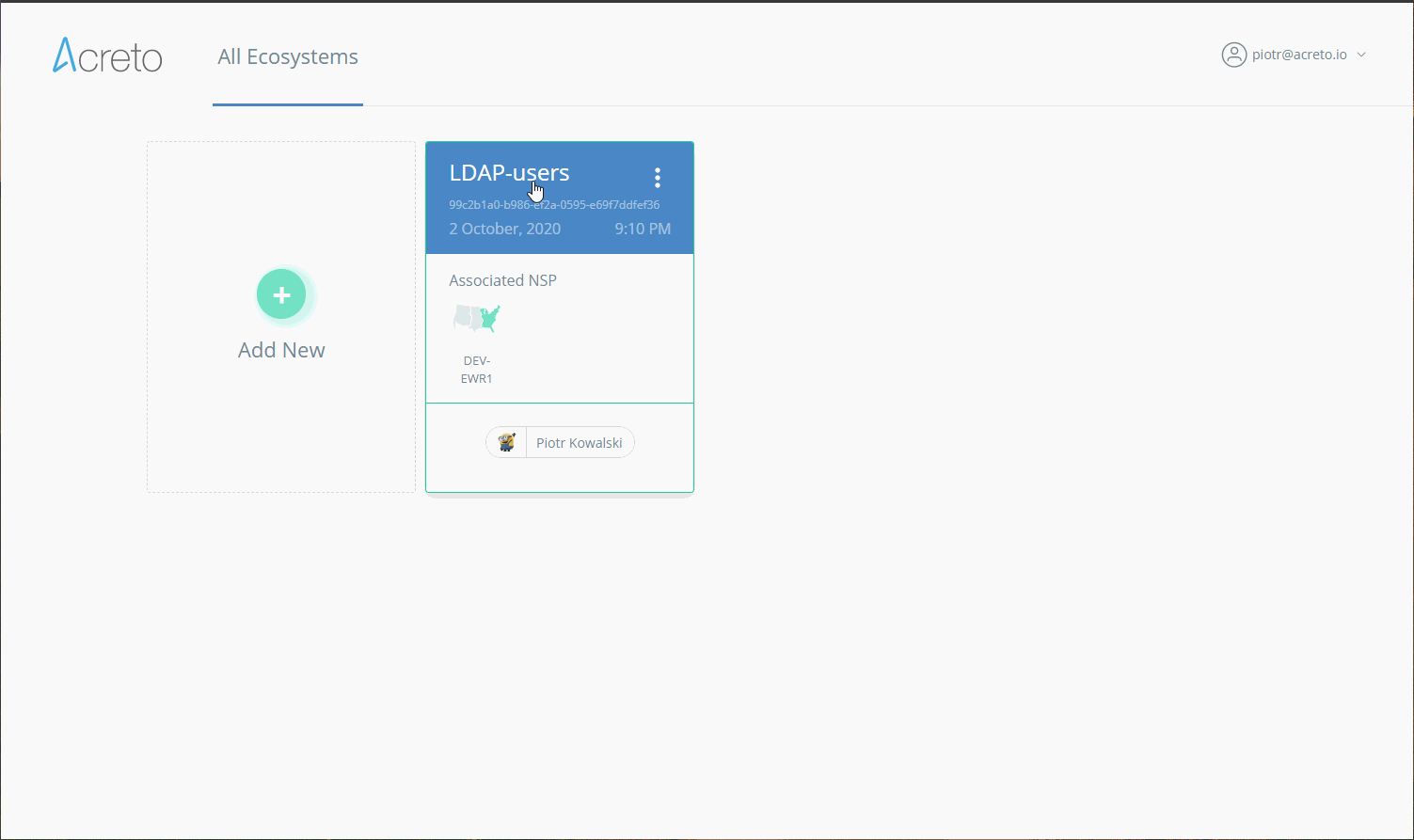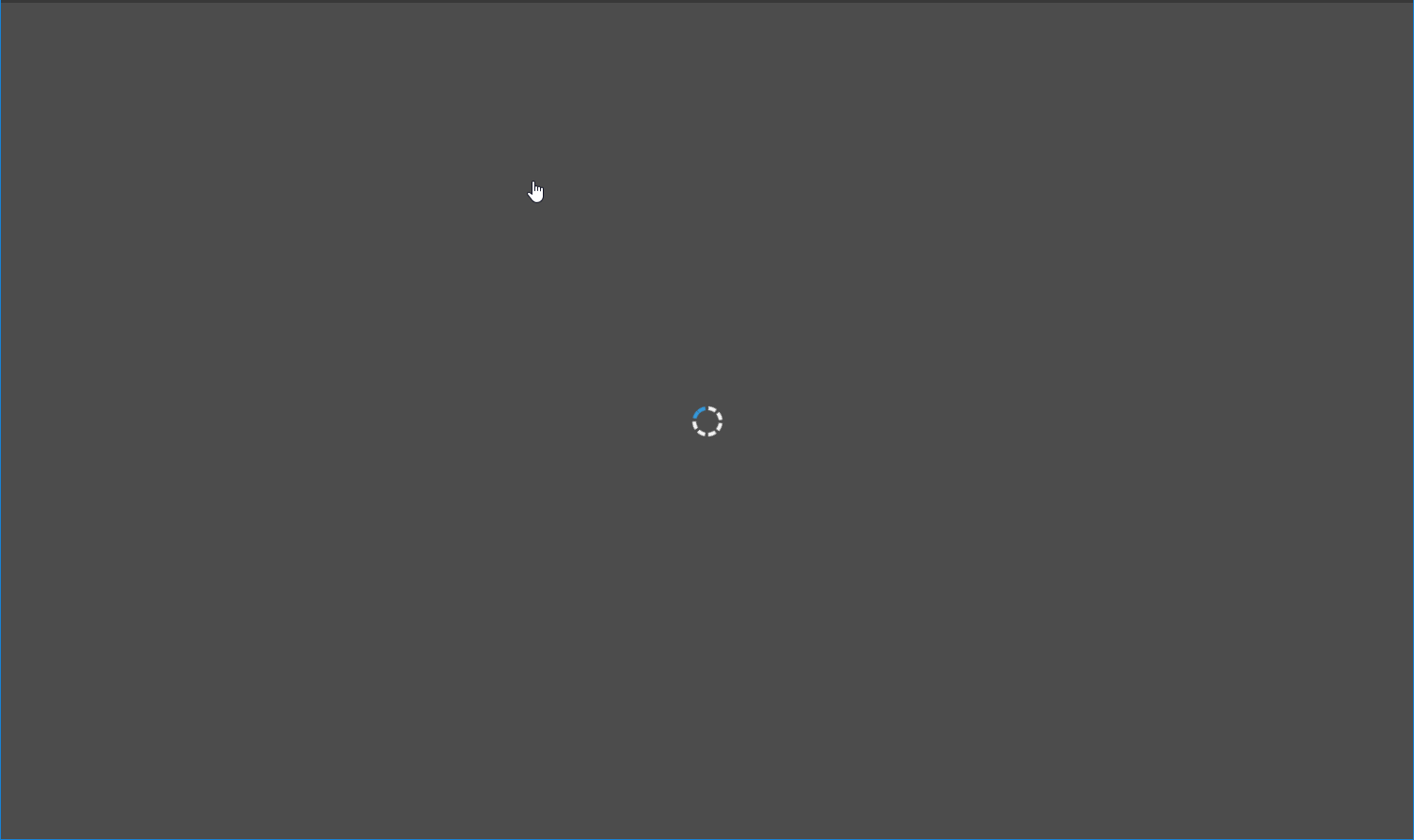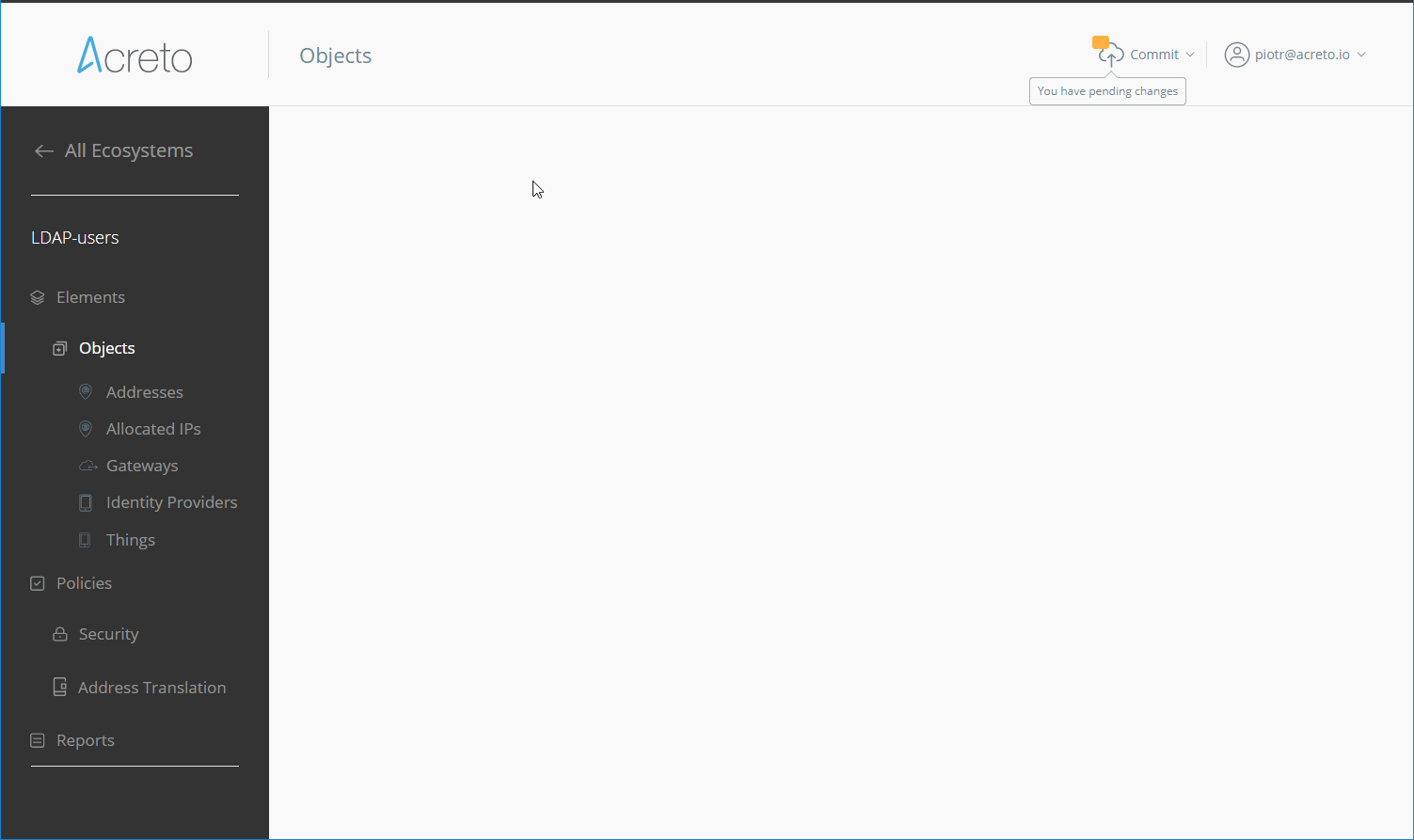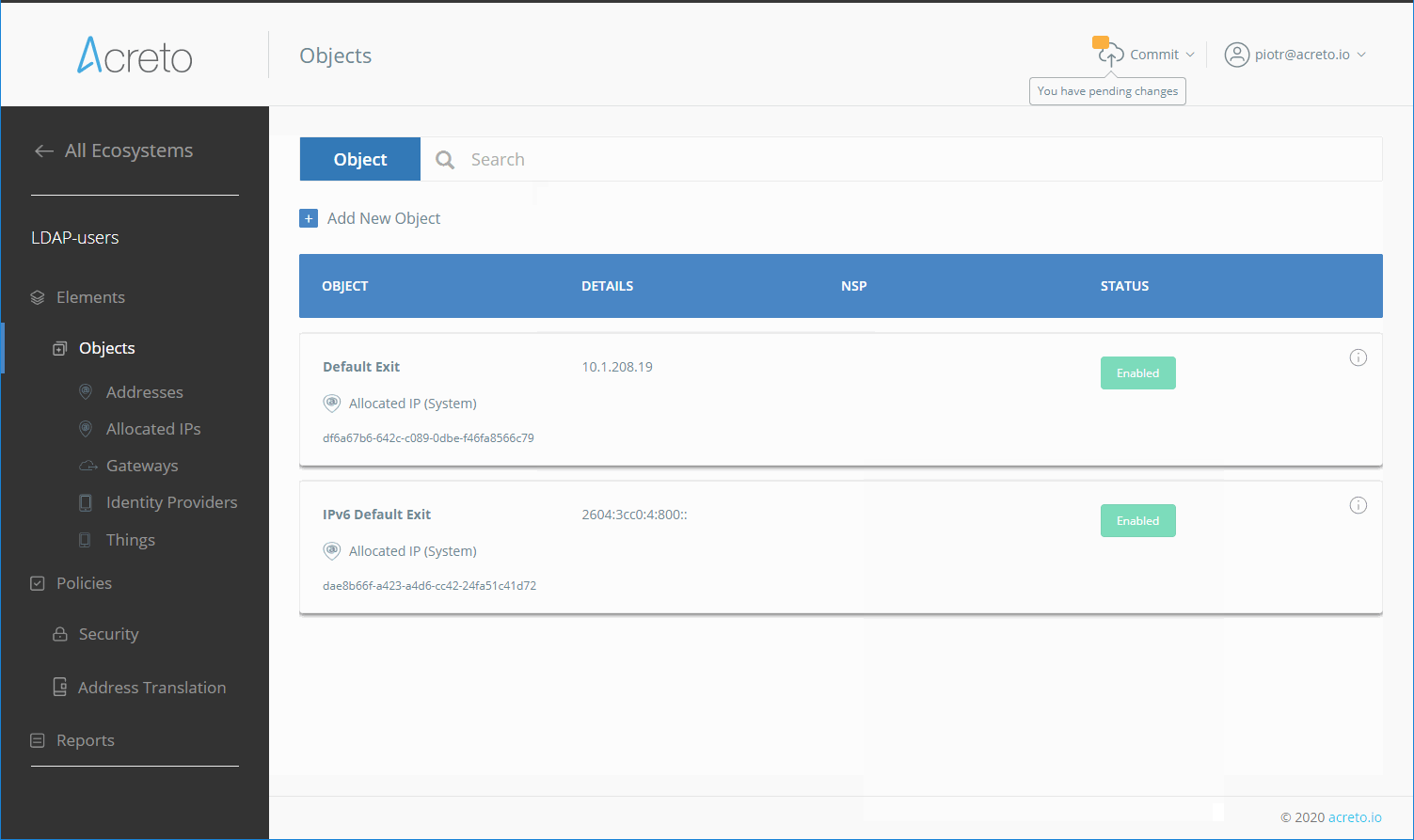
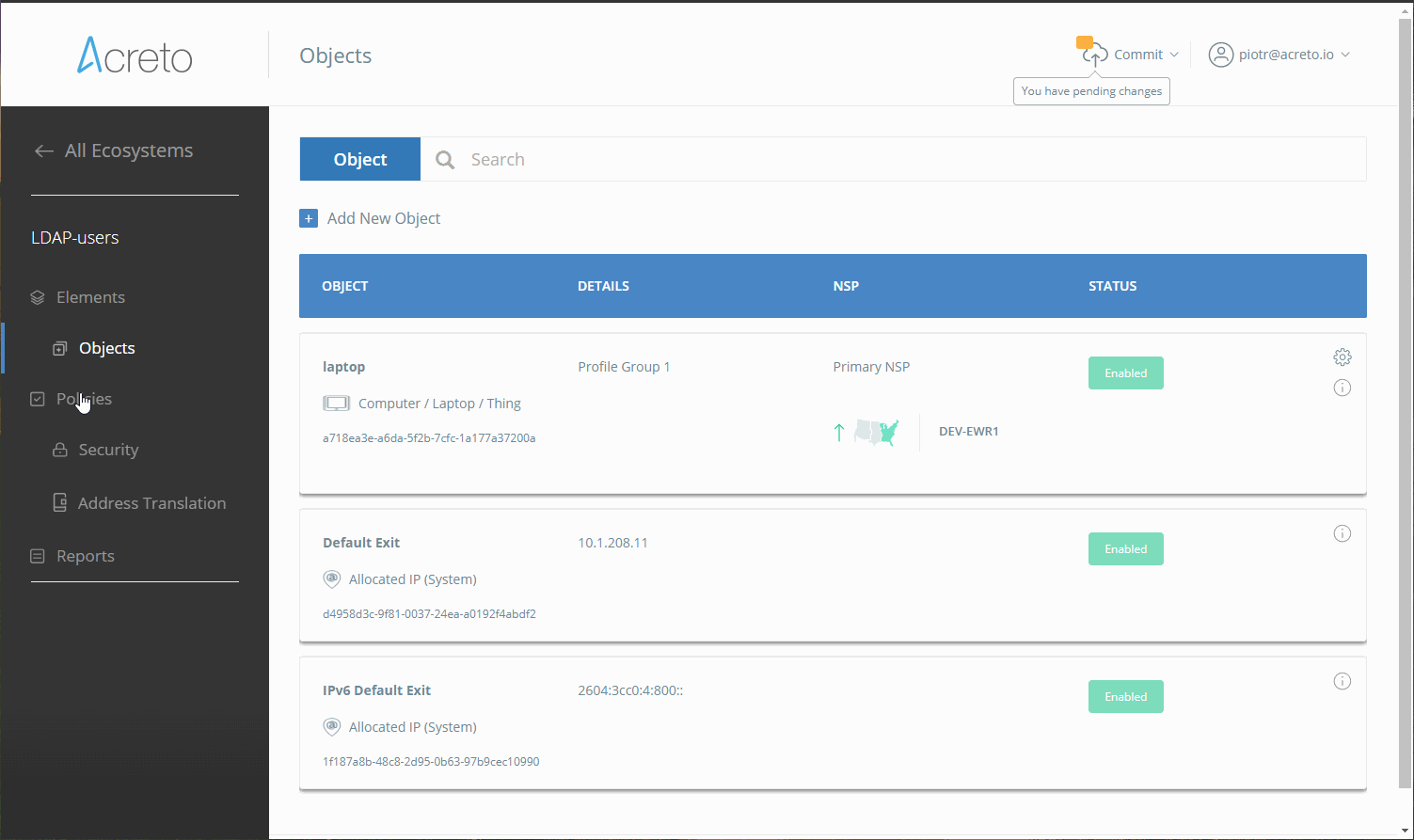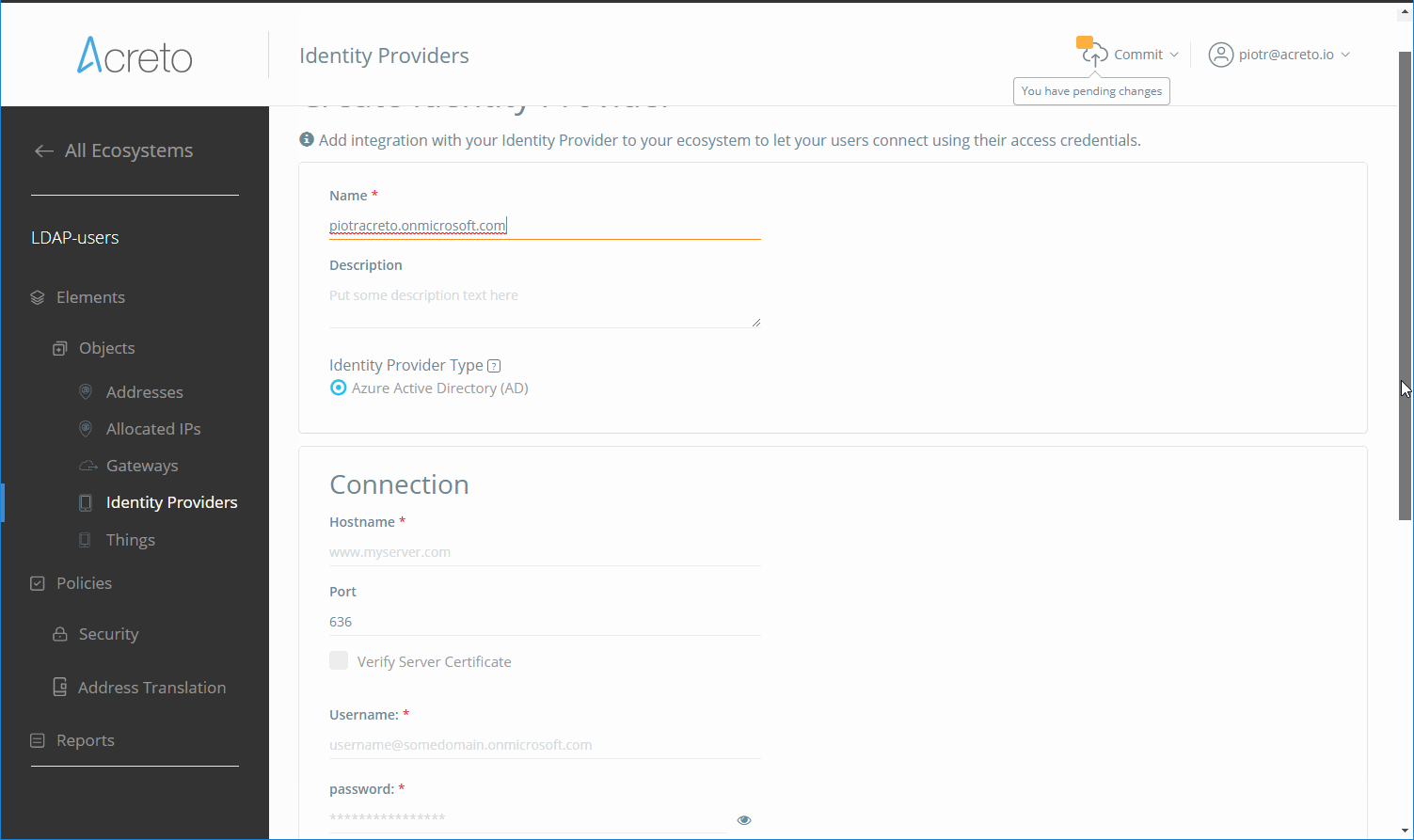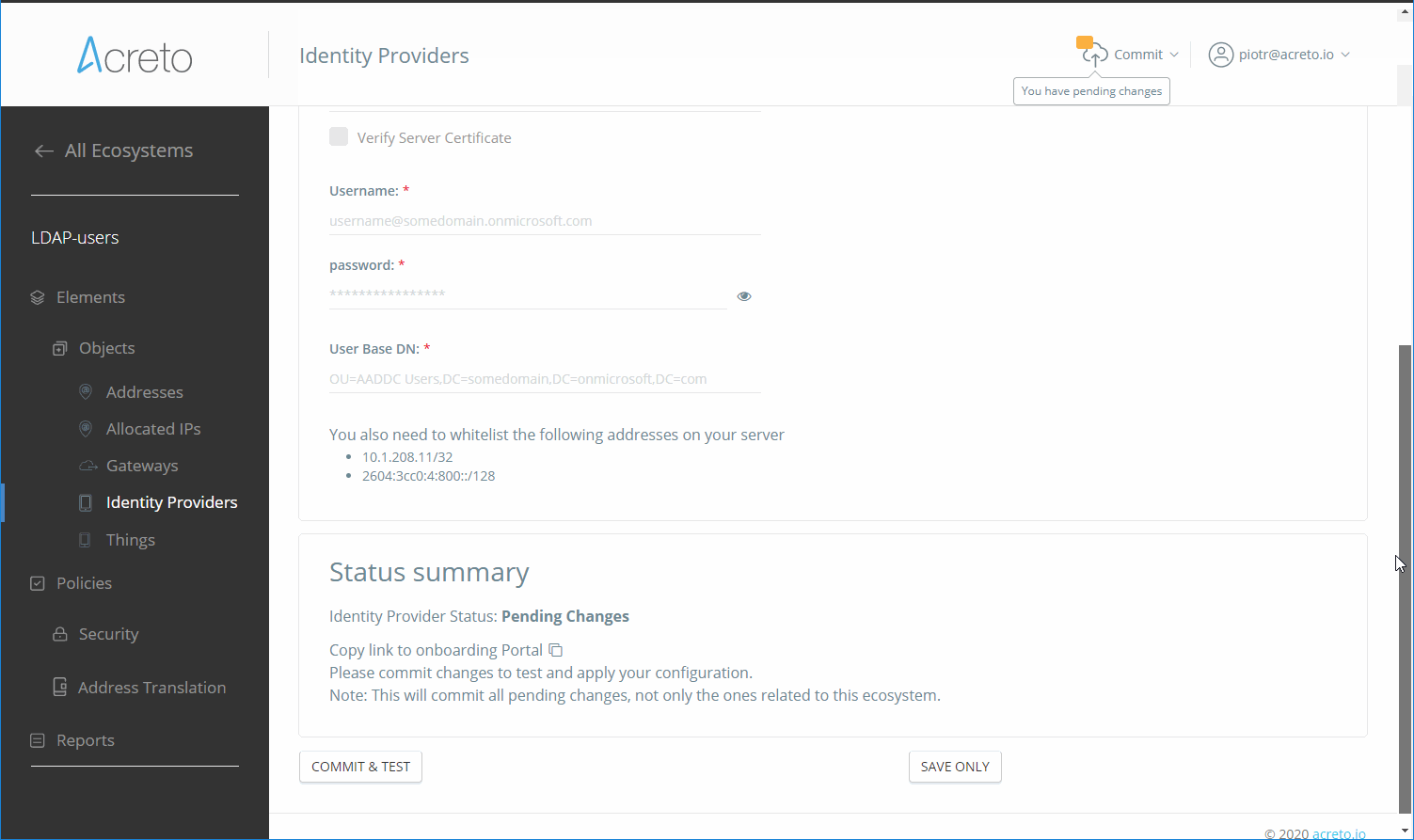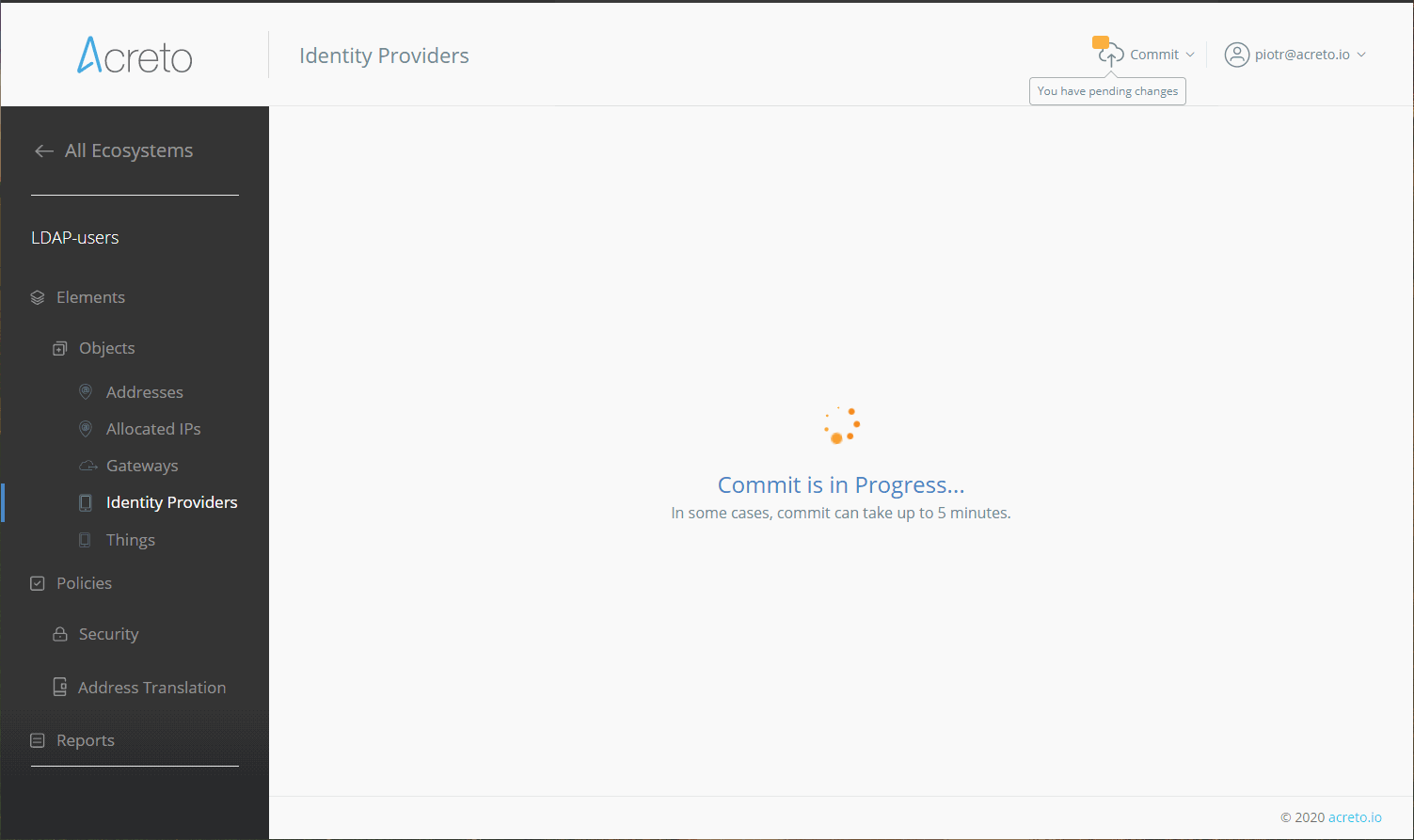
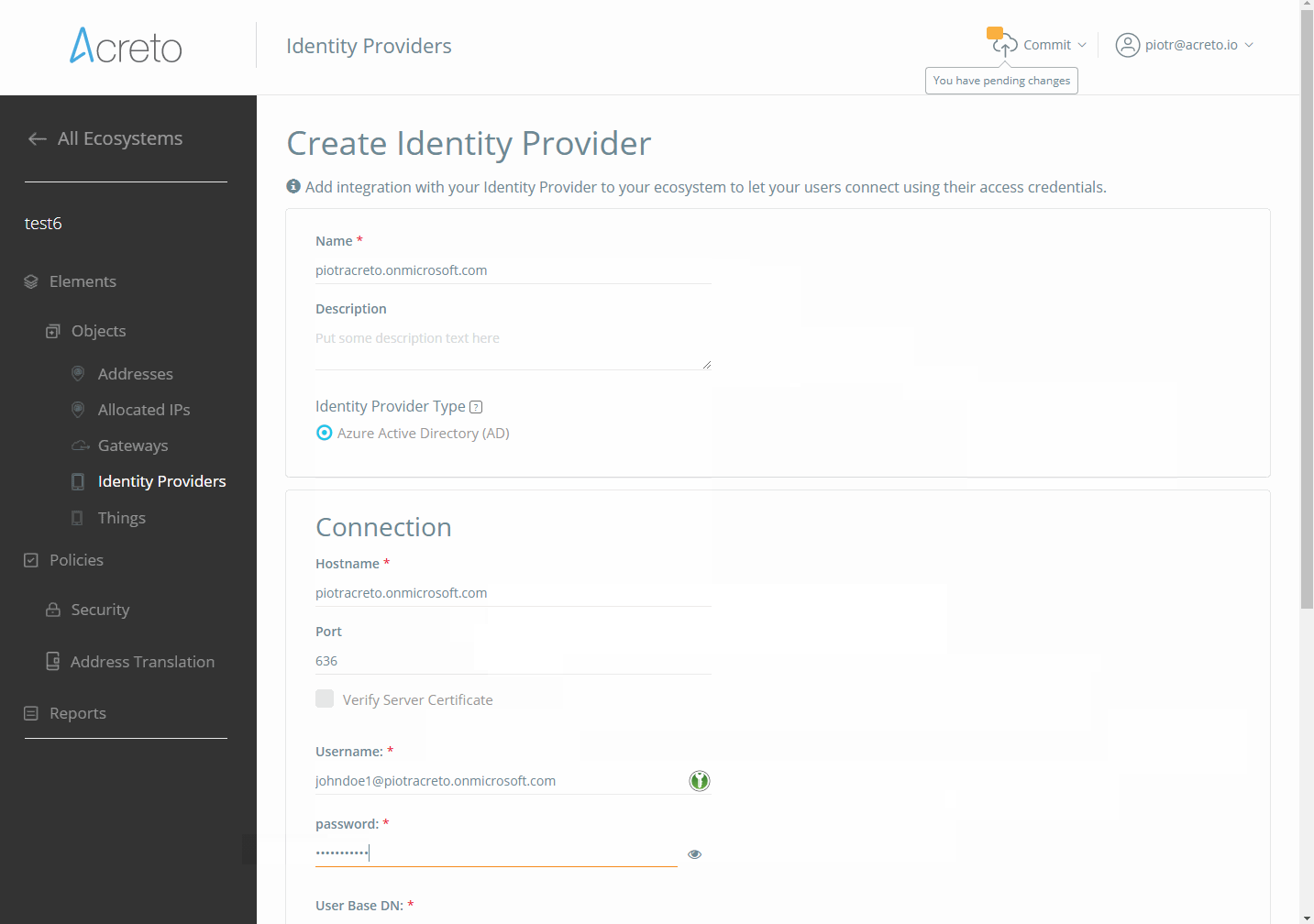
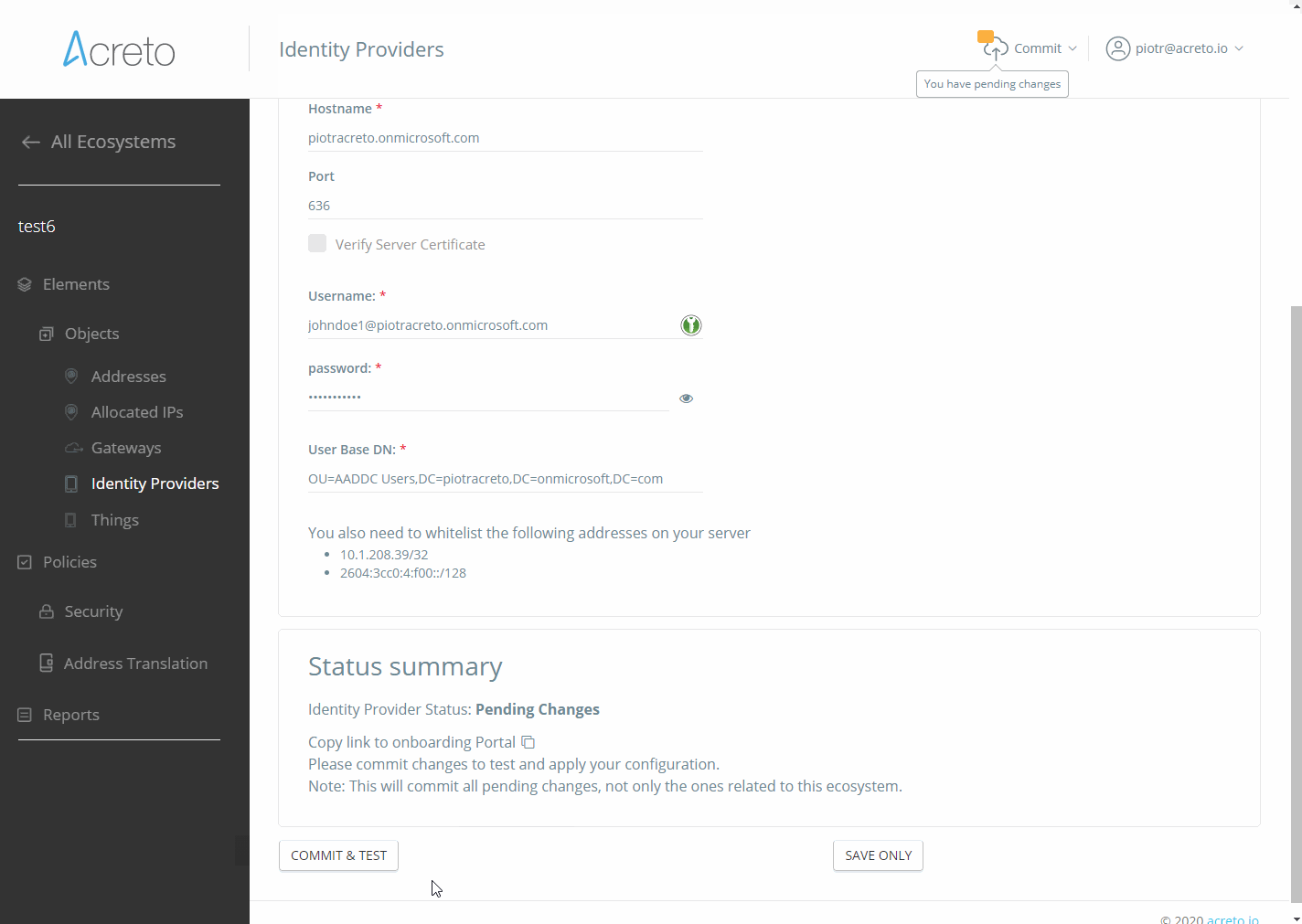
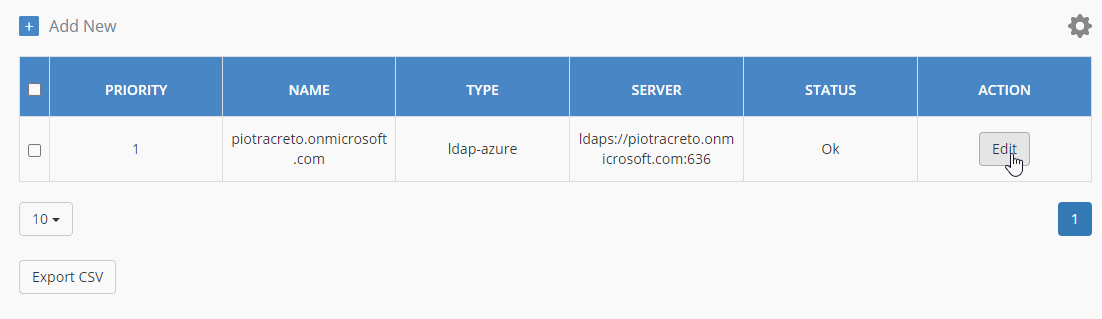
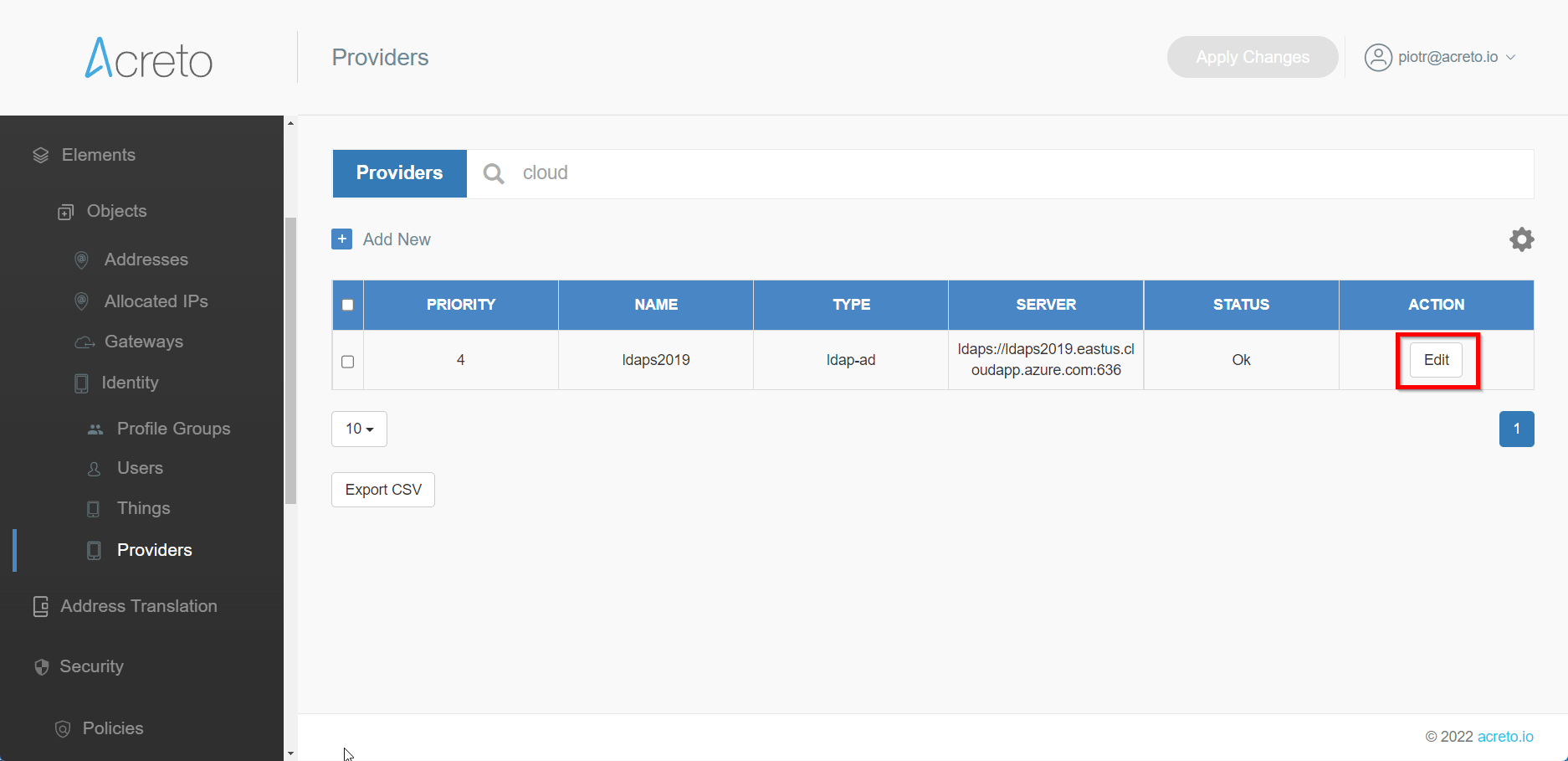
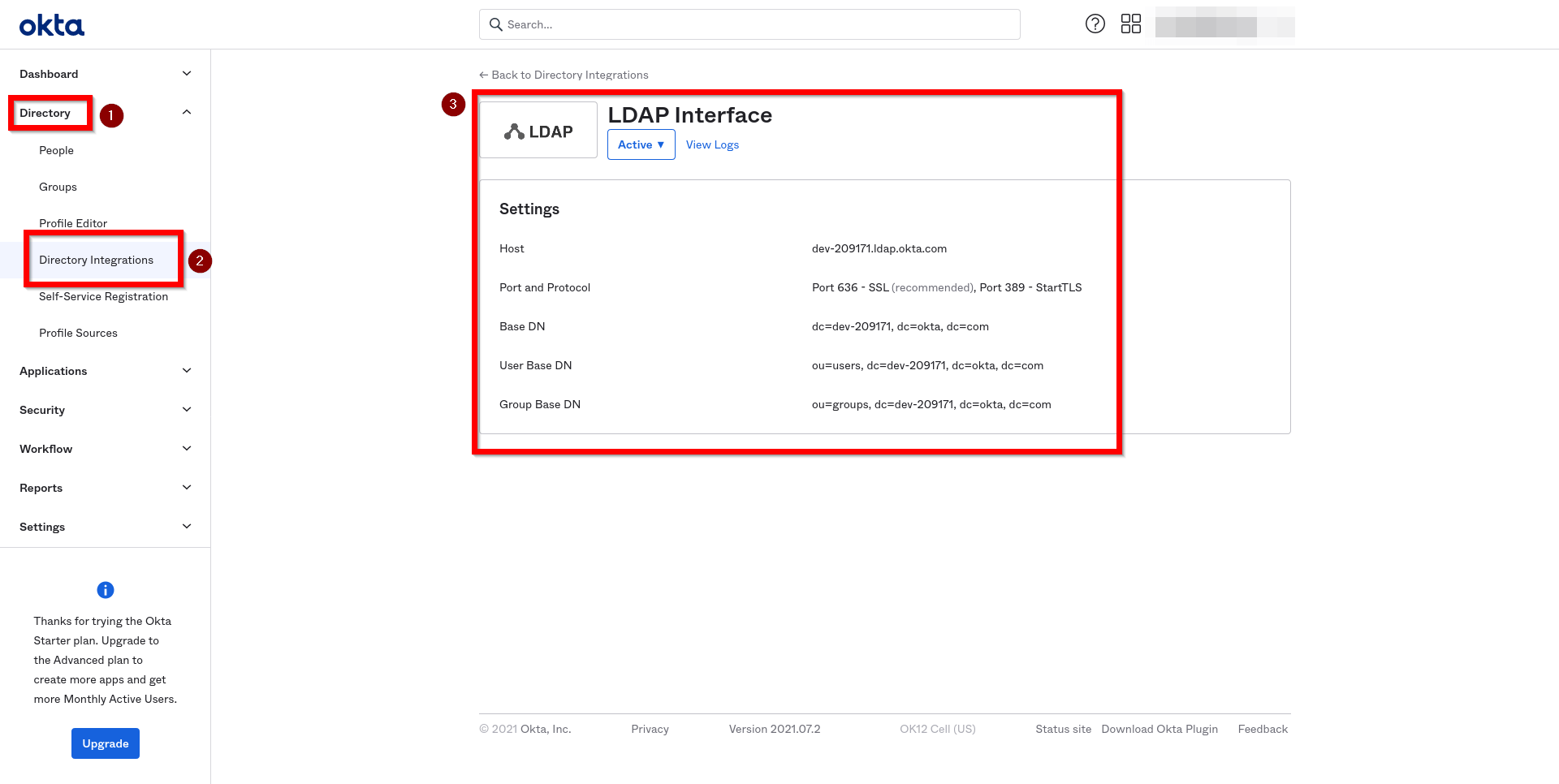
Identity Provider on the Acreto Platform
An Identity Provider is a service that verifies and stores user identity information. Some examples of Identity Providers are:
- Microsoft Active Directory
- Okta
- OpenLDAP
2-Factor Authentication
In addition to an Identity Provider, you might also want to configure a 2-Factor Authentication (2FA) provider.
Using a 2FA provider will require your users to provide more than one type of credential when authenticating; for example, a password (something users know) and a code displayed via mobile phone (something users own).
Benefits of Identity Provider Integration
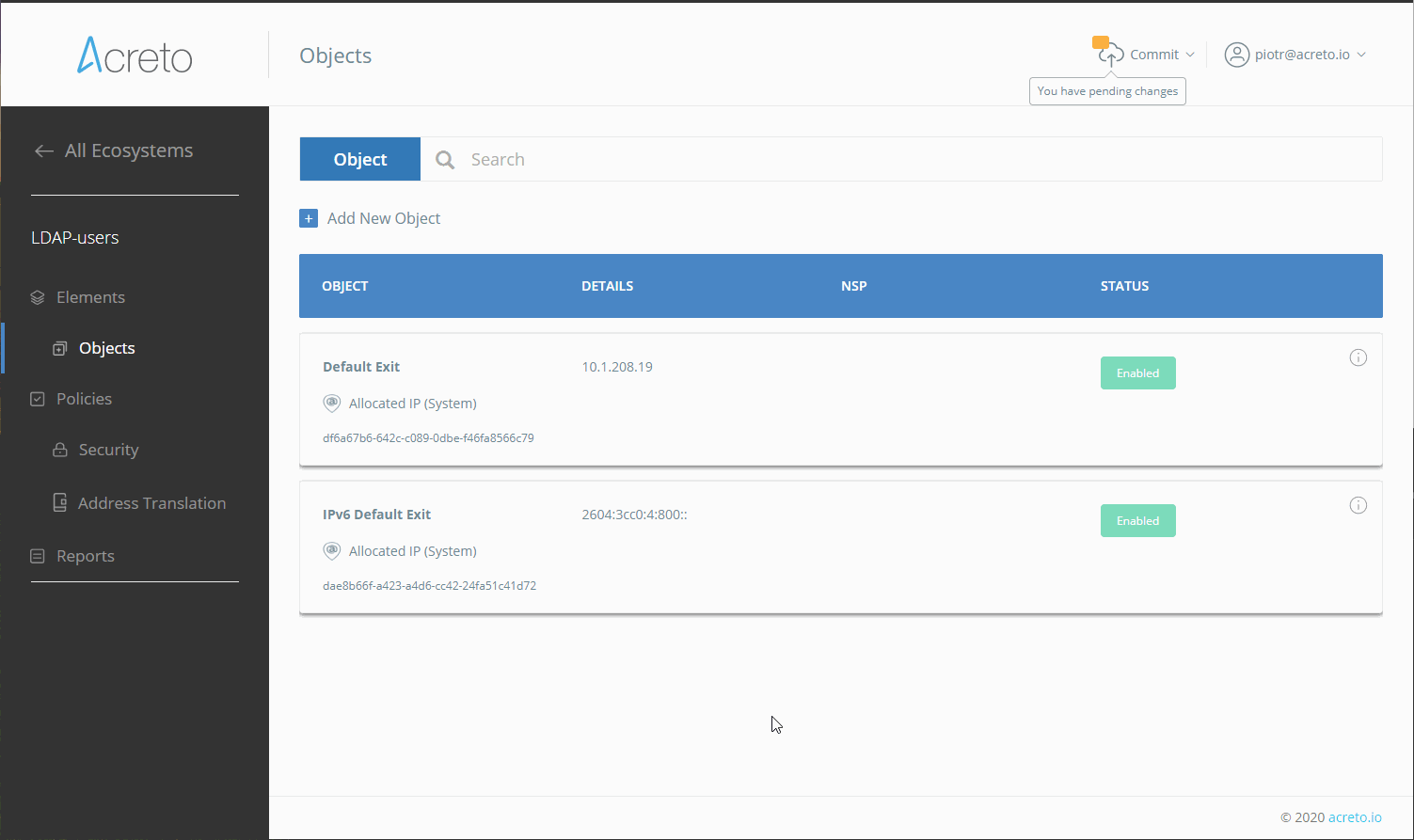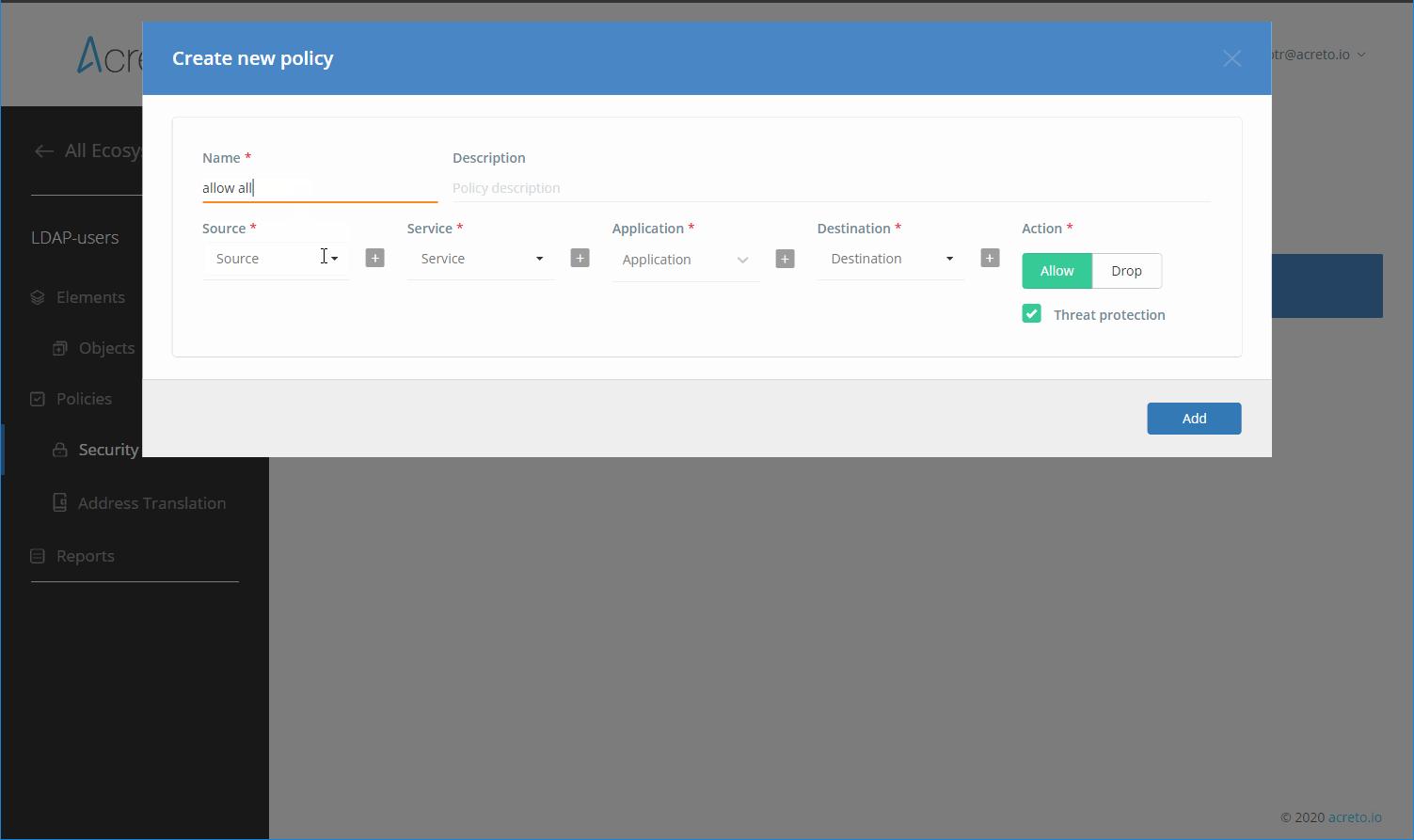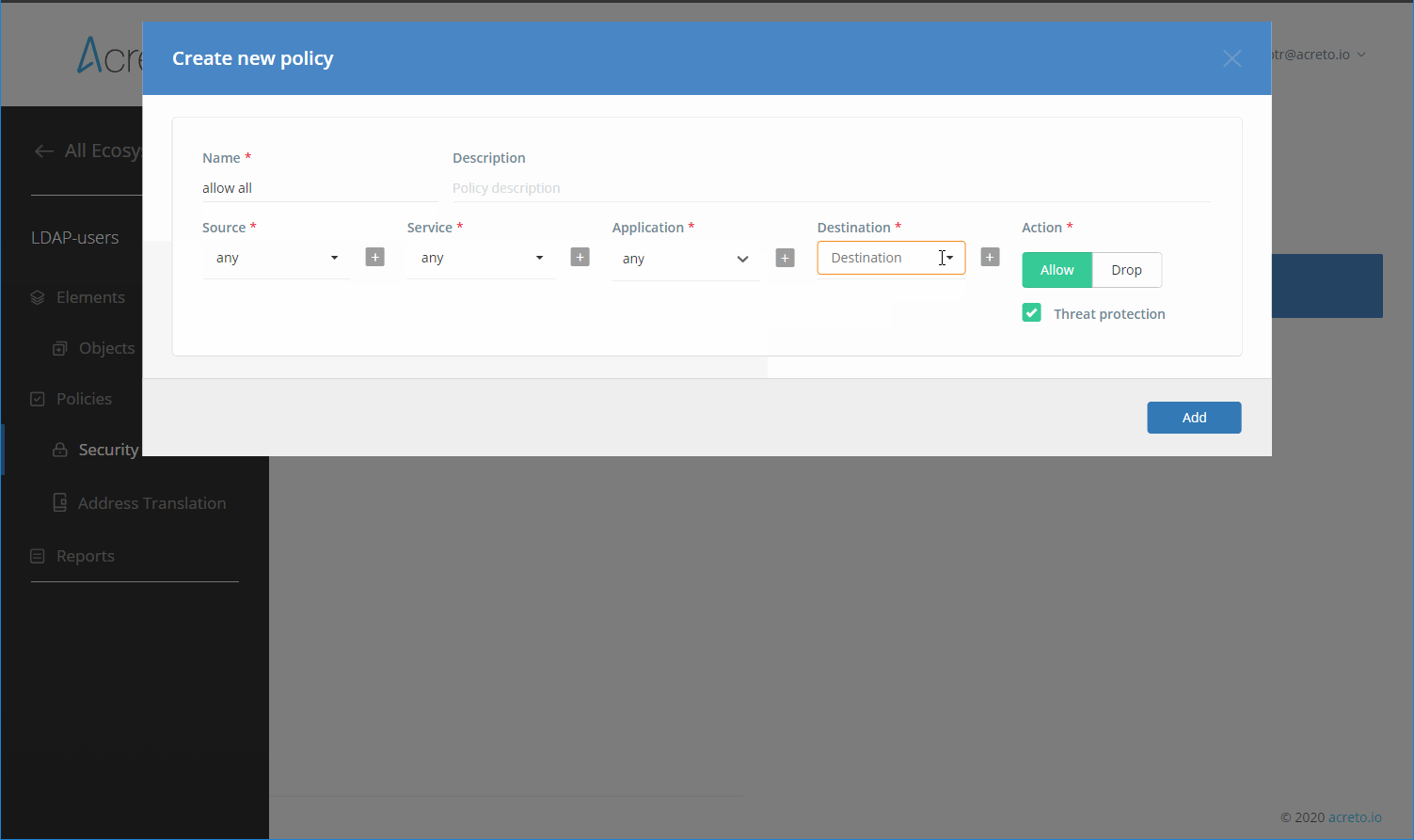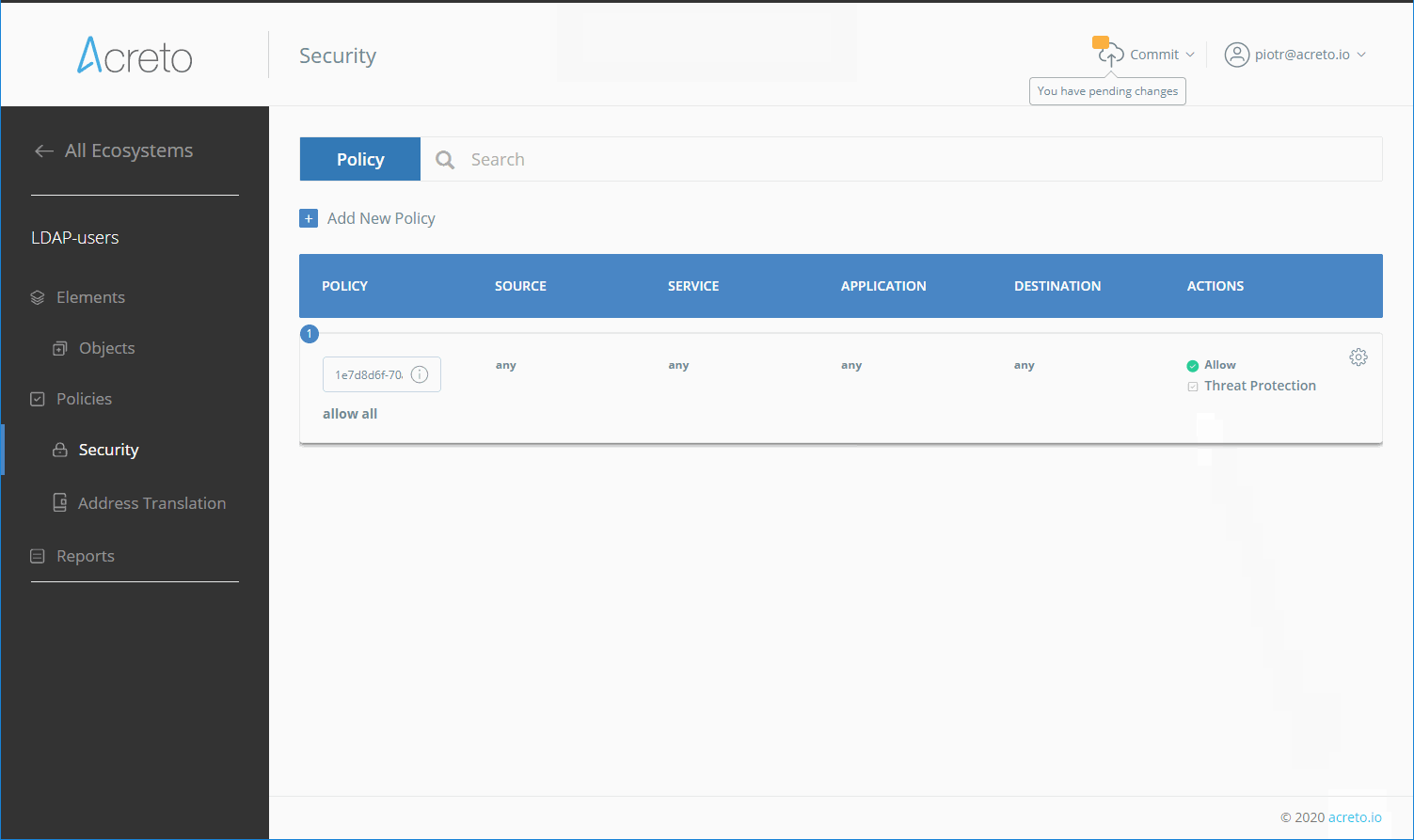
Integrating an Identity Provider will allow you to:
- Keep credentials under control with centralized management.
- Avoid data duplication by storing user data in one place only.
- Control user data processing to ensure compliance with personal data processing regulations, such as GDPR.
- Limit risks by managing access to your network based on rules and policies.
- Disable access of company resources for former partners or employees by removing or limiting access rights in a single place.
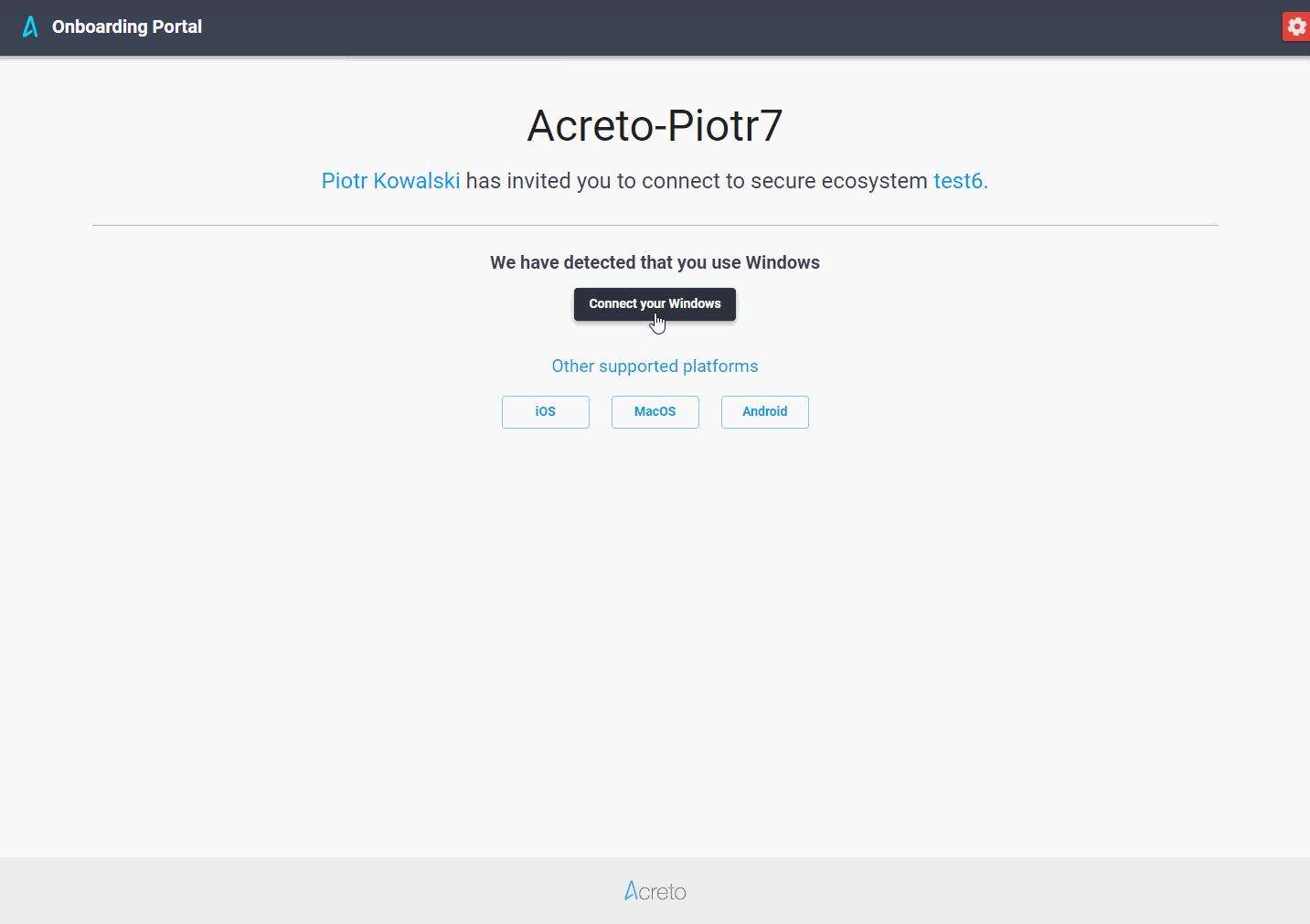
- Easily Onboard employees and organization members.
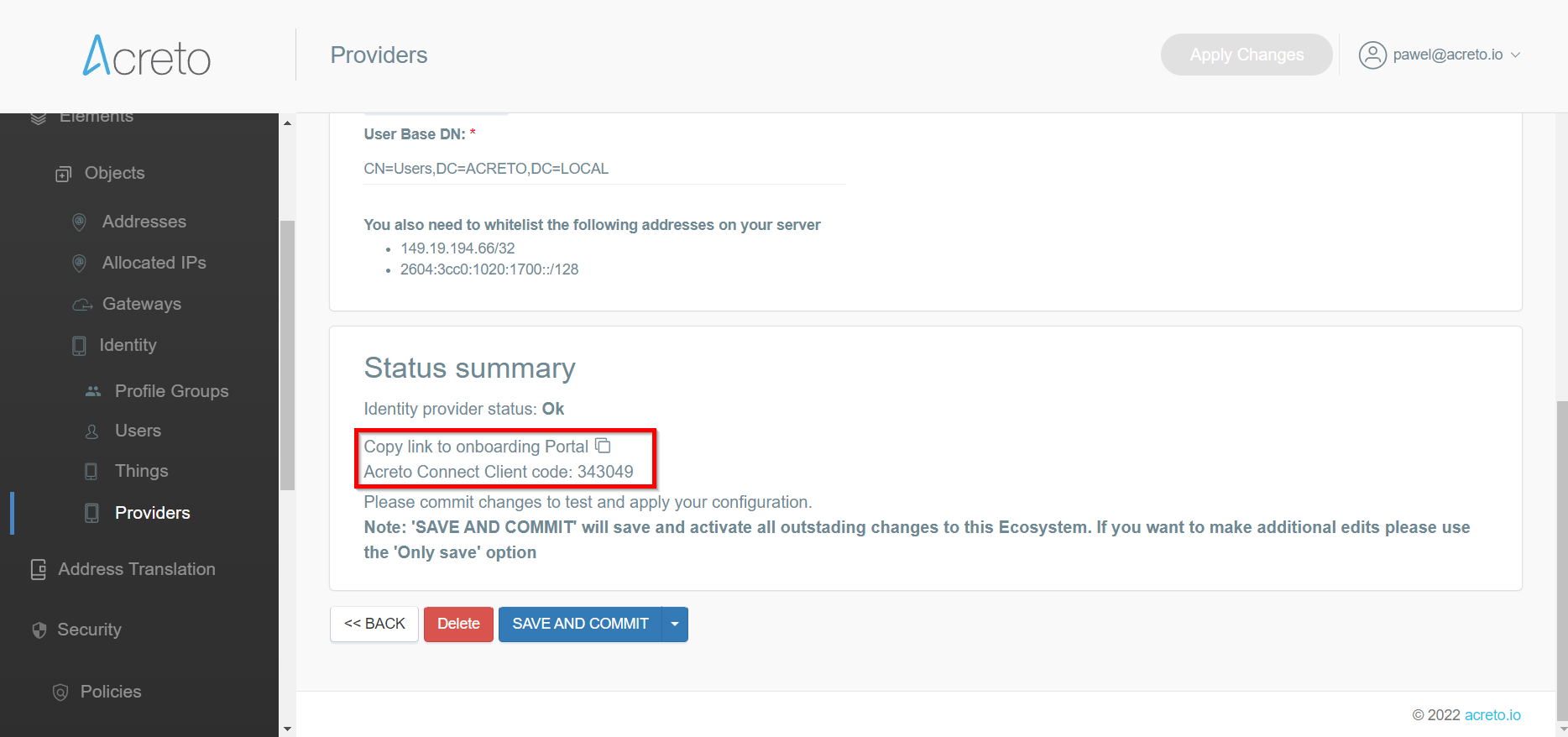
- Connect to the Acreto Ecosystem with the Identity Provider credentials.
How Acreto Uses Identity Providers
Acreto uses Identity Providers to deliver the following features for data plane users:
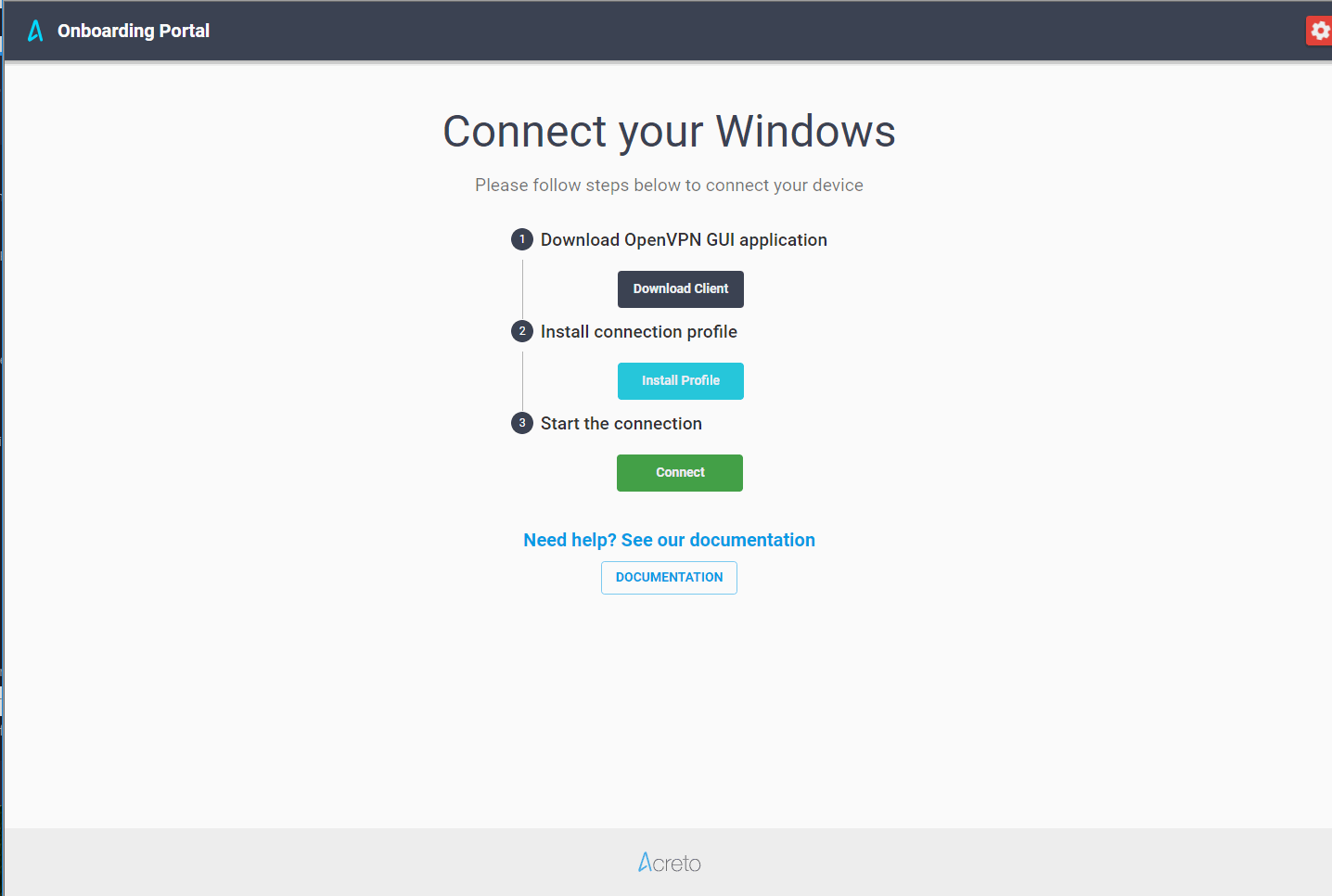
- Authentication of users connecting with Acreto TLS-Client and OpenVPN
- Ability to send invitation emails to data plane users
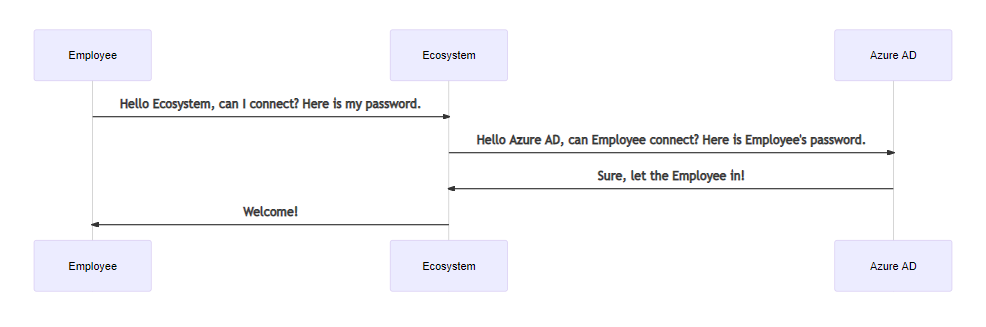
Acreto sends a request to the Identity Provider each time it needs to access user information. We only store some anonymized user identity data (for example, in Active Directory it is Guid). We might also cache some user data in memory on a short-term basis.
Identity Providers are only used to authenticate an Ecosystem’s data plane users or while connecting to an Ecosystem with OpenVPN or Acreto TLS-Client.