Subsections of IPsec Gateway
AWS EC2 - Automatic IPsec Configuration
Prerequisites
- Acreto Ecosystem
- Basic knowledge about AWS VPC.
- Basic knowledge about AWS EC2.
AWS - Create VPC
- Login to AWS console.
- follow the official guide and create a VPC.
- If your VPC already exists, make sure that there’s at last one subnet.
- Open setting for VPC (Networking & Content Delivery section) or use the search option to find VPC settings.
- Please note the network address of this subnet.
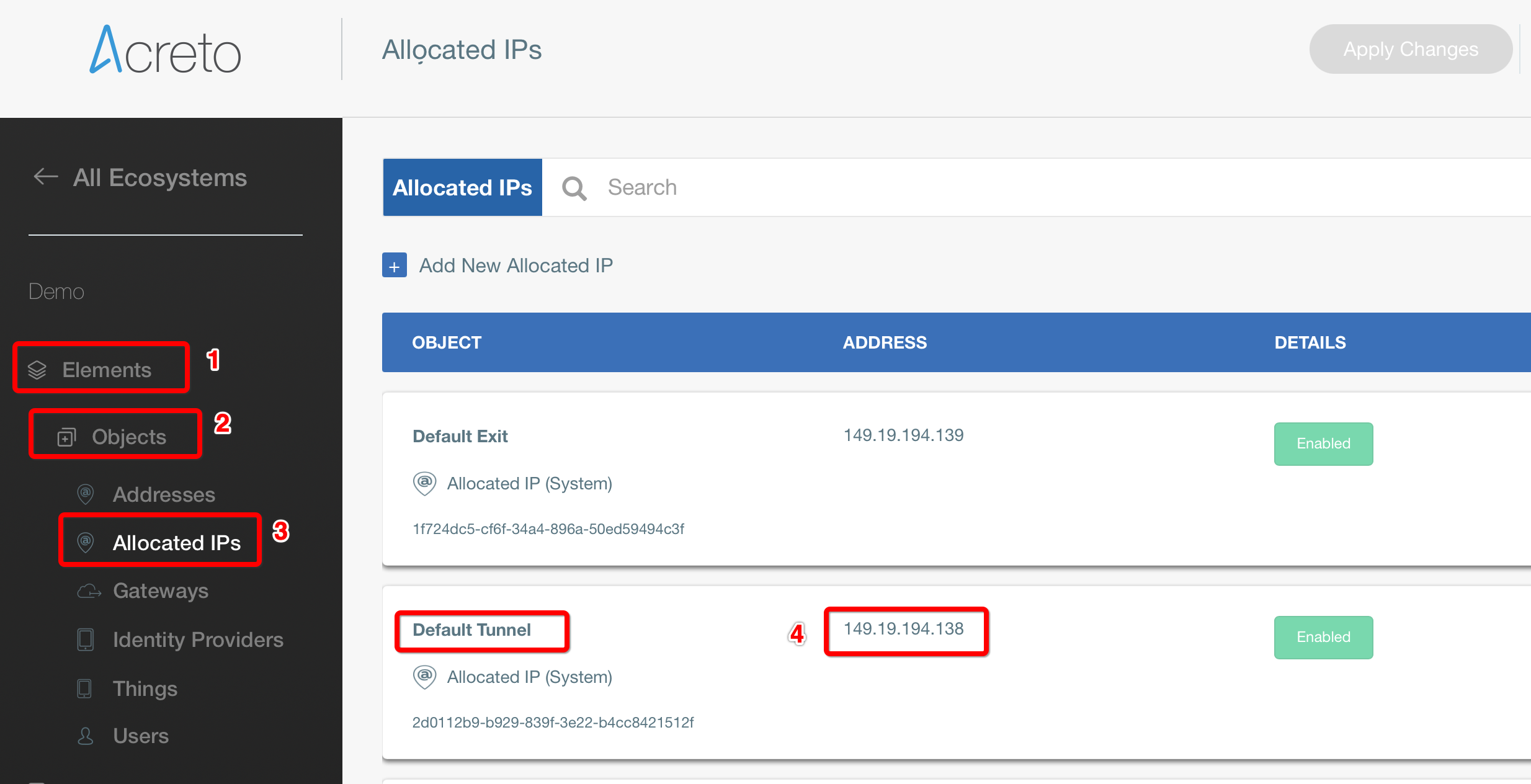
Acreto - Create Gateway
- Log in to Acreto Portal.
- Create new Gateway - IPSec type - follow this article.
- When configuring new Gateway add network(s) - same as VPC subnet in Local networks area.
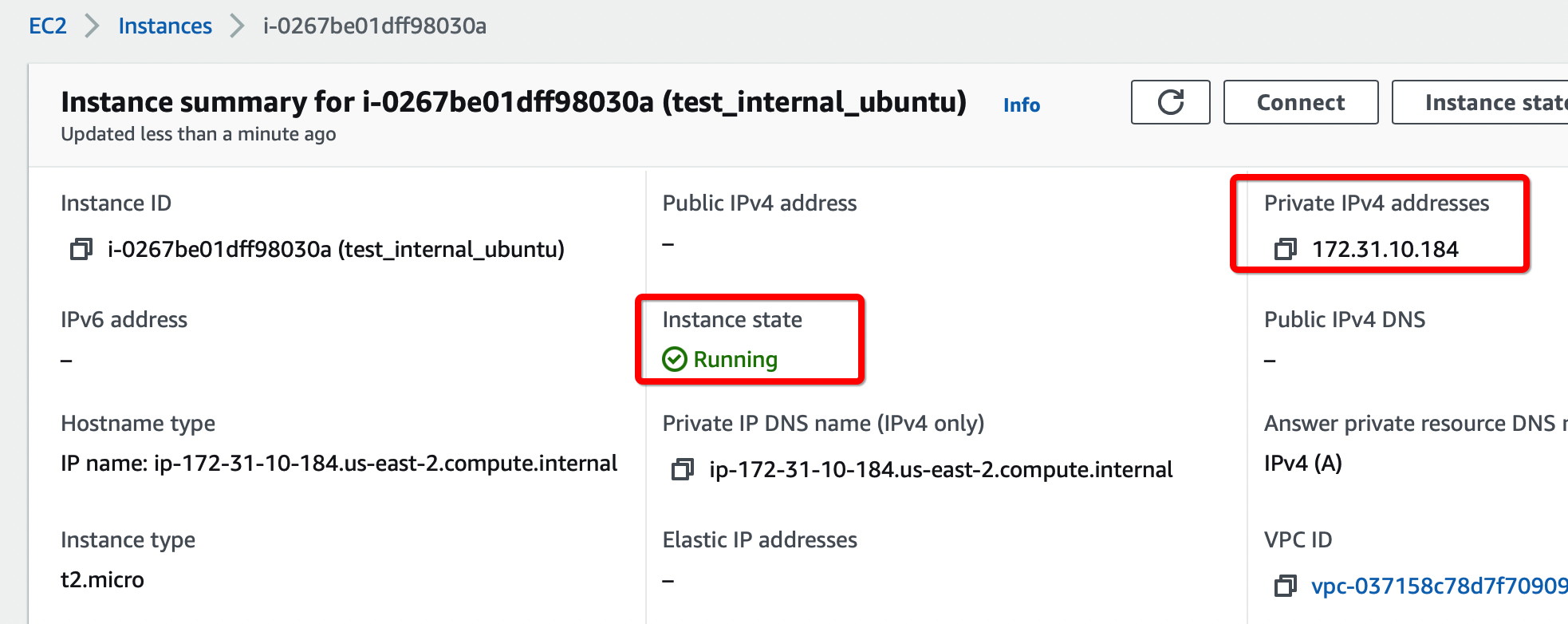
AWS VPC - Create EC2 and Install Acreto Gateway Software
- Create new EC2 with Ubuntu in selected VPC.
- Connect with SSH to the new EC2 instance (username:
ubuntu)
- Copy and paste the command for acreto auto installation script - don’t press ENTER yet.
- Acreto - Generate IPsec config and copy the link
- Paste the link in the SSH terminal and press ENTER
AWS VPC - Update VPC Subnet Route Table
- Open the VPC panel on AWS, and from the left menu choose Route Tables.
- Modify the VPC Route Table - read more
- Info: A routing table that’s associated with a subnet for the VPC.
- Add
100.64.0.0/16 on the Route Table
- Destination
100.64.0.0/16.
- Target Instance - “Acreto Gateway” (
eni- of that instance).
- If there are more AZ (Availability Zones), update the route table for the other subnets as well.
- Update AWS Security Group to allow all inbound and outbound traffic for Acreto subnet
100.64.0.0/16- Allow all traffic from/to this subnet, because we control the traffic on Acreto Security Policies
AWS EC2 - Disable source/destination checks for EC2 instance
- To disable source/destination checking using the console
- Open the Amazon EC2 console at https://console.aws.amazon.com/ec2/.
- In the navigation pane, choose Instances.
- Select the NAT instance, choose Actions, Networking, Change Source/destination check.
- Verify that source/destination checking is stopped. Otherwise, choose Stop.
- Choose Save.
- Read more on AWS
- Create a Security Policy to allow traffic from selected Gateway and/or Profile Group(s) to the VPC subnet
AWS Site-to-Site VPN using Virtual Private Gateway
Before You Start
Overview
This article describes how to configure a Route-Based Site-to-Site IPsec VPN between an Acreto Ecosystem and the Amazon Web Services (AWS) Virtual Private Cloud (VPC) using static routing:
- Network Diagram
- Concepts and Glossary
- Prerequisities
- The Purpose of Site-to-Site IPsec VPN
- Configuring Acreto Gateway object for IPsec AWS Site-to-Site VPN tunnel
- Setting up the Amazon AWS Virtual Private Cloud and VPN Connection
- References and Related Articles
Network Diagram
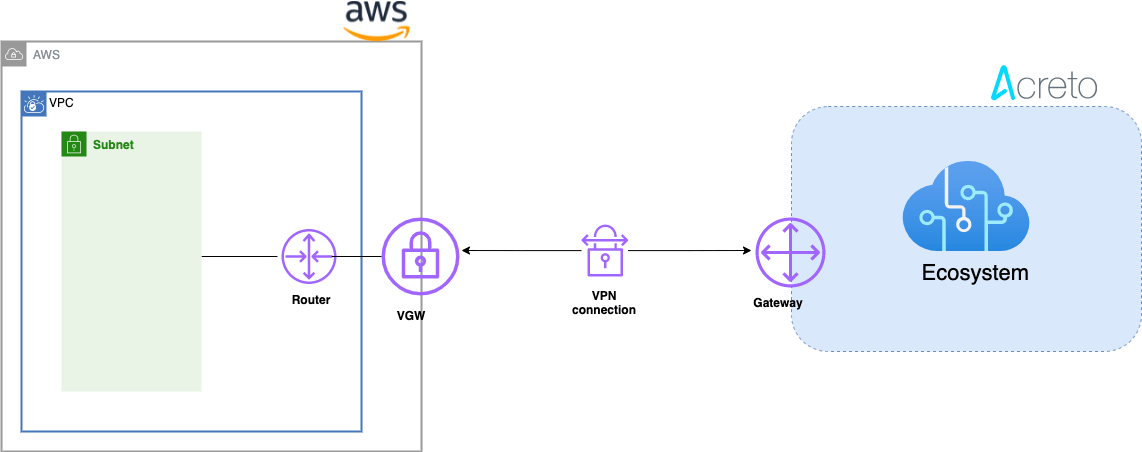

Concepts and Glossary
- IPsec VPN tunnel: An encrypted link where network traffic can pass between Acreto Ecosystem and AWS VPS.
- Customer gateway: An AWS resource that provides information to AWS about the Acreto IPsec Gateway object.
- Virtual private gateway: The VPN concentrator on the Amazon side of the Site-to-Site VPN connection.
Prerequisites
In order to setup IPsec Site-to-Site VPN tunnel between Acreto Ecosystem and AWS VPS you need:
- Access to Active Acreto Ecosystem
- Access to AWS Management Console
The Purpose of Site-to-Site IPsec VPN
Acreto as a Cloud Provider allows to connect and integrate multiple networks, both physical and virtual. All connections require stable and secure links. Virtual (EC2) Instances running on Amazon VPC can’t communicate securely with your own (remote) network by default. It is possible to connect your network to Acreto Ecosystem and then you can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection, and configuring routing to pass traffic through the connection.
Acreto Ecosystem configures the routing automatically and passes the traffic between AWS VPC and your network. Additionally, the traffic is scanned by the Acreto Threat Engine to block suspicious traffic and malware.
Tip
AWS Site-to-Site VPN limitations: IPv6 traffic is not supported for VPN connections on a virtual private gateway. An AWS VPN connection does not support Path MTU Discovery. In addition, take the following into consideration when you use Site-to-Site VPN.
Use the following procedures to manually set up the AWS Site-to-Site VPN connection on Amazon AWS.
You can create a Site-to-Site VPN connection with either a virtual private gateway or a transit gateway as the target gateway.
Step 1: Create VPC
Use existing VPC or create a new VPC using the steps below :
-
Login to AWS console.
-
Goto the region where you want to create your VPC.
-
Search VPC in the Services search tab.
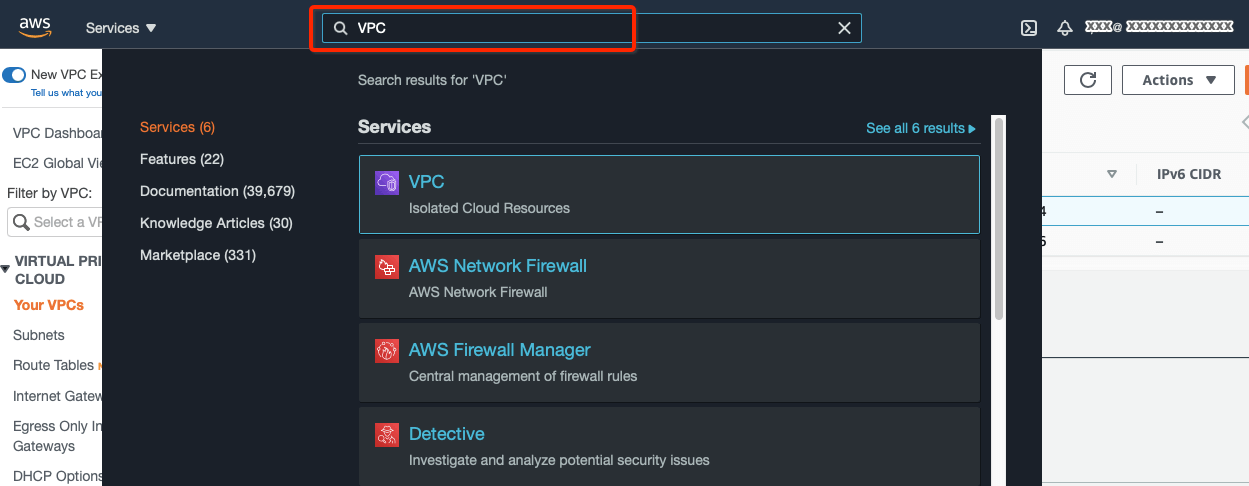

-
From the VPC Dashboard, click Your VPCs under VIRTUAL PRIVATE CLOUD in the left sidebar and click Create VPC
-
Create a VPC with the following values:
- IPv4 CIDR Block: 172.16.0.0/22
- IPv6 CIDR Block: No IPv6 CIDR Block
- Tenancy: default
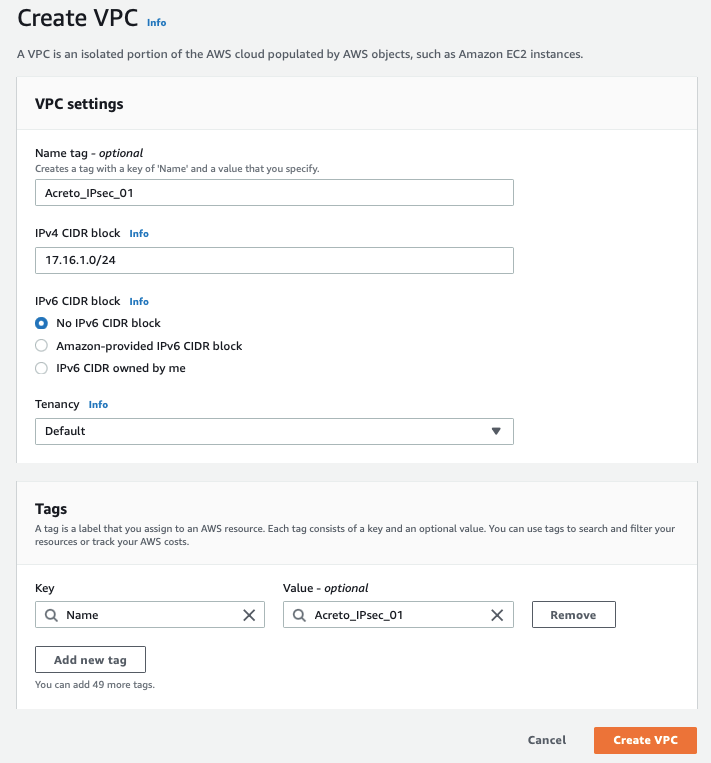

-
Click Create VPC
Step 2: Create Subnet
Now create a new subnet in the VPC address range. If you want to use an existing subnet, you can skip this step and use the pre-existing subnet in subsequent steps.
-
From the VPC Dashboard, click Subnets under VIRTUAL PRIVATE CLOUD in the left sidebar and click Create Subnet
-
Select the new VPC created in the Step 1 or your existing VPC in the VPC ID options.
-
Create a new Subnet under Subnet settings with the below details :
- Availability Zone: No preference
- IPv4 CIDR block: 172.16.1.0/24
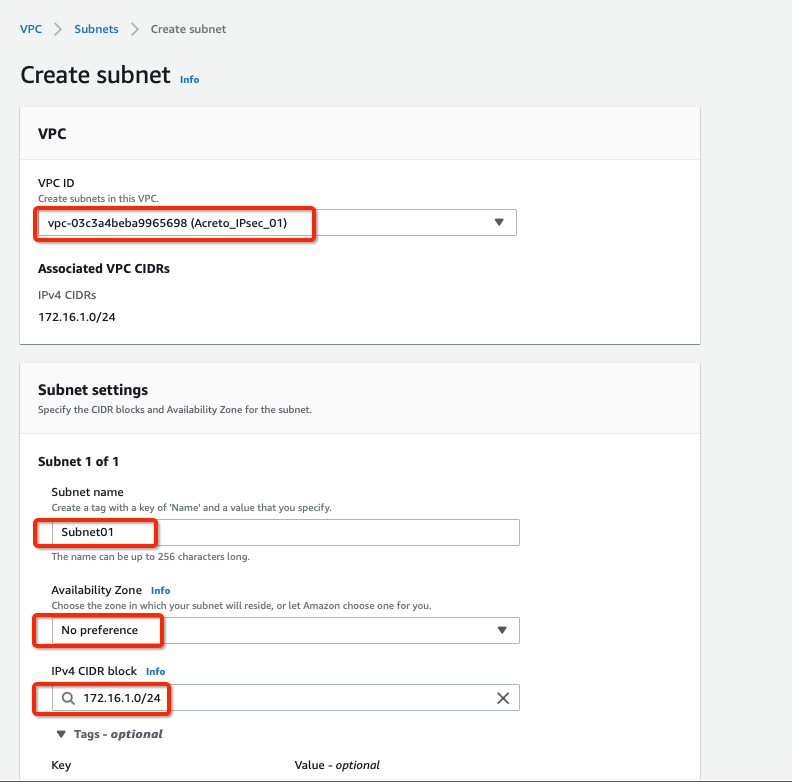

-
Click Create Subnet button
Step 3: Create Internet Gateway
-
From the VPC Dashboard, click Internet Gateway under VIRTUAL PRIVATE CLOUD in the left sidebar and click Create Internet Gateway
-
Give the name for the Internet gateway and click Create internet gateway
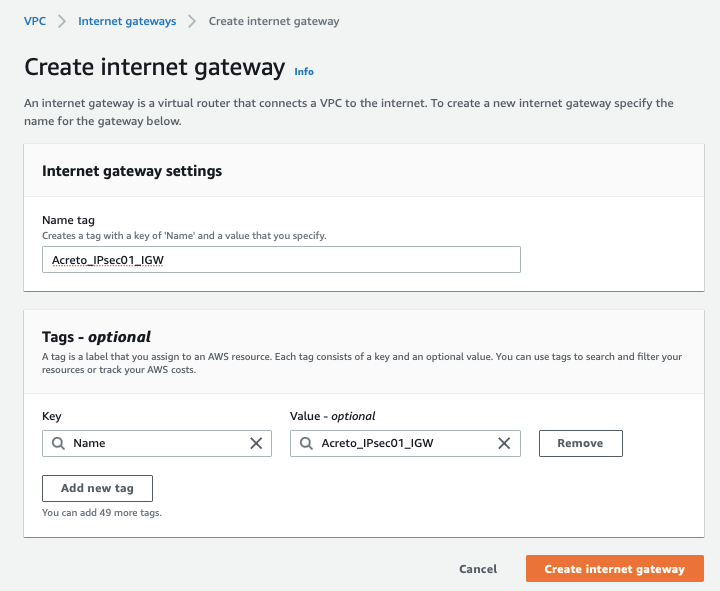

-
Select the Internet gateway and click Actions and Attach to VPC
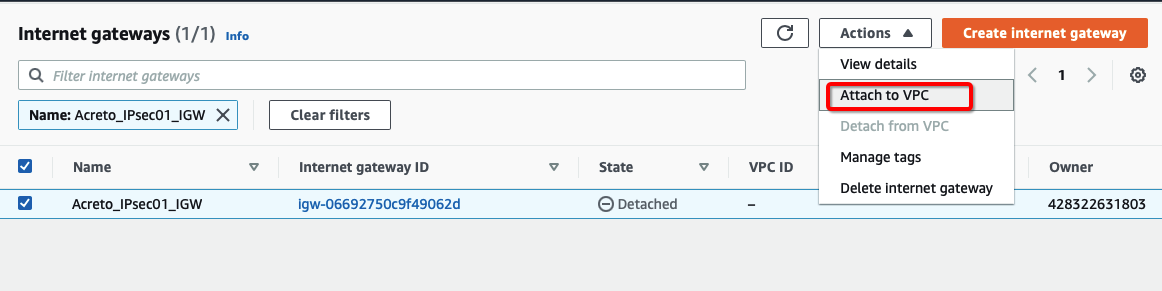

-
Assign your VPC
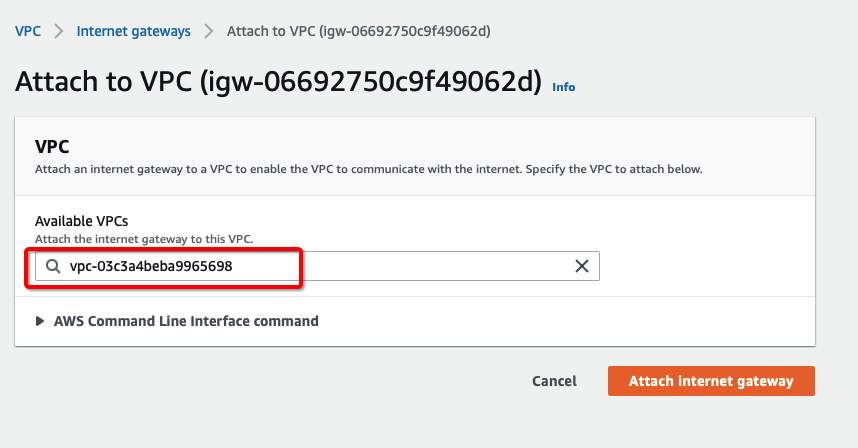

-
Click Attach internet gateway.
Step 4: Create Route Table
Configure Route table for the above subnet to reach Acreto’s public IP through Internet Gateway.
-
From the VPC Dashboard, click Route Tables under VIRTUAL PRIVATE CLOUD in the left sidebar and click Create Route Table
-
Create a Route table with the following values:
- Name: Acreto_ipsec_RT
- VPC: Select the VPC created in Step 1
-
Click Create Route Table, with parameters as shown in screenshot below:
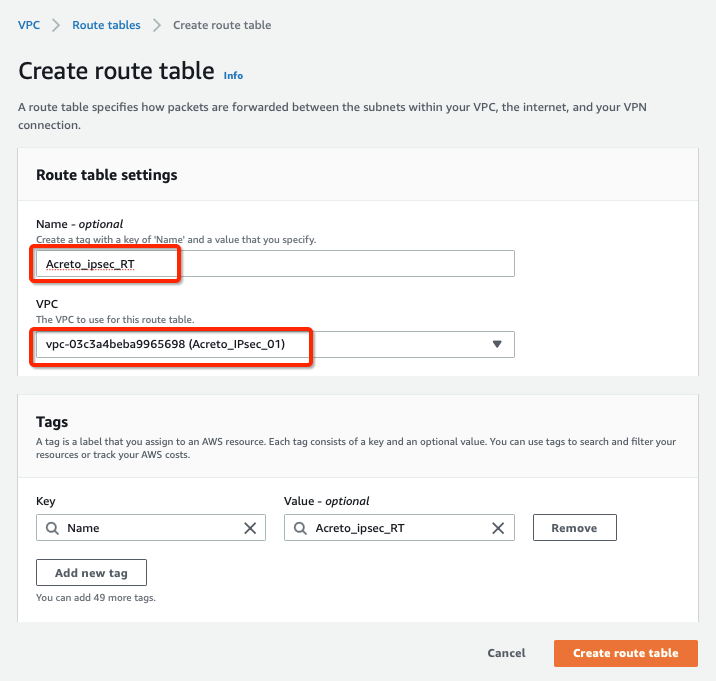

-
Select the Route table created above and click Subnet association, with parameters as shown in screenshot below:
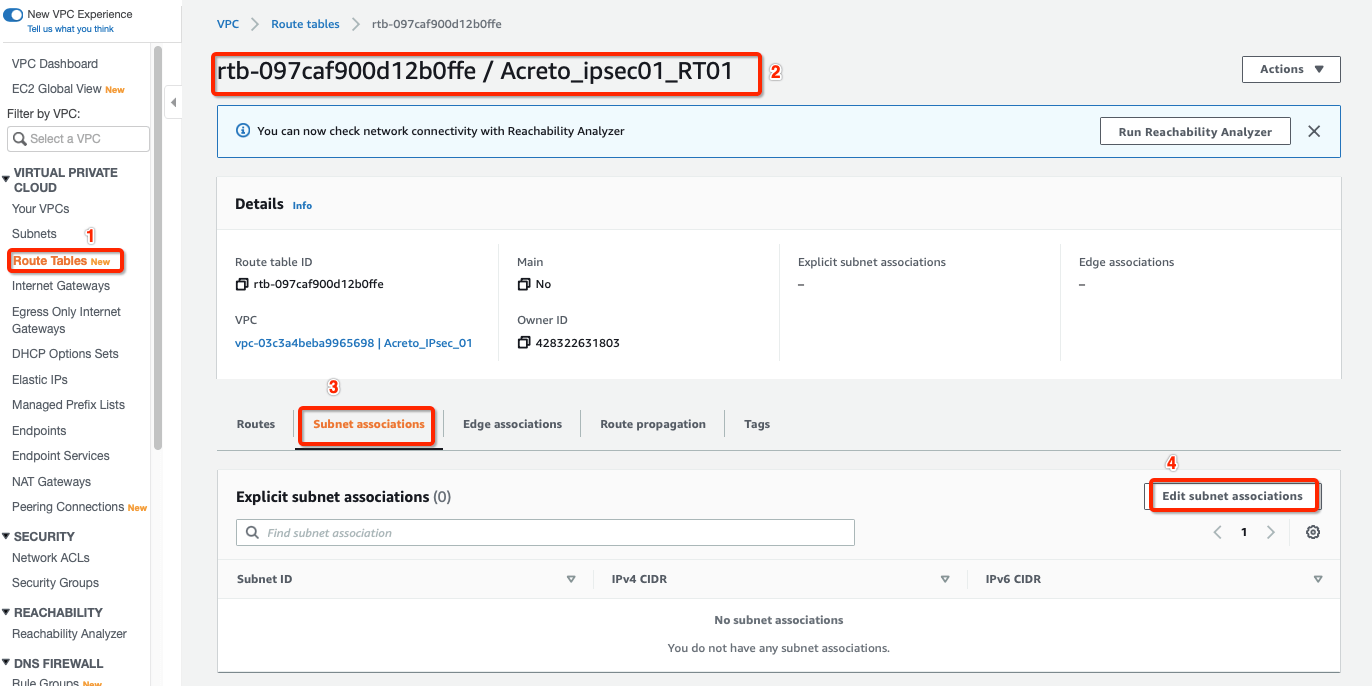

-
Select your Subnet and click Save associations, with parameters as shown in screenshot below:
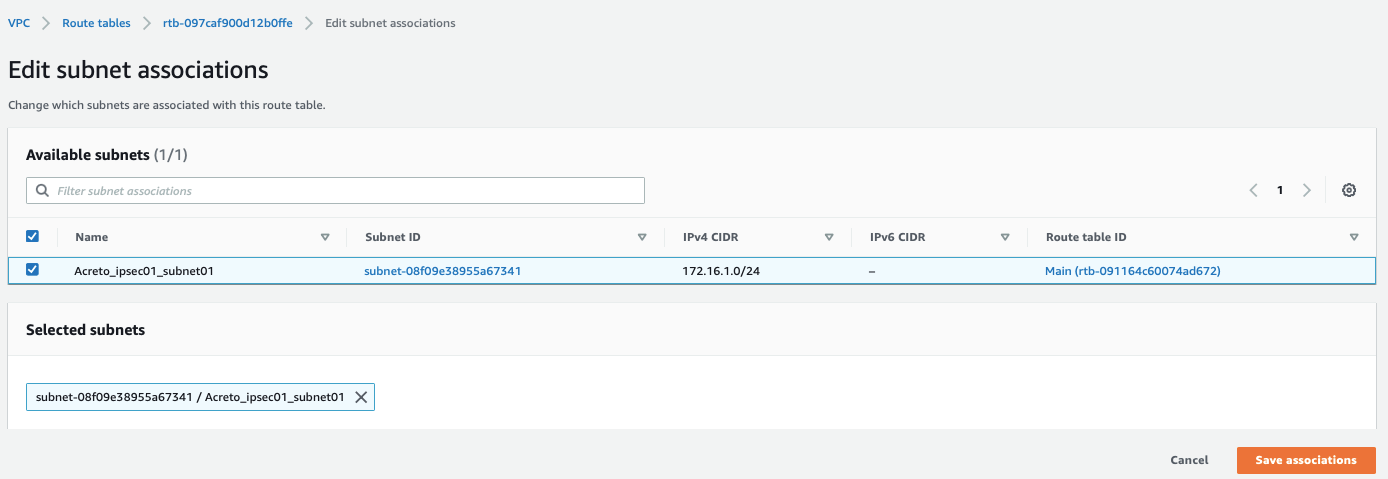

-
Select the routes and click Edit routes, with parameters as shown in screenshot below:
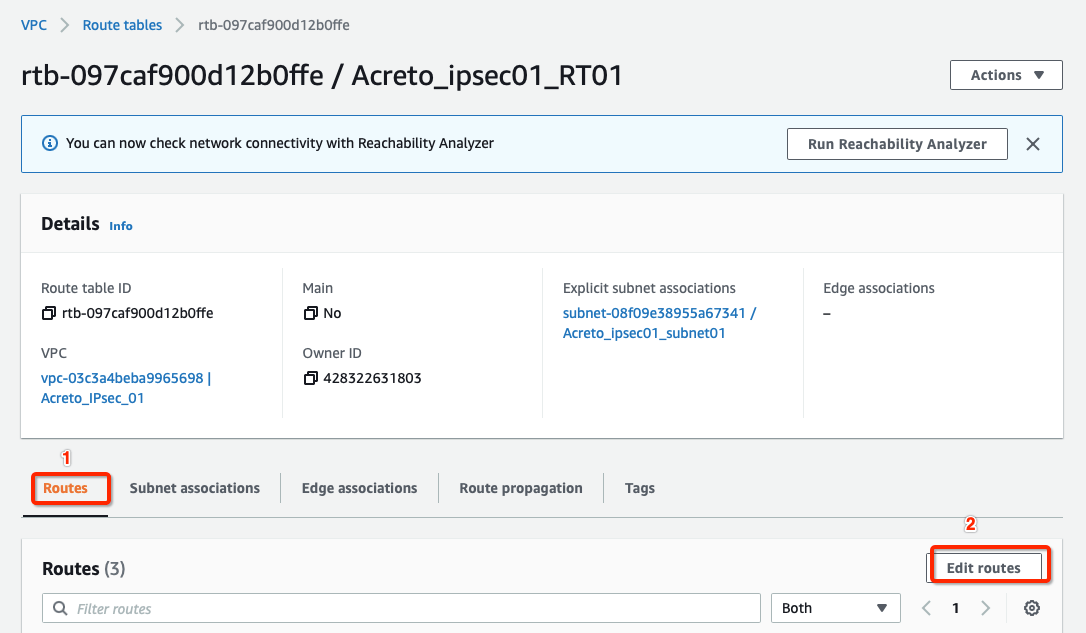

-
Add route for Acreto’s Default Tunnel IP used to form the VPN through the Internet Gateway, with parameters as shown in screenshot below:
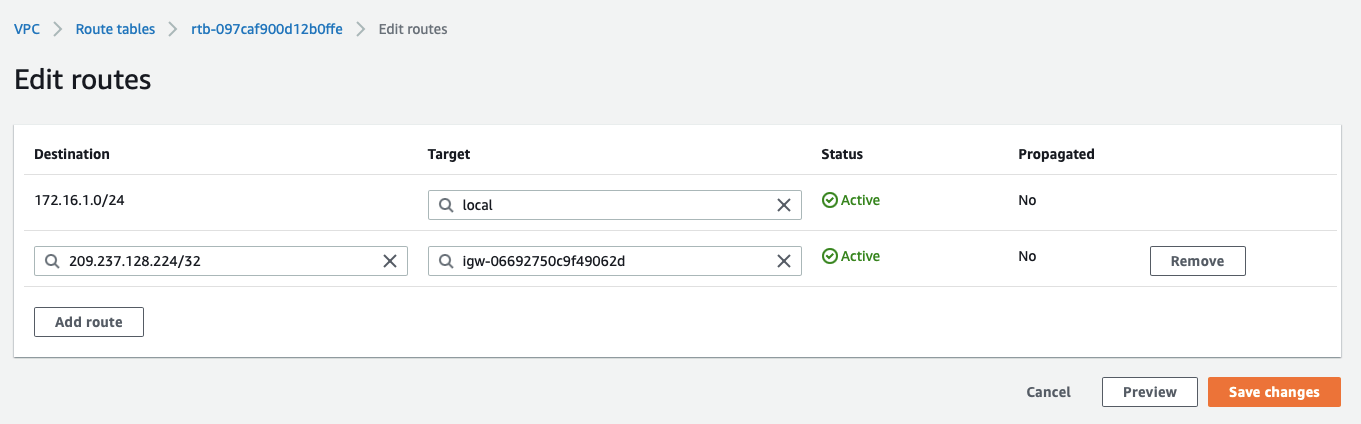

-
Click Save changes.
Step 5: Create Customer Gateway
Create new Customer Gateway with Acreto’s public IP.
-
From the VPC Dashboard in the left side bar, goto VIRTUAL PRIVATE NETWORK (VPN) » Customer Gateways
-
Click Create Customer Gateway
-
Provide the following values :
- Name: Acreto
- Routing: Static
- IP Address: Acreto’s Default Tunnel IP

-
Click Create Customer Gateway.

Step 6: Create Virtual Private Gateway
Create a Virtual Private gateway that will be used to form the Ipsec tunnel with Acreto.
-
From the VPC Dashboard in the left sidebar, goto VIRTUAL PRIVATE NETWORK (VPN) » Virtual Private Gateways
-
Click Create Virtual Private Gateway
-
Give the name and click Create Virtual Private Gateway

-
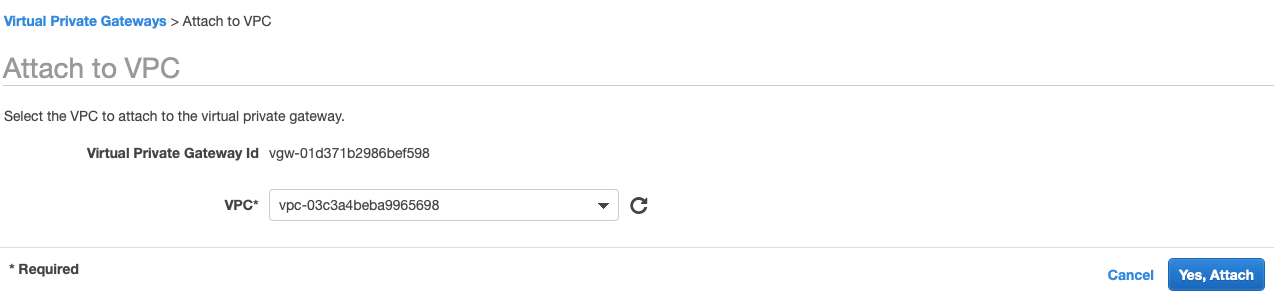
Select the Virtual Private Gateway and click Actions » Attach to VPC

-
Select your VPC and click Yes, Attach button.

-
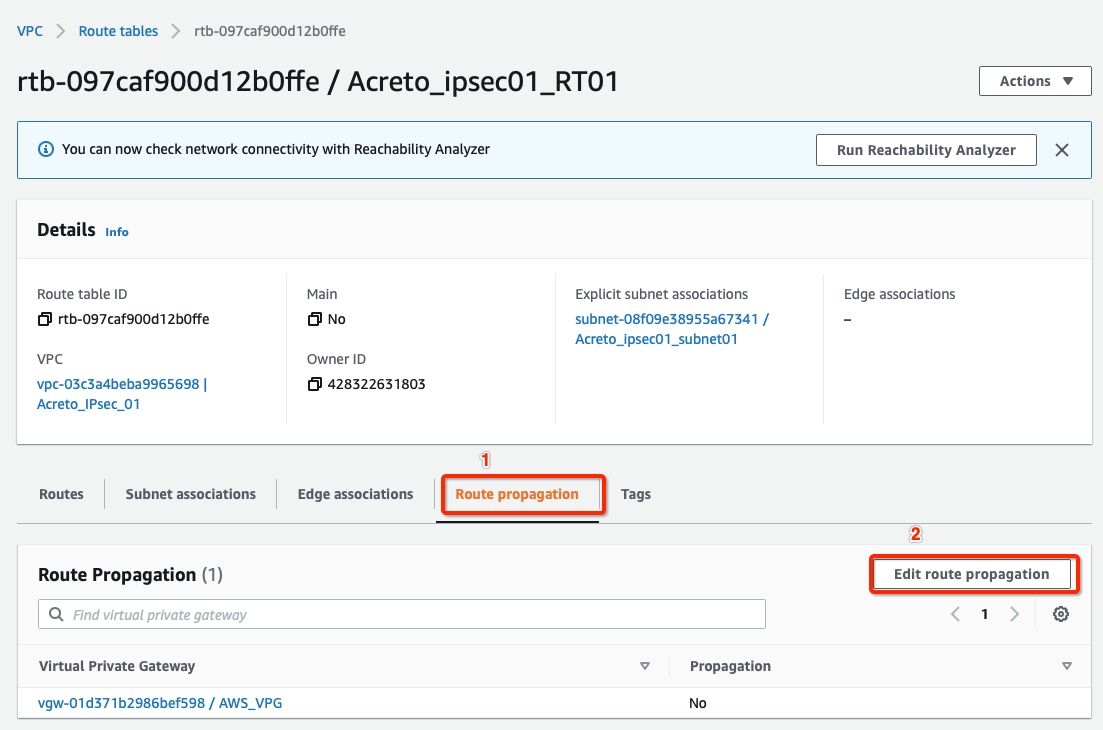
From the VPC Dashboard, click Route Tables under VIRTUAL PRIVATE CLOUD in the left sidebar.
-
Select the route table created in Step 4
-
Select the Route Propagation tab and click the button Edit route propagation.

-
Check Enable
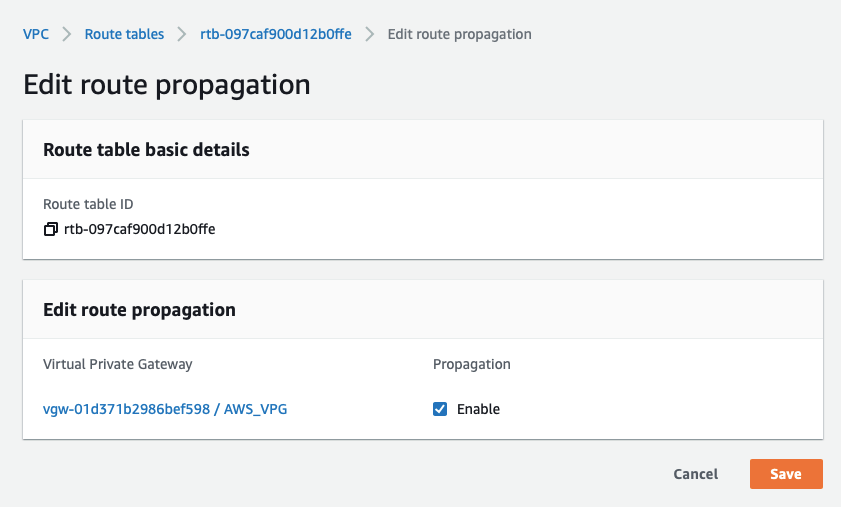

-
Click the Save button.
Tip
This step ensures that the AWS virtual hosts receive a route for the 100.64.0.0/16 network (Acreto Ecosystem Internal network) after the VPN establishes.
Create a new VPN connection and associate the previously created VGW and CGW.
-
From the VPC Dashboard in the left sidebar, go to VIRTUAL PRIVATE NETWORK (VPN) » Site-to-Site VPN Connections.
-
Click Create VPN Connection.
-
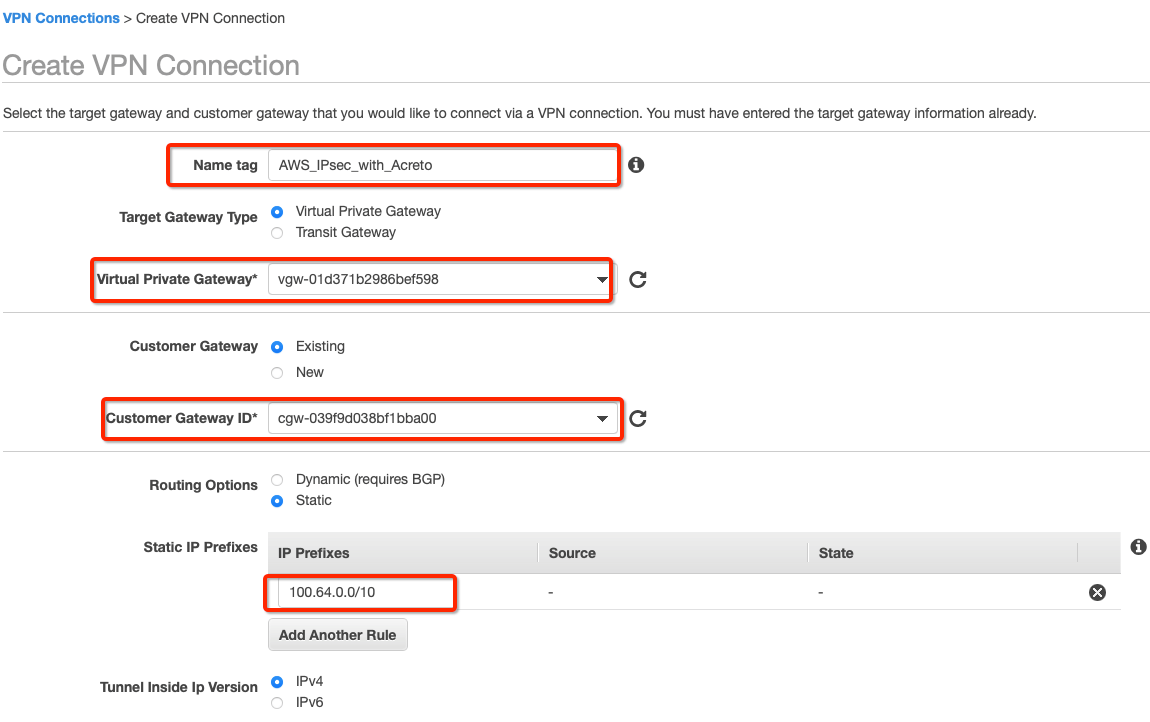
Provide the following values in the tunnel setting:
- Name: Acreto_ipsec
- Target Gateway Type: Virtual Private Gateway
- Virtual Private Gateway: Select the Virtual Private gateway created above
- Customer Gateway: Existing
- Customer Gateway ID: Select the Customer gateway created above
- Routing Options: Static
- Static IP Prefixes: 100.64.0.0/16

-
Click Create VPN Connection.
-
Select the VPN created and click the tab Tunnel Details. Copy the Outside IP address of the tunnel to form a VPN with Acreto.
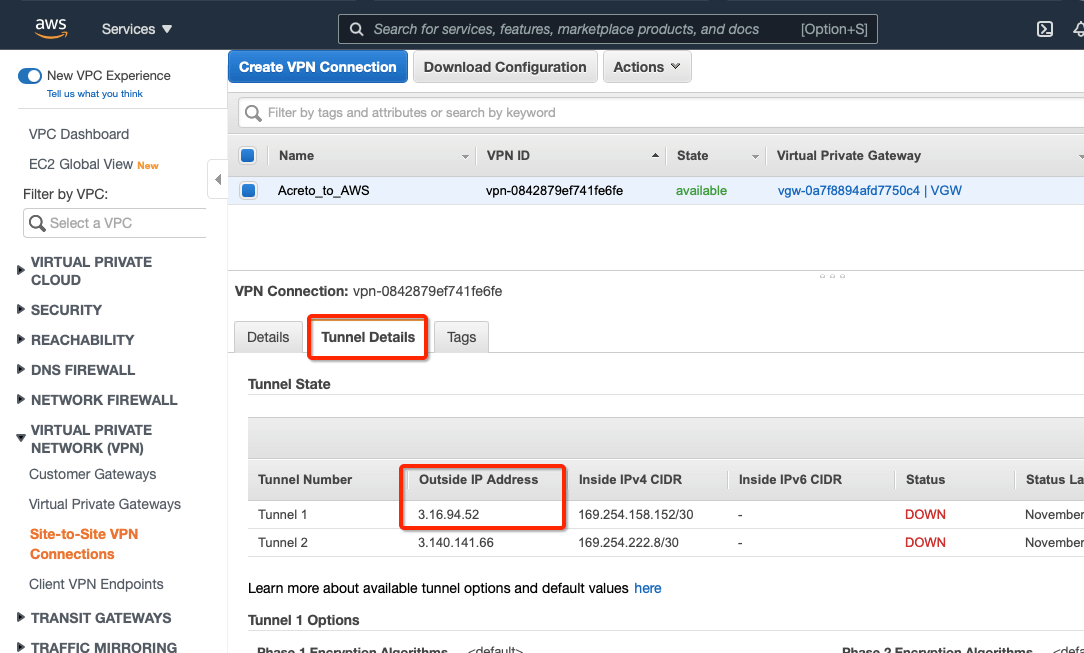

This Outside IP address will be used in the next steps to configure the Acreto gateway on Wedge Ecosystem.
Step 8: Create Acreto Gateway for IPsec
Create Gateway on Ecosystem by following the instruction in the link. Provide the following values:
- Type: IPsec
- Category: Data Center
- Model: AWS site-to-site VPN
- Connections from: AWS Tunnel’s Outside IP address
- Local network: local_network
- Save and Commit the changes.
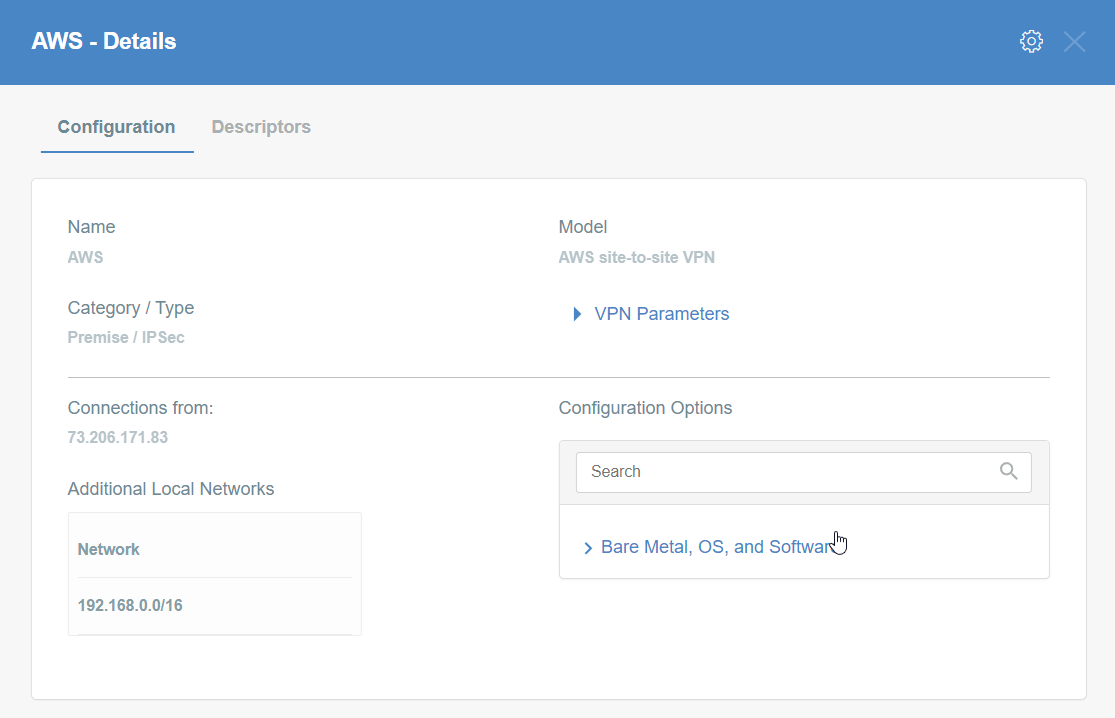

Step 9: Read the Configuration
-
Click the gateway created on wedge.
-
Click the Play button under Configuration Options to generate the strongSwan Config.
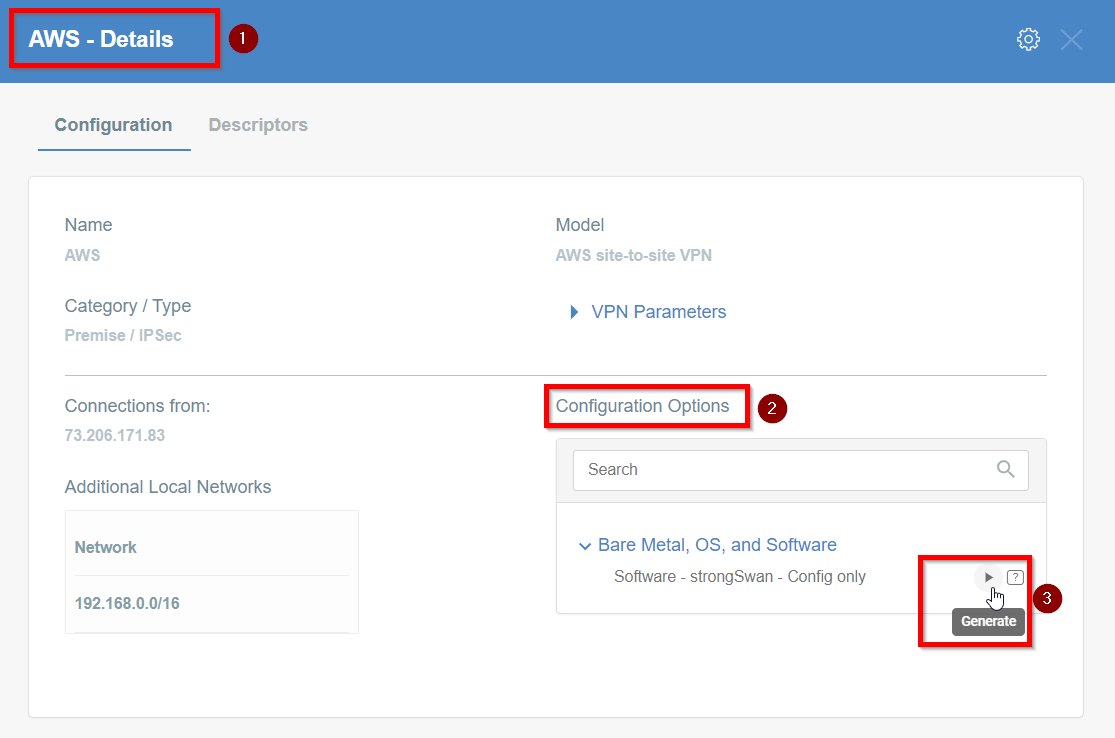

-
Once the Config file is generated, click the Download button to download the configuration on the local computer.
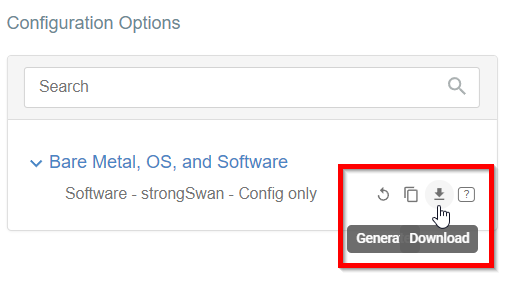

-
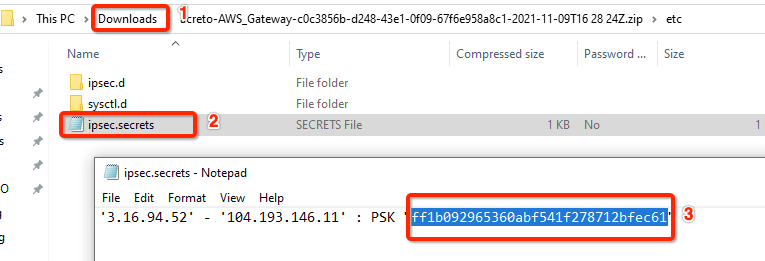
Unzip the downloaded file and copy the psk from the file ipsec.secrets
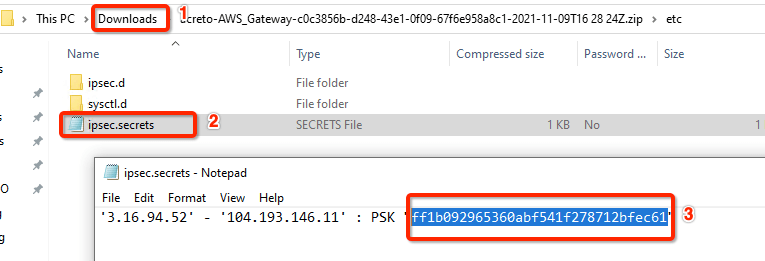

Step 10: Update AWS VPN tunnel configuration
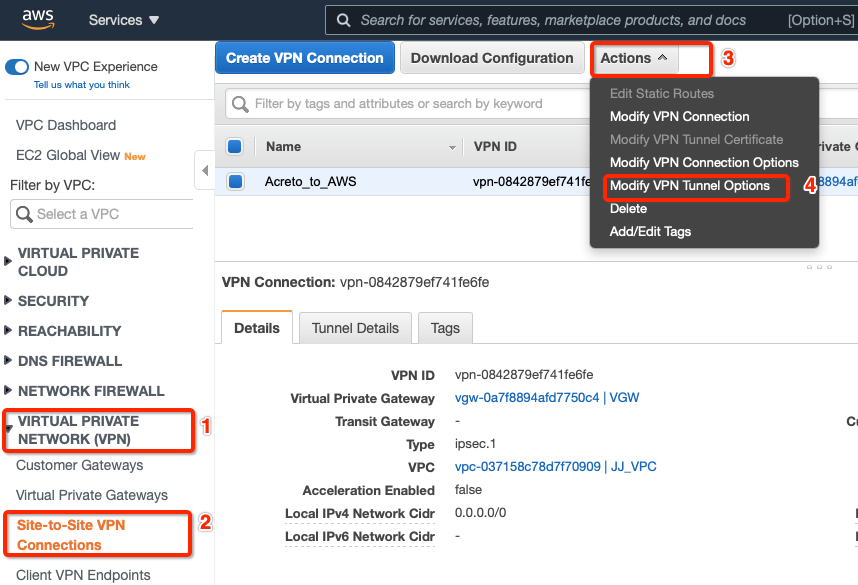
-
Goto AWS Site-to-Site VPN connections
-
Select the VPN and click Actions » Modify VPN Tunnel Option

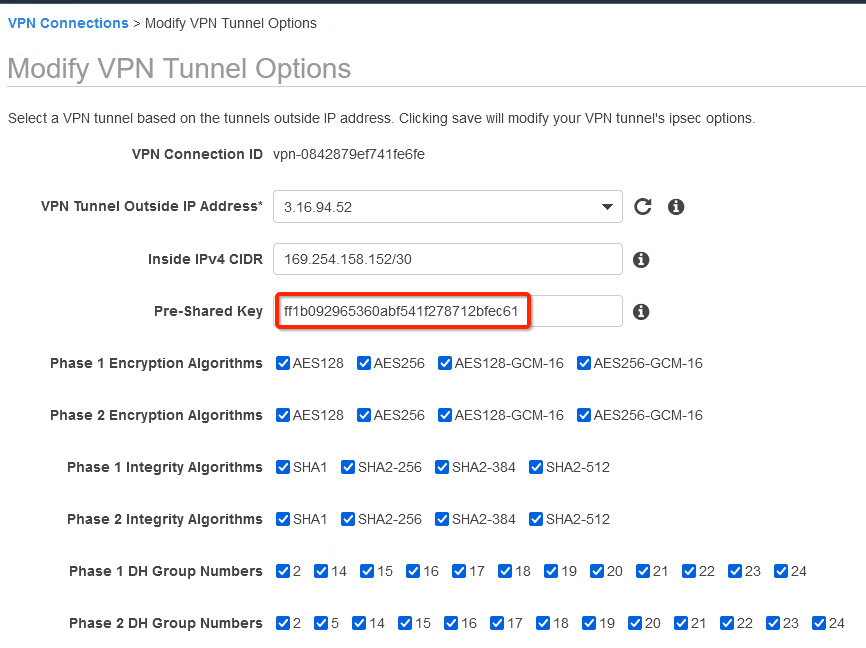
-
Select the tunnel used to create the VPN with Acreto.
-
Update the password copied from the ipsec.secrets file from strongSwan config file downloaded from Wedge

-
In the same window “Modify VPN Tunnel Options” scroll down and select the following action under tunnel configuration:
- DPD Timeout Action: Restart
- Startup Action: Start
-
Click Save
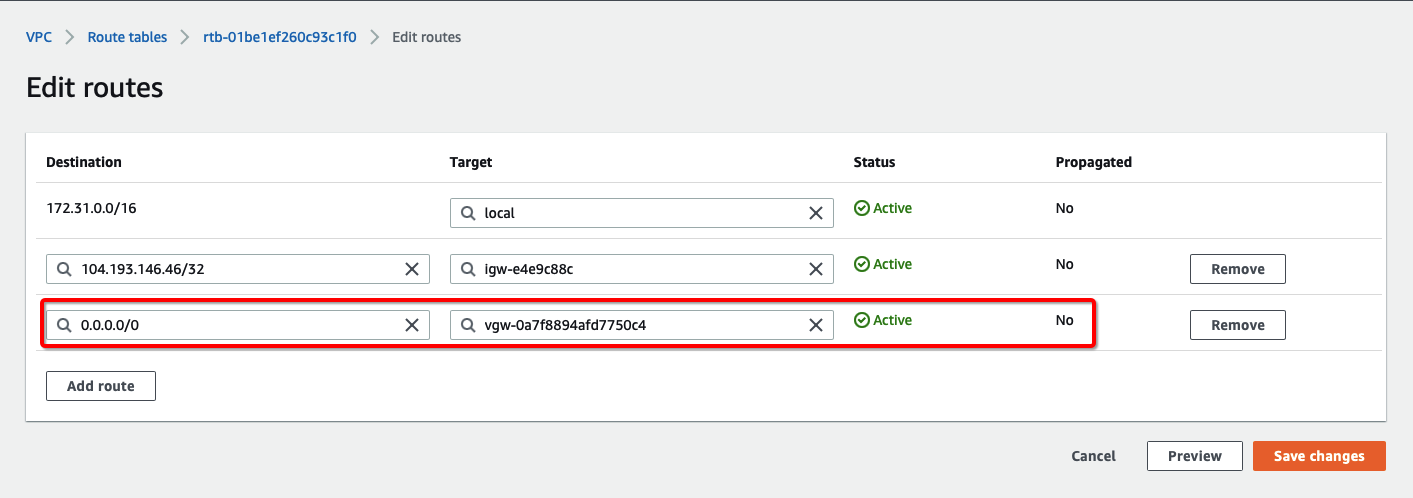
How-to: Update Route Table in AWS
Configure Route table to set the default route to VPN tunnel
-
From the VPC Dashboard, click Route Tables under VIRTUAL PRIVATE CLOUD in the left sidebar
-
Select the Route table and click Edit routes


-
Add the following route :
- Destination: 0.0.0.0/0
- Target: Select the Virtual Private Gateway id

-
Click Save changes.
Verify the connections
Once the tunnel connection is successfully established, the status of the connection will be up.
-
To verify on AWS, navigate to the VPN created under VIRTUAL PRIVATE NETWORK (VPN) » Site-to-Site VPN Connections .
-
Verify the following:
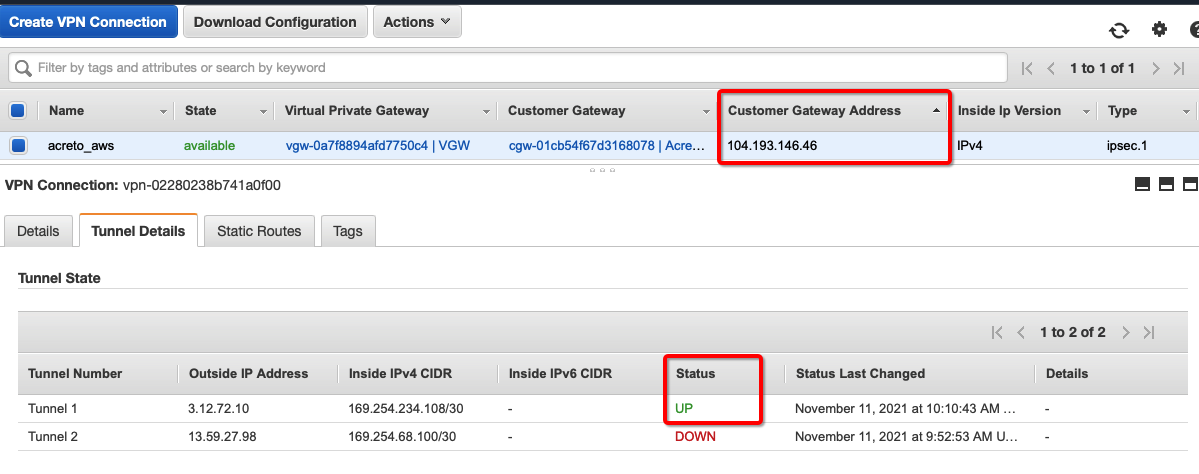

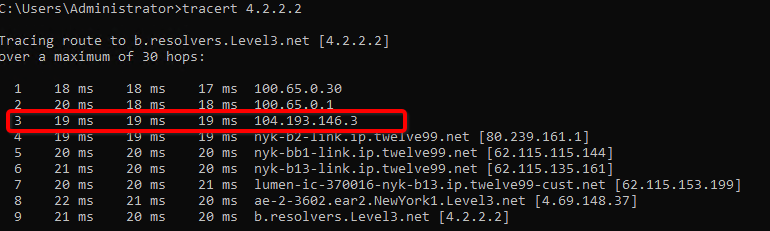
-
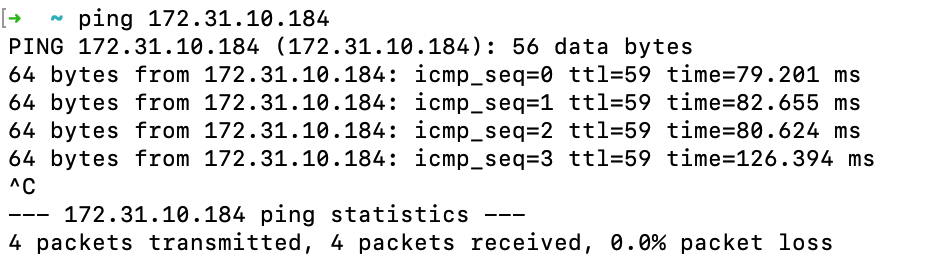
Do a traceroute or equivalent command from an internal server to public IP like 4.2.2.2. It should show Acreto’s IP in the path.

References and Related Articles
What is AWS Site-to-Site VPN?
Summary
Acreto IPsec Gateway allows to set up VPN tunnel to connect Acreto Ecosystem with Amazon Web Services (AWS) Virtual Private Cloud (VPC).
Azure Site-to-Site connection using VPN Gateway
Before You Start
Overview
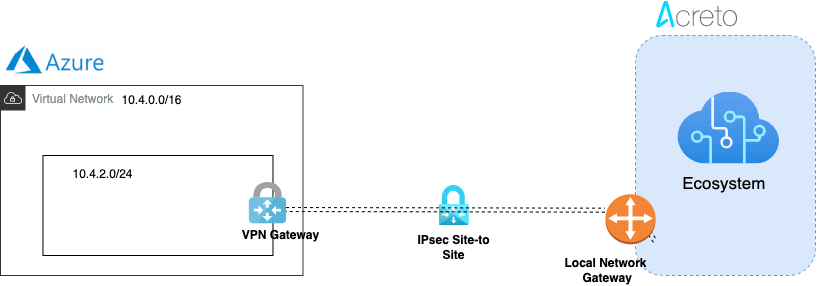
This article describes configuring a Route-Based Site-to-Site IPsec VPN between an Acreto Ecosystem and Azure network.
Network Diagram

Pre-requisite
To set up an IPsec Site-to-Site VPN tunnel between Acreto Ecosystem and Azure, you need:
- Access to Active Acreto Ecosystem (Wedge)
- Access to Azure Portal
Use the following procedures to set up the Azure Site-to-Site VPN connection manually.
Step 1: Create a virtual network
Use an existing virtual private network or create a new virtual private network using the steps below:
- Login to Azure Portal
- Click on Create a resource
- Click on Networking from the left sidebar.
- Click on Virtual Network
- Fill in the following fields in the Basics tab.
- Project details
- Subscription
- Resource group
- Instance details
- Name
- Region

- Fill in the following fields in the IP Addresses tab
- Address space
- Subnet Name
- Subnet Address range
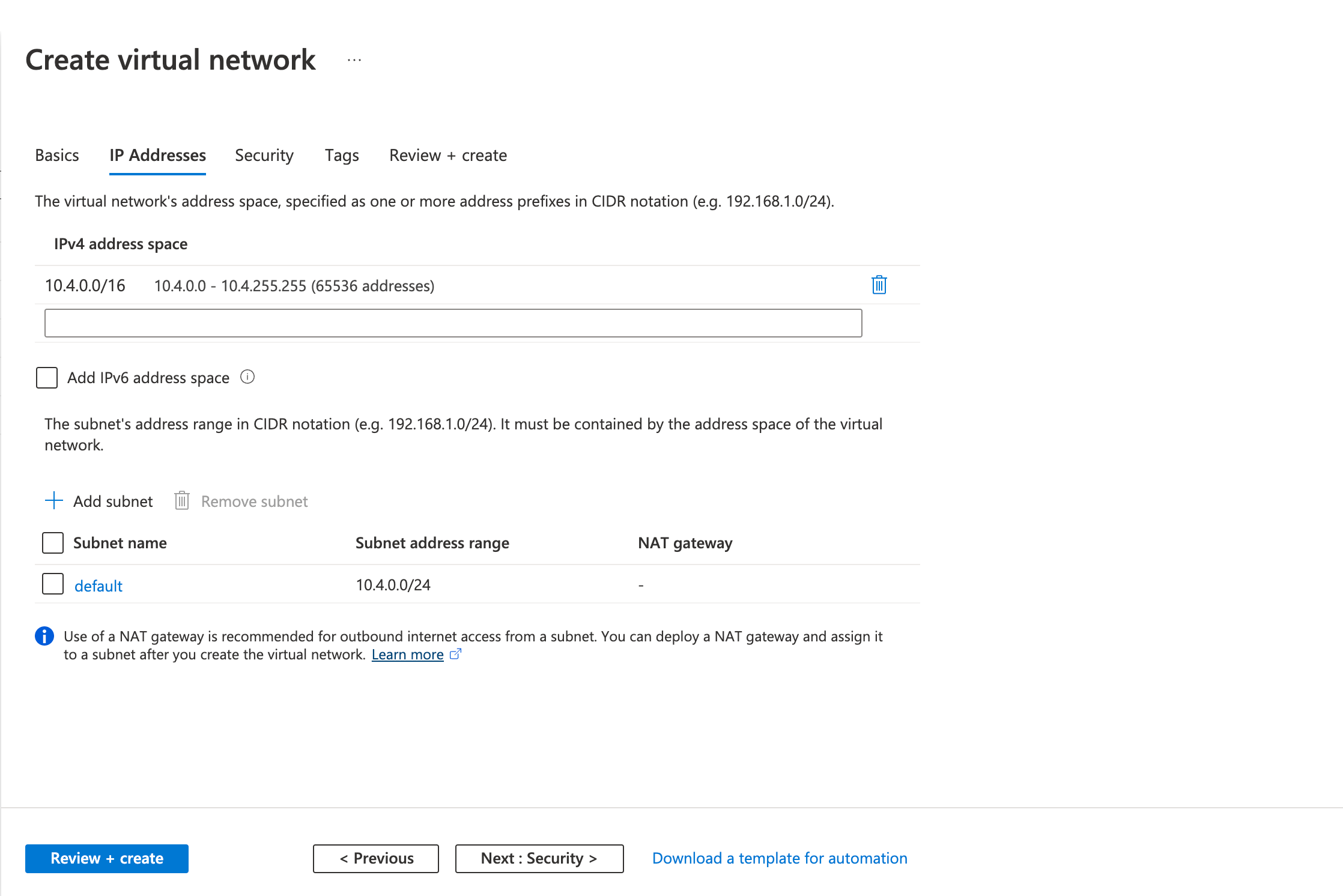

- Review the configurations on the Review + create tab and click Create
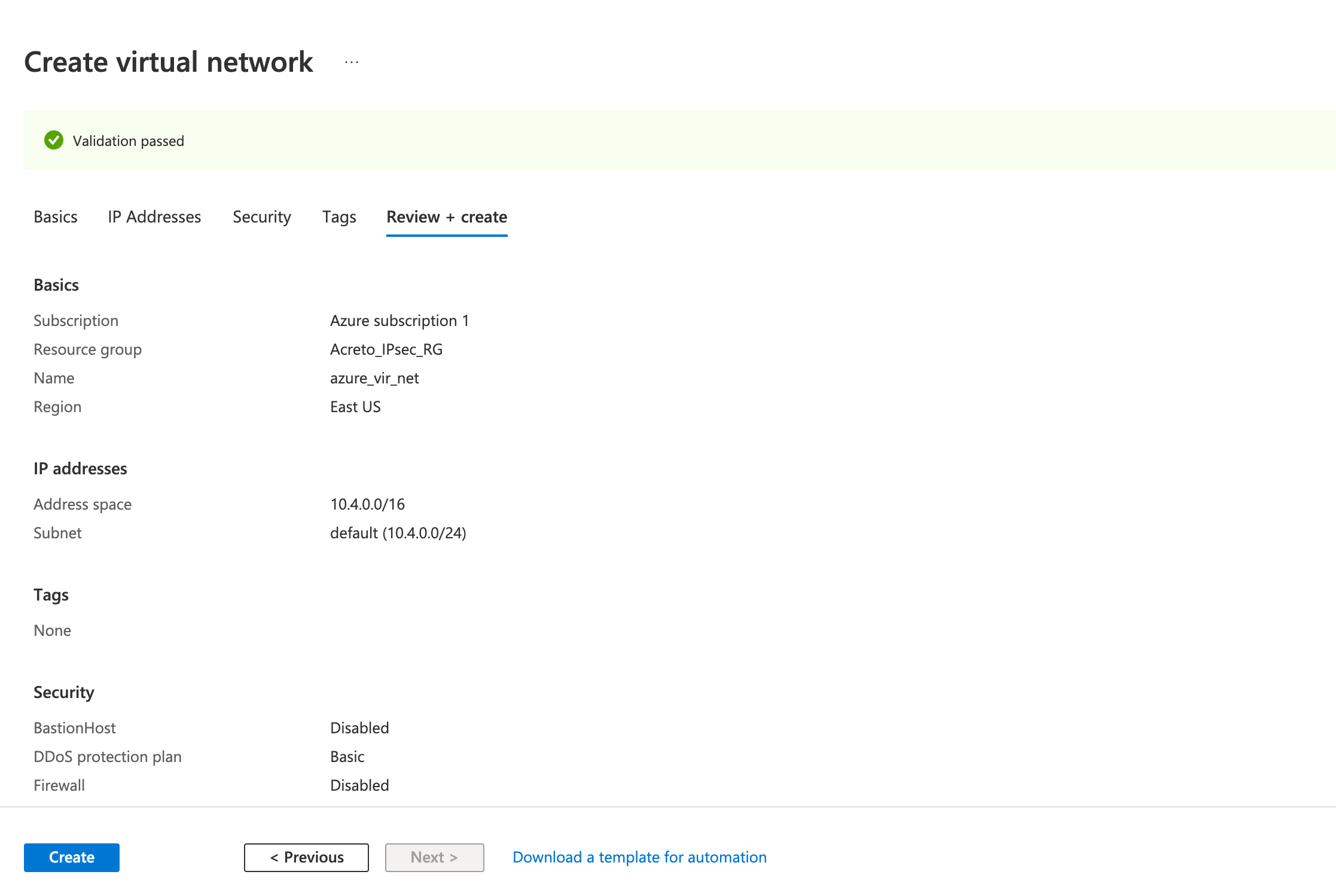

Wait for the deployment to finish and the Virtual Network to be created.
Step 2: Create a VPN gateway
Create the virtual network gateway for your virtual network. Creating a gateway can often take 45 minutes or more, depending on the selected gateway SKU.
- Click on Create a resource
- Click on Networking from the left sidebar
- Click on Virtual network gateway
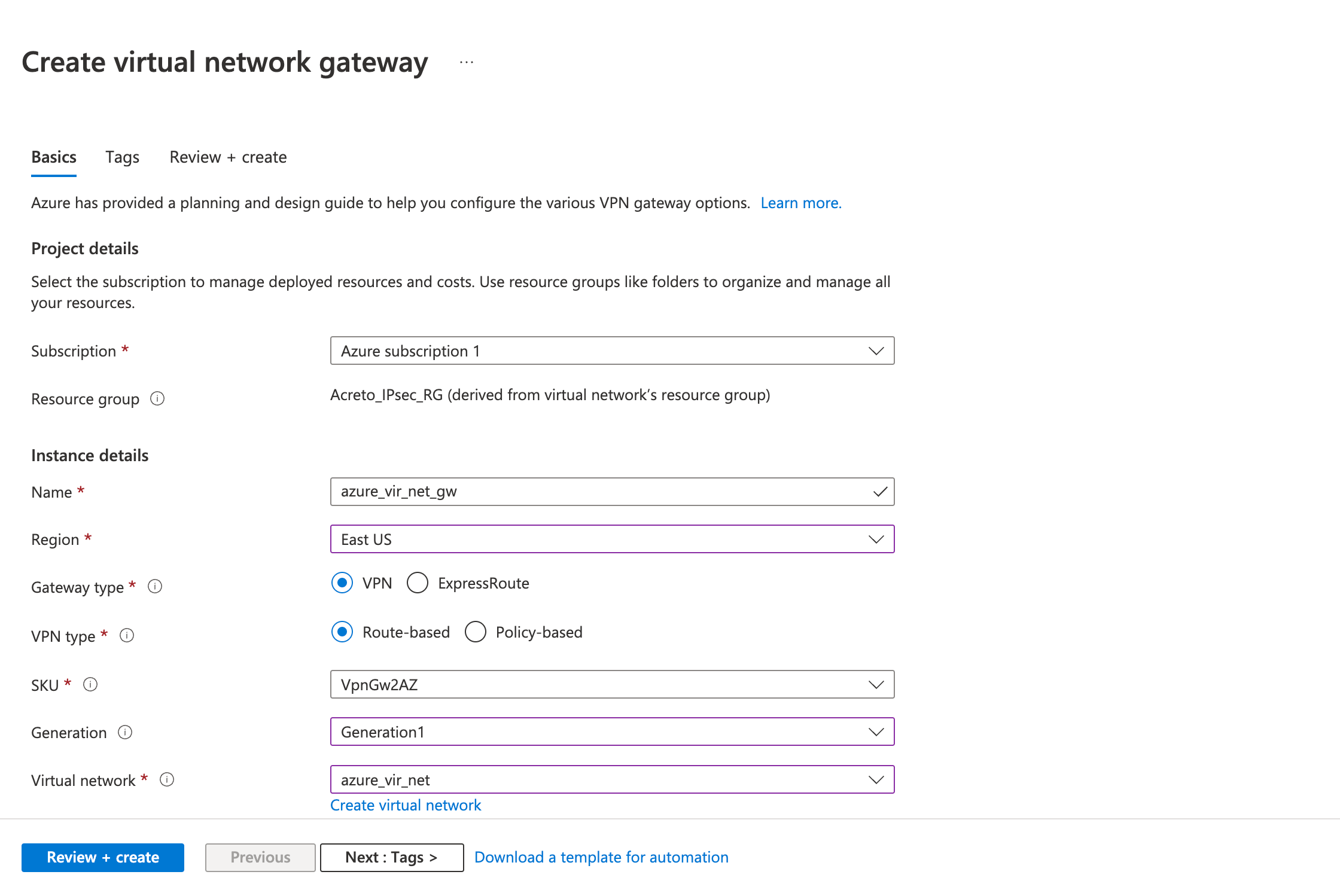
- Fill in the following fields in the Basics tab.
- Project details
- Instance details
- Name
- Region
- Gateway type: VPN
- VPN type: Route-based
- SKU
- Generation: Generation 1
- Virtual Network: (select the virtual network you created earlier)
- Gateway Subnet address range

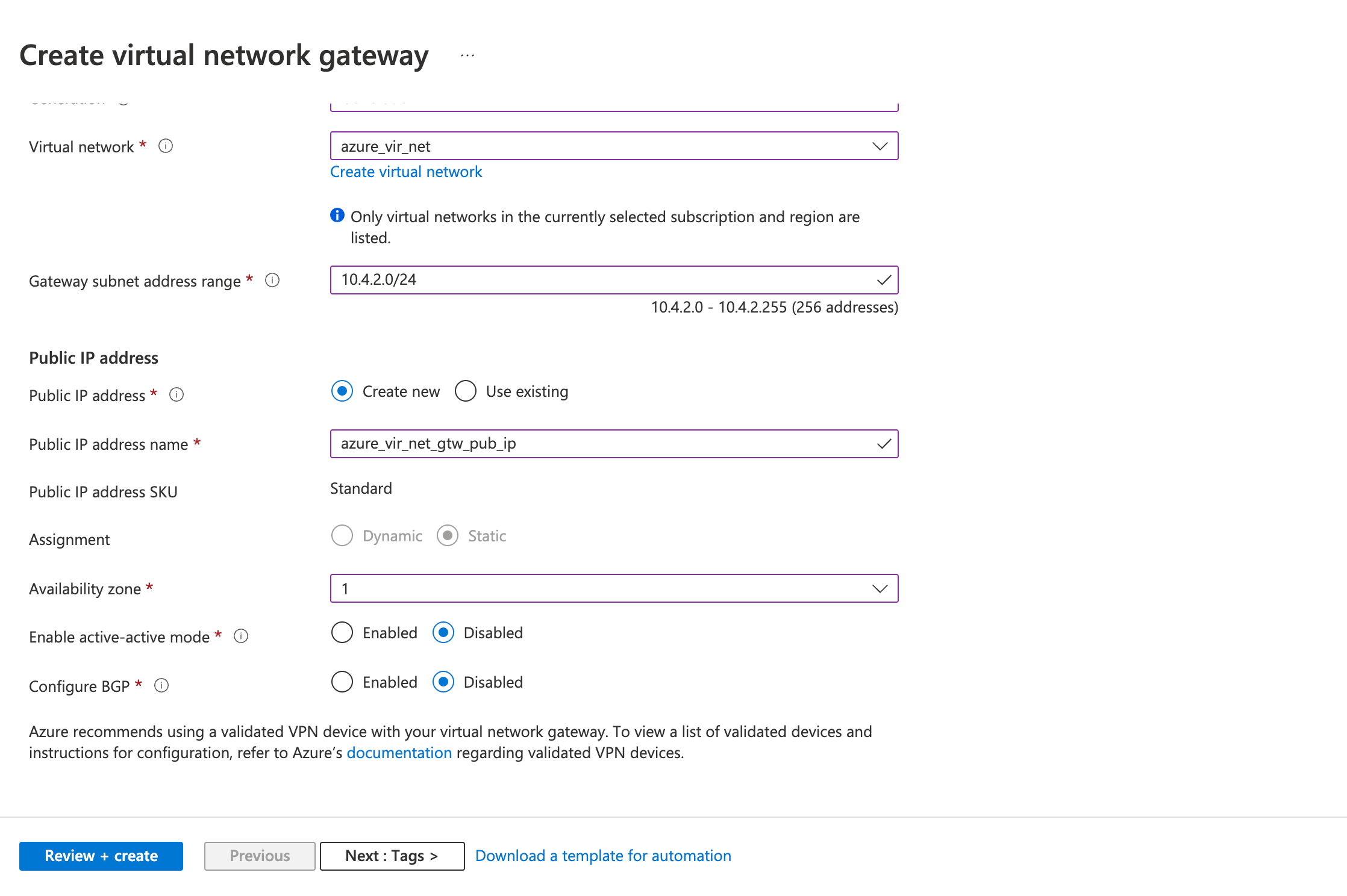

- Public IP address
- Public IP address: Create a new ( or use existing)
- Public IP address name
- Review the configurations on the Review + create tab and click Create
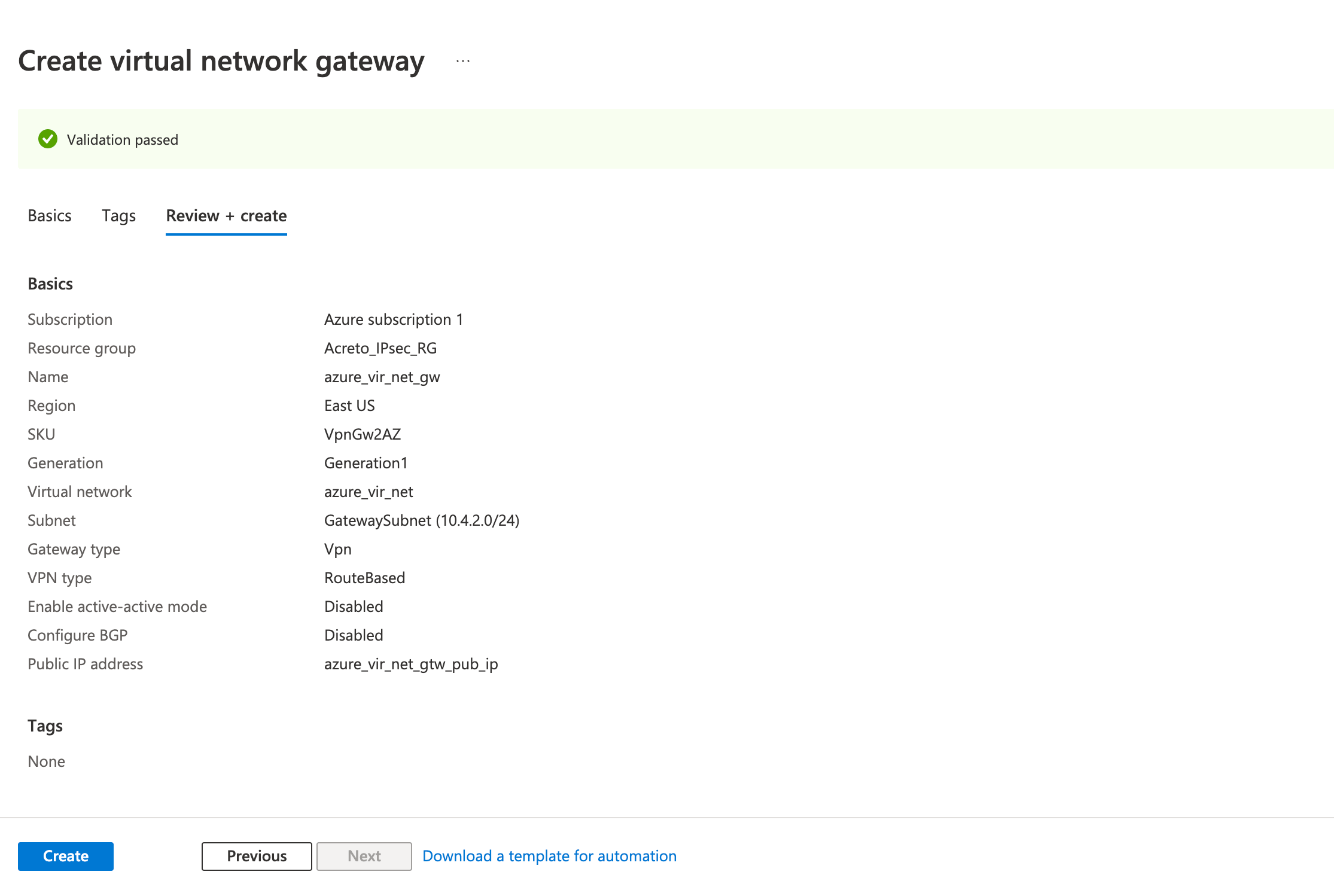

Step 3: Create a local network gateway
The next step is to create a local gateway representing your local network.
- Click on Create a resource
- In the search bar, search for Local Network Gateway
- Click on Create.
- Fill in the following fields in the Basics tab.
- Project details
- Subscription
- Resource group
- Instance details
- Name
- Region
- Endpoint: IP address
- IP Address: Acreto’s Tunnel IP
- Address Space(s): 100.64.0.0/16
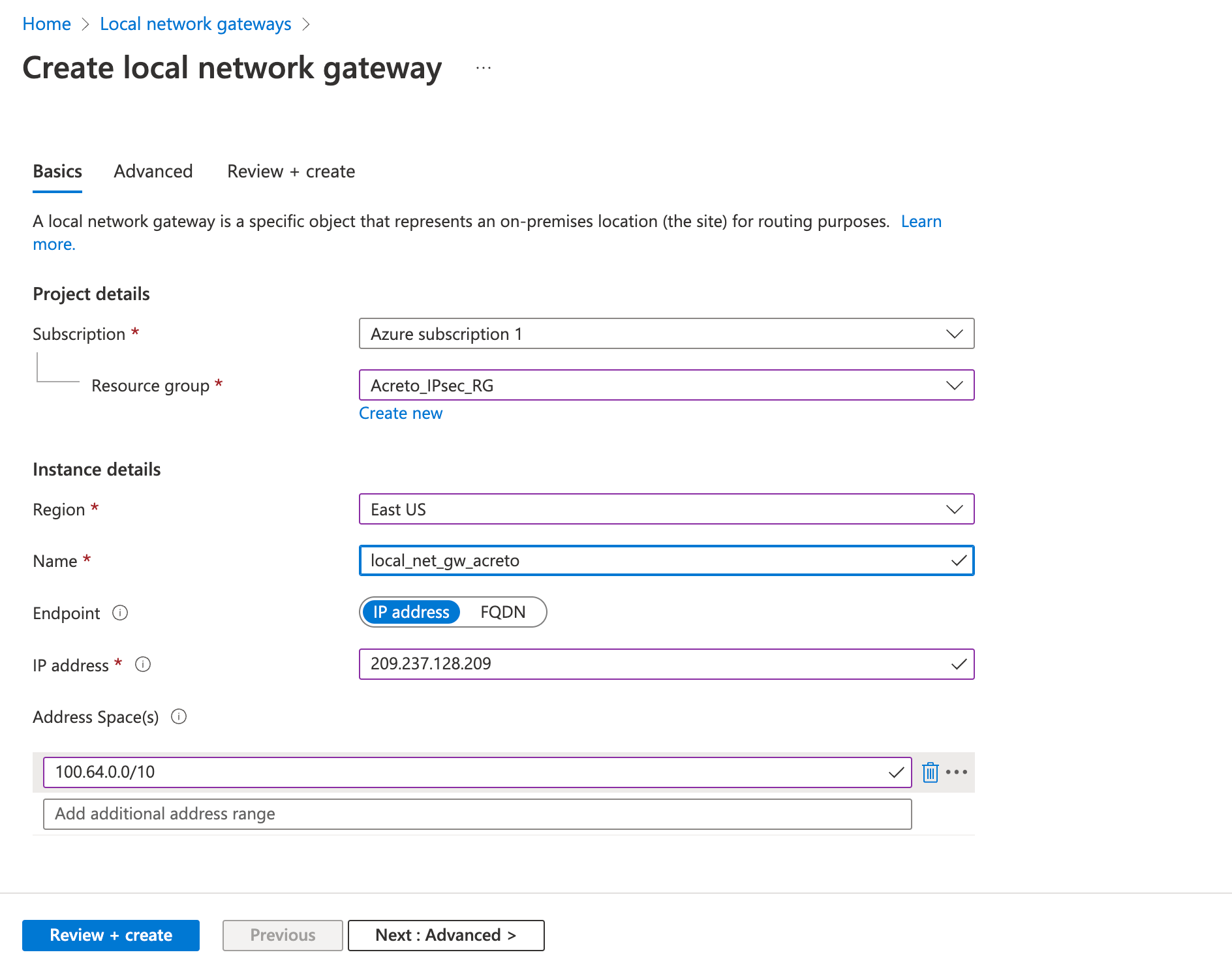

- Review the configurations and click Create
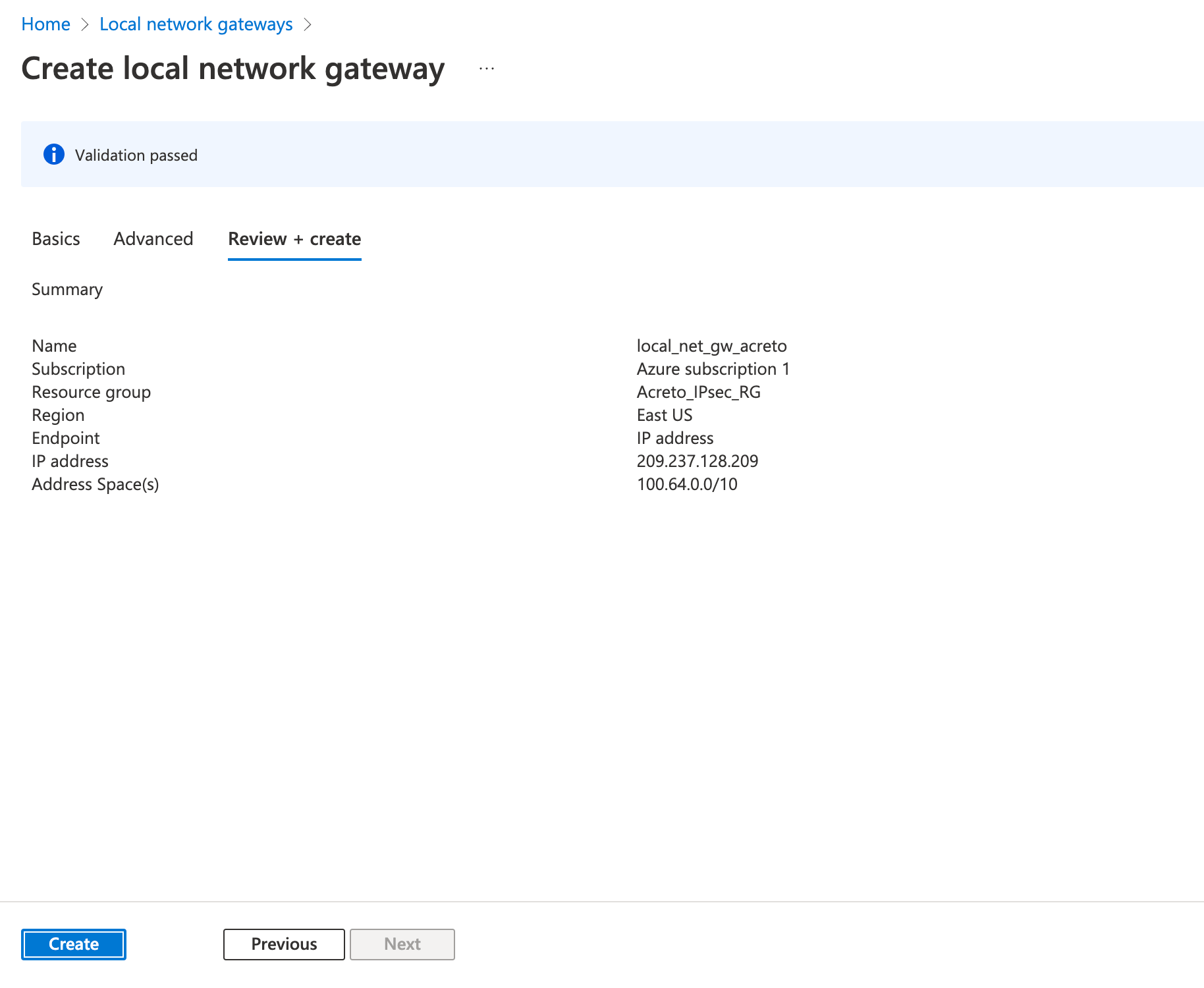

Step 4: Create a VPN connection
This step creates a Site-to-Site VPN connection between your VPN device and the virtual network gateway.
- Click on Create a resource
- In the search bar, search for Connection
- Click on Create.
- On the Basics tab, fill in the following fields:
- Connection type (Site-to-site)
- Subscription (select the same subscription as before)
- Resource group (select the same resource group as before)
- Location (select the same location as before)
- Click on Next
- On the Settings tab, fill in the following fields:
- Virtual network gateway (created in step 2)
- Local network gateway (created in step 3))
- Shared key (create a temporary password)
- Click on Next
- Click on Review + Create
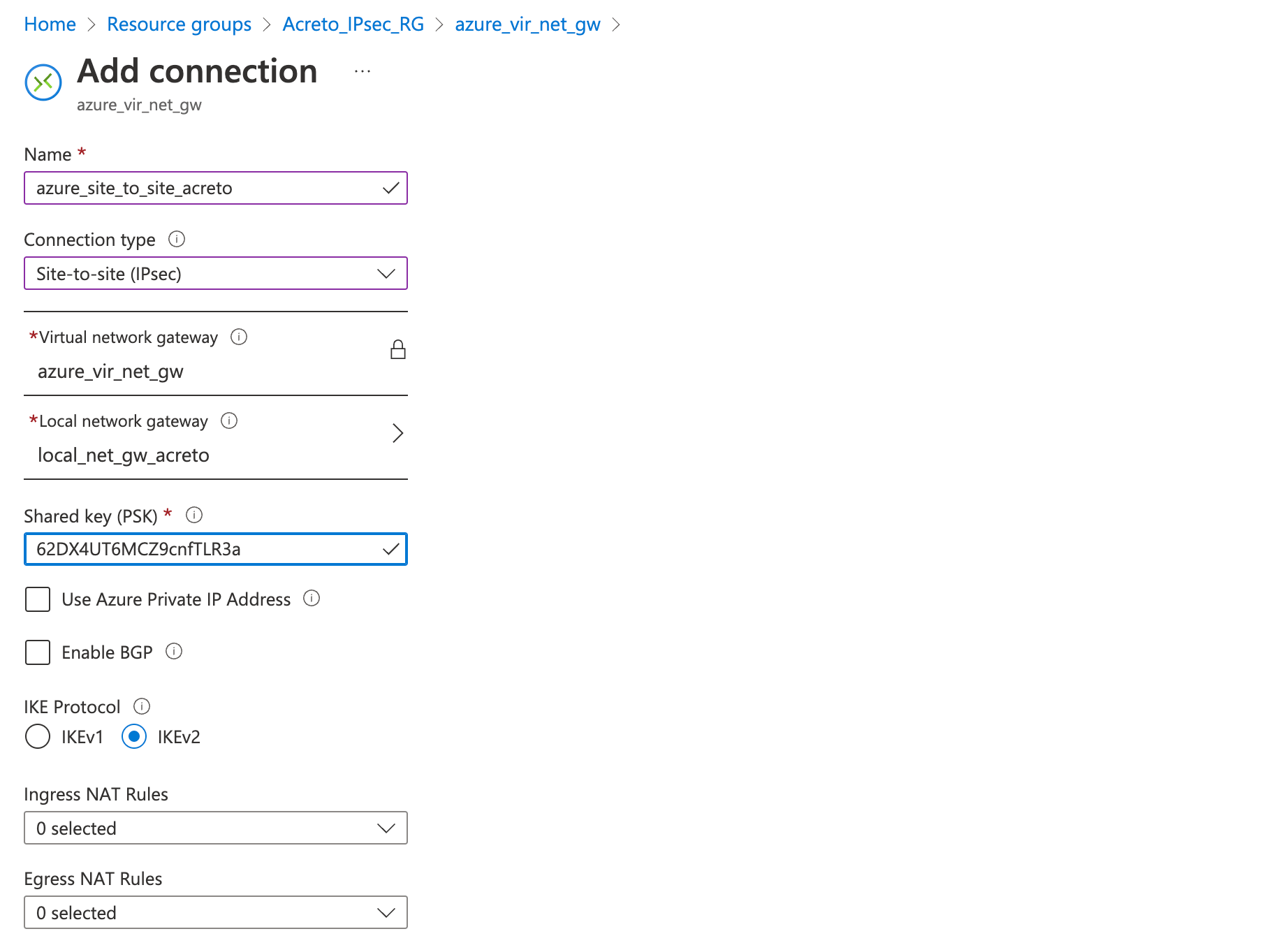

Wait for the deployment to finish and the connection created.
Step 5: Download strongswan configuration
Next, download the VPN configurations from Azure to use it to configure the Acreto gateway.
- Go to the VPN connection created in step 4.
- Click Overview from the left sidebar
- Click Download Configuration
- Select any Device vendor, Device family, and Firmware version of your choice.
- Click the button Download configuration

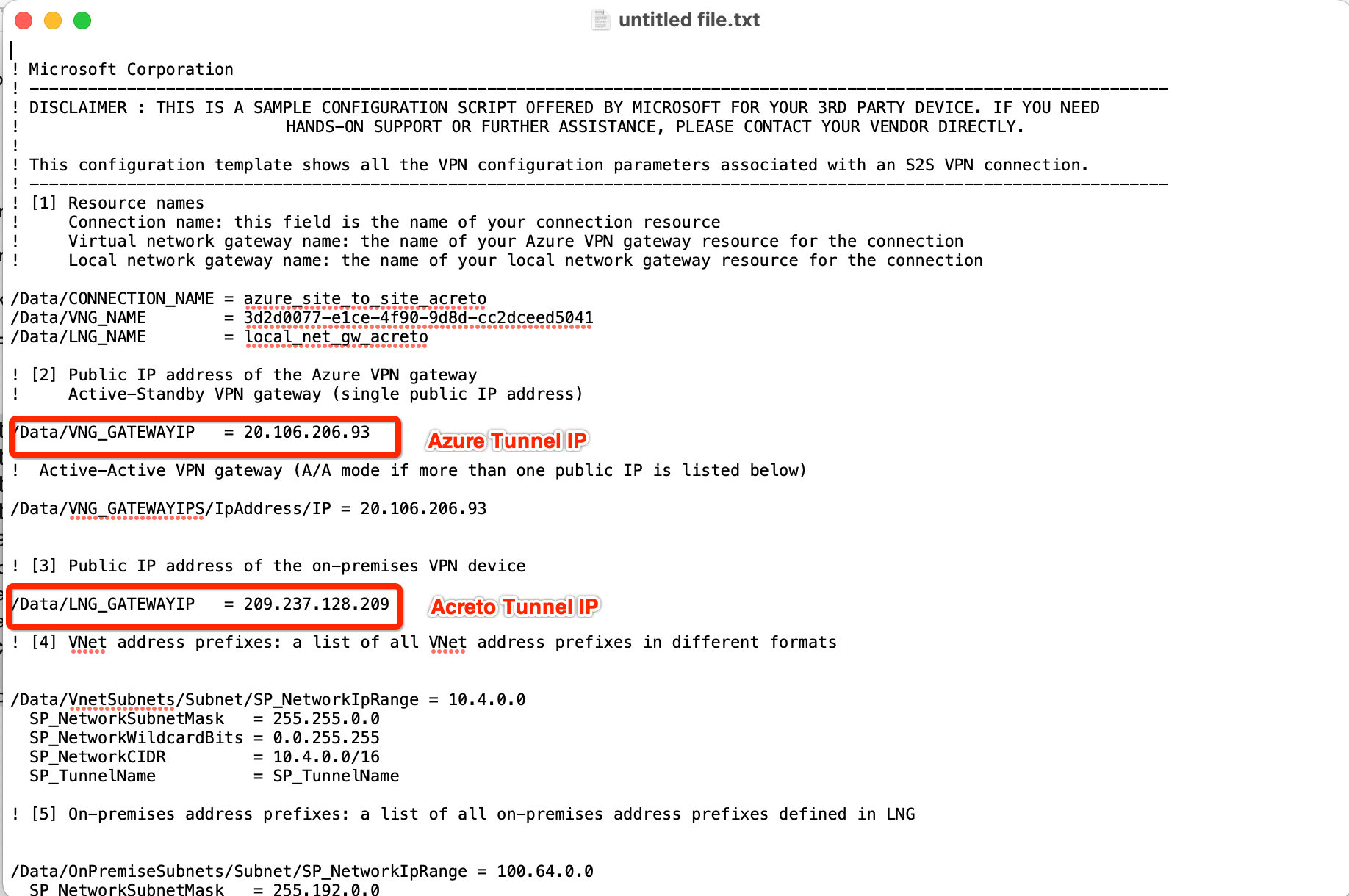
- Open the downloaded file and note the Azure VPN Gateway IP

Step 6: Create Gateway on Wedge with option AWS Site-to-Site IPsec and Azure Tunnel IP
Create Gateway on Ecosystem by following the instruction in the link. Provide the following values:
-
Goto Objects » Gateways
-
Add New Gateway
-
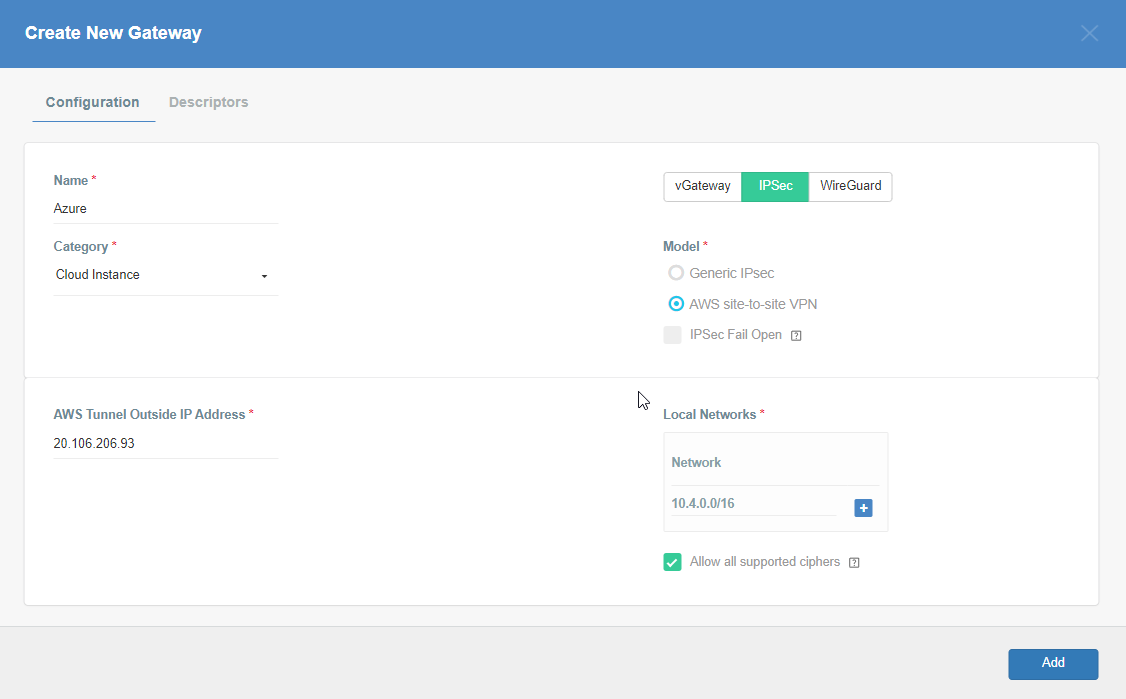
Provide the following information :
- Name: Azure
- Category: Cloud Instance
- Type: IPSec
- Model: AWS site-to-site VPN
- AWS Tunnel Outside IP Address: <Azure VPN gateway IP from Step 5>
- Local Network

Step 7: Read the Configuration
Read the PSK information from the Acreto gateway created in the previous steps.
- Click the gateway created on Acreto in Step 5.
- Click the Play button under Configuration Options to generate the strongSwan Config.
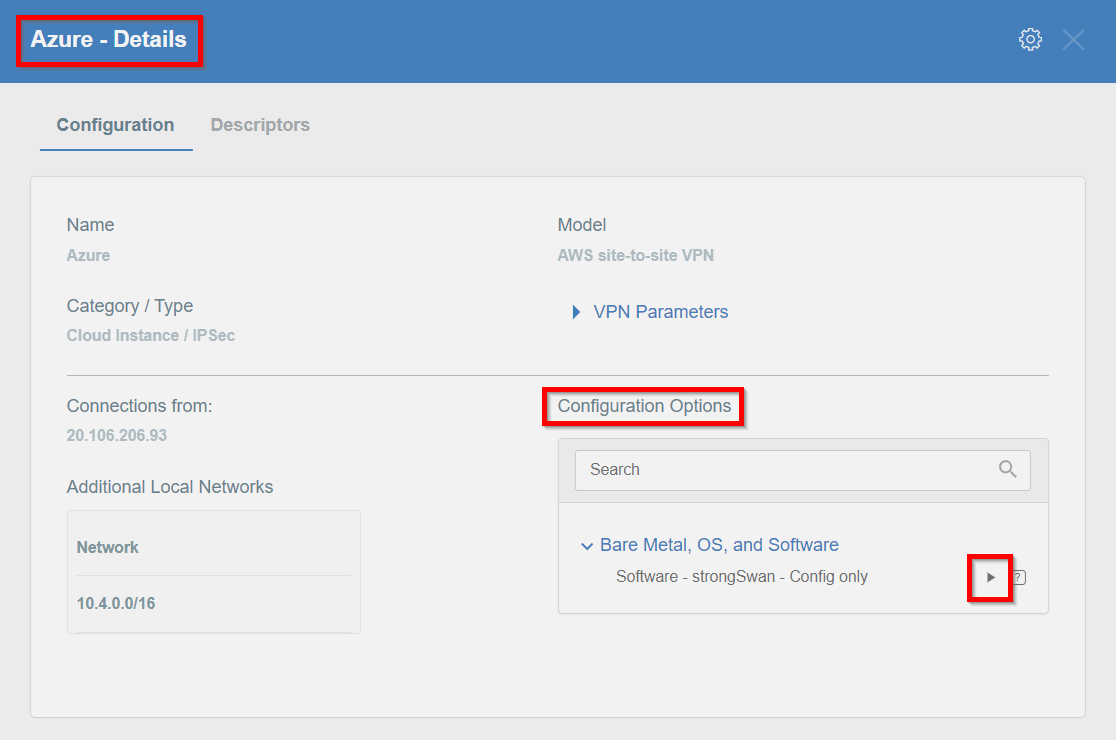

- Once the Config file is generated, click the Download button to download the configuration on the local computer.
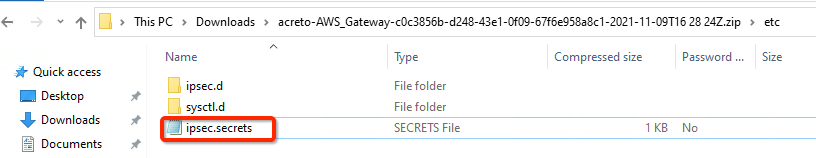

- Unzip the downloaded file and copy the PSK from the file ipsec.secrets

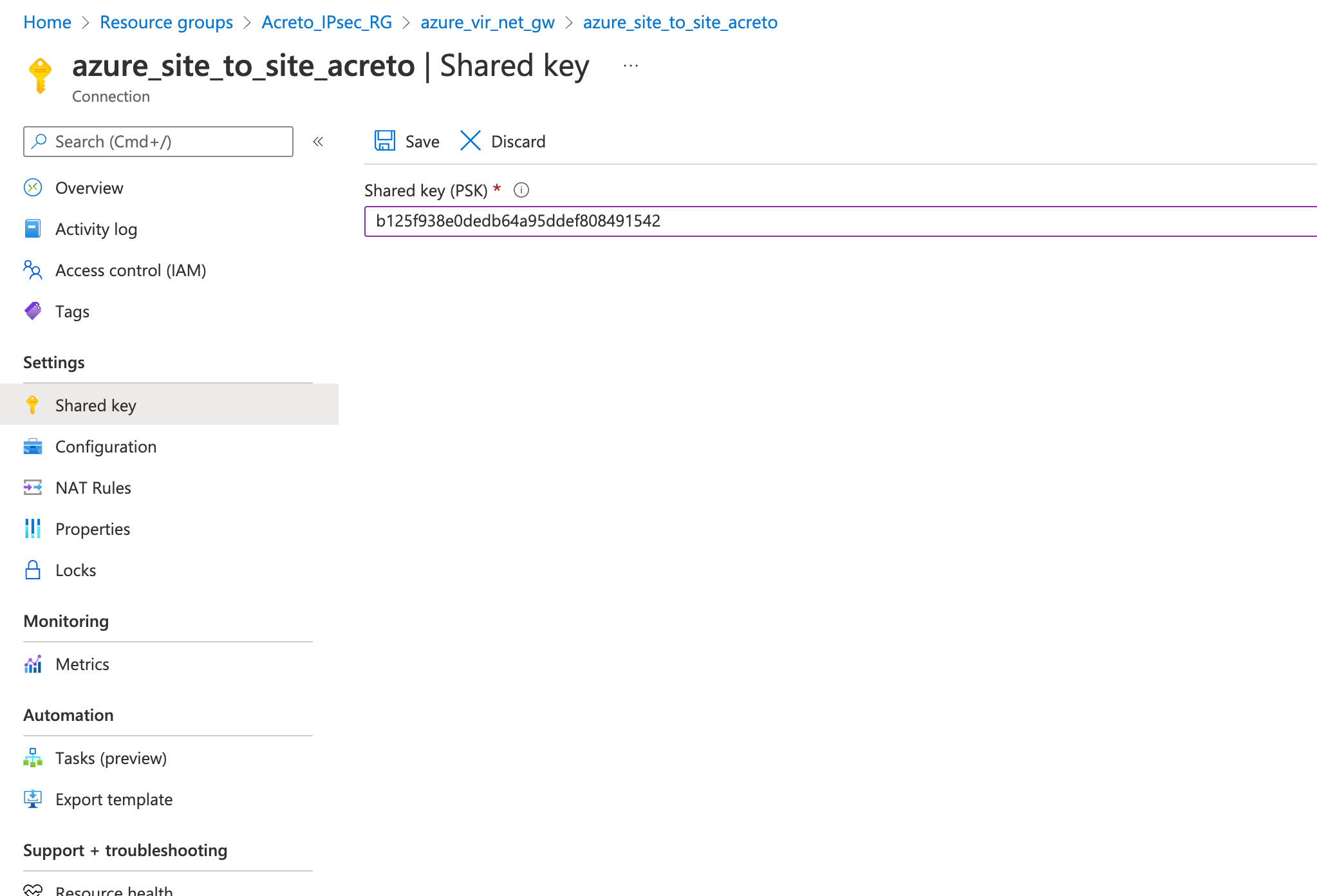
Step 8: Update the PSK from Wedge in Azure VPN
Update the new PSK from the previous step and update the VPN connection on Azure.
- Goto VPN connection created in step 4
- From the left sidebar, click Settings » Shared key
- Update the Shared key (PSK) from the Step 7
- Save

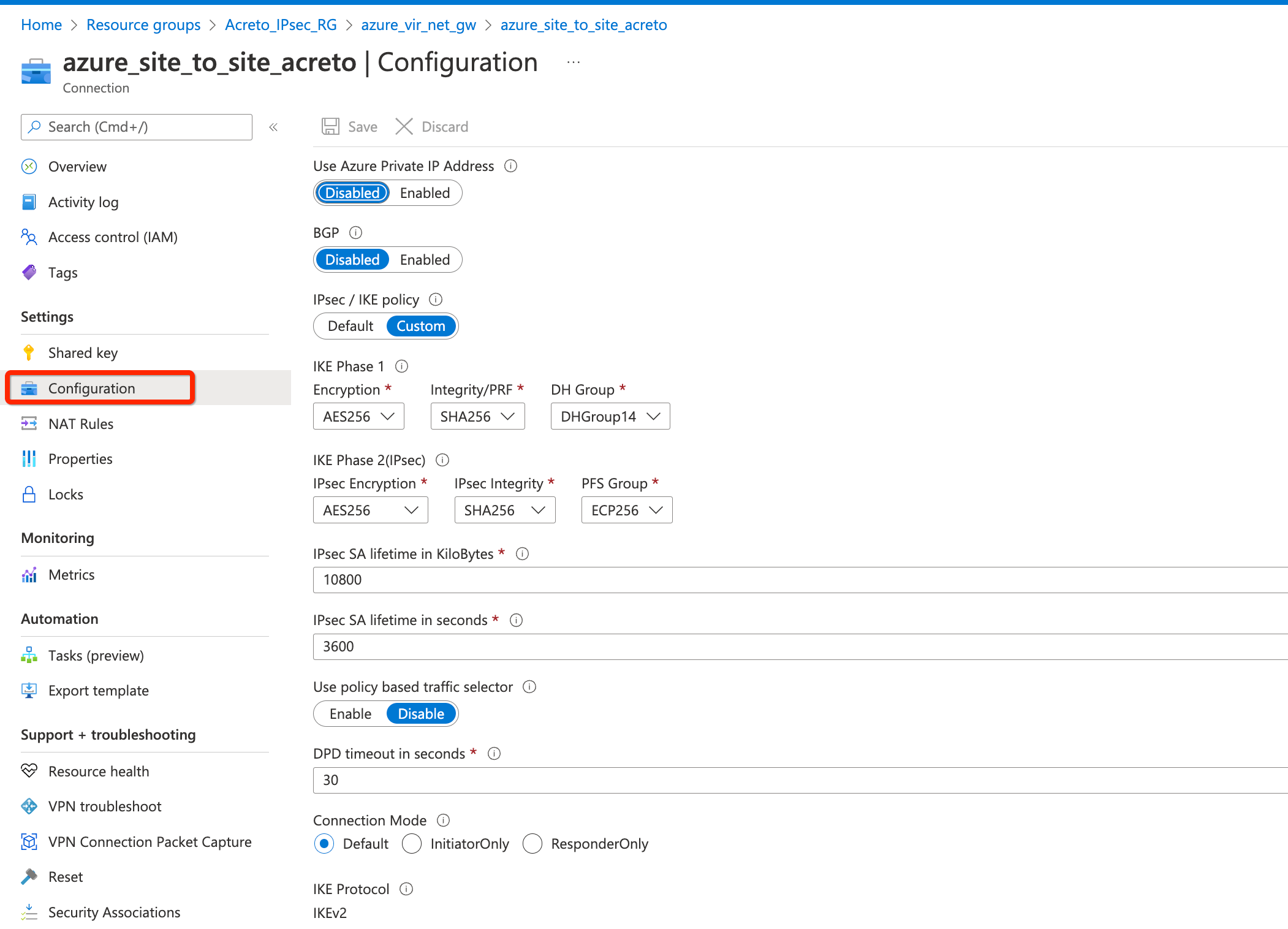
Step 9: Update IPsec Parameter
- Goto VPN connection created in step 4.
- From the left sidebar, click Settings » Configuration
- Update the following
- IPsec / IKE policy - Custom
- IKE Phase 1
- Encryption - AES256
- Integrity/PRF - SHA256
- DH Group - DHGroup14
- IKE Phase 2(IPsec)
- Encryption - AES256
- Integrity/PRF - SHA256
- DH Group - ECP256
- IPsec SA lifetime in seconds - 3600
- DPD timeout in seconds - 30
- Save.

Step 10: Check Connection
- Goto VPN connection created in step 4.
- From the left sidebar, click Settings » Connections
- Give a few minutes for changes to be effective.
- Once all the configurations are saved, the status of the VPN connection will be shown as Connected.


References and Related Articles
What is Azure Site-to-Site connection?
Summary
Acreto IPsec Gateway allows to set up VPN tunnel to connect Acreto Ecosystem with Azure VPN Gateway.
Connect to multiple VPCs in AWS using Transit Gateway
Before You Start
Overview
This article describes configuring a Route-Based Site-to-Site IPsec VPN between an Acreto Ecosystem and the Amazon Web Services (AWS) Transit Gateway to access multiple VPCs.
Network Diagram
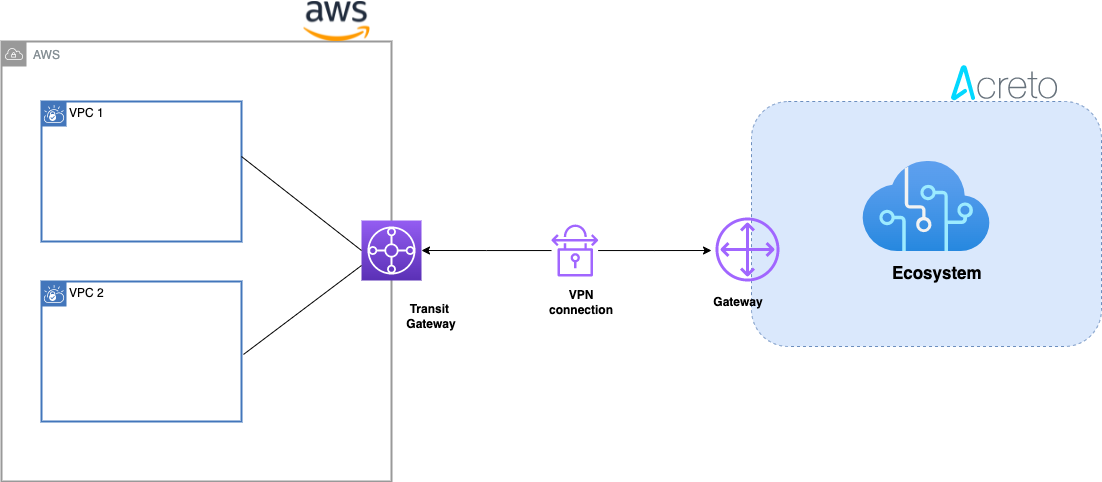

Concepts and Glossary
- IPsec VPN tunnel: An encrypted link where network traffic can pass between Acreto Ecosystem and AWS VPS.
- Customer gateway: An AWS resource that provides information to AWS about the Acreto IPsec Gateway object.
- Virtual private gateway: The VPN concentrator on the Amazon side of the Site-to-Site VPN connection.
Prerequisites
To setup an IPsec Site-to-Site VPN tunnel between Acreto Ecosystem and AWS VPS, you need:
- Access to Active Acreto Ecosystem
- Access to AWS Management Console
- Pre-configured VPC, subnets, route tables, NACL, and security groups
The Purpose of Site-to-Site IPsec VPN
Acreto, as a Cloud Provider, allows to connect and integrate multiple physical and virtual networks. All connections require stable and secure links. Virtual (EC2) Instances running on Amazon VPC can’t communicate securely with your own (remote) network by default. However, it is possible to connect your network to Acreto Ecosystem. Then, you can enable access to your remote network from your VPC by creating an AWS Site-to-Site VPN (Site-to-Site VPN) connection and configuring routing to pass traffic through the connection.
Acreto Ecosystem configures the routing automatically and passes the traffic between AWS VPC and your network. Additionally, the traffic is scanned by the Acreto Threat Engine to block suspicious traffic and malware.
How To
Use the following procedures to manually set up the AWS Site-to-Site VPN connection transit gateway on Amazon AWS.
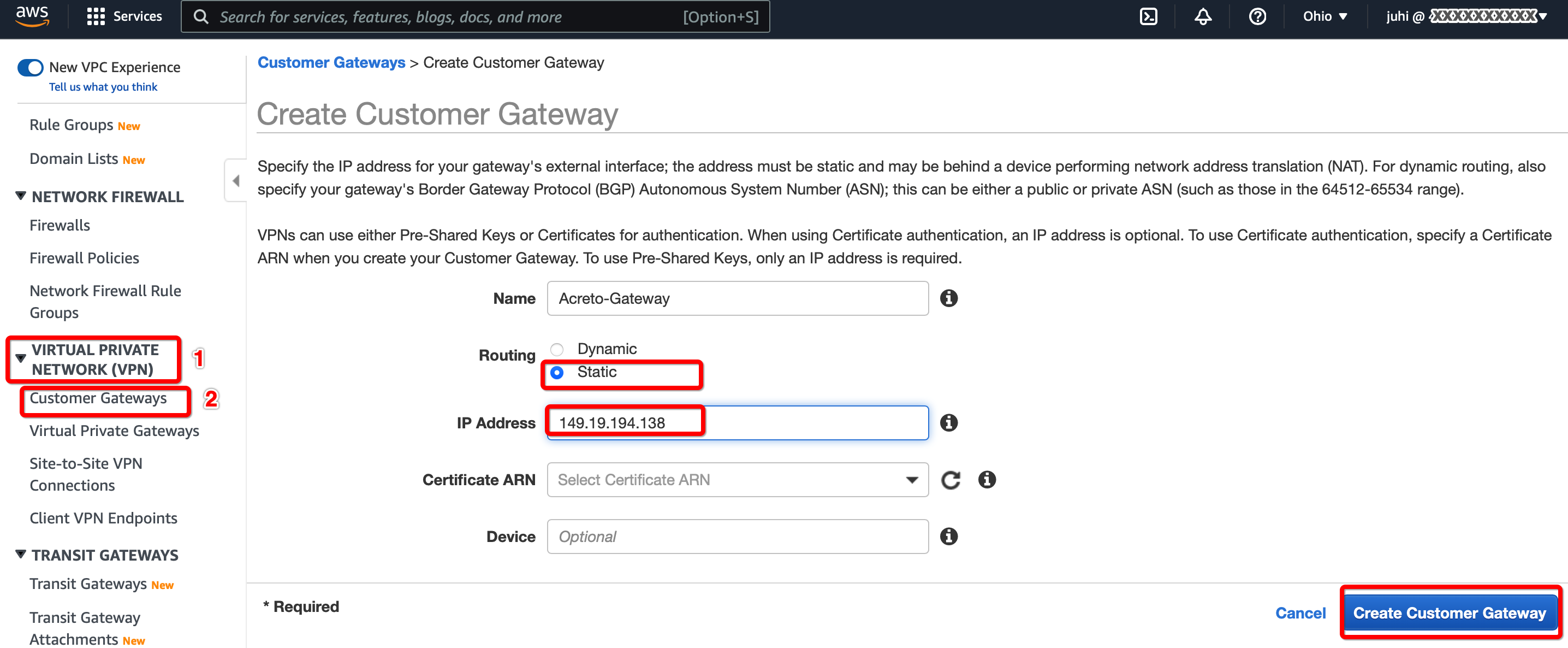
Step 1.1: Create Customer Gateway
Create a new Customer Gateway with Acreto’s public IP.
-
From the VPC Dashboard in the left sidebar, go to VIRTUAL PRIVATE NETWORK (VPN) » Customer Gateways
-
Click Create Customer Gateway
-
Provide the following values :
- Name: Acreto
- Routing: Static
- IP Address: Acreto’s Default Tunnel IP

-
Click Create Customer Gateway.

Step 1.2: Create Transit Gateway
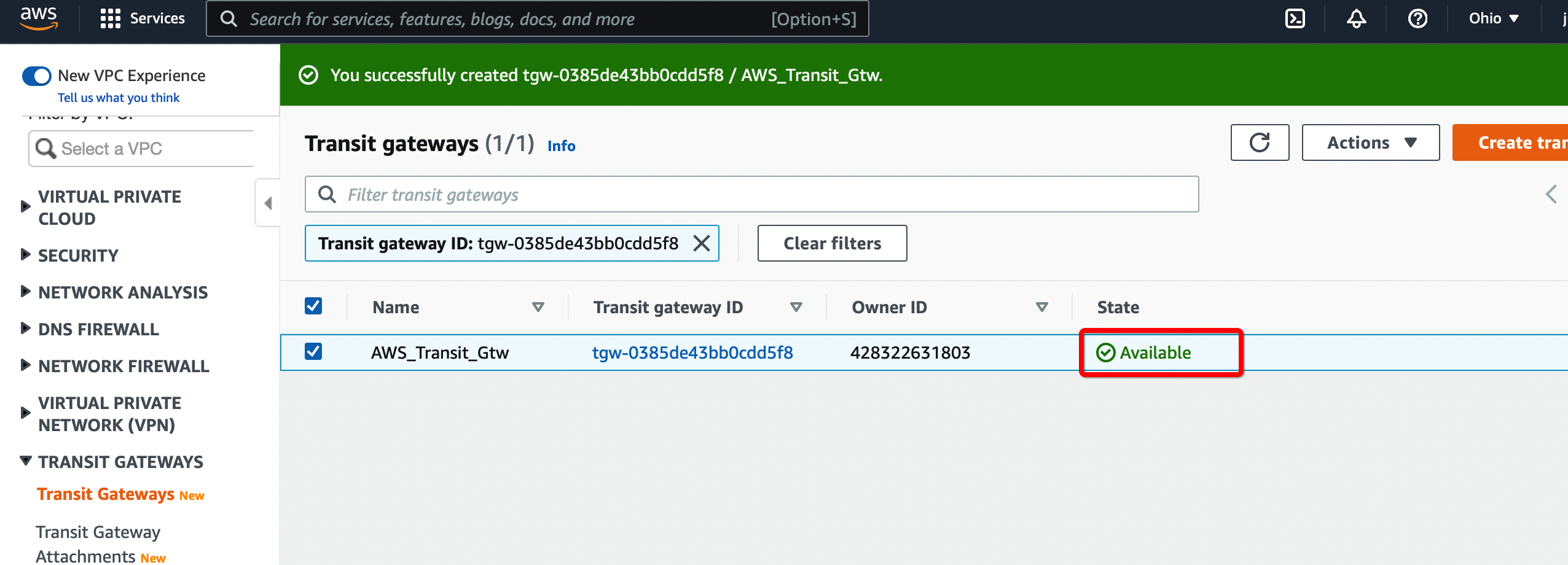
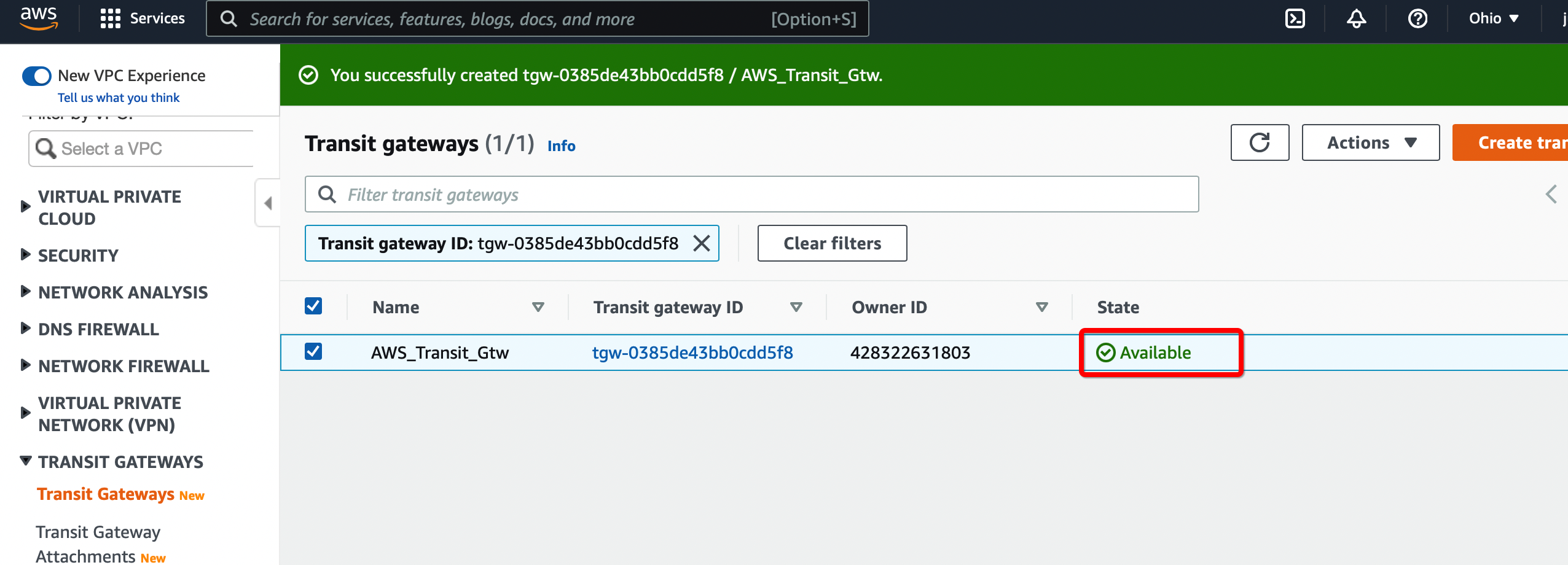
Create a Transit gateway that will be used to form the IPsec tunnel with Acreto.
-
From the VPC Dashboard in the left sidebar, go to TRANSIT GATEWAYS » Transit Gateways.
-
Click Create Transit Gateway.
-
Give the name and click Create Transit Gateway
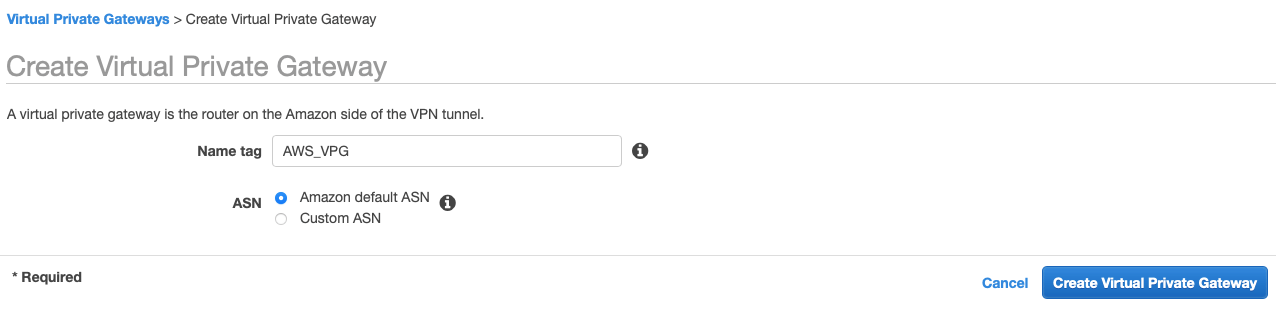

-
Wait for a few minutes to get the state of Transit Gateway to Available.

Step 1.3: Create Transit Gateway attachment
Create a Transit gateway attachment that will attach to the primary VPC.
-
From the VPC Dashboard in the left sidebar, go to TRANSIT GATEWAYS » Transit Gateways Attachment
-
Click Create Transit Gateway Attachment
-
Provide the following values
- Transit Gateway ID - Select the Transit gateway created in the previous step
- Attachment type - VPC
- VPC ID - Select the VPC
- Subnet IDs - Select the subnets that will communicate over the VPN

-
Click Create Transit Gateway attachment
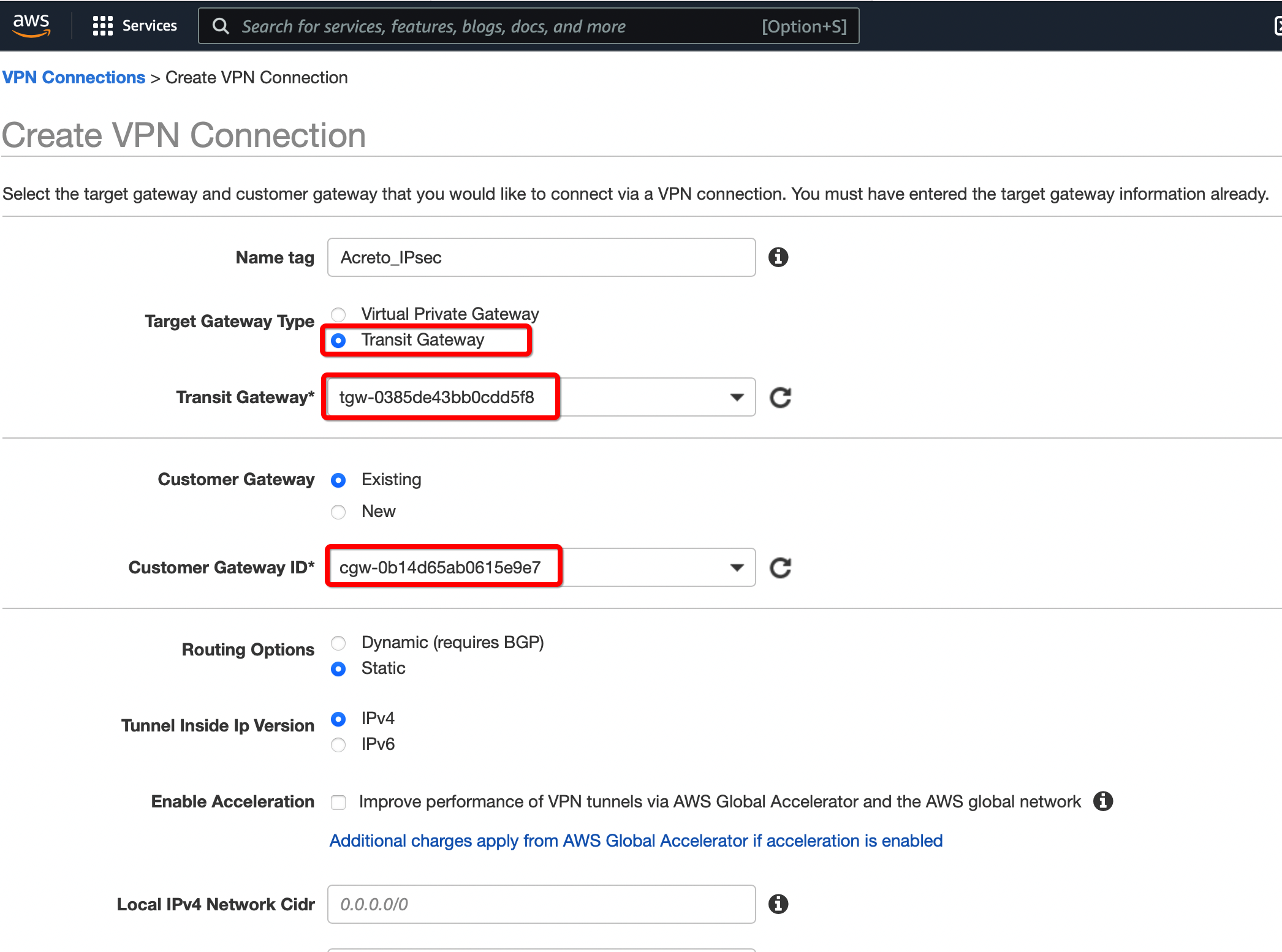
Create a new VPN connection and associate the previously created Virtual Gateway in Step 2 and Customer Gateway in Step 1.
-
From the VPC Dashboard in the left sidebar, go to VIRTUAL PRIVATE NETWORK (VPN) » Site-to-Site VPN Connections.
-
Click Create VPN Connection.
-
Provide the following values in the tunnel setting:
- Name: Acreto_ipsec
- Target Gateway Type: Transit Gateway
- Transit Gateway: Select the Transit gateway created Step 6
- Customer Gateway: Existing
- Customer Gateway ID: Select the Customer gateway created in Step 5
- Routing Options: Static
- Static IP Prefixes: 100.64.0.0/16

-
Click Create VPN Connection.
-
Select the VPN created and click the tab Tunnel Details. Copy the Outside IP address of the tunnel to form a VPN with Acreto.
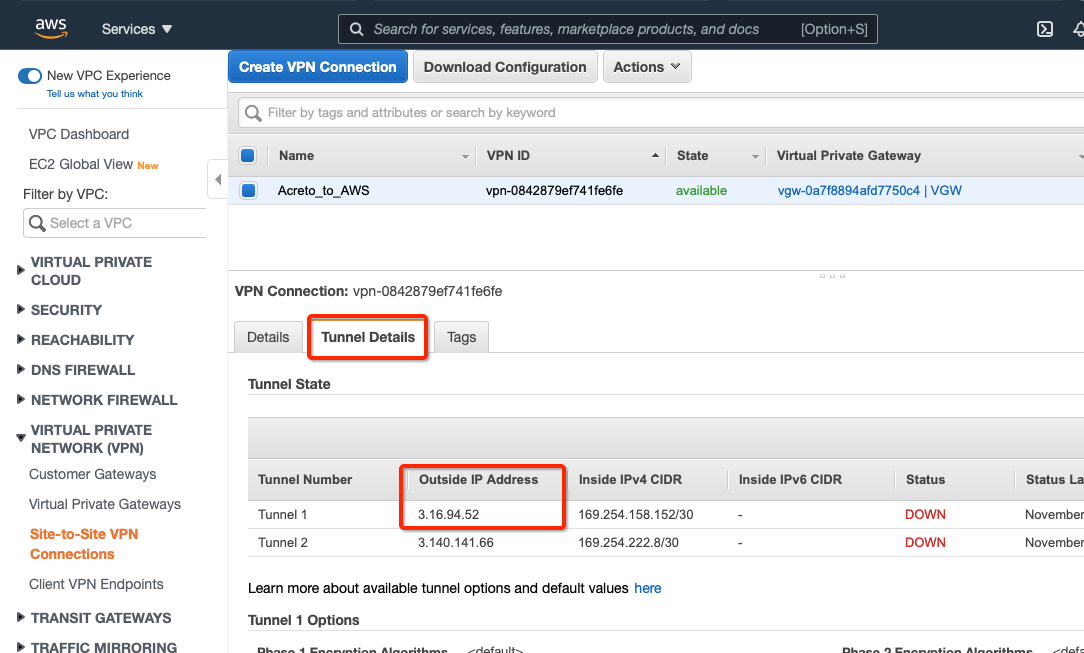

This Outside IP address will be used in the next steps to configure the Acreto gateway on Wedge Ecosystem.
Step 1.5: Create Acreto Gateway for IPsec
Create Gateway on Ecosystem by following the instructions in the link. Provide the following values:
- Type: IPsec
- Category: Data Center
- Model: AWS site-to-site VPN
- Connections from: AWS Tunnel’s Outside IP address
- Local network: local_network
- Save and Commit the changes.

Step 1.6: Read the Configuration
-
Click the gateway created on the Wedge.
-
Click the Play button under Configuration Options to generate the strongSwan Config.
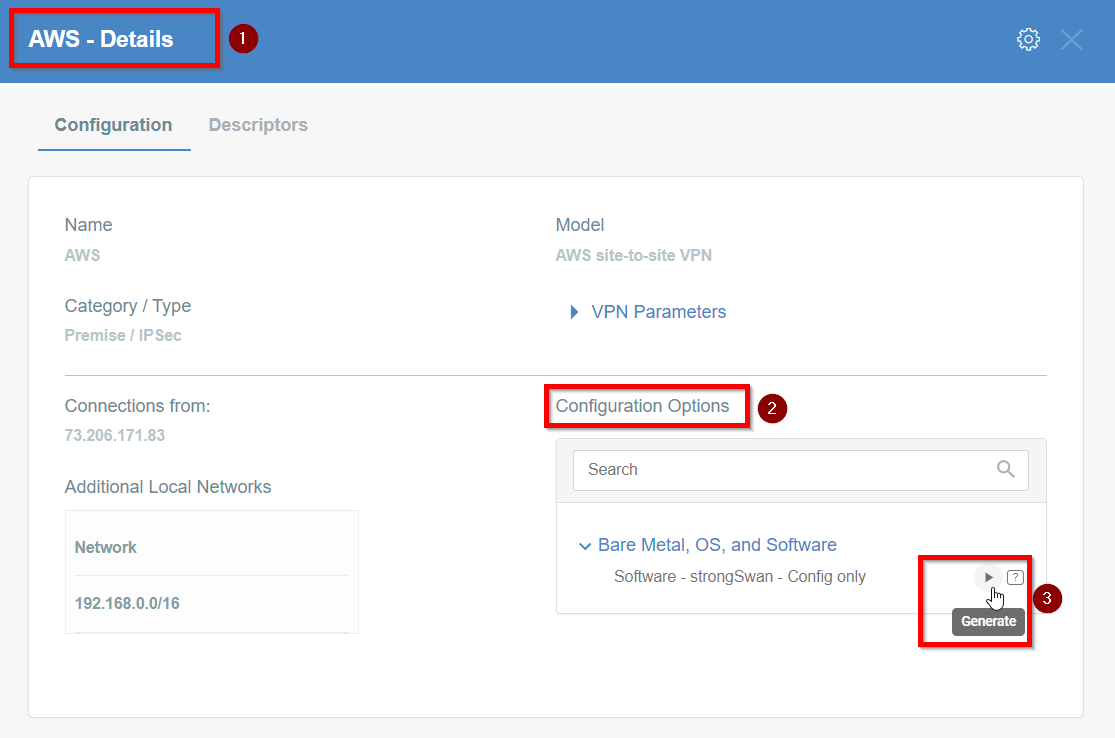

-
Once the Config file is generated, click the Download button to download the configuration on the local computer.

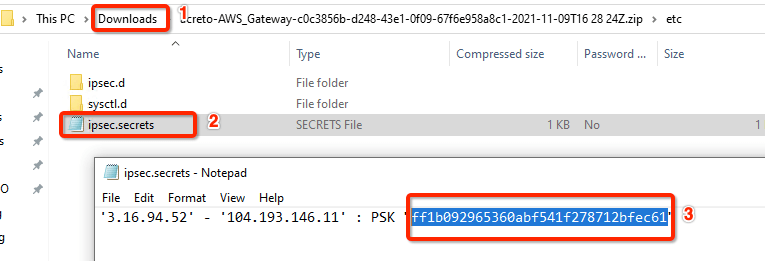
-
Unzip the downloaded file and copy the PSK from the file ipsec.secrets

Step 1.7: Update AWS VPN tunnel configuration
-
Goto AWS Site-to-Site VPN connections
-
Select the VPN and click Actions » Modify VPN Tunnel Option
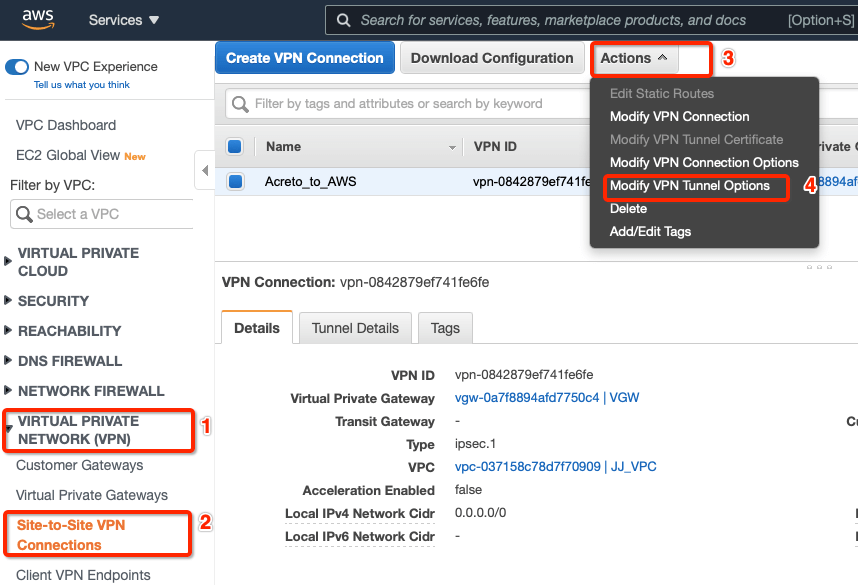

-
Select the tunnel used to create the VPN with Acreto.
-
Update the password copied from the ipsec.secrets file from strongSwan config file downloaded from Wedge
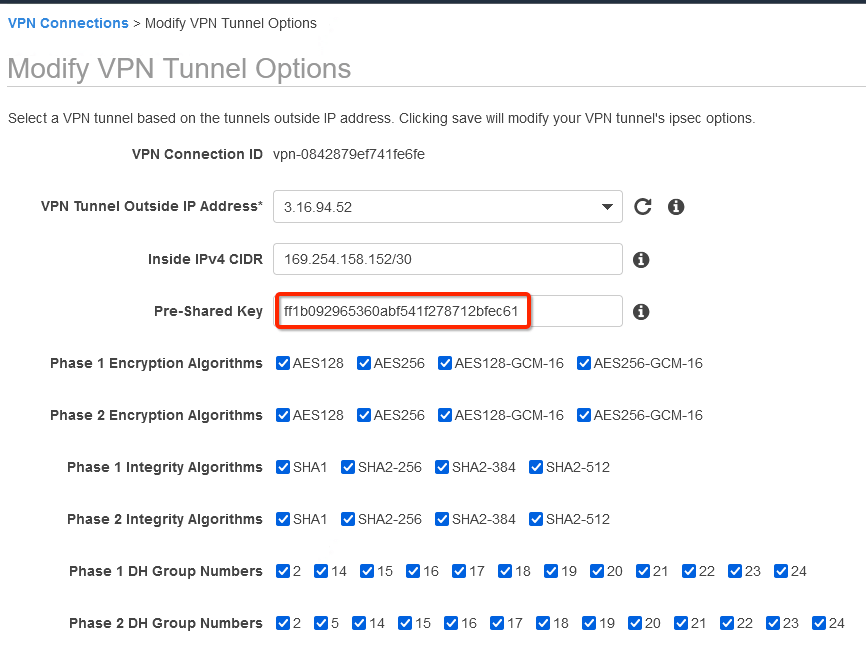

-
In the same window “Modify VPN Tunnel Options” scroll down and select the following action under tunnel configuration:
- DPD Timeout Action: Restart
- Startup Action: Start
-
Click Save
Step 1.8: Update the Transit Gateway Route Table
Configure the Route table to set the default route to the VPN tunnel.
-
From the VPC Dashboard, click Transit Gateway Route Table under TRANSIT GATEWAYS in the left sidebar
-
Select the Transit gateway Route table entry.
-
Select tab Routes and click Create Static Route
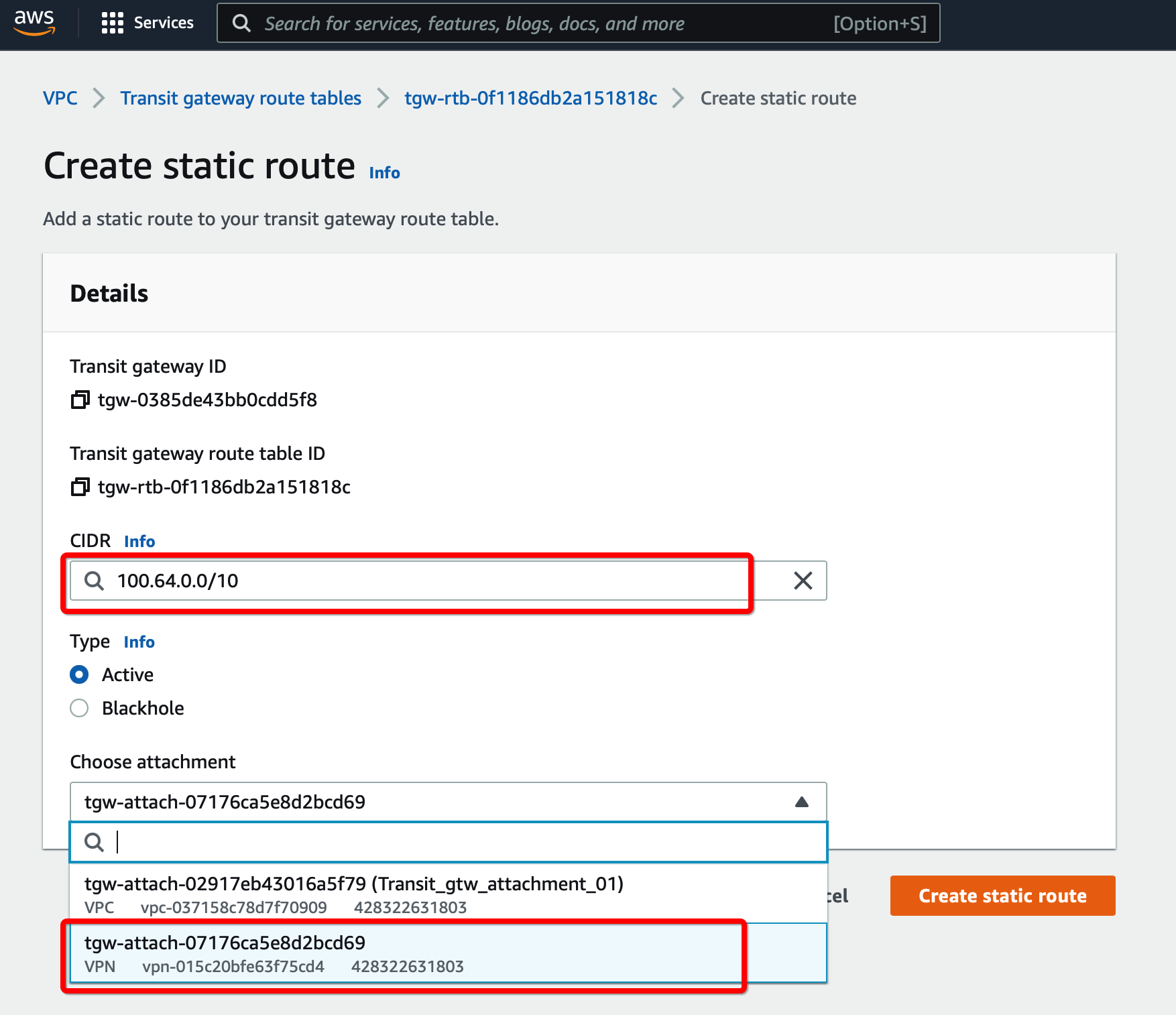

-
Click Create Static Route
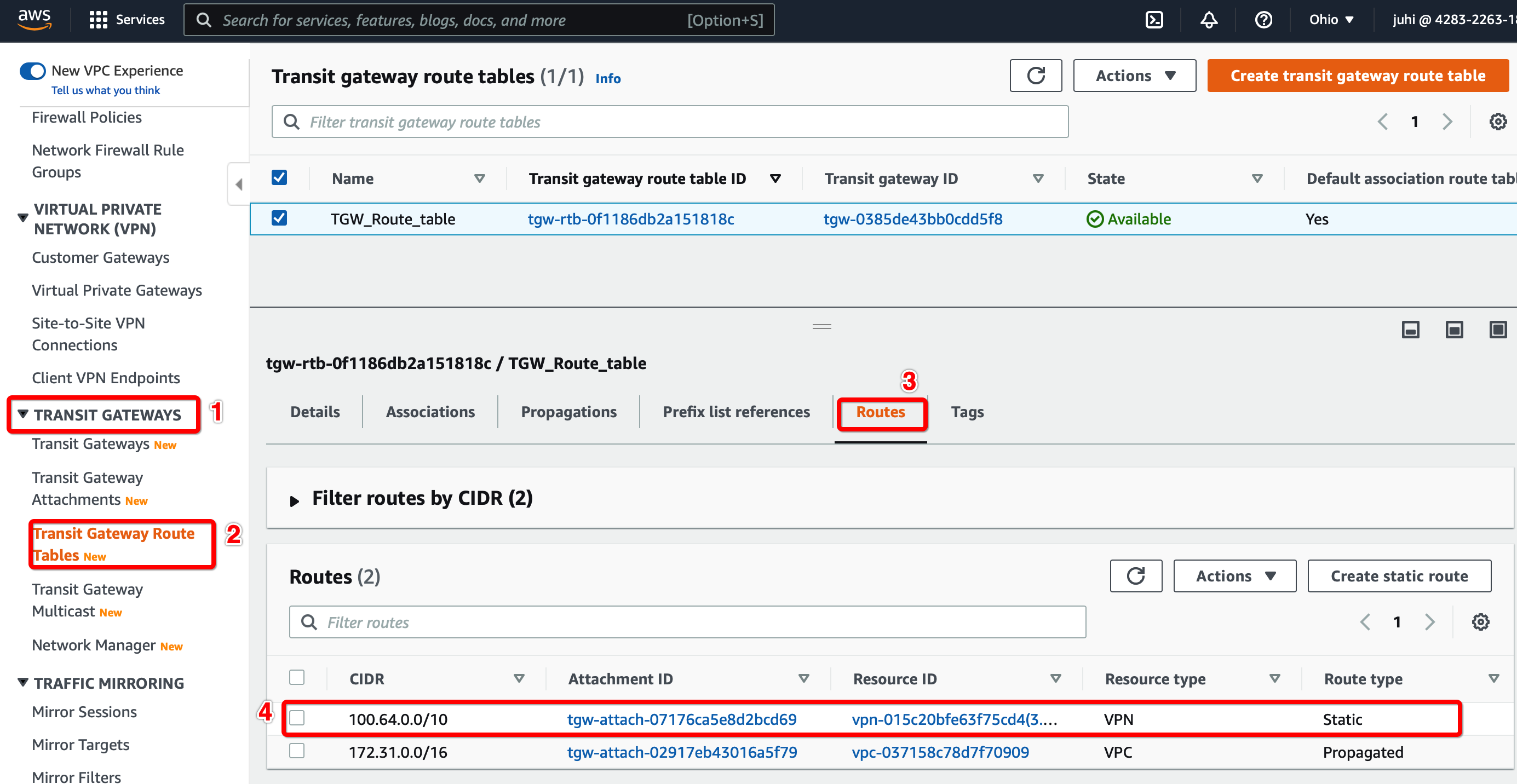

Step 1.9: Update Route the Table for the Subnet
-
From the VPC Dashboard, click Route Tables under VIRTUAL PRIVATE CLOUD in the left sidebar
-
Select the Route table and click Edit routes. Add the following values :
- CIDR - 100.64.0.0/16
- Attachment - Select the Transit VPN attachment id
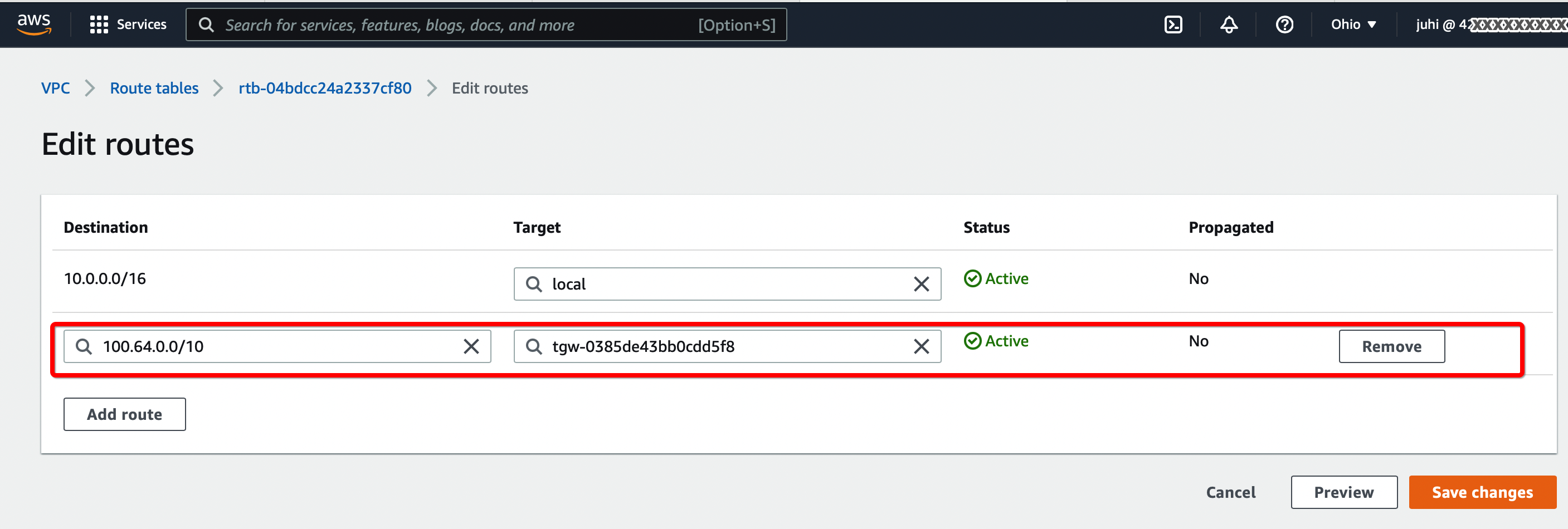

-
Click Save changes.
Attach Secondary VPC in the same account to the Transit Gateway
Step 2.1: Create Transit Gateway attachment for Secondary VPC
to TRANSIT GATEWAYS » Transit Gateways Attachment
-
Click Create Transit Gateway Attachment
-
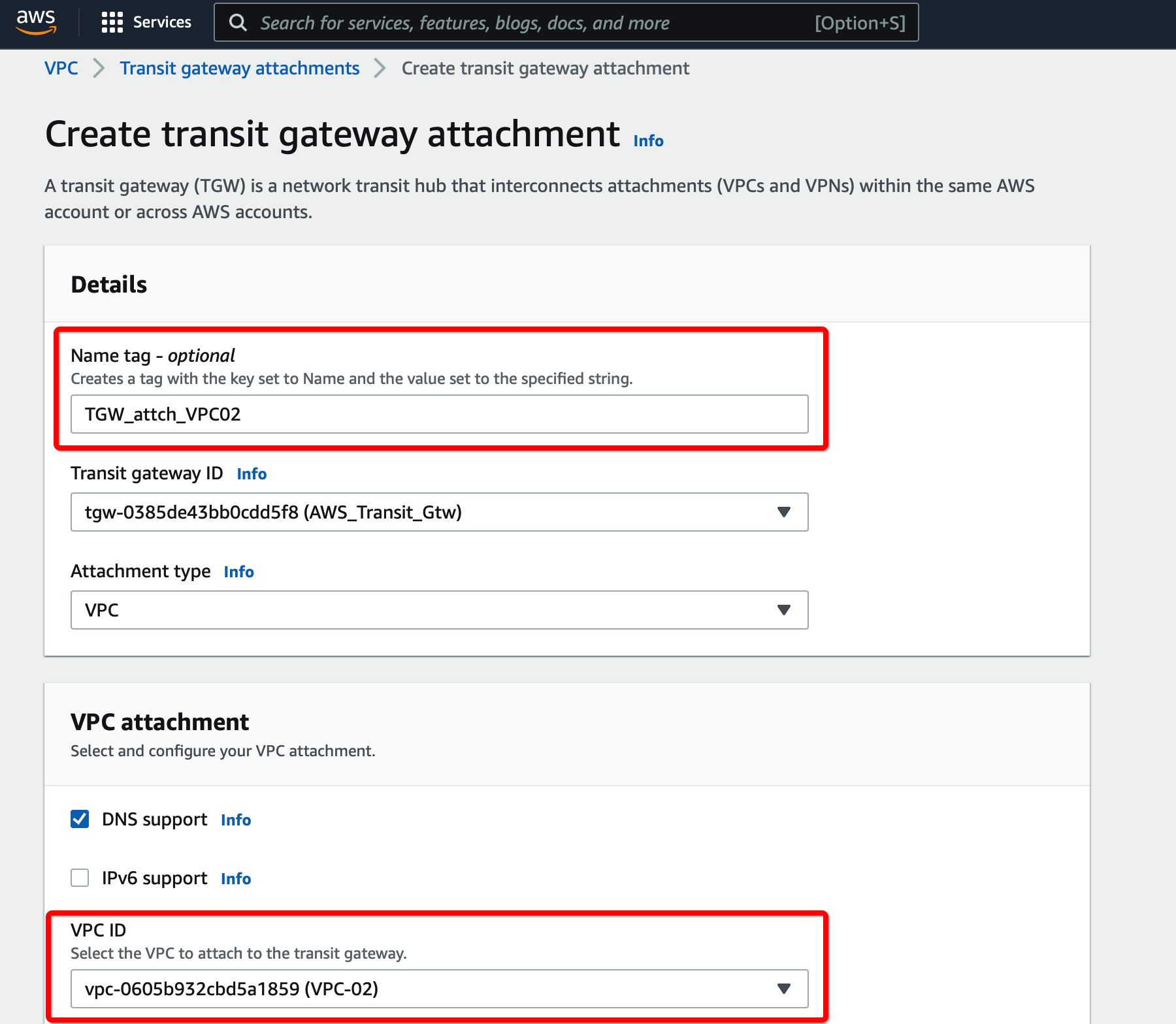
Provide the following values
- Transit Gateway ID - Select the Transit gateway created in step 6
- Attachment type - VPC
- VPC ID - Select the new VPC
- Subnet IDs - Select the subnets that will communicate over the VPN
 .
.
-
Click Create Transit Gateway attachment
Step 2.2: Verify the routes from the new VPC Transit Gateway attachment is available on the Transit Gateway Route table.
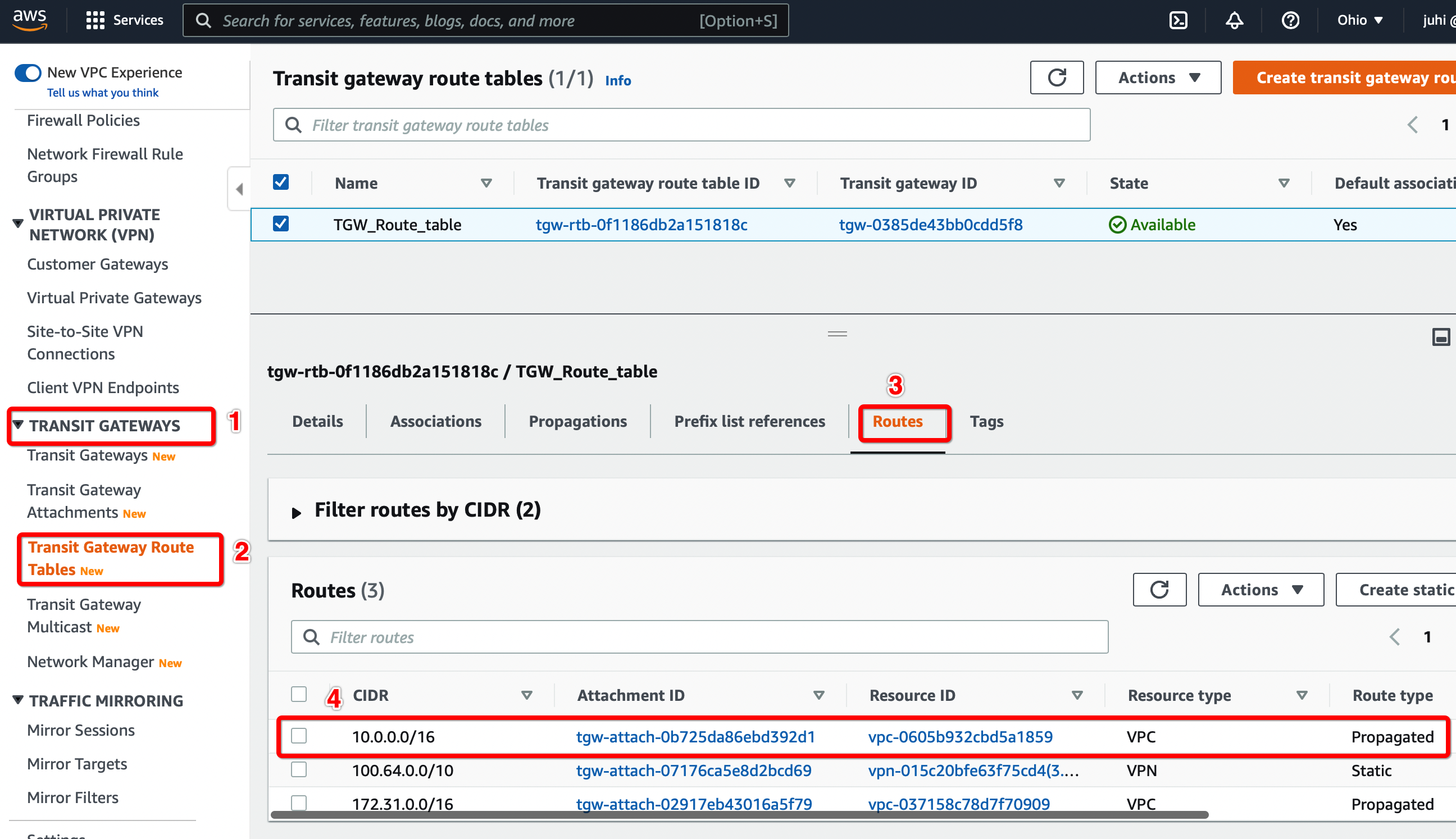
Configure Routes from the new VPC transit gateway attachment appears in the Transit Gateway Route table.
-
From the VPC Dashboard, click Transit Gateway Route Table under TRANSIT GATEWAYS in the left sidebar
-
Select the Transit gateway Route table entry.
-
Select tab Routes
-
Check the Static route from the new VPC Transit Gateway attachment is available

Step 2.3: Update the routes for the Subnet in Secondary VPC
Follow Step 1.9 to add the route for Acreto subnet 100.64.0.0/16 through the transit gateway.


Verify the connections
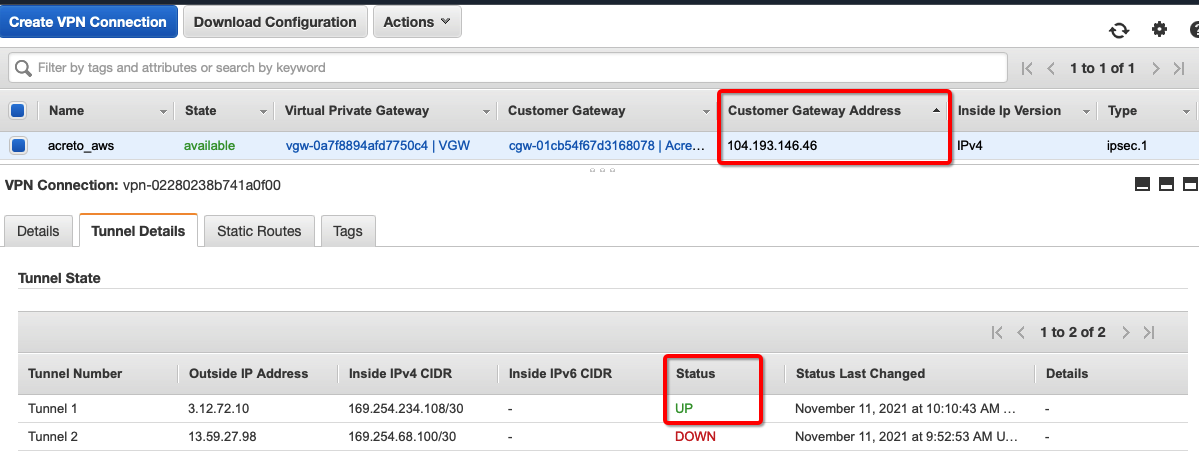
Once the tunnel connection is successfully established, the status of the connection will be up.
-
To verify on AWS, navigate to the VPN created under VIRTUAL PRIVATE NETWORK (VPN) » Site-to-Site VPN Connections. Verify the following:

-
Connect a Remote user with the Acreto Connect Client and access the resources in the VPC connected using Transit Gateway.


References and Related Articles
Summary
Acreto Gateway allows setting up an IPsec VPN tunnel with AWS Transit Gateway, which can be used to access resources in multiple VPCs.
Fortinet FortiGate Dual VPN setup
Before You Start
Overview
This article illustrates a Dual VPN setup and explains how to connect the secondary tunnel from your environment to the second Ecosystem which can act as a backup in case of failure of the Primary ISP or Ecosystem. With this setup, when the first tunnel is down, the traffic will automatically start going through the second tunnel to the backup Ecosystem.
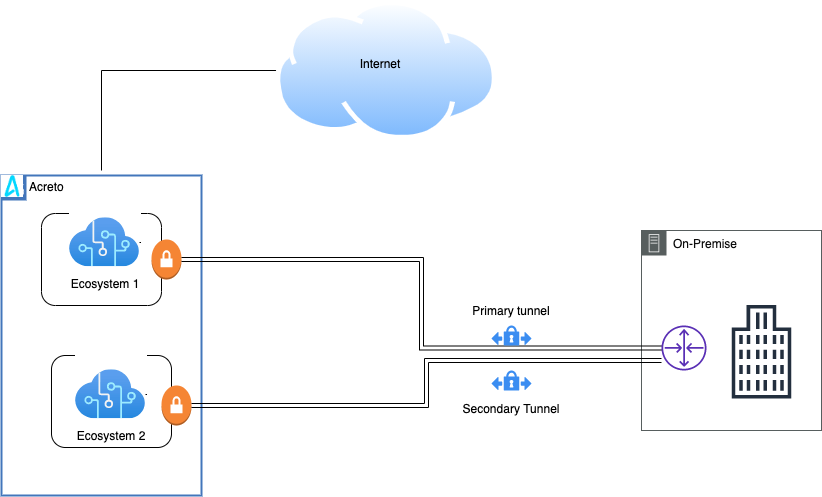

Prerequisites
- FortiGate installation
- Ecosystem set up with proper security policies
How-To
Create Gateway for IPsec
Firstly, you will need to create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
- Name: IPsec connection name must meet the same requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed through this gateway.


Info
To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow you to test connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
Task 1: Read IPsec Gateway Values Required for FortiGate Configuration
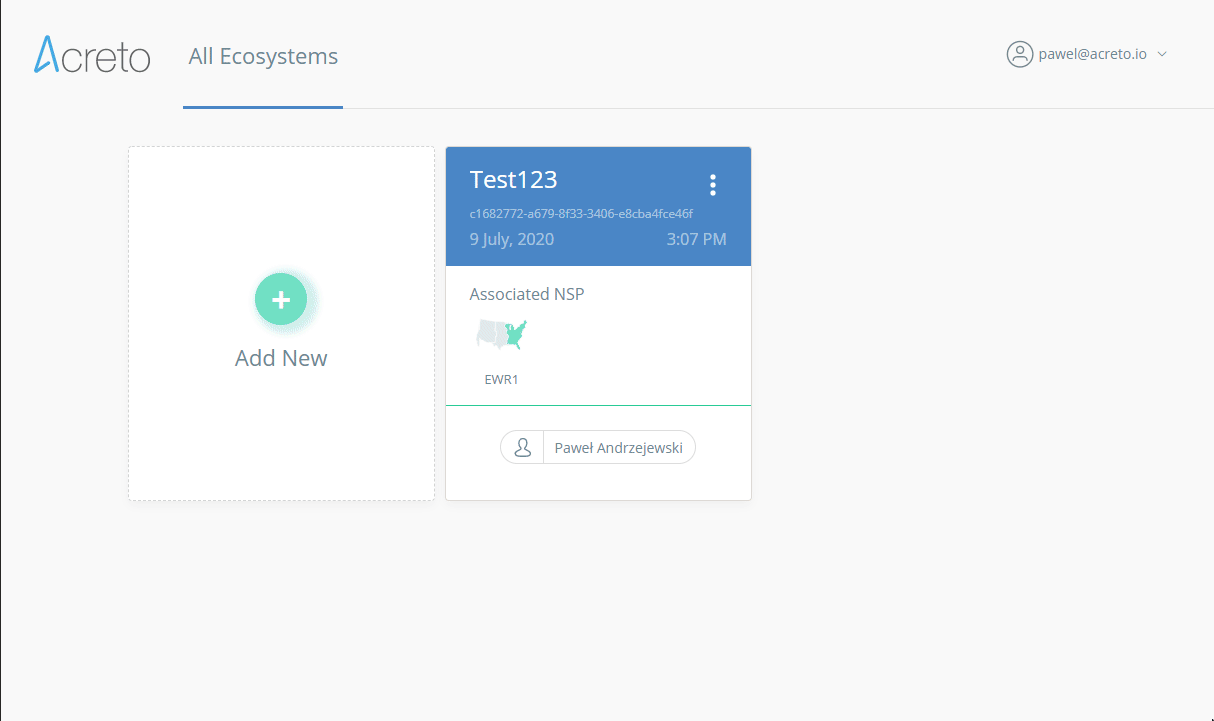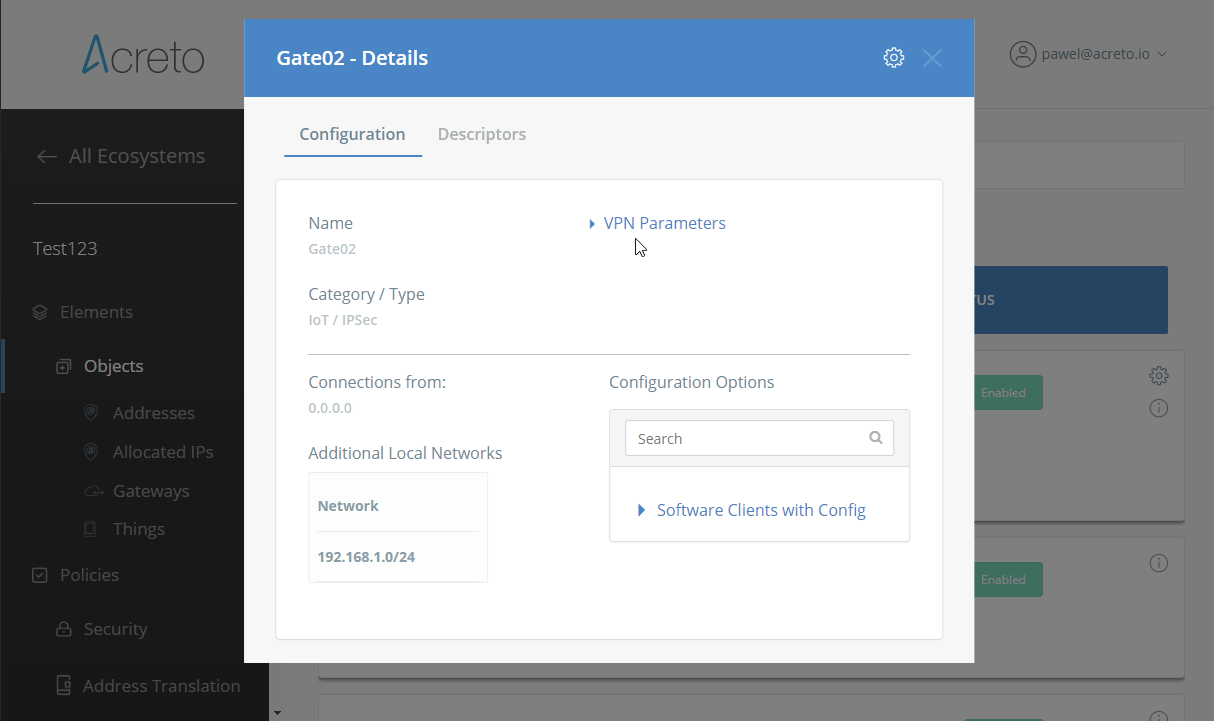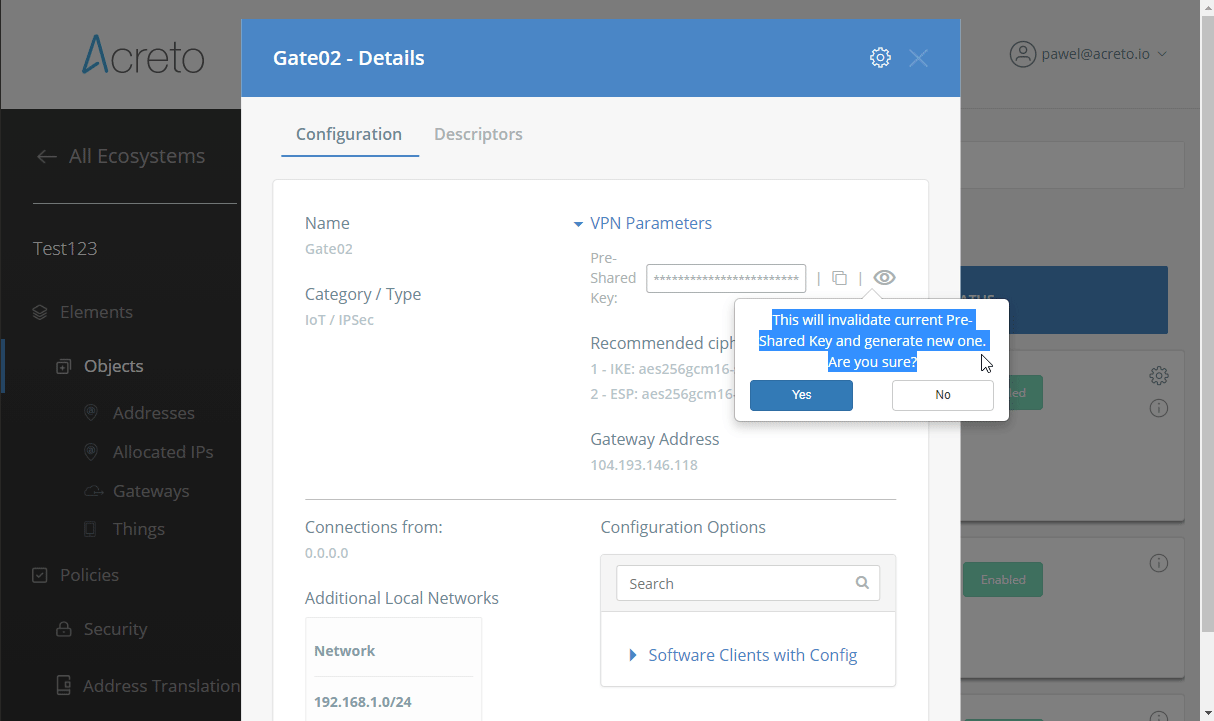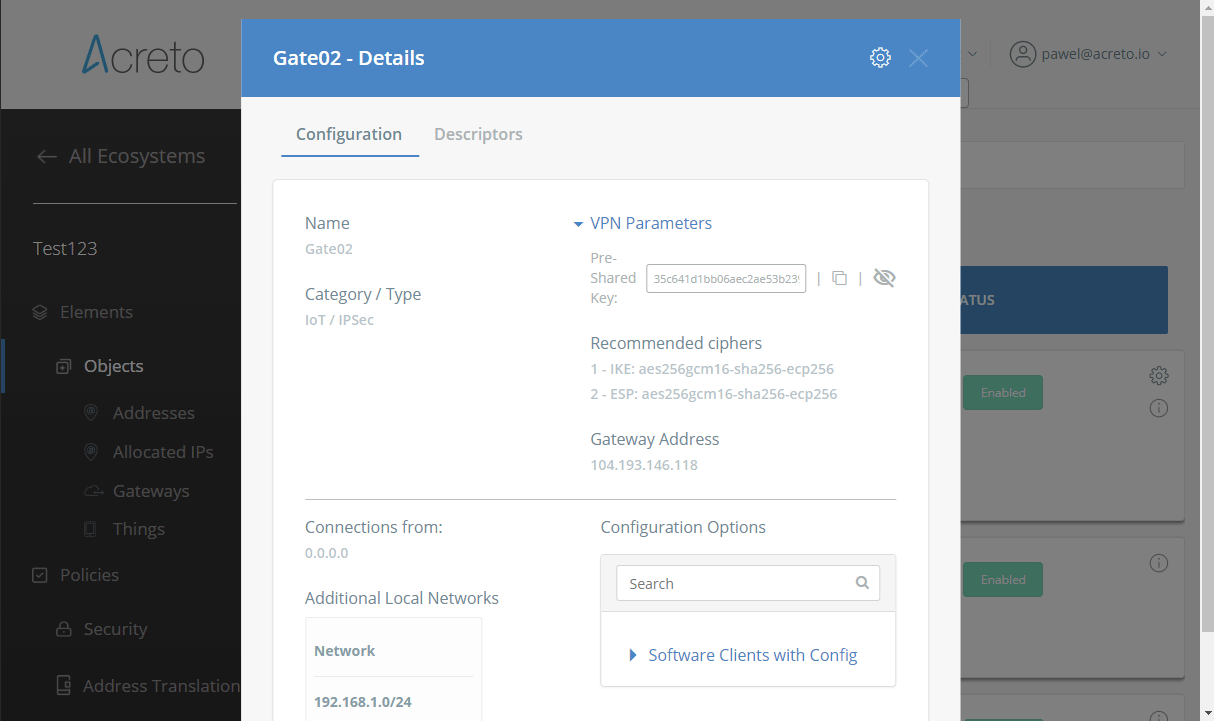
To proceed with the FortiGate configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All of these may be found within the Gateway details panel - view the below animation for further instruction.
- In FortiGate, go to VPN > IPsec Tunnels. From Create New drop-down menu, select IPsec Tunnel
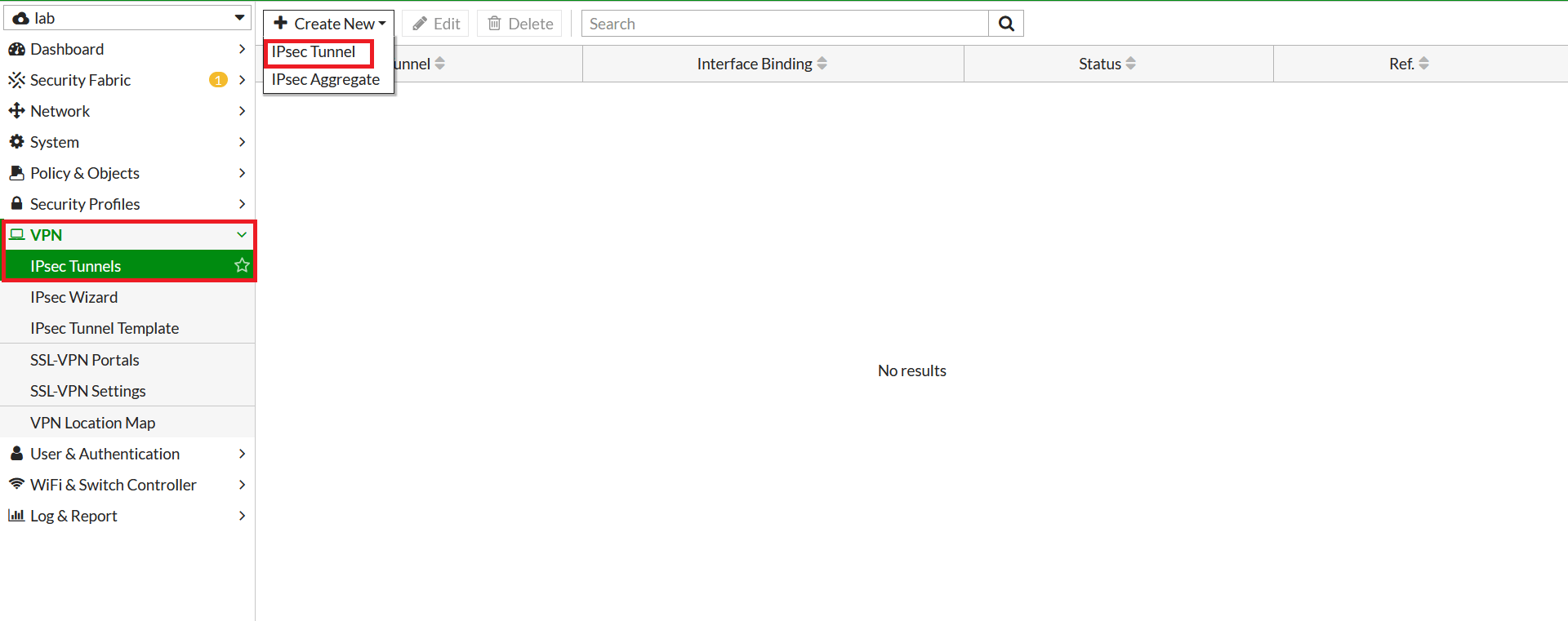

- In the next window, give the primary tunnel name and click on Custom and click on Next.
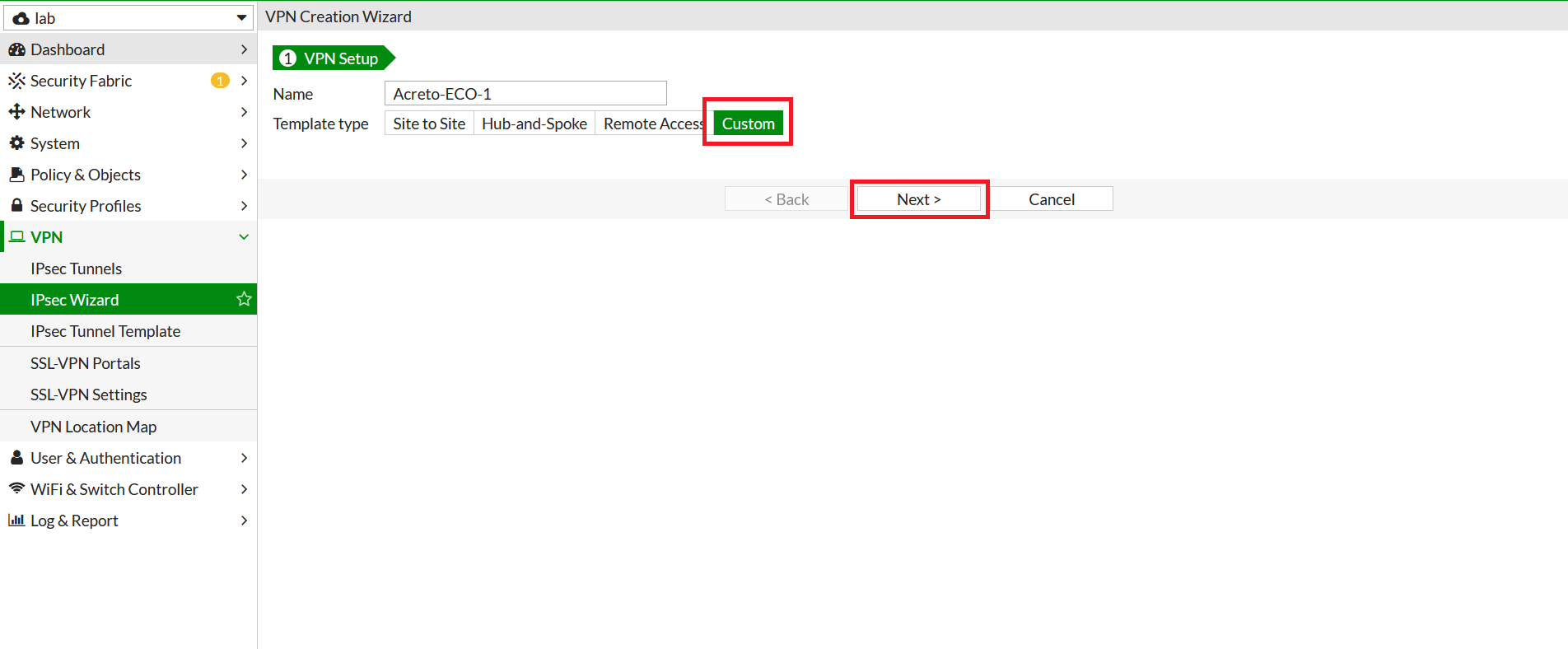

- Configure the following VPN settings:
- IP Version: IPv4
- Remote Gateway: Static IP Address
- IP Address: Primary EcoSystem Gateway
- Interface: Select WAN Interface
- Mode Config: Enable
- DPD Retry interval: 30
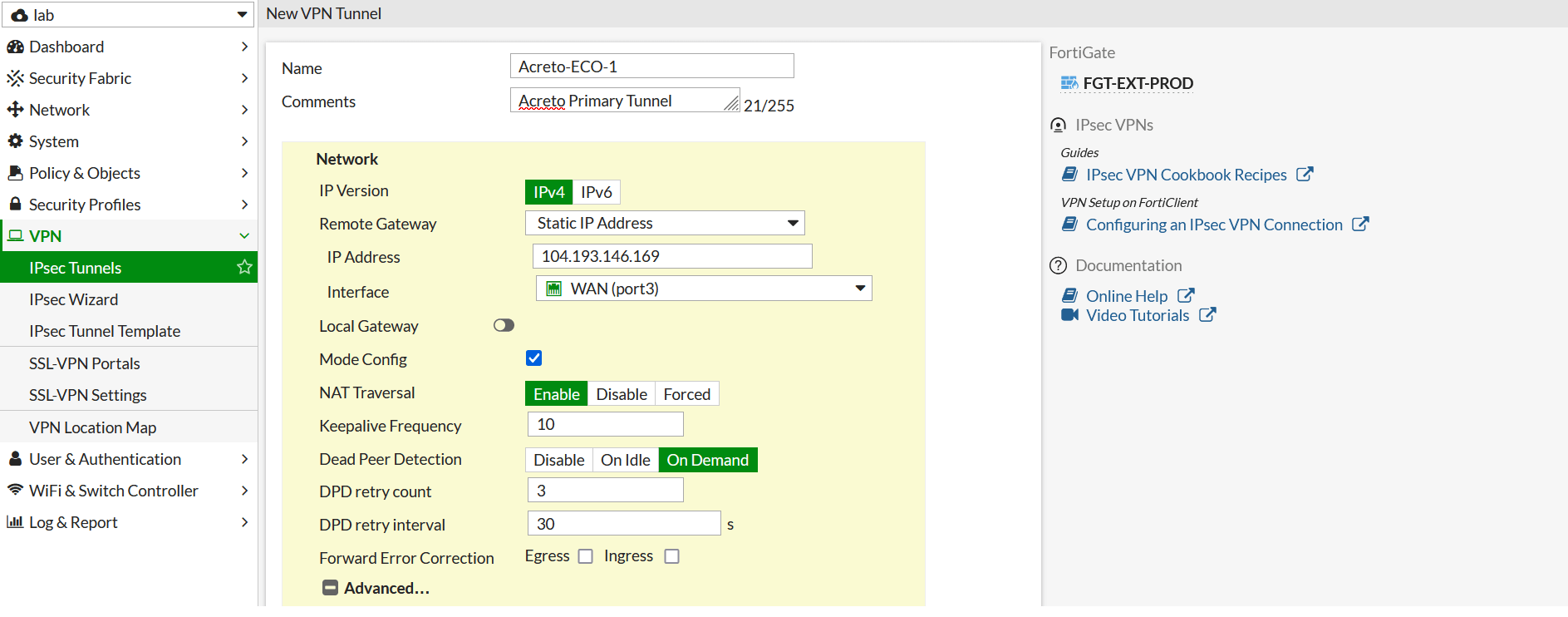

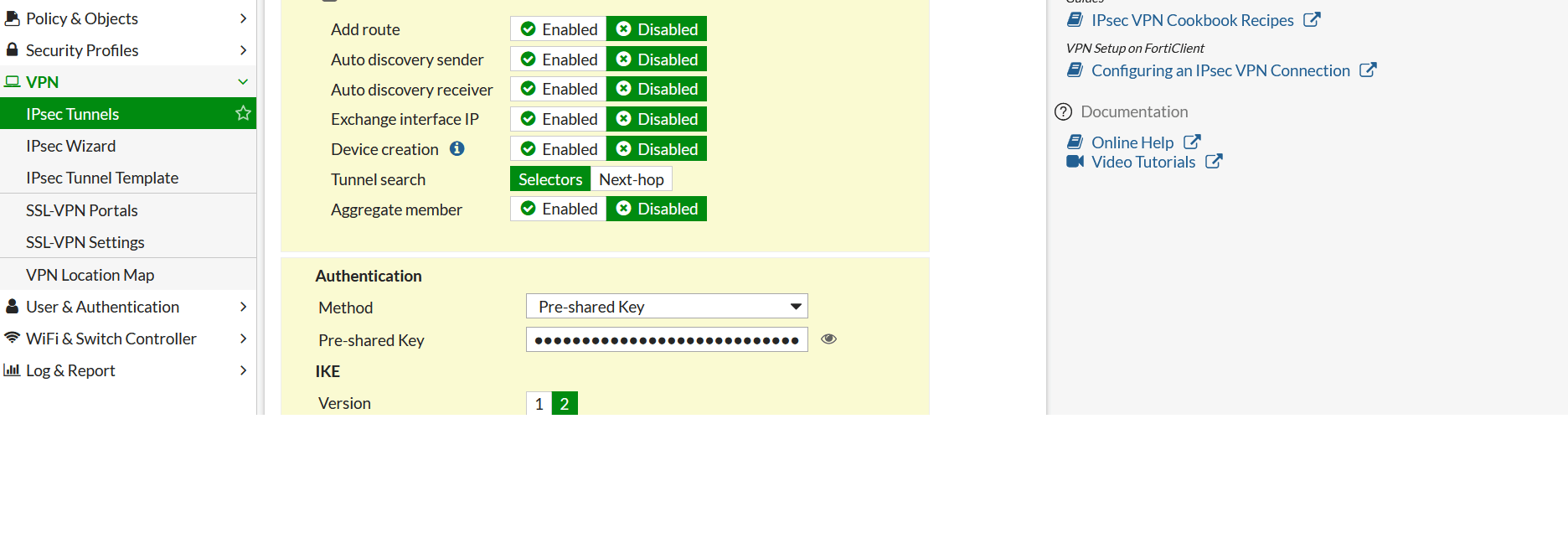
- Expand Advance Option and configure as below:
- Add Route: Disabled
- Authentication Method: Pre-shared Key
- Pre-shared Key: enter the pre-shared key
- IKE Version: 2

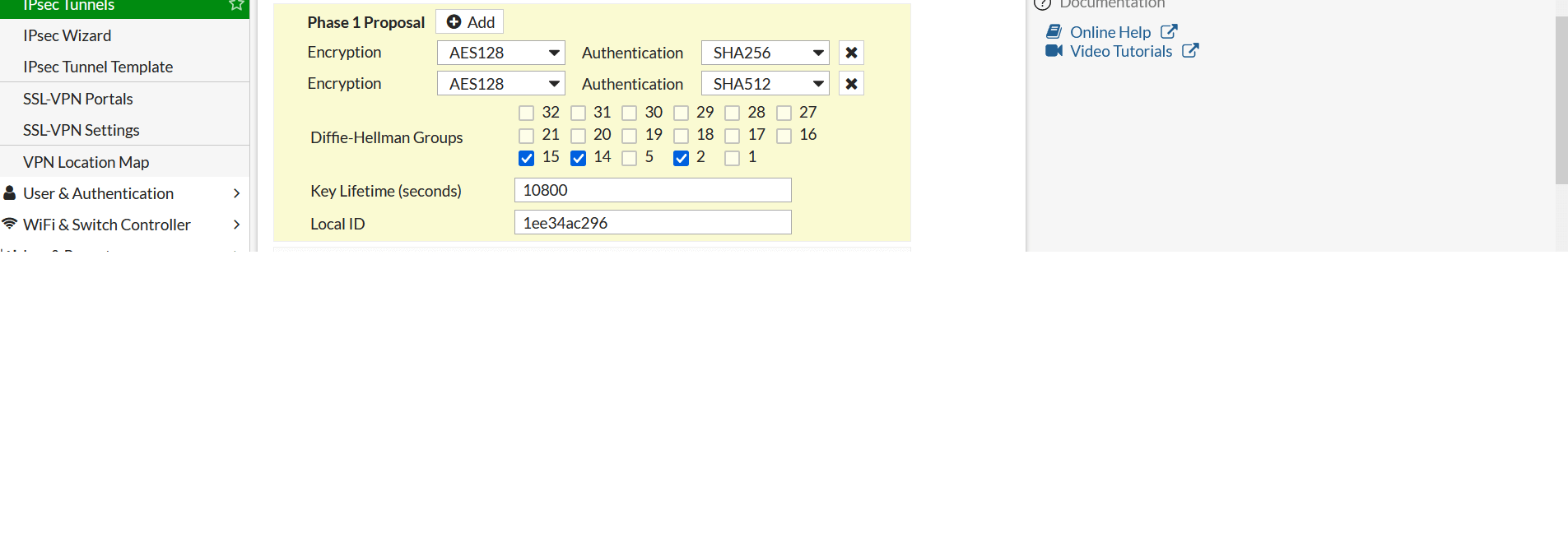
- In Phase1 Proposal. Delete all proposals except two as below:
- Encryption: AES 128 Authentication: SHA256
- Encryption: AES 128 Authentication: SHA512
- DH Group: 15 , 14, 2
- Key Lifetime: 10800
- Local ID: enter the peer id

- In Phase2 setting, please enter below:
- Encryption: AES 128 Authentication: SHA256
- Encryption: AES 128 Authentication: SHA512
- PFS: Enable
- DH Group: 15 , 14, 2
- Auto Keep Alive: Enable
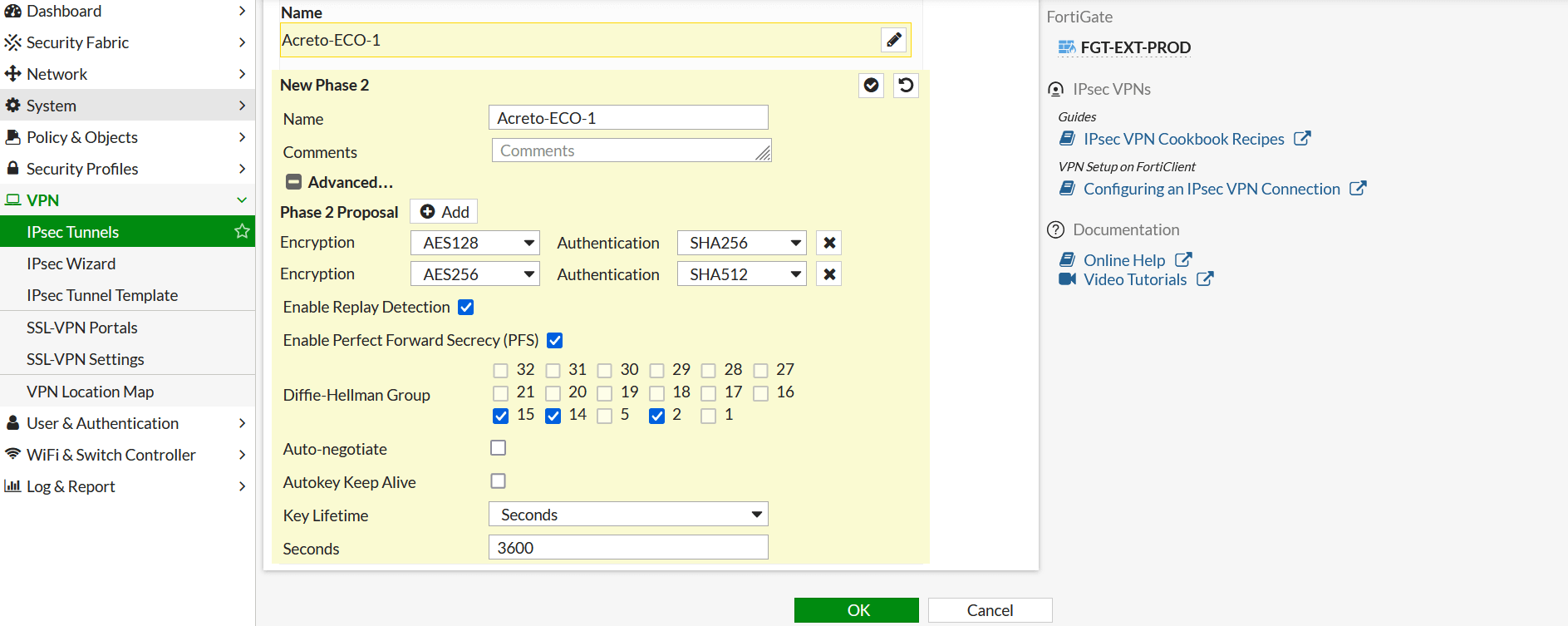

- Click OK to save the VPN setting.
- Repeat the above steps for the creation of a secondary tunnel. We will use Acreto-ECO-2 as the name of a secondary tunnel in this article.
This step is required for policy routing to work. Any dummy/unused IPs can be used for interfaces.
- Go to Network > Interfaces. Select Acreto-ECO-1 Tunnel interface and click on Edit

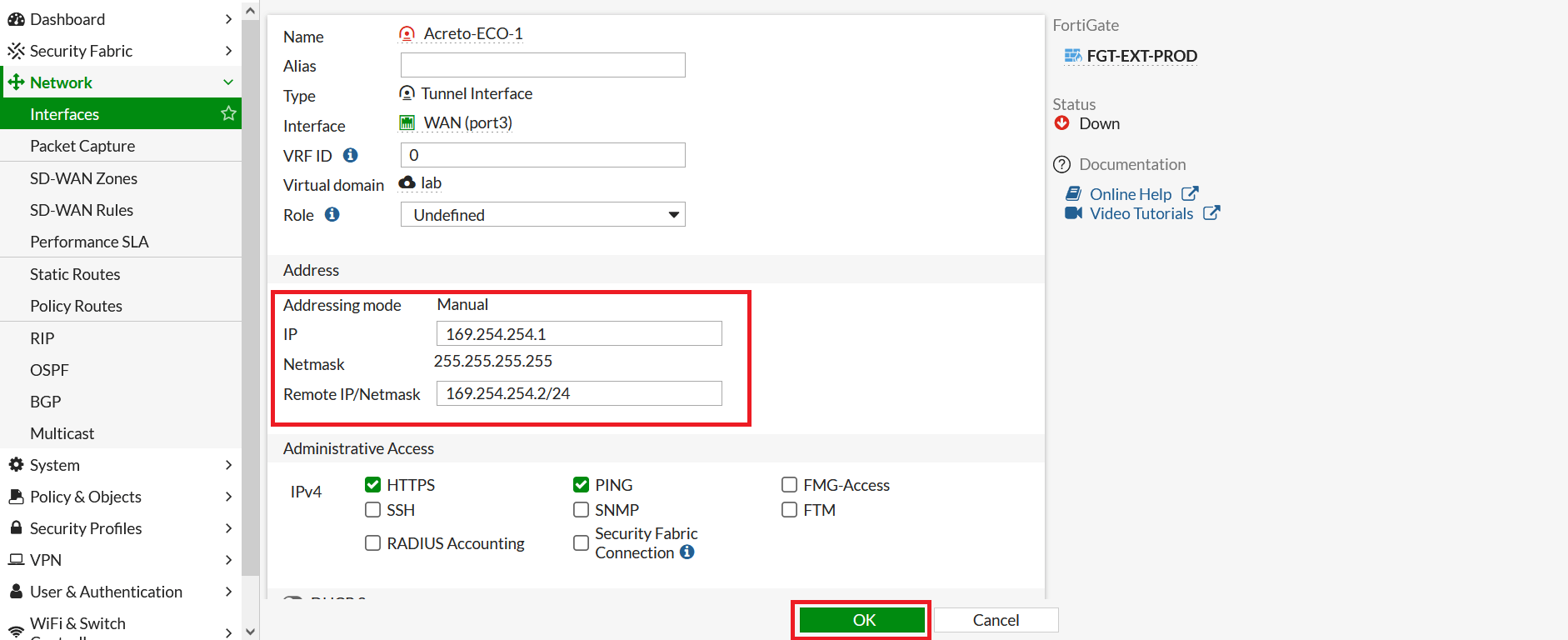
- Configure IP as below:
- IP: 169.254.254.1
- Remote IP: 169.254.254.2/32
- Click on Save

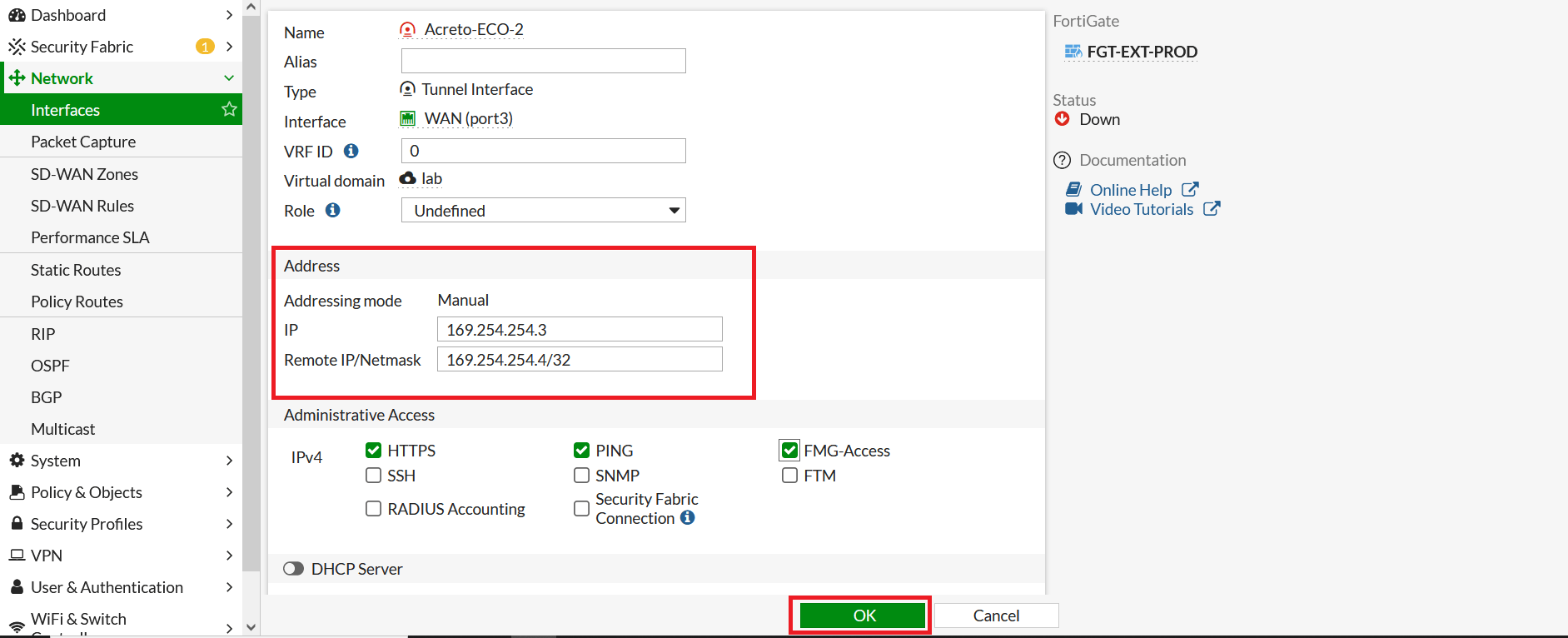
- Repeat the step to configure IP on the secondary tunnel interface.
- Go to Network > Interfaces. Select Acreto-ECO-2 Tunnel interface and click on Edit.
- Configure IP as below:
- IP: 169.254.254.3
- Remote IP: 169.254.254.4/32
- Click on Save.

- Go to Network > Static Route. Click on Create New.
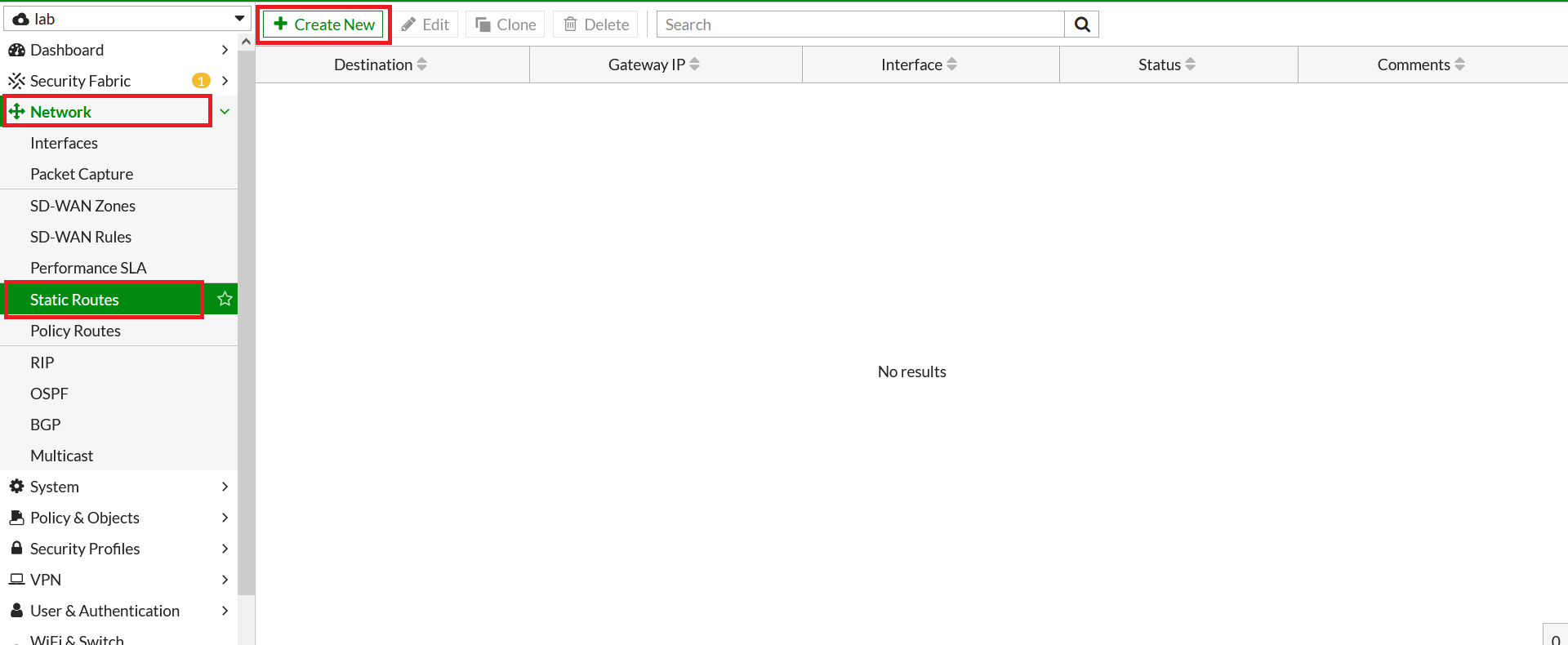

- In the next window, configure the static route as below:
- Destination: 0.0.0.0/0
- Interface: Acreto-ECO-1 (Acreato-primary-tunnel)
- Administrative Distance: 30
- Click on Save
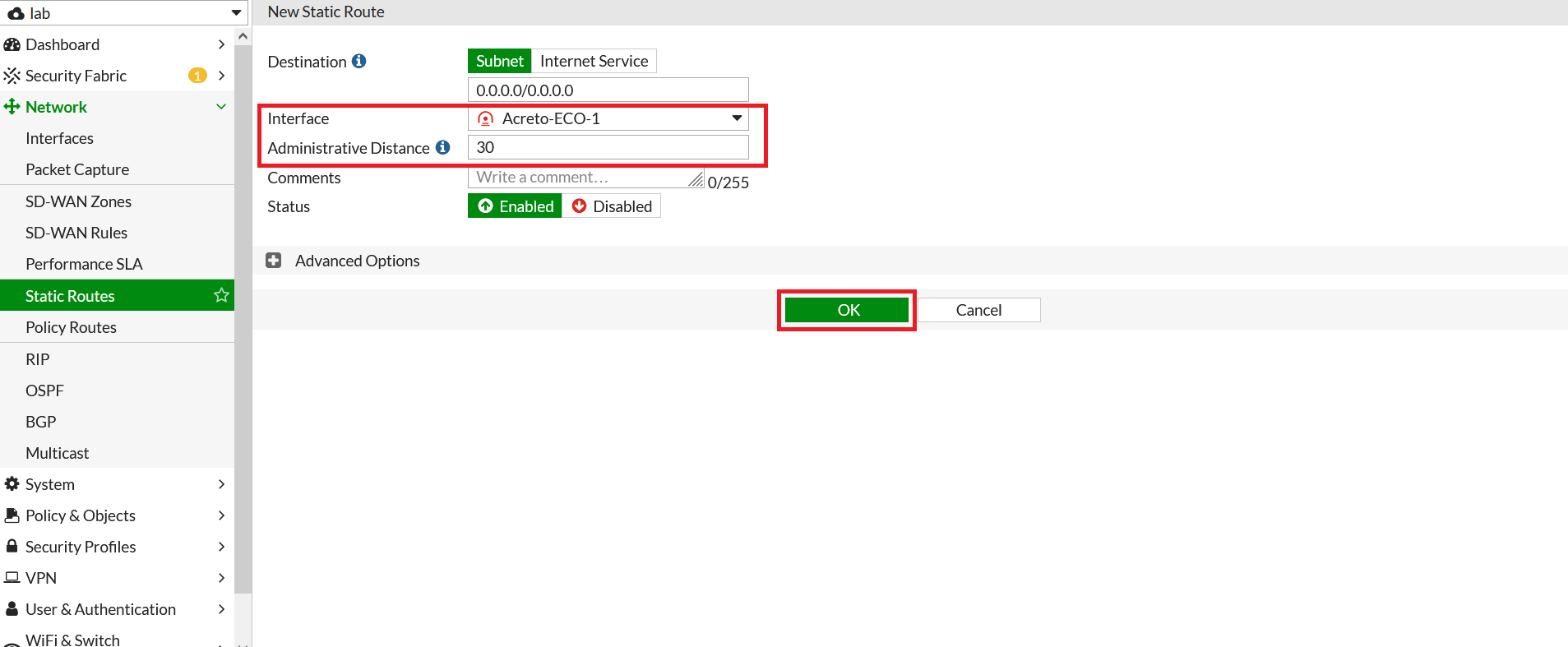

- Repeat the step to configure a static route for the secondary tunnel.
- Go to Network > Static Route. Click on Create New.
- In the next window, configure the static route as below:
- Destination: 0.0.0.0/0
- Interface: Acreto-ECO-2 (Acreato-secondary-tunnel)
- Administrative Distance: 30
- Click on Save

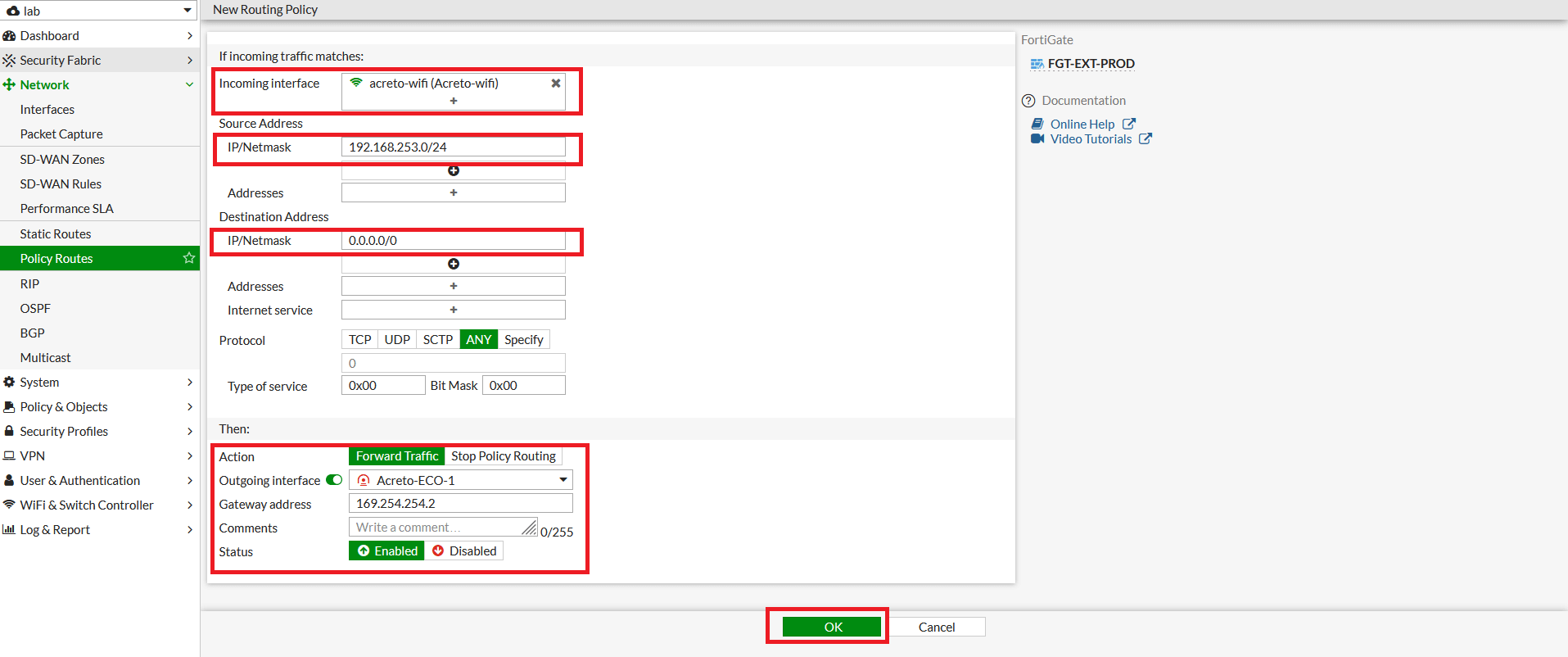
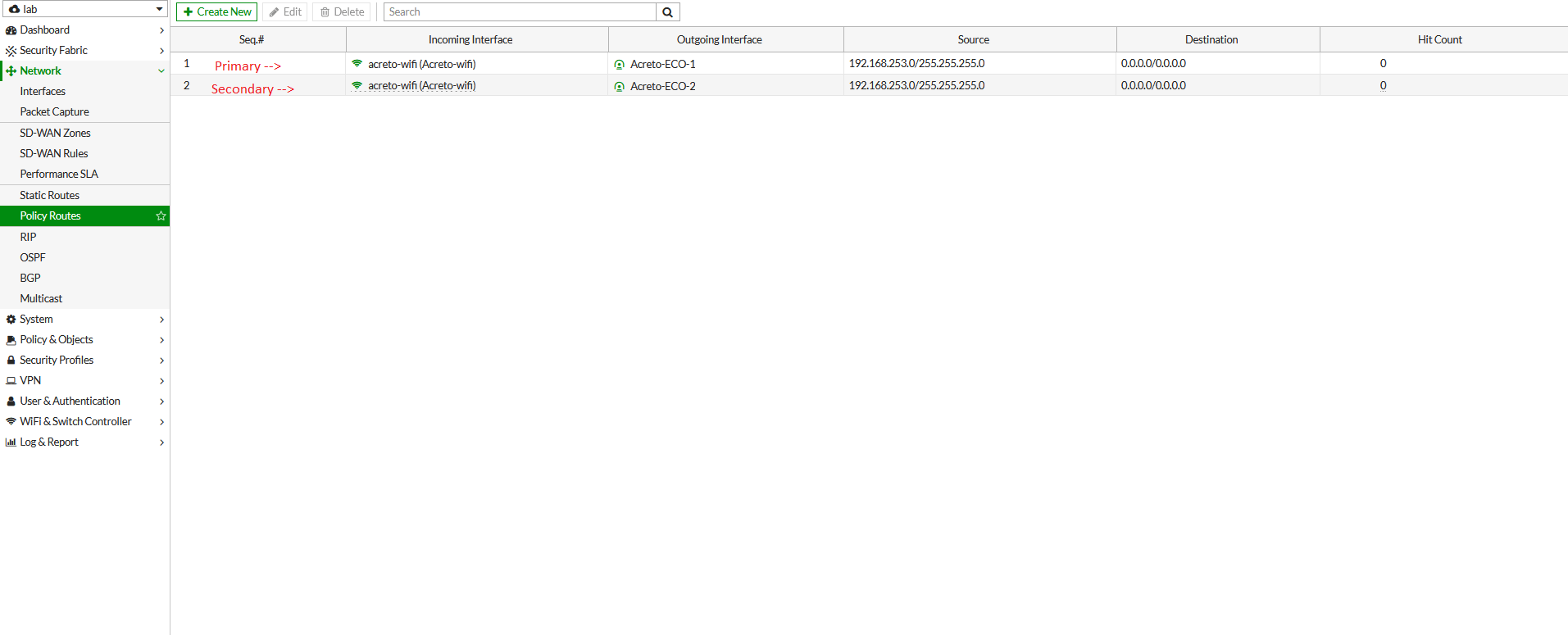
- To configure the policy route, Go to Network > Policy Route. Click on Create New.
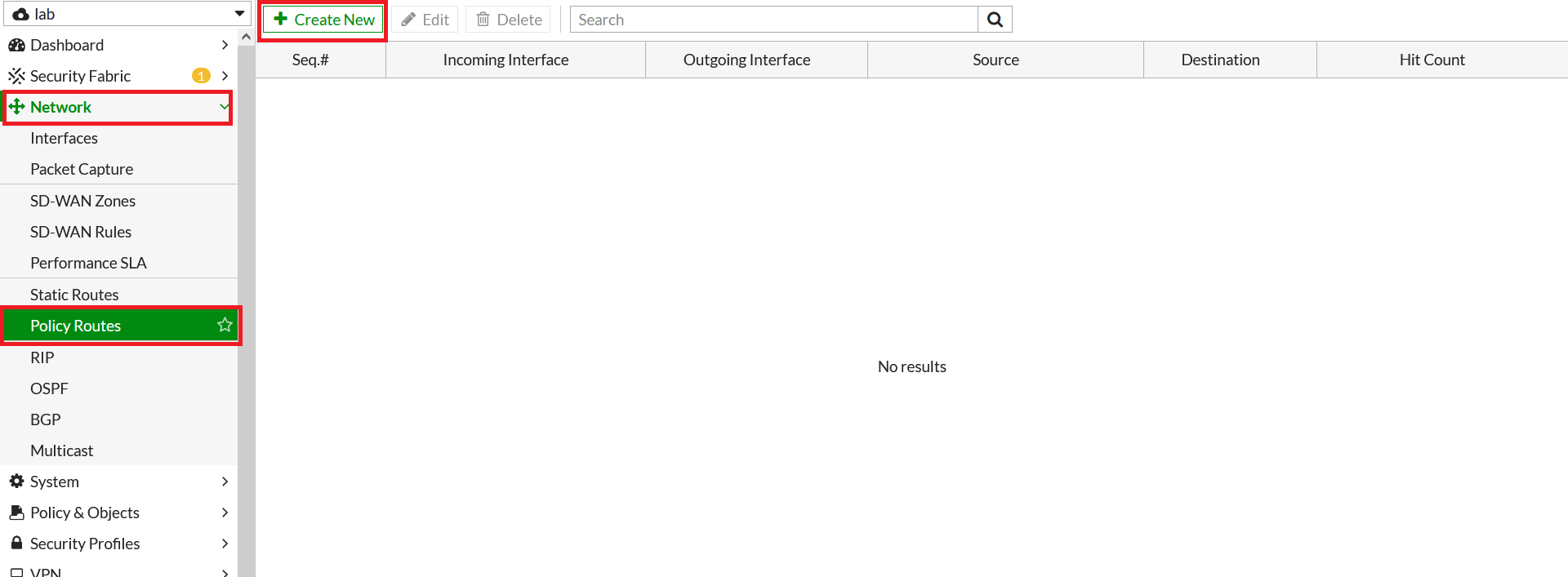

- In the next window, configure policy route setting as below:
- Incoming Interface: Select LAN interface
- Source - IP/Netmask: 192.168.253.0/24 (LAN Network)
- Destination - IP/Netmask: 0.0.0.0/0
- Outgoing Interface: Acreto-ECO-1 (Primary Tunnel)
- Gateway Address: 169.254.254.2 (Remote IP for primary tunnel interface)
- Click on save.

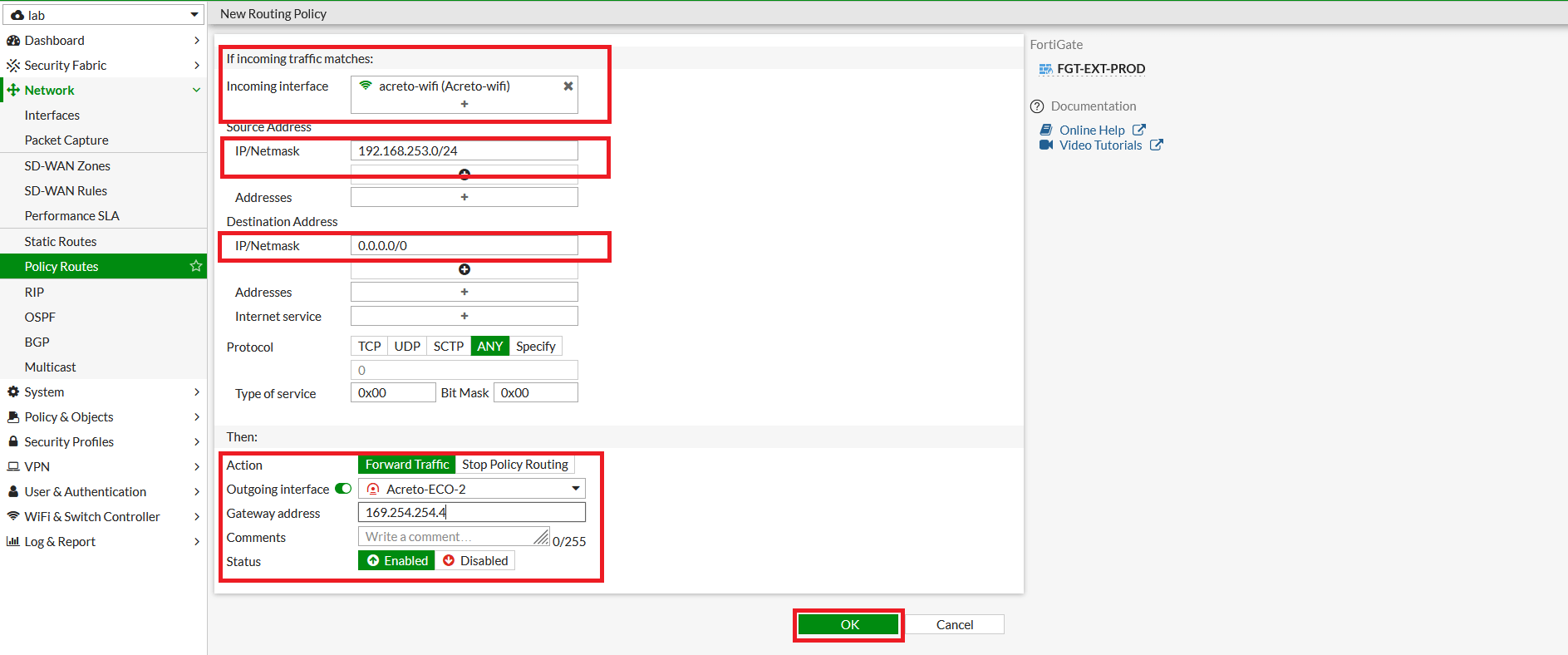
- Repeat the step to configure the policy route for the secondary tunnel.
- Go to Network > Policy Route. Click on Create New.
- In the next window, configure policy route setting as below:
- Incoming Interface: Select LAN interface
- Source - IP/Netmask: 192.168.253.0/24 (LAN Network)
- Destination - IP/Netmask: 0.0.0.0/0
- Outgoing Interface: Acreto-ECO-2 (secondary Tunnel)
- Gateway Address: 169.254.254.4 (Remote IP for secondary tunnel interface)
- Click on Save.

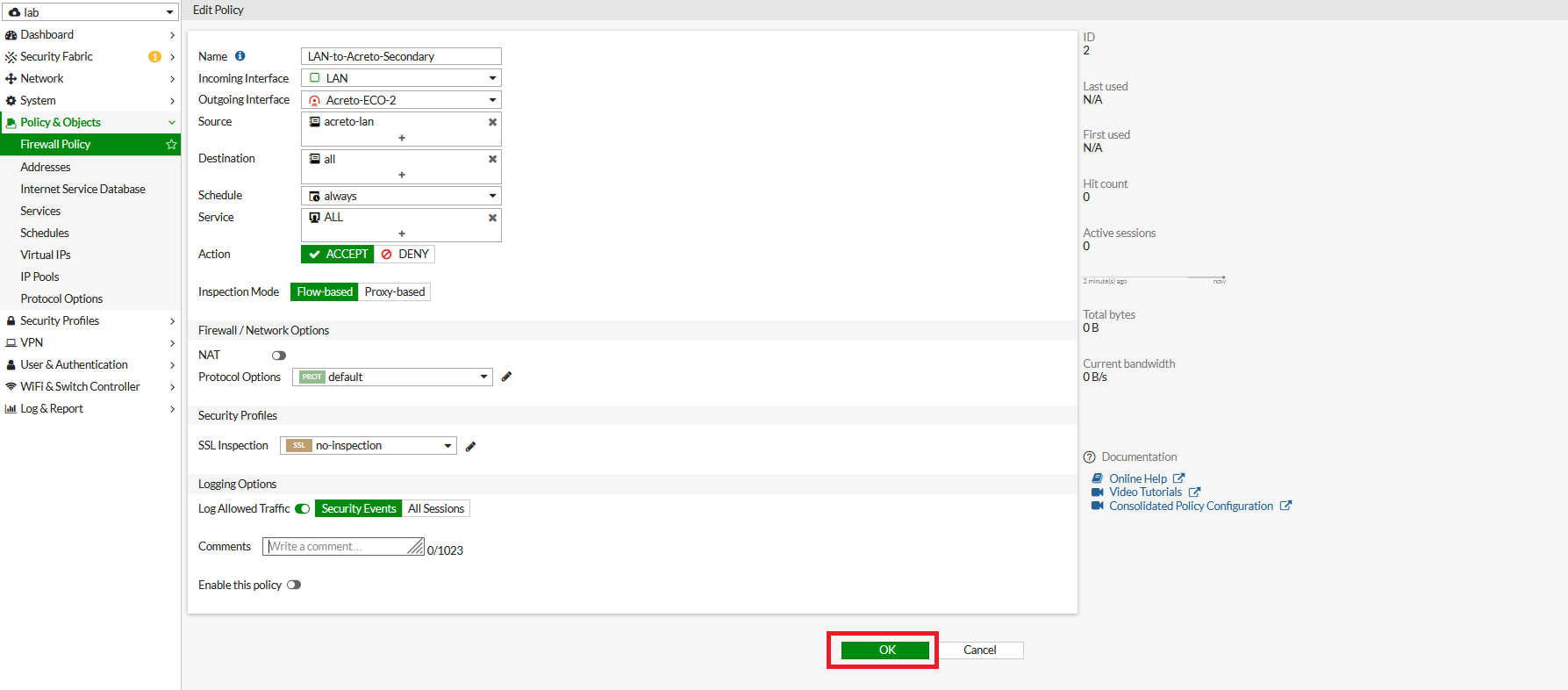
- Go to Policy & Objects > Firewall Policy. Click on Create New.

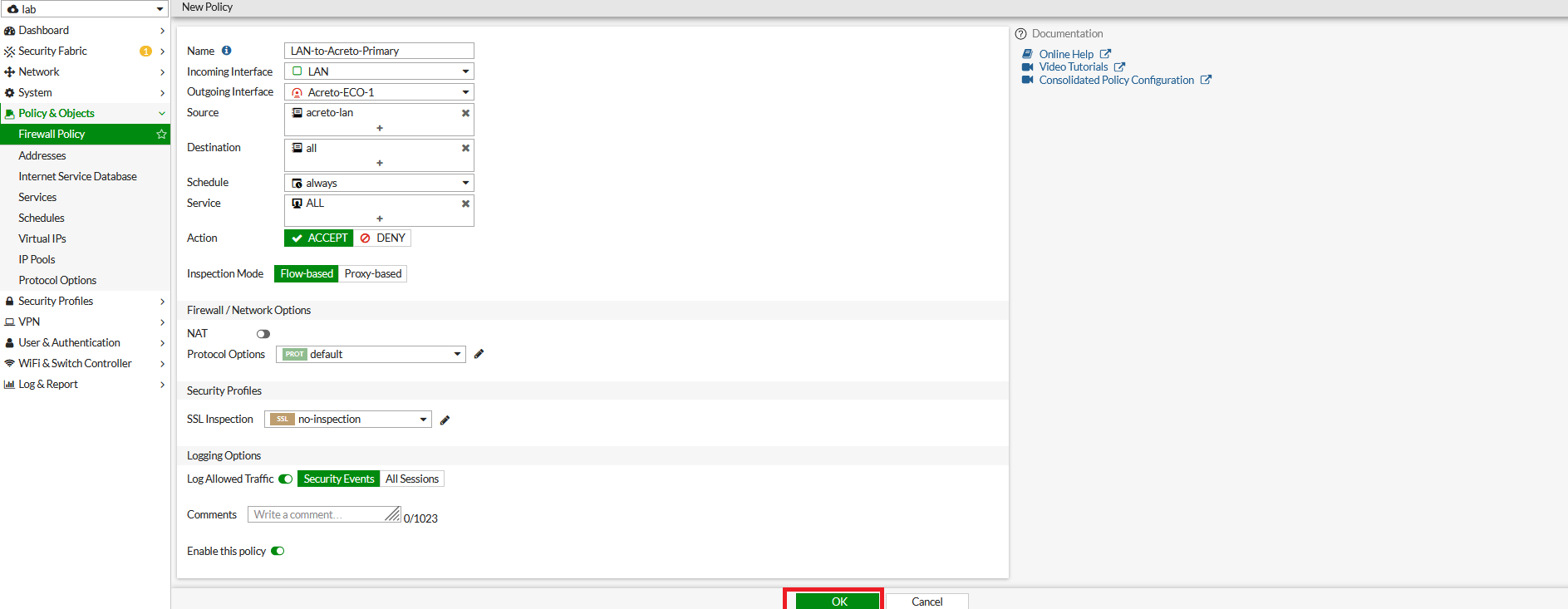
- In the next window, configure the policy setting as below for primary VPN.
- Name: Give a name to the primary policy
- Incoming Interface: LAN
- Outgoing Interface: Acreto-ECO-1 (Primary Tunnel Interface)
- Source: LAN Address
- Destination: all
- Schedule: Always
- Service: All
- Action: Accept
- NAT: Disable
- Protocol Option: default
- SSL Inspection: no-inspection
- Logging: As needed
- Click on Save.

- Repeat the step to create a firewall policy to allow traffic on secondary VPN.
- Go to Policy & Objects > Firewall Policy. Click on Create New.
- Name: Give a name to the secondary policy
- Incoming Interface: LAN
- Outgoing Interface: Acreto-ECO-2 (Secondary Tunnel Interface)
- Source: LAN Address
- Destination: all
- Schedule: Always
- Service: All
- Action: Accept
- NAT: Disable
- Protocol Option: default
- SSL Inspection: no-inspection
- Logging: As needed
- Click on Save.

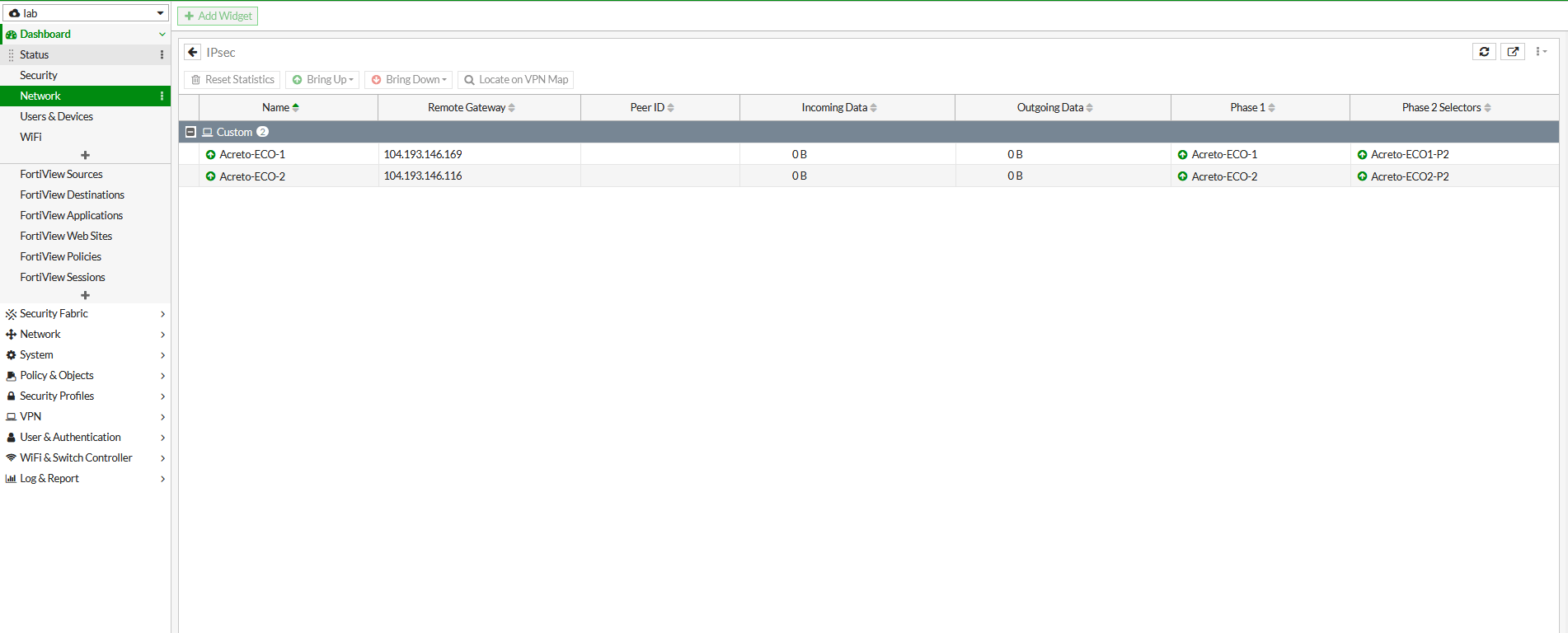
Task 8. Check the status of the VPN.
- Go to Dashboard > Network > IPsec.
- If the tunnel is showing down. Select the tunnel and click on Bring UP

- Primary and secondary VPN selection is handled by Policy Route.
Traffic will be matched with the policy on top if both tunnels are up.

Summary
After this setup, there are two tunnels created from FortiGate to Acreto Primary and Secondary Ecosystem through Primary and Secondary tunnel respectively. If the primary tunnel goes down, all traffic will start going from the backup tunnel, which in this case is the Secondary tunnel.
Fortinet FortiGate IPsec Configuration
Prerequisites
- FortiGate installation
- Ecosystem set up with proper security policies
Create Gateway for IPsec
Firstly, you will need to create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
- Name: IPsec connection name must meet the same requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed through this gateway.


Info
To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow you to test connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
How-To
Step 1: Read IPsec Gateway Values Required for FortiGate Configuration
To proceed with the FortiGate configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All of these may be found within the Gateway details panel - view the below animation for further instruction.
Use VPN Wizard to create all basic configurations.
- Log in to the FortiGate Dashboard.
- In the navigation panel, select VPN > IPsec Wizard and view VPN Creation Wizard
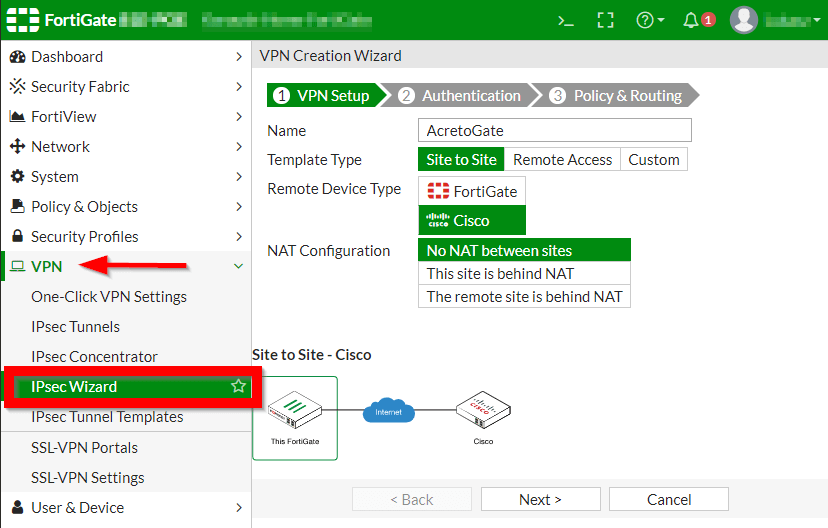

- Complete the first step of VPN Wizard, VPN Setup, by inserting these values:
- Name: AcretoGate (or your own readable name)
- Template Type: Site to Site
- Remote Device Type: Cisco
- NAT Configuration: No NAT between sites
- When the form is ready, click Next.
- Complete the second step of the VPN wizard, Authentication.
- Remote Device: IP address
- IP Address: Input the IP address of your Acreto Gateway created in Wedge.
- Outgoing Interface: Select the existing interface that will be used for this connection.
- Authentication Method: Pre-shared Key
- Pre-shared Key: Enter the Pre-shared Key common for Acreto and FortiGate (available on Acreto Wedge in the Gate configuration panel).
- When the form is ready, click Next.
- Complete the last step of the VPN wizard, Policy & Routing.
- Local Interface: Select the local interface that will use this connection.
- Local Subnets: Define local subnets for this connection.
- Remote Subnets: Define remote (Acreto site) subnets for this connection (0.0.0.0/0 - for all networks).
- Internet Access: None
- Click on Save.
- From the side menu, choose VPN > IPsec Tunnels to confirm that the newly created VPN is displayed on the list in the Site to Site section.
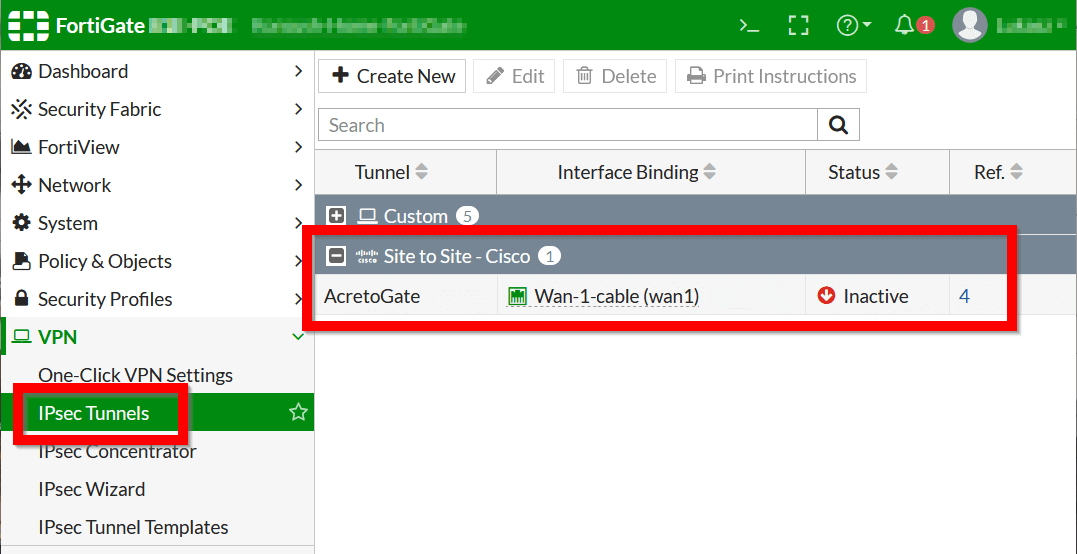

- From the side menu, choose VPN > IPsec Tunnels. You should see the Acreto Gate tunnel created in the previous step.
- Double-Click on the tunnel name to open editing options.
- On the Edit VPN tunnel screen, click Convert To Custom Tunnel- this action will convert your VPN to a custom tunnel, allowing you to configure additional settings.
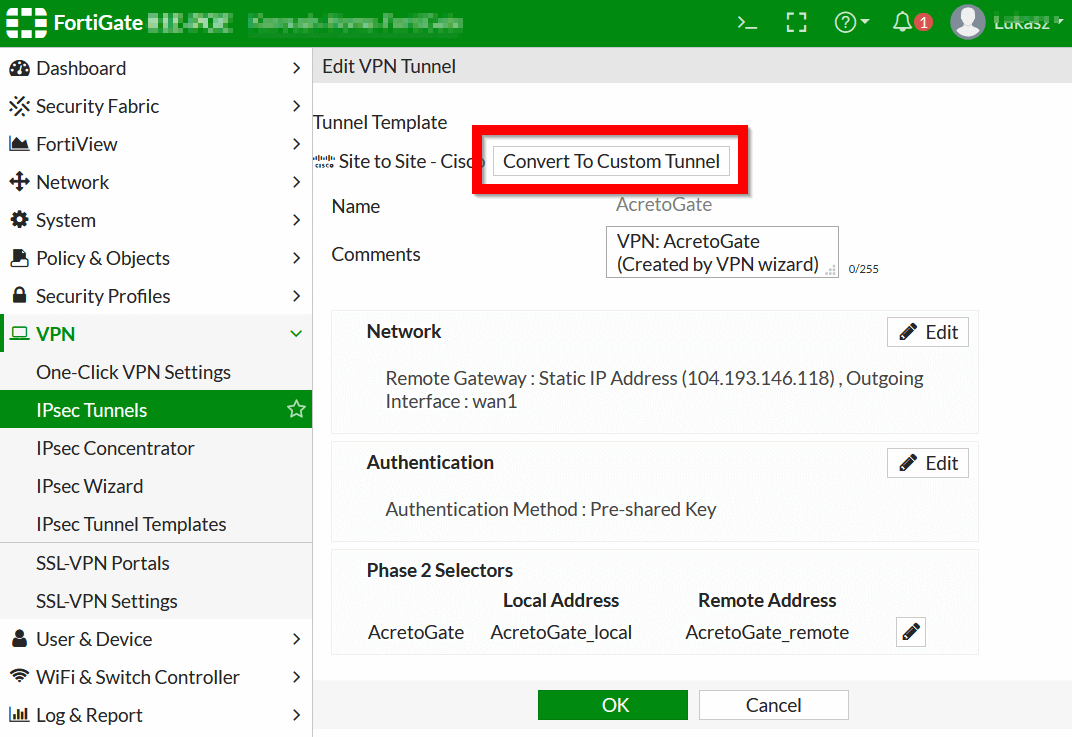

- After you click on Convert To Custom Tunnel, a few additional options will be displayed on the screen.
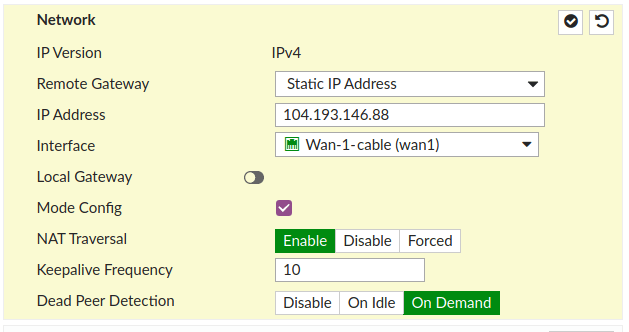
- Edit Network by clicking on Edit and set the Mode Config to check, as shown on the screen below (IP address and Interface will be different).

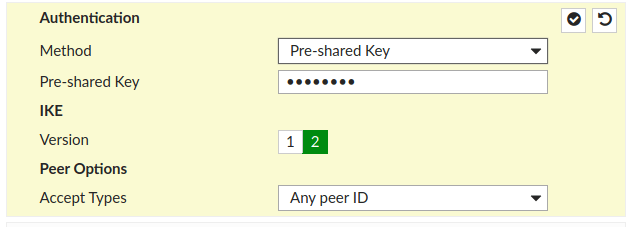
- Edit Authentication by clicking on Edit and set Version to 2, as shown on the screen below.

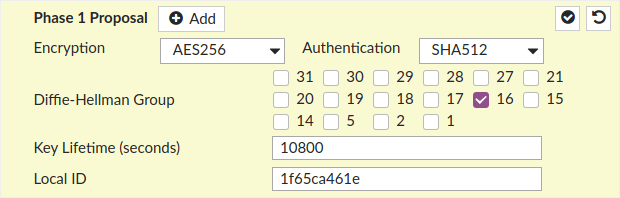
- Edit Phase 1 Proposal by clicking on Edit and set Version to 2, as shown on the screen below.
- Encryption: AES256
- Authentication: SHA512
- Diffie-Hellman Group: 16
- Key Lifetime: 3600

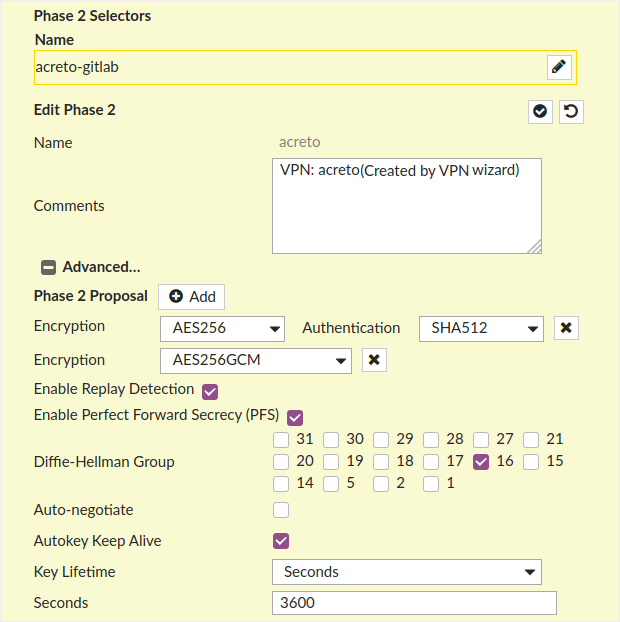
- Edit Phase 2 Selectors by clicking on Edit > Advanced, as shown on the screen below:
- Encryption: AES256
- Authentication: SHA512
- Enable Replay Detection: check
- Enable Perfect Forward Secrecy (PFS): check
- Diffie-Hellman Group: 16
- Autokey Keep Alive: check
- Key Lifetime: Seconds
- Seconds: 3600

- When all edits are complete, click OK at the bottom of the screen to convert the tunnel. From now on, the IPsec tunnels panel will show as Custom.
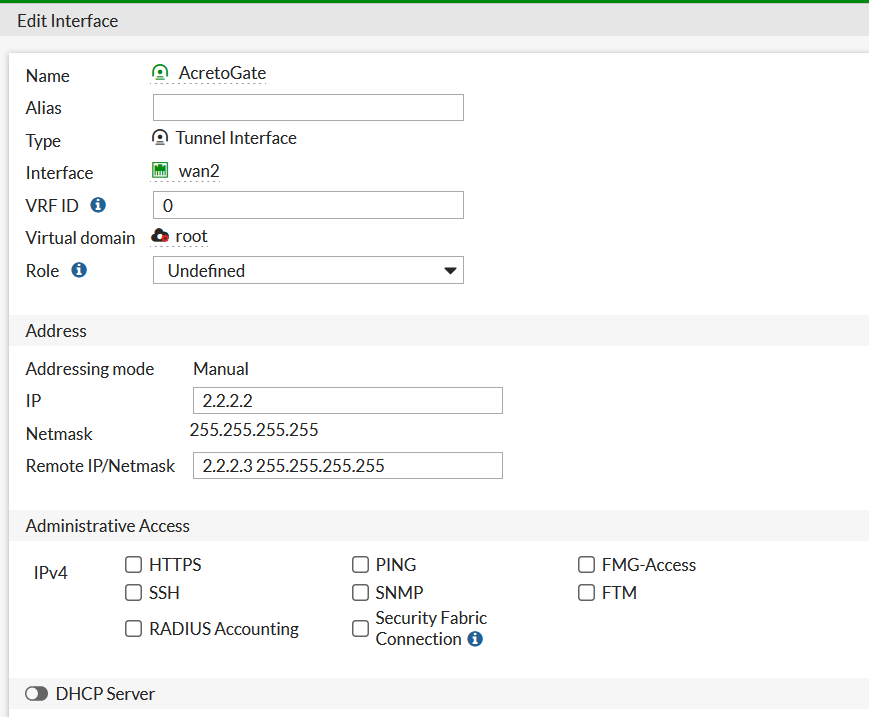
- From the side menu, choose Network > Interfaces. Find the tunnel interface name AcretoGate under WAN interface.
- Edit the interface and assign local and remote IP. You can choose any IP, it will not affect the traffic.
- IP: <any /32 IP>
- Netmask: 255.255.255.255
- Remote IP/Netmask: <any /32 IP>

- From the side menu, choose Network > Static Routes. Find the static route created by the wizard. Should be with the name
<Tunnel_name>_remote.
- Edit the static route and change the Administrative Distance to 50.
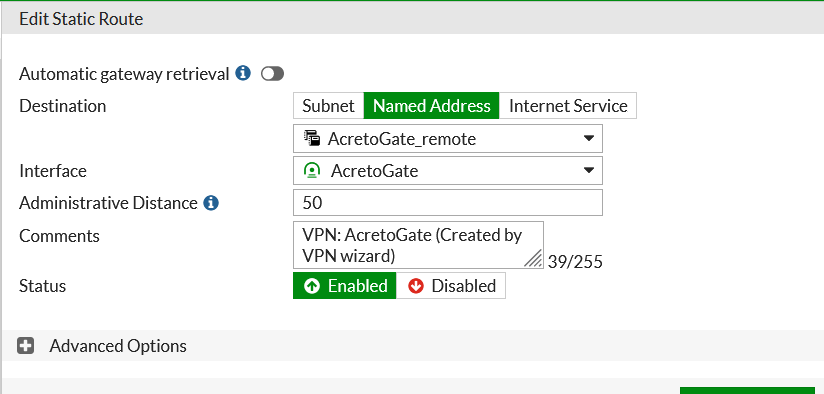

- Click OK to save the route.
- From the side menu choose Network > Policy Routes and click on Create New
- Configure the new Policy Route, as shown on the screen below.
- Incoming Interface: <select your local interface>
- Source Address-Ip/Netmask : <enter local subnet >
- Destination Address-Ip/Netmask : 0.0.0.0/0
- Action : Forward Traffic
- Outgoing Interface : AcretoGate OR <choose your tunnel interface>
- Gateway Address : <enter Remote IP configured in Step 4.2.3>
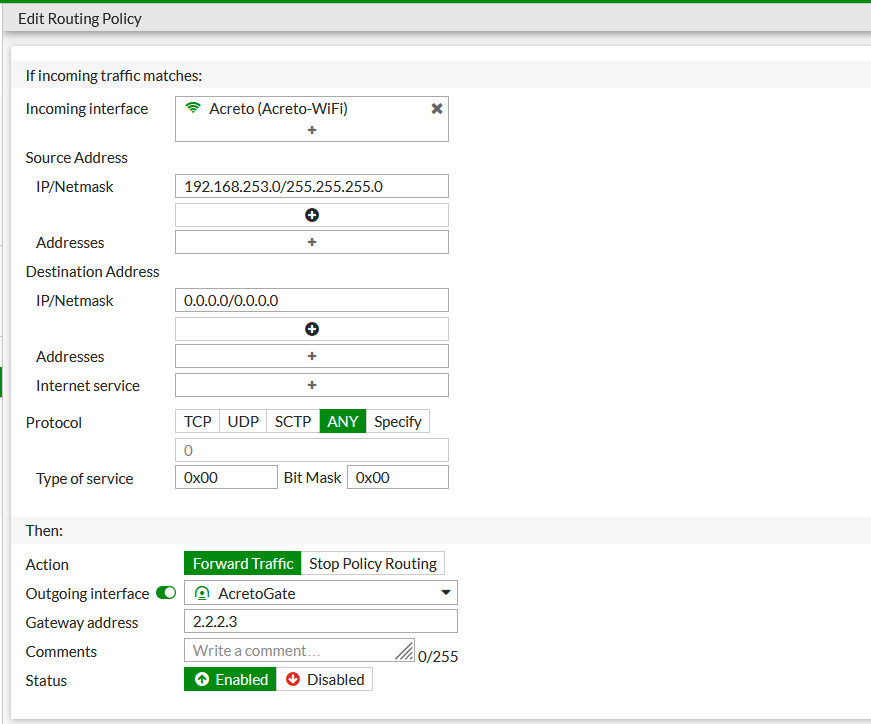

- Click OK to Save
- From the side menu, choose Dashboard > Network > IPsec
- Select the Tunnel and click on Bring Up.
When the configuration is complete, all network traffic on the selected interface and the selected subnet(s) is redirected through Acreto.
Fortinet FortiGate IPsec Configuration through CLI
Before you start
Overview
This article will show you how to use CLI to connect the FortiGate managed network to the Acreto Ecosystem.
Prerequisites
- FortiGate installation
- Ecosystem set up with proper security policies
How-To
Create Gateway for IPsec
This step is optional, skip it if you already own the Gateway.
Firstly, you will need to create a new Gateway device in the Acreto
platform. Instructions on how to create a new Gateway are available
here.
- Name: IPsec connection name must meet the same requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address
where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed
through this gateway.


Info
To simplify testing, add the IP addresses of all
interfaces connected to your gateway as Local Networks (you can use /32
prefix for public interface). This will allow you to test connectivity
from the gateway through Acreto by using Ping, Traceroute, or similar
tools.
Step 1: Read IPsec Gateway Values Required for Fortigate Configuration
To proceed with the Fortigate configuration, you will need a few values
from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All of these may be found within the Gateway details panel - view the
below animation for further instruction.
Use the following commands to create a VPN through CLI.
Log in to the Fortigate CLI.
-
Configure IPsec VPN Phase-1
config vpn ipsec phase1-interface
edit AcretoGate
set interface <wan_interface>
set peertype any
set net-device disable
set mode-cfg enable
set proposal aes128-sha256 aes256-sha512
set ike-version 2
set keylife 10800
set remote-gw acreto-peer-ip (Copy from Wedge Dashboard)
set psksecret psk (Copy from Wedge Dashboard)
set dhgrp 16
set localid local-id (Copy from Wedge Dashboard)
next
end
-
Configure IPsec VPN Phase-2
config vpn ipsec phase2-interface
edit AcretoGate
set phase1name AcretoGate
set proposal aes256-sha512 aes256gcm
set dhgrp 16
set keepalive enable
set keylifeseconds 3600
next
end
-
Create addresses for all local addresses/subnets
config firewall address
edit AcretoGate_local_1
set allow-routing enable
set subnet 192.168.1.0 255.255.255.0
next
edit AcretoGate_local_2
set allow-routing enable
set subnet 192.168.2.0 255.255.255.0
next
end
-
Create an address group to add all the addresses created in the previous step
config firewall addrgrp
edit AcretoGate_local_grp
set member AcretoGate_local_1 AcretoGate_local_2
next
end
-
Outbound Policy for traffic originating from Local lan interface to internet through Acreto VPN
config firewall policy
edit 0
set name Outbound_toAcreto
set srcintf lan_interface_ip
set dstintf AcretoGate
set srcaddr AcretoGate_local_grp
set dstaddr all
set action accept
set schedule always
set service ALL
next
end
-
Inbound Policy for traffic coming from Acreto VPN to Local lan
config firewall policy
edit 0
set name Inbound_fromAcreto
set srcintf AcretoGate
set dstintf lan_interface_ip
set srcaddr all
set dstaddr AcretoGate_local_grp
set action accept
set schedule always
set service ALL
next
end
Scenario 1: When traffic from all local subnet/interfaces need to pass through the tunnel
-
Add Static Route
config router static
edit 0
set dst Acreto_PeerIP
set device wan_interface
Set gateway ISP_Gateway
next
edit 0
set dst 0.0.0.0 0.0.0.0
set device AcretoGate
set distance 4
next
end
Scenario 2: When traffic from a specific subnet/interface needs to pass through the tunnel.
-
Add IP at the tunnel interface
config system interface
edit "AcretoGate"
set ip 2.2.2.2 255.255.255.255
set remote-ip 2.2.2.3 255.255.255.255
next
end
-
Add Static Route to direct the traffic through the tunnel with a higher administrative distance
config router static
edit 0
set distance 254
set device AcretoGate
set dst 0.0.0.0 0.0.0.0
next
end
-
Add Policy Route to direct the specific traffic through the tunnel
config router policy
edit 0
set input-device lan_interface
set srcaddr AcretoGate_local_grp
set dstaddr all
set output-device AcretoGate
Set gateway 2.2.2.3
next
end
Run the following command to bring the tunnel up bash diagnose vpn tunnel up AcretoGate
diagnose vpn tunnel up AcretoGate
- Check the status of tunnel Phase-1
diagnose vpn ike gateway list name AcretoGate
diagnose vpn tunnel list name AcretoGate
Summary
Once the VPN connection is successfully established, all the internet traffic will be routed through Acreto.
Linux - Automatic IPsec Configuration
Prerequisites
- Ubuntu 18.04 or newer installed on your device
- Ecosystem set up with proper security policies
Create Gateway for IPsec
If you didn’t do it yet, you need to create a new Gateway device on the Acreto
platform.
-
Login to the Acreto platform at wedge.acreto.net
-
Select your ecosystem and go to Objects using the left menu.
-
Click Add new Object and select Gateway.
-
Fill at least:
-
Name: the name of the IPSec connection needs to be compatible with
Strongswan connection name requirements (basically, only letters and
numbers)
-
Category: IoT
-
Allow connection from: Empty (describes the source IP address where the
IPsec connection will be permitted)
-
Local Networks: - your local network addresses that should be routed
through this gateway
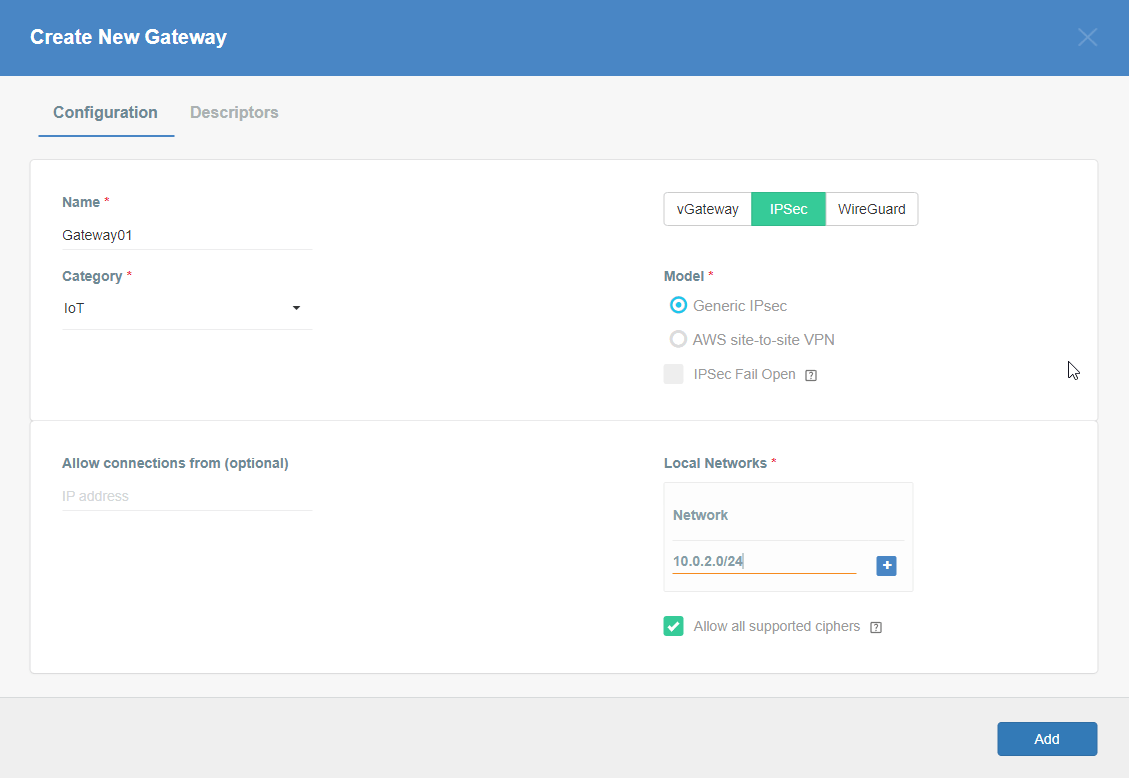

Note: To simplify testing, add IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow testing connectivity from the gateway through Acreto using ping, traceroute, and similar tools.
-
Save the created Gateway by pressing Add.
-
Add a security policy that will allow communication from the Gateway device to the Internet.
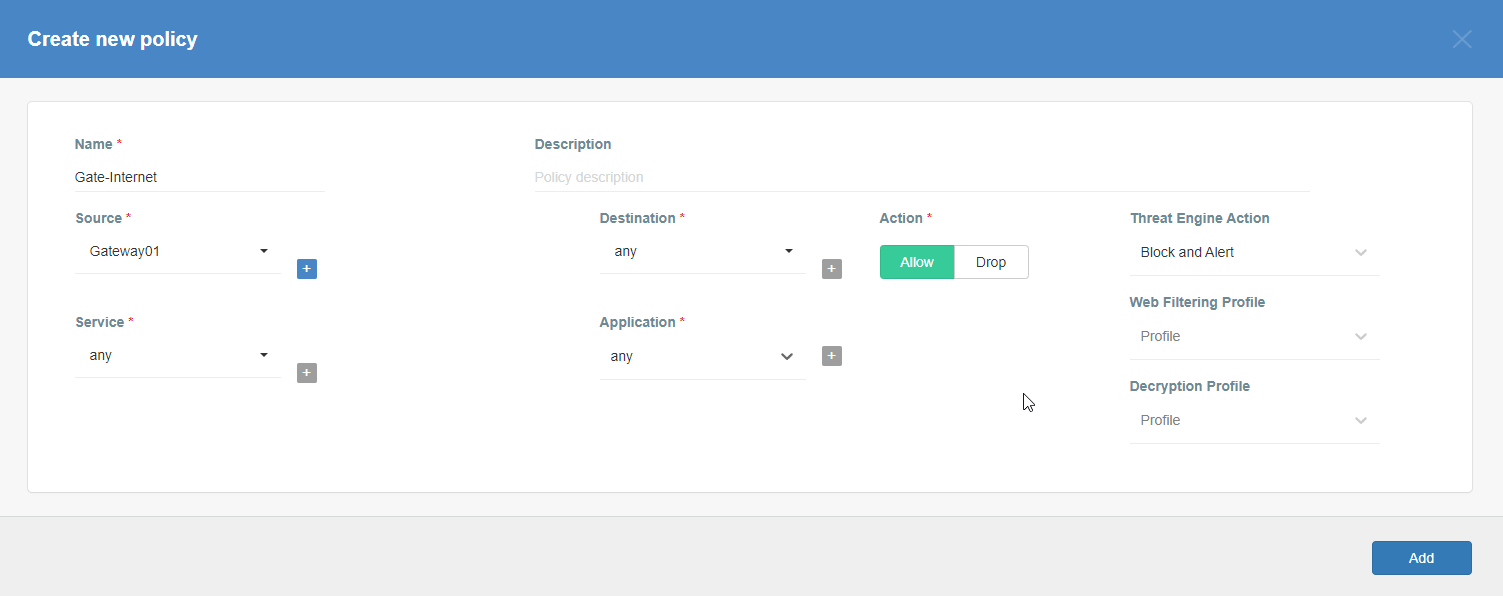

-
Commit pending changes (top of the screen)
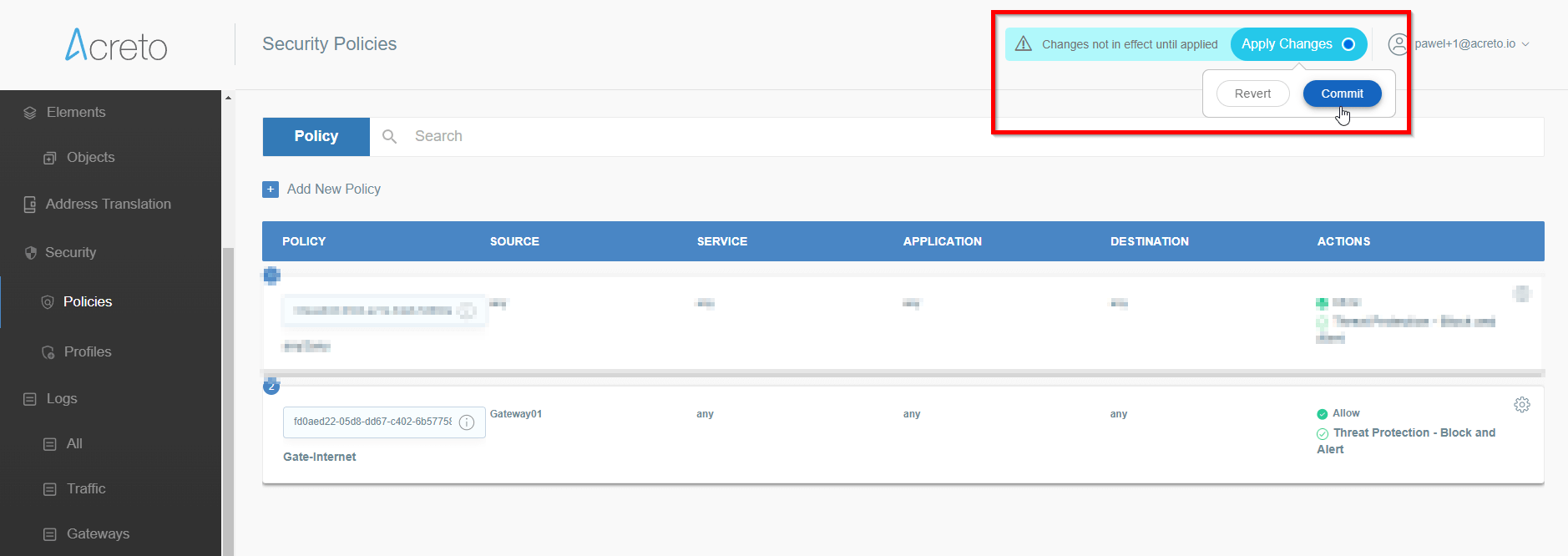
 Note: to successfully test your connectivity, you also need to create a
security policy that will allow traffic going through your device.
Note: to successfully test your connectivity, you also need to create a
security policy that will allow traffic going through your device.
Generate Strongswan config files
-
Log in to the Acreto platform at
wedge.acreto.net
-
Select your ecosystem and go to Objects using the left menu
-
Open the gateway object which you want to use by clicking on its “Info” button.
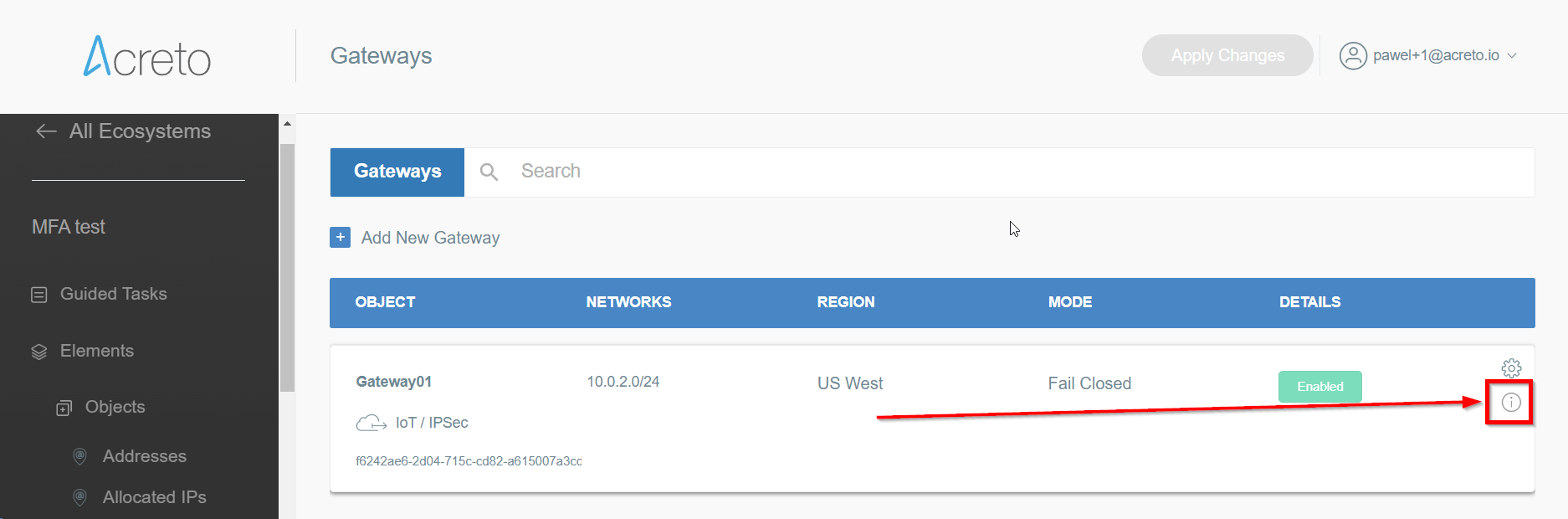

-
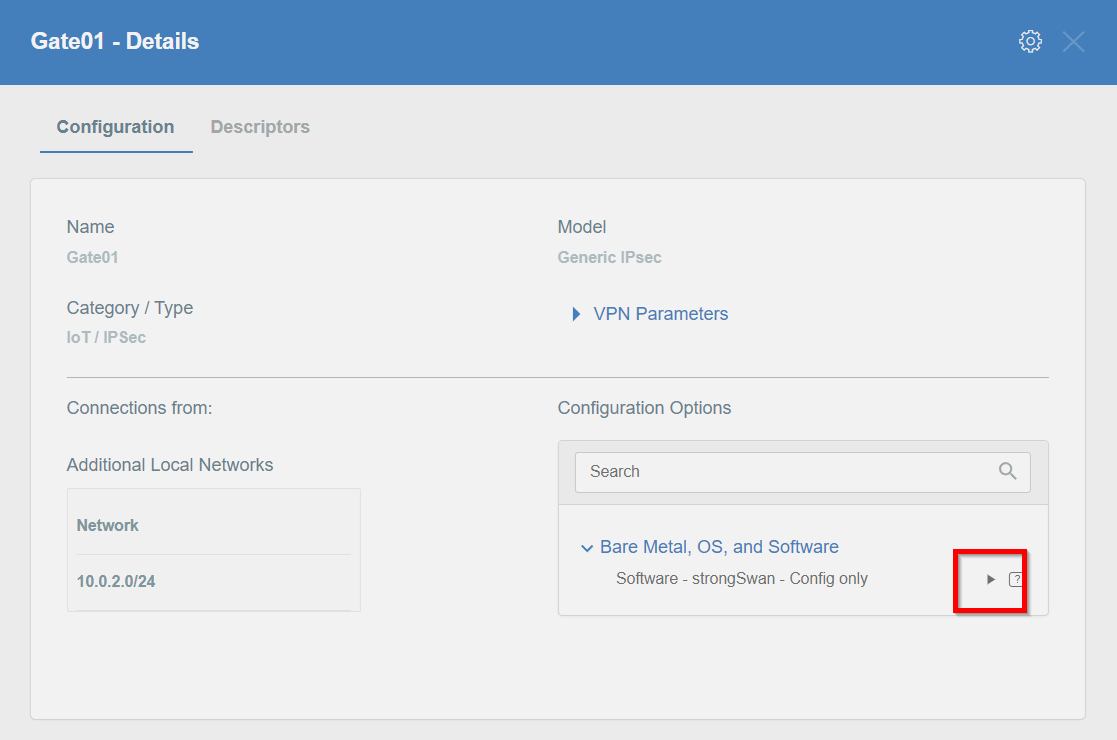
Generate the IPsec strongSwan config using Configuration Options >
Bare Metal, OS and Software
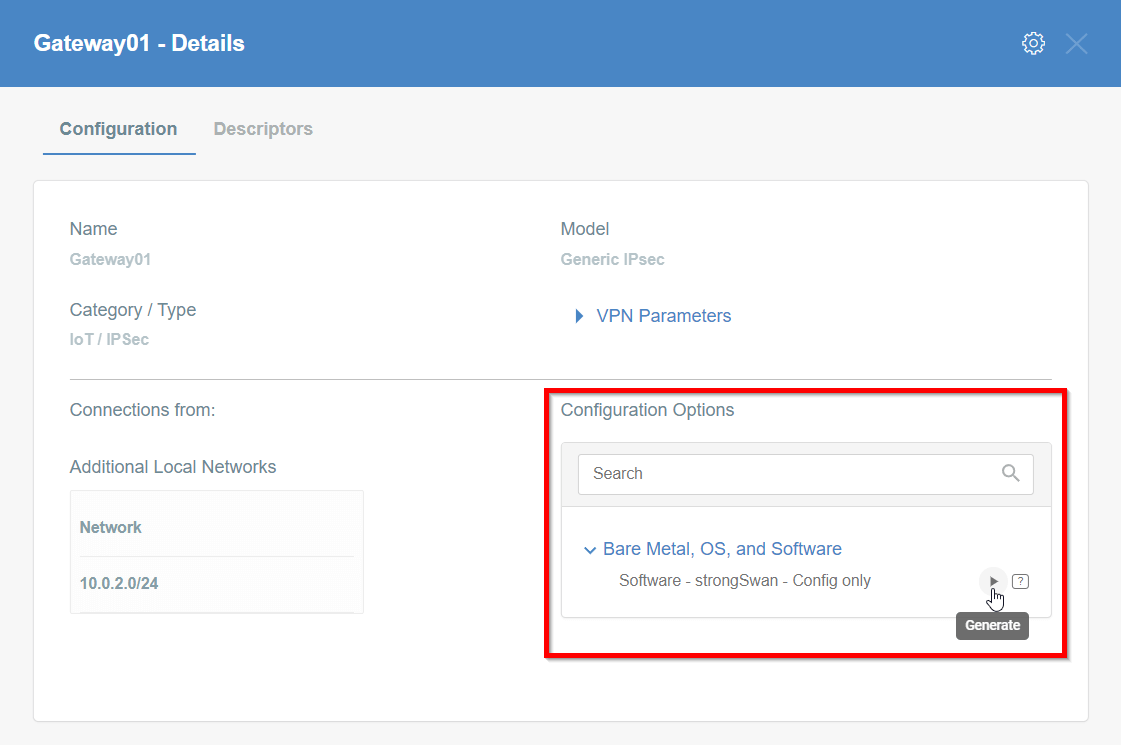

Then Click on [Play Button]
-
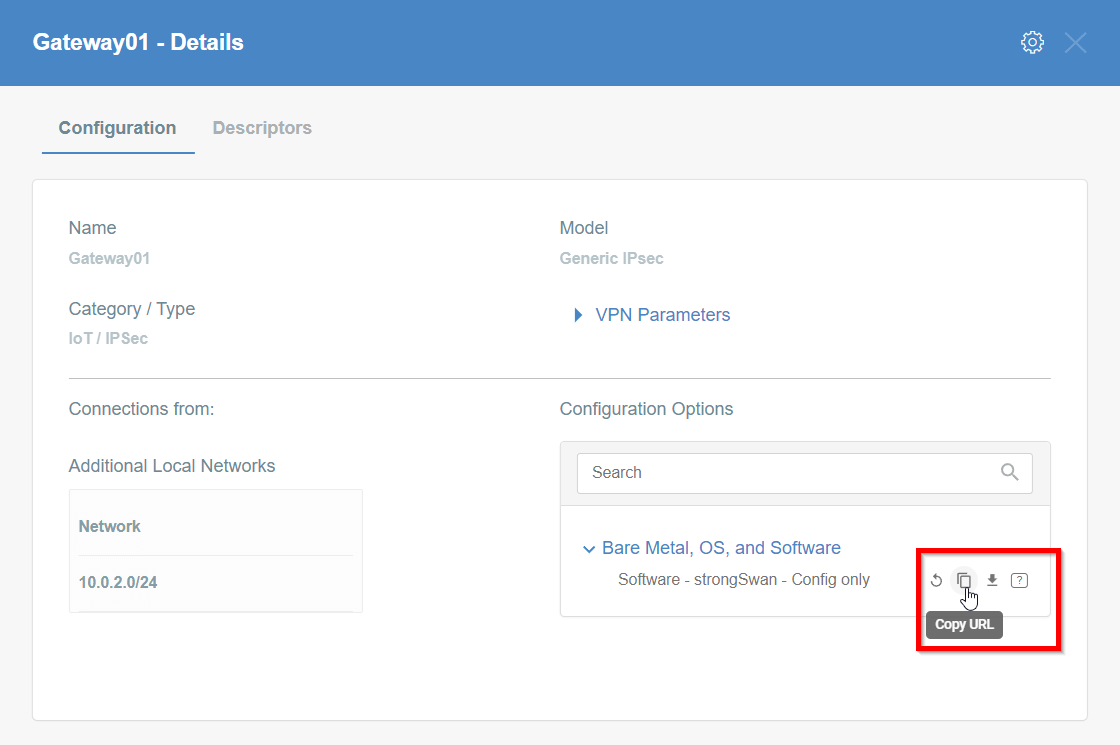
Copy the link to the IPsec strongSwan config file

Installation using acreto-ipsec.sh script
-
Execute the following commands on your Linux shell
curl -fsSL https://kb.acreto.net/reference-material/downloads/acreto-ipsec.sh | sudo bash -s -- [URL_to_strongswan_config]
where [URL_to_strongswan_config] is the URL copied in previous step.
Example:
curl -fsSL https://kb.acreto.net/reference-material/downloads/acreto-ipsec.sh | sudo bash -s -- https://api-is-rock-solid.acreto.net/v2/gateways/ipsec/config/strongswan?_token=s.WNJJeTxWsIeXMkgeIA96SOe8
IPsec tunnel and routing verification
-
Ensure that traffic goes through Acreto (with traceroute or mtr)
Execute the command:
The ouput should indicate that packets go through 100.65.0.x:
Host Loss% Snt Last Avg Best Wrst StDev
1. 100.65.0.30 0.0% 9 225.1 225.1 224.6 225.8 0.3
2. 100.65.0.1 0.0% 8 225.9 227.5 225.7 237.1 3.9
3. ???
4. nyk-b2-link.telia.net 0.0% 8 226.0 226.9 226.0 228.3 0.7
5. 72.14.218.254 0.0% 8 227.1 227.8 226.4 230.4 1.2
6. 108.170.248.97 0.0% 8 227.1 227.2 226.8 227.9 0.4
7. 108.170.227.211 0.0% 8 226.5 226.9 226.0 227.7 0.6
8. dns.google 0.0% 8 226.7 227.6 226.7 229.2 0.8
IPsec Operational Commands
-
Restart IPsec service with the following command: ipsec restart
-
Wait approximately 10 seconds, and check the status of IPsec: ipsec statusall
-
If the connection did not start, try to take it up manually:
CONN=`grep '^conn .*' /etc/ipsec.d/*.conf|cut -d' ' -f2`; echo $CONN
ipsec up $CONN
It should display information useful for debugging purposes.
-
Ensure everything works fine with:
ipsec statusall
ip address show
ip route show
-
Check if you have Internet access
IPsec Watchdog
In case you Internet connection if very unstable or your ISP changes your public IP, then you may consider running an IPsec watchdog that verifies every minute if the tunnel is passing the traffic to Acreto Ecosystem.
Please download the script and follow the steps from the comments section at the beginning of this script.
Click on the button and save the script in your home directory:
Get ipsec-watchdog.sh
or open the terminal and download the script directly to your vGateway using the command:
cd /etc/ipsec.d/
wget https://kb.acreto.net/reference-material/downloads/ipsec-watchdog.sh
Linux - Manual IPsec Configuration
Prerequisites
- Ubuntu 18.04 or newer installed on your device
- Ecosystem set up with proper security policies
Create Gateway for IPsec
If you didn’t do it yet, you need to create a new Gateway device on the Acreto
platform.
-
Log in to the Acreto platform at wedge.acreto.net
-
Select your ecosystem and go to Objects using the left menu.
-
Click Add new Object and select Gateway.
-
Fill at least:
-
Name: - the name of IPSec connection, needs to be compatible with
Strongswan connection name requirements (basically, only letters and
numbers)
-
Category: IoT
-
Allow connection from: Empty (describes the source IP address where the
IPsec connection will be permitted)
-
Local Networks: - your local network addresses that should be routed
through this gateway


Note: To simplify testing, add IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow testing connectivity from the gateway through Acreto using ping, traceroute, and similar tools.
-
Save the created Gateway by pressing Add.
-
Add security policy that will allow communication from the Gateway device to the Internet.

-
Commit pending changes (top of the screen)
Note: to successfully test your connectivity, you also need to create a
security policy that will allow traffic going through your device.
Generate Strongswan config files
-
Log in to the Acreto platform at
wedge.acreto.net
-
Select your ecosystem and go to Objects using the left menu
-
Open the gateway object which you want to use by clicking on its “Info” button.

-
Download Strongswan configuration using Configuration Options >
Software Clients with Config

-
Download Strongswan configuration to your device.
Install dependencies on the device
-
Log in to your device.
-
Set up time/date server, to do that use the following command:
sudo timedatectl set-ntp on
ntpdate -s ntp.ubuntu.com
-
Install required packages:
sudo apt-get update
sudo apt-get install -y --no-install-recommends \
apt-utils \
ifupdown2 \
inetutils-ping \
strongswan \
kmod \
openssl \
libstrongswan-standard-plugins
Apply configuration files
-
Log in to your device.
-
Unzip downloaded config file and copy respective files to their location:
unzip -x 10b6c4d8-0e9a-f5c7-c4c9-7edd6a6493ed.zip
sudo cp -r etc/* /etc
-
Ensure the files are in proper location
/etc/ipsec.d/[connection uuid].conf/etc/ipsec.d/leftifupdown.sh/etc/ipsec.secrets
Enable gateway mode (optional)
To work in gateway mode, you need to configure IPsec to use VTI devices.
Modify /etc/strongswan.d/charon.conf - leave all on defaults except for the
following:
install_routes = no
install_virtual_ip = no
ignore_routing_tables = 220
Modify connection file /etc/ipsec.d/*.conf to enable VTI support -
uncomment mark and leftupdown options:
# uncomment this line for policy routing configuration
mark=105
# uncomment this line for policy routing configuration
leftupdown=/etc/ipsec-leftupdown.sh
Determine connection name as defined in ipsec configuration:
CONN=`grep '^conn .*' /etc/ipsec.d/*.conf|cut -d' ' -f2`; echo $CONN
Create a routing file that will contain (remote) networks which should be
routed through the Acreto platform - by default, it would be a default gateway:
cat > /etc/ipsec.d/$CONN.route << EOF
0.0.0.0/0
EOF
Enable IP forwarding
echo net.ipv4.ip_forward=1 > /etc/sysctl.d/10_ac_ip_forward.conf
systemctl restart systemd-sysctl
sed -i'' -e s/auto=route/auto=start/ /etc/ipsec.d/*.conf
Start IPSec
-
Restart ipsec service with following command:
-
Wait approximately 10 seconds, and check status of ipsec:
-
If the connection did not start, try to take it up manually:
CONN=`grep '^conn .*' /etc/ipsec.d/*.conf|cut -d' ' -f2`; echo $CONN
ipsec up $CONN
It should display information useful for debugging purposes.
-
Ensure everything works fine with:
ipsec statusall
ip address show
ip route show
Check if you have Internet access enabled.
-
Check if you have Internet access enabled.
Validation
Ensure that traffic goes through our platform (with traceroute, mtr,). Verify
with the command below
Tunnel verification command
Expected output after successful tunnel creation
Host Loss% Snt Last Avg Best Wrst StDev
1. 100.65.0.30 0.0% 9 225.1 225.1 224.6 225.8 0.3
2. 100.65.0.1 0.0% 8 225.9 227.5 225.7 237.1 3.9
3. ???
4. nyk-b2-link.telia.net 0.0% 8 226.0 226.9 226.0 228.3 0.7
5. 72.14.218.254 0.0% 8 227.1 227.8 226.4 230.4 1.2
6. 108.170.248.97 0.0% 8 227.1 227.2 226.8 227.9 0.4
7. 108.170.227.211 0.0% 8 226.5 226.9 226.0 227.7 0.6
8. dns.google 0.0% 8 226.7 227.6 226.7 229.2 0.8
Palo Alto Networks IPsec Configuration
This section describes how to configure two IPSec VPN tunnels on a PA-200 firewall running version 9.1.x. Refer to Palo Alto Networks documentation for additional information about the web interface.
IPSec Connectivity Guide for Palo Alto Networks Firewall
The ethernet1/2 interface is connected to the internal corporate network. This interface will act as a gateway to the internal corporate network. The ethernet1/1 interface is the external interface. The internal network configuration will be in a trust security zone, and the external network interface configuration will be in an untrust security zone. Also, ensure that both interfaces use the same Virtual Router service.
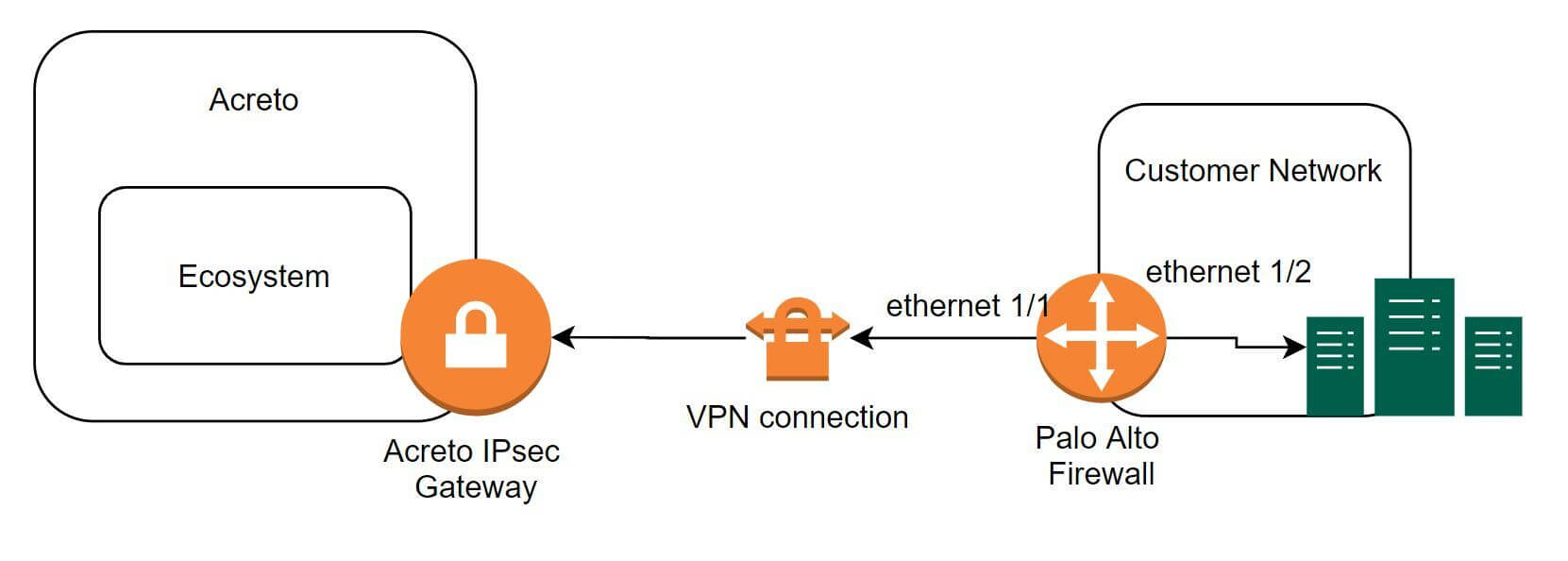

To configure the IPSec VPN tunnels on PA-200, complete the following tasks:
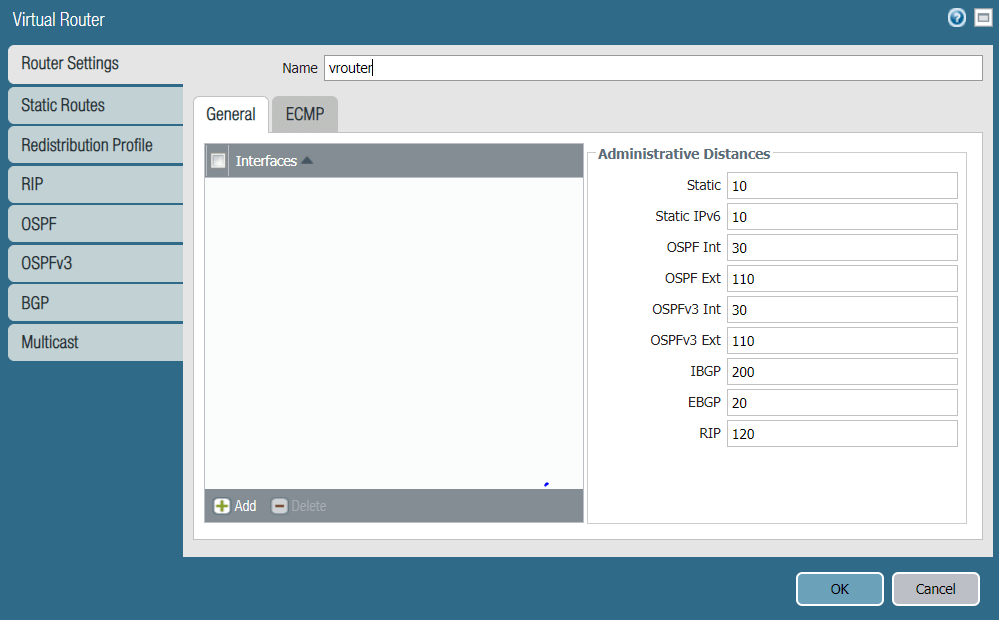
Task 1: Create a New Virtual Router
For this task, you will create a new Virtual Router. To configure the new Virtual Router:
- In the Palo Alto Networks web interface, go to Network → Virtual Routers.
- Click Add to add a new Virtual Router.
- Enter the Virtual Router name, in this case vrouter.
- Click OK to save the vRouter configurations.
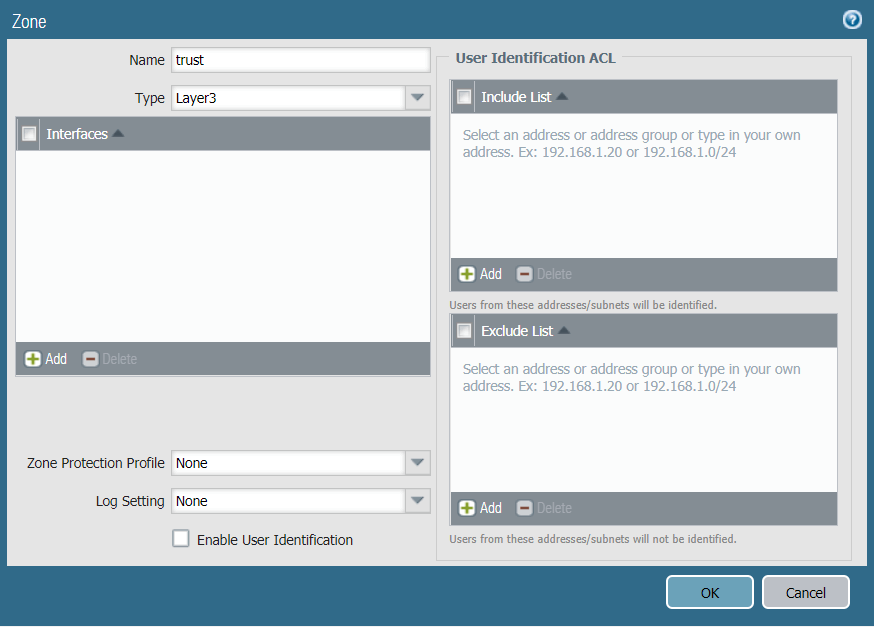
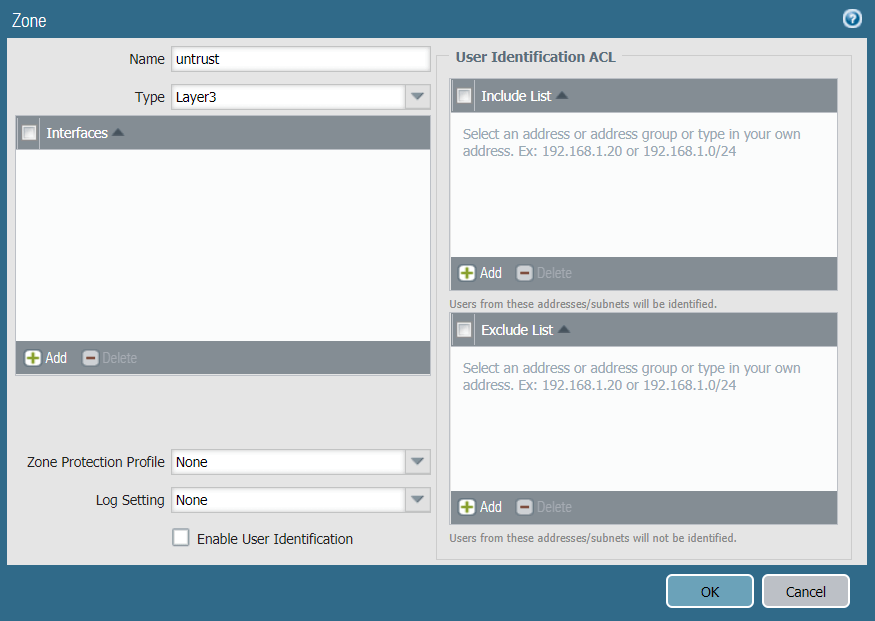
Task 2: Create New Zones
It is recommended to use separate zones to setup IPsec tunnels with PAN.
To configure trust and untrust zones, execute the following commands:
- In the Palo Alto Networks web interface, go to Network → Zones.
- Click Add to create a new zone.
- Enter the trust zone name, in this case trust. Choose zone type Layer3.
- Click OK to save the zone.
- Click Add to create a new zone.
- Enter the untrust zone name, in this case untrust. Choose zone type Layer3.
- Click OK to save the zone.
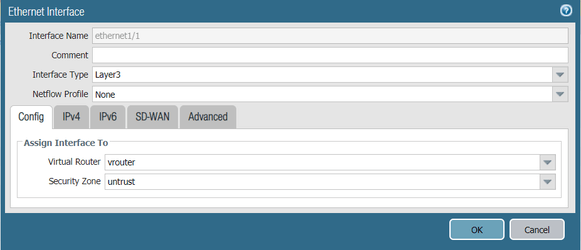
Task 3: Configuring the External Ethernet Interface
Configure the external network interface on PAN to be an untrust zone.
- In the Palo Alto Networks web interface, go to Network -> Interfaces
- Navigate to the Ethernet tab and click on Ethernet 1/1
- Set the Interface Type to Layer3
- Configure the ethernet 1/1, assign it to an untrust zone and connect to vrouter Virtual Router
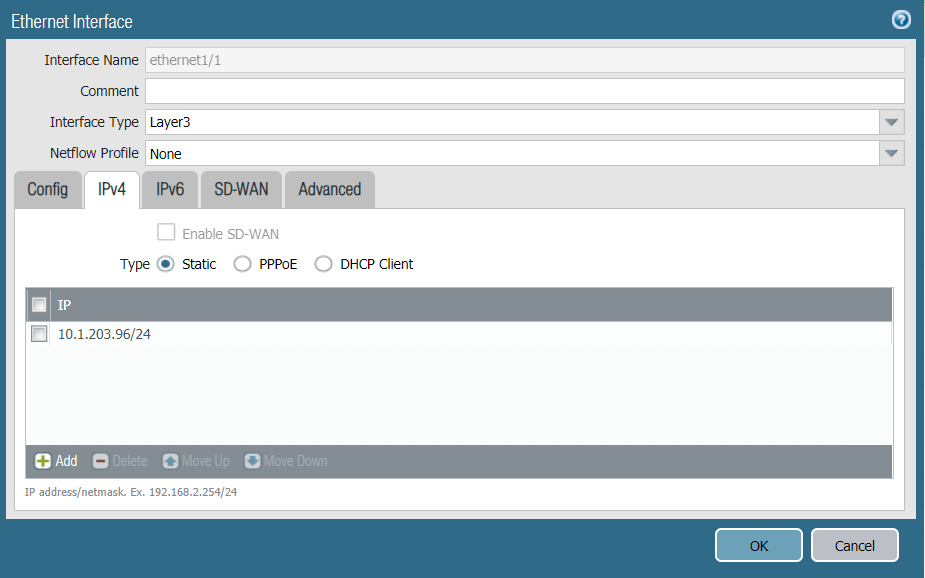
- Configure the IP address on the external network, in this example 10.1.203.96/24
- Click OK to save the configurations
Task 4: Configuring the Internal Ethernet Interface
Configure the internal network interface on PAN to be a trust zone.
- In the Palo Alto Networks web interface, go to Network -> Interfaces.
- Navigate to the Ethernet tab and click on Ethernet 1/2.
- Set the Interface Type to Layer3.
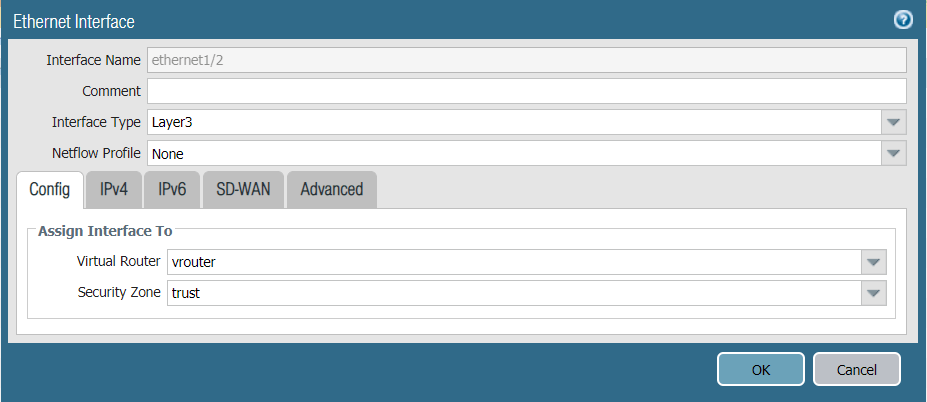
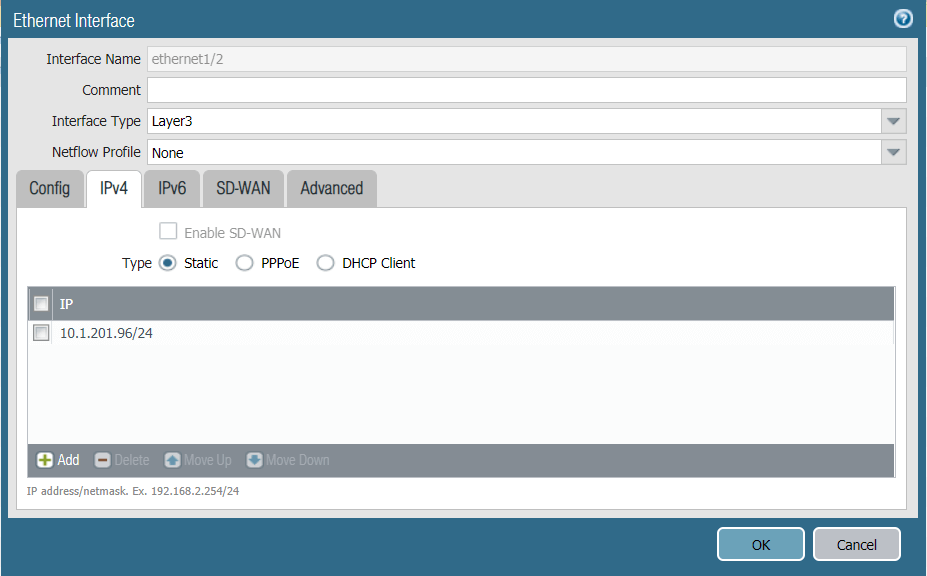
- Configure the ethernet 1/2, assign it to a trust zone and connect to vrouter Virtual Router.
- Configure the IP address on the internal interface, in this case 10.1.201.96/24.
- Click OK to save the configurations.
Task 5: Configuring the Tunnel Interfaces
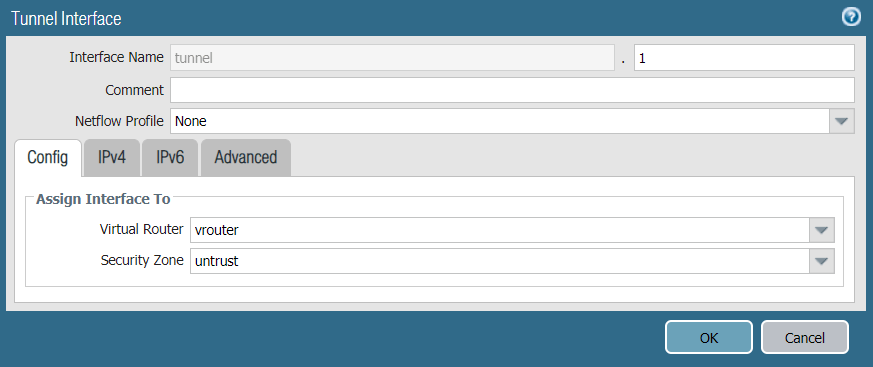
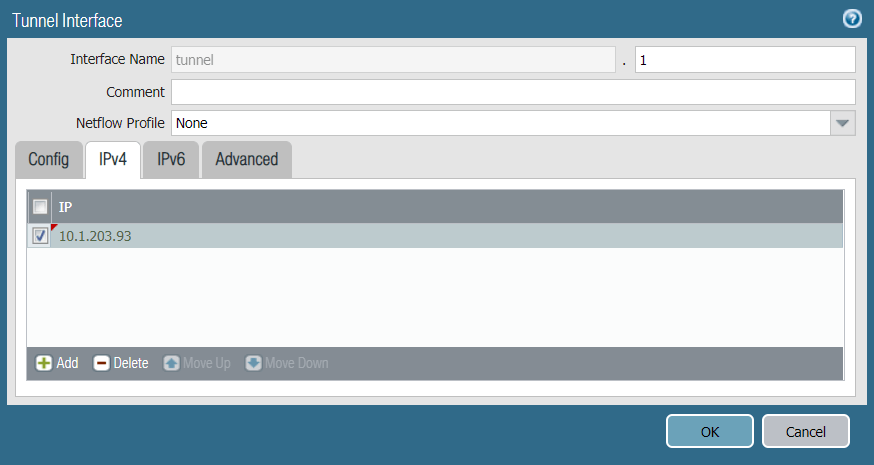
Configure the tunnel interface on the external interface (ethernet1/1). Ensure the tunnel is configured in the untrust security zone. In this example, the tunnel interface is named tunnel.1 with a source IP address 10.1.203.93.
To configure the primary tunnel interface:
- In the Palo Alto Networks web interface, go to Network -> Interfaces.
- Click the Tunnel tab.
- Click Add to create a new tunnel interface.
- In the Tunnel Interface window, complete the following:
- Interface Name: Enter a name for the tunnel interface, such as tunnel.1.
- Netflow Profile: Choose the appropriate NetFlow profile. In this example, it’s None.
- Comment: Enter additional notes or information (optional).
- Assign Interface To:
- Virtual Router: Choose vrouter.
- Security Zone: Choose untrust.
- Under the IPv4 tab, assign IP address 10.1.203.93 to the tunnel.1 interface.
- Click OK to save the tunnel interface.
- Click *Commit to apply the configurations.
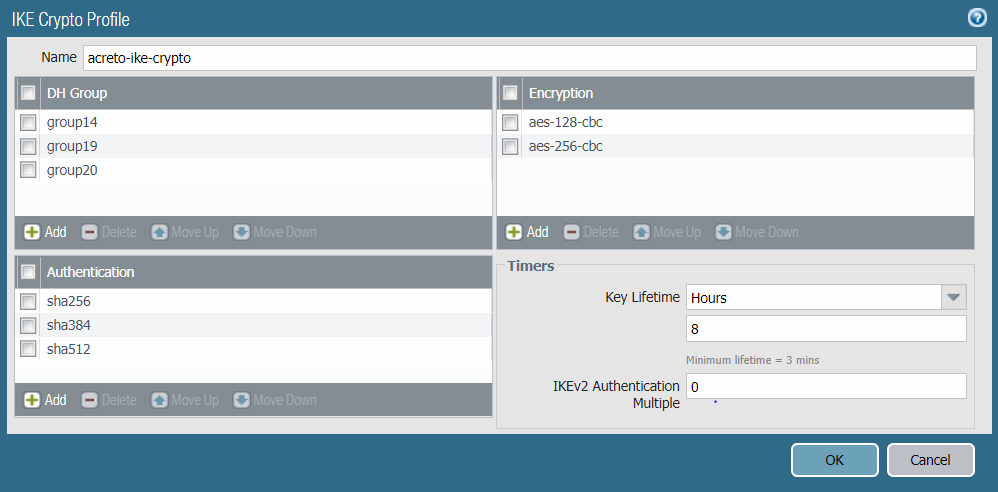
Task 6: Creating the IKE Crypto Profile
Create an IKE crypto profile that specifies the security settings for the IKE phase 1 negotiations.
To create an IKE crypto profile:
- In the Palo Alto Networks web interface, go to Network.
- Expand Network Profiles.
- Select IKE Crypto.
- Click Add to create an IKE crypto profile.
- In the IKE Crypto Profile window, complete the following:
- Name: Enter a name for the IKE crypto profile. In this case: acreto-ike-crypto.
- DH Group: Click Add and choose group14, group19, group20.
- Encryption: Click Add and choose aes-128-cbc aes-256-cbc.
- Authentication: Click Add and choose sha256, sha384, sha512.
- Lifetime: Set it to 8 hours.
- Click OK to save configurations.
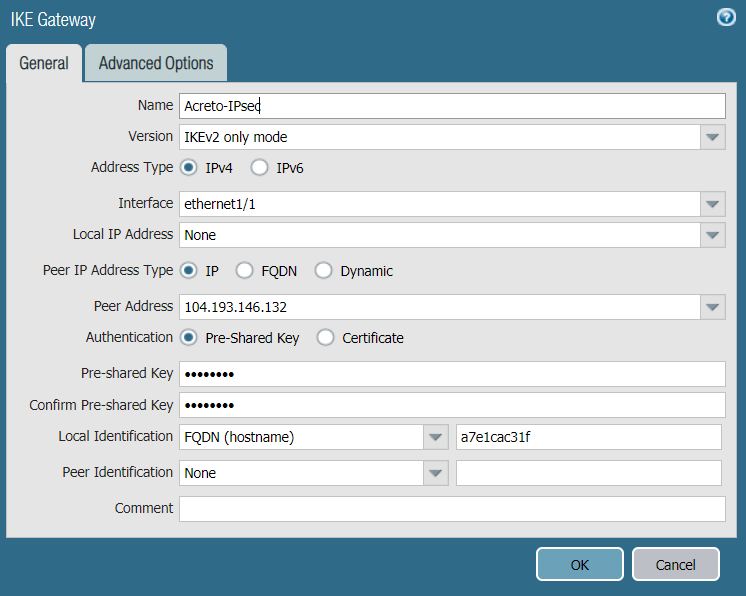
Task 7: Creating the IKE Gateway
Create IKE gateways using the Acreto Gateway IP address. In this case: 104.193.146.132.
To create the primary IKE gateway:
- In the Palo Alto Networks web interface, go to Network.
- Expand Network Profiles.
- Click IKE Gateways.
- Click Add.
- In the IKE Gateway window, complete the following:
- Name: Enter a name for the IKE gateway, such as Acreto-IPsec.
- Version: Select IKEv2 only mode.
- Interface: Choose the external interface ethernet 1/1.
- Local IP Address: Choose None.
- Peer IP Type: Choose Static.
- Peer IP Address: Enter the Acreto Gateway address for the primary gateway. In this case, it's 104.193.146.132.
- Pre-shared Key: Enter the pre-shared key you generated in the Acreto web Portal.
- Confirm Pre-shared Key: Reenter the pre-shared key.
- Local Identification: Enter the Peer ID from the Acreto Web Portal.
- Peer Identification: Choose None.
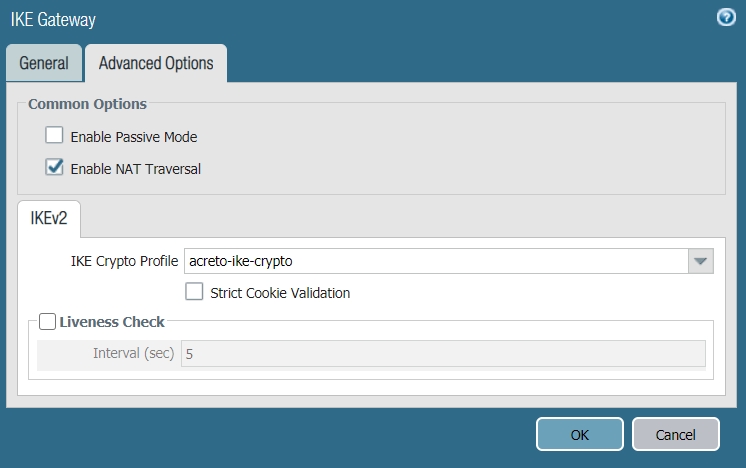
- Show Advanced Phase 1 Options: Select to show the following options.
- IKE Crypto Profile: Choose the IKE crypto profile you created in the previous step. In this case, it's acreto-ike-crypto.
- Enable Passive Mode: Deselect.
- Enable NAT Traversal: Select.
- Liveness Check: Deselect.
- Below are reference snapshots of the IKE gateway configurations.
- Click OK to save configurations.
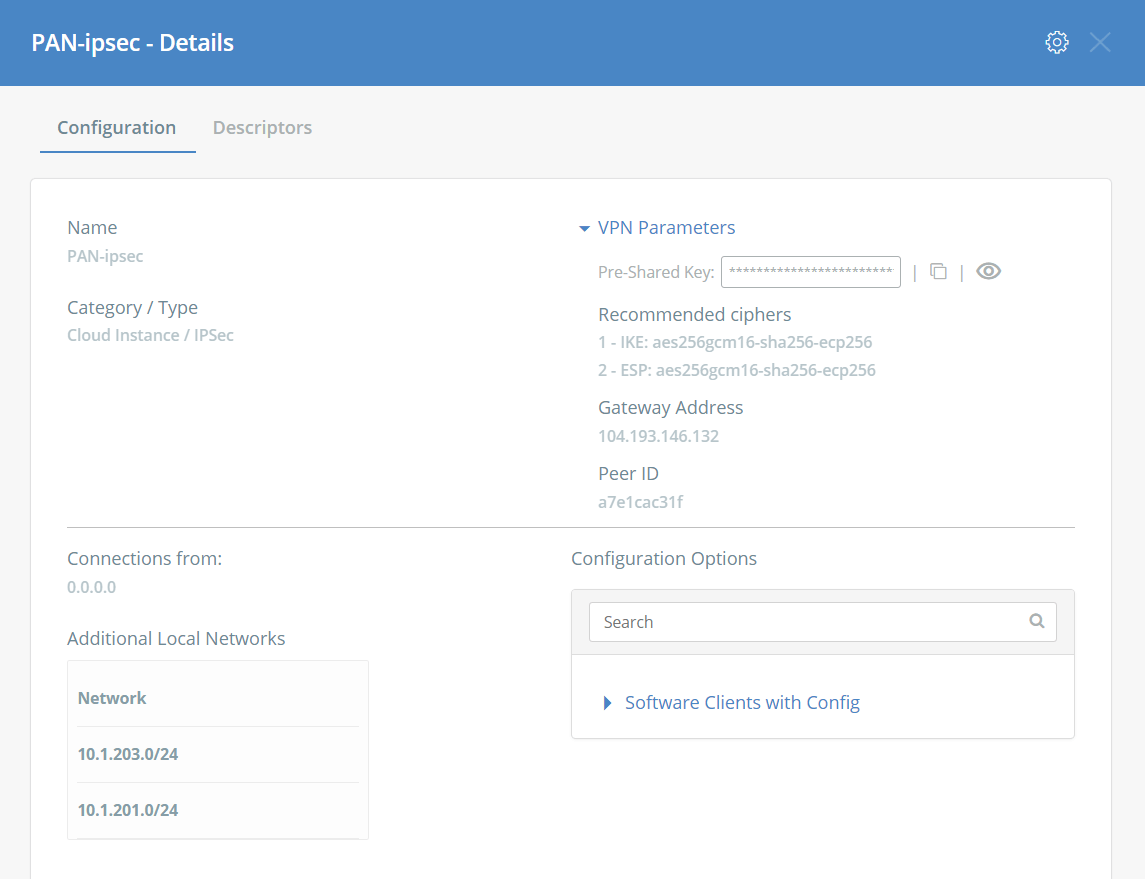
Note: To view the Acreto Web Portal information, complete the following steps:
- Log in to https://wedge.acreto.net/.
- Click on the Ecosystem you want to connect to.
- Navigate to Elements → Objects → Gateways.
- Navigate to the gateway you want to connect to and click the Information sign on the right.
- A new window will appear. Click on “VPN Parameters” to expand the details:
- From here you can view the Pre-Shared Key, Gateway Address and Peer ID.
- These parameters will be used for Task #7.
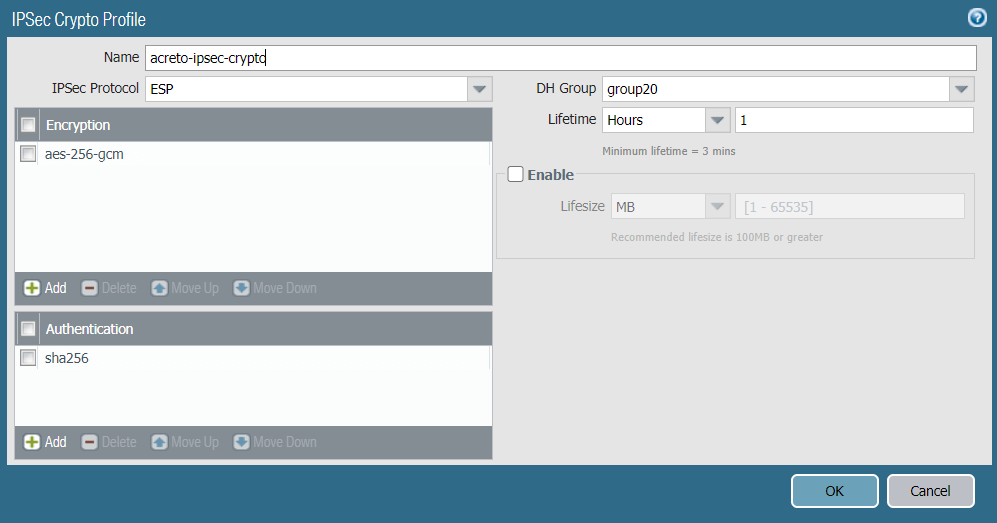
Task 8: Creating the IPSec Crypto Profile
Create an IPSec crypto profile that specifies the security parameters for the IKE phase 2 negotiations.
To create an IPSec crypto profile:
- In the Palo Alto Networks web interface, go to Network.
- Expand Network Profiles.
- Click IPSec Crypto.
- Click Add to create a IPSec crypto profile.
- In the IPSec Crypto Profile window, complete the following:
- Name: Enter a name for the IPSec crypto profile, such as acreto-ipsec-crypto.
- IPSec Protocol: Ensure ESP is chosen.
- Encryption: Click Add and choose aes-256-gcm to encrypt the traffic.
- Authentication: Click Add and choose sha256.
- DH Group: Ensure group20 is chosen.
- Lifetime: Set it to 1 Hour.
- Lifesize: Set the lifesize according to your incoming traffic volume (optional).
- Reference snapshot of IPsec crypto profile.
- Click OK to save configurations.
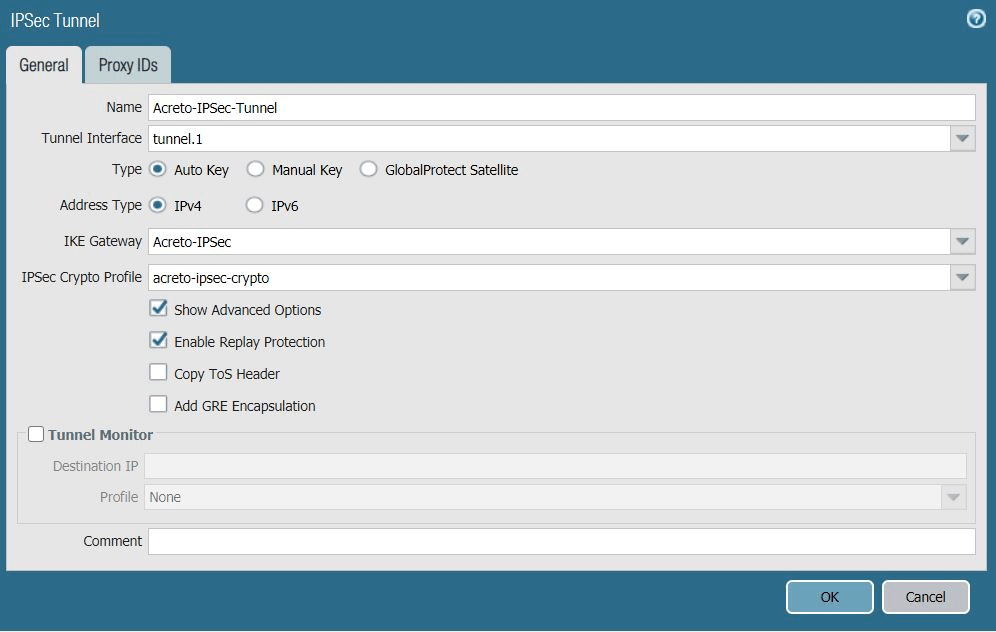
Task 9: Creating the IPSec VPN Tunnels
Configure the IPSec VPN Tunnel using the Acreto Gateway Address. In this case, 104.193.146.132
To create the IPSec VPN tunnel:
- In the Palo Alto Networks web interface, go to Network -> IPSec Tunnels.
- Click Add to create a new IPSec tunnel.
- In the IPSec Tunnel window under the General tab, complete the
following:
- Name: Enter a name for the tunnel, such as Acreto-IPsec-Tunnel.
- Tunnel Interface: Choose the tunnel interface you created in Configuring the Tunnel Interfaces. In this case, it's tunnel.1.
- Type: Ensure Auto Key is chosen.
- IKE Gateway: Choose the primary IKE gateway you created in Creating the IKE Gateway section. In this case, it's Acreto-IPsec.
- IPSec Crypto Profile: Choose the IPSec crypto profile you created in Creating the IPSec Crypto Profile. In this case, it's acreto-ipsec-crypto.
- Show Advanced Options: Select to show the following options.
- Enable Replay Protection: Select.
- Copy TOS Header: Deselect.
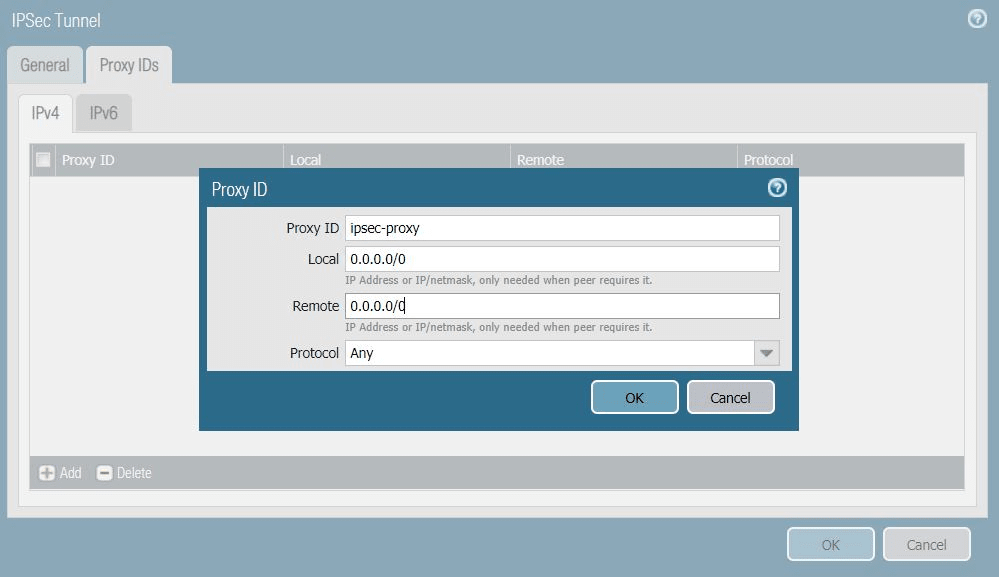
- In the Proxy IDs tab, click Add and complete the following:
- Proxy ID: Enter a name for the proxy.
- Local: Enter the local IP address 0.0.0.0/0.
- Remote: Enter the remote IP address 0.0.0.0/0.
- Protocol: Ensure Any is chosen.
- Click OK to save the proxy ID.
- Click OK again to save the IPSec tunnel configurations.
- Reference configuration for the IPSec Tunnel is described in the snapshots below:
- Click Commit to apply configurations on PAN.
Task 10: Defining the Policy-Based Forwarding Rule
Defining two policy-based forwarding rules to route the traffic from the Palo Alto Network appliance into the tunnel.
To define the primary policy-based forwarding rule:
- In the Palo Alto Networks web interface, go to Policies -> Policy-Based Forwarding.
- Click Add to create a new rule.
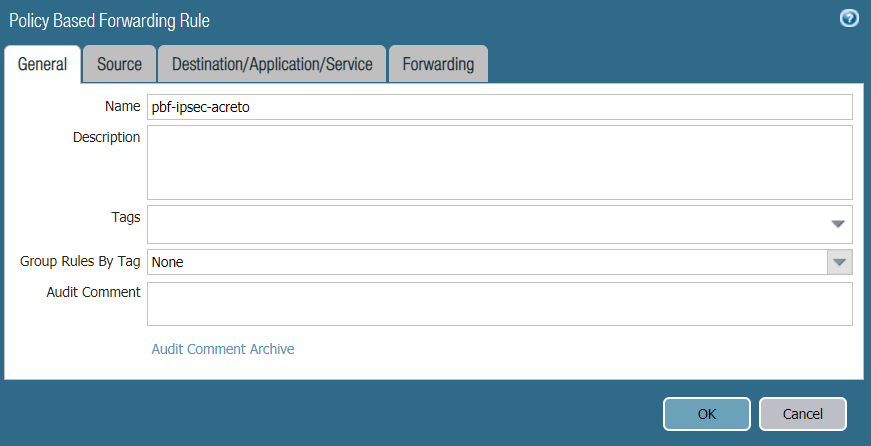
- In the General tab, complete the following:
- Name: Enter a name for the policy, such as
pbf-ipsec-acreto.
- Description: Enter a description (optional).
- Tags: Choose a tag (optional).
- Reference configurations are described in the image below:
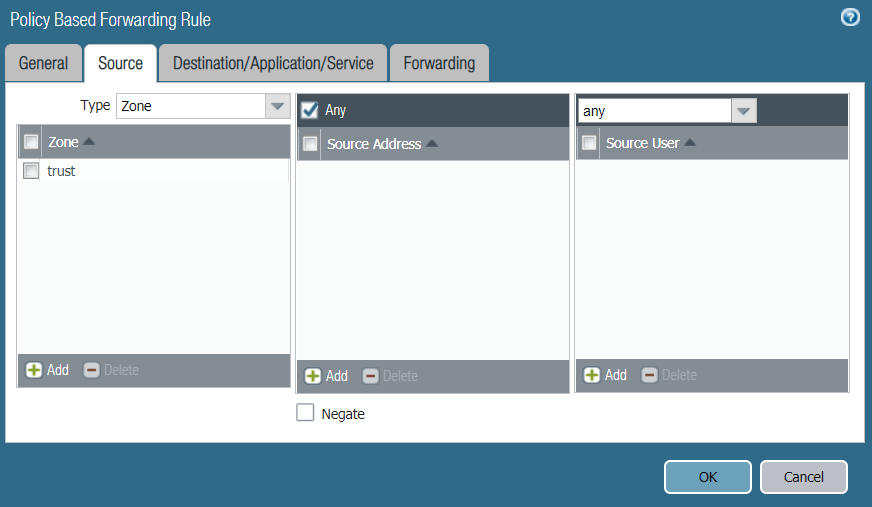
- In the Source tab, choose Type Zone. Under Zone, click Add and choose trust. Reference configurations of the Source tab are below:
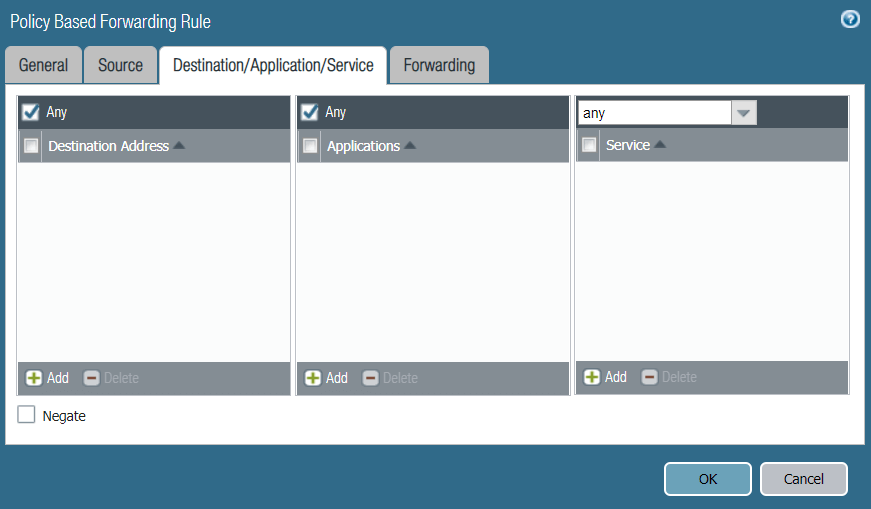
- In the Destination/Application/Service tab, complete the following:
- Destination Address: Ensure Any is selected.
- Applications: Ensure Any is selected.
- Service: Ensure Any is selected.
- Reference configurations of this tab are described in the image below:
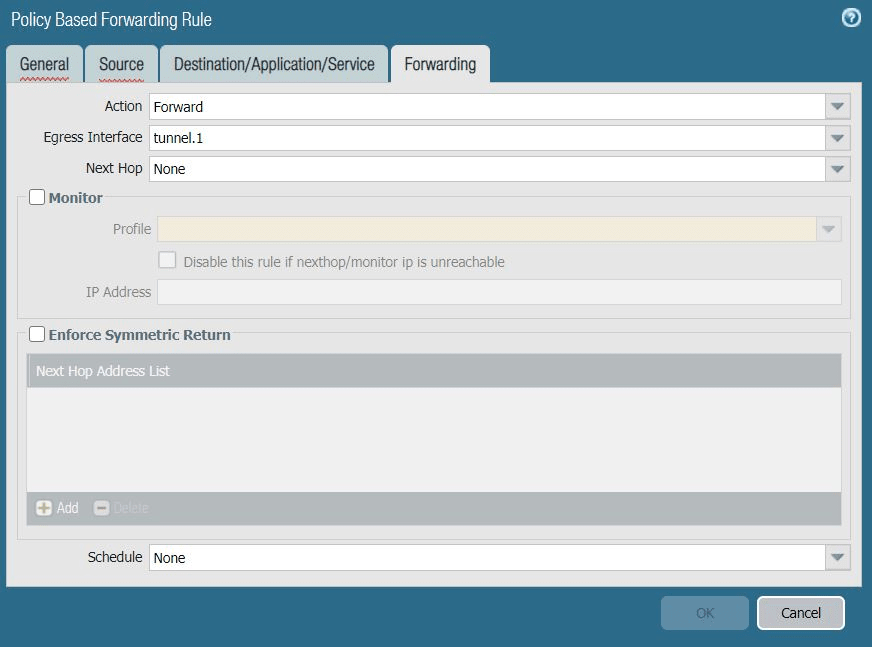
- In the Forwarding tab, complete the following:
- Action: Choose Forward.
- Egress Interface: Choose the primary tunnel interface you created in task 5. Configuring the Tunnel Interfaces. In
this case, it's tunnel.1.
- Next Hop: Leave this field blank.
- Monitor: Deselect.
- Enforce Symmetric Return: Deselect.
- Schedule: Choose None.
- Reference configurations for this tab are described in the image below:
- Click OK to save the configurations.
- Commit the changes in PAN.
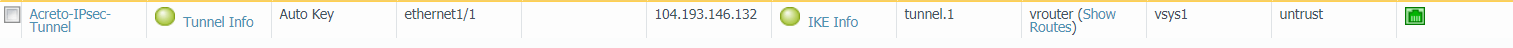
Task 11: IPSec Tunnel Status
Once completing the above step, the IPsec tunnel will be established between PAN
and the Acreto IPsec Gateway. To check the status of the tunnel, navigate to
Network → IPSec Tunnels and view the tunnel status. A green
color status signifies that the tunnel is established correctly.

To validate the network traffic going from PAN to the Acreto IPsec gateway,
routes must be configured in the virtual router in PAN. Execute
the following steps to configure the routes:
- In the Palo Alto Networks web interface, go to Networks -> Virtual Routers.
- Click on the router that was created in the previous task, in this case vrouter.
- From the left panel, select Static Routes.
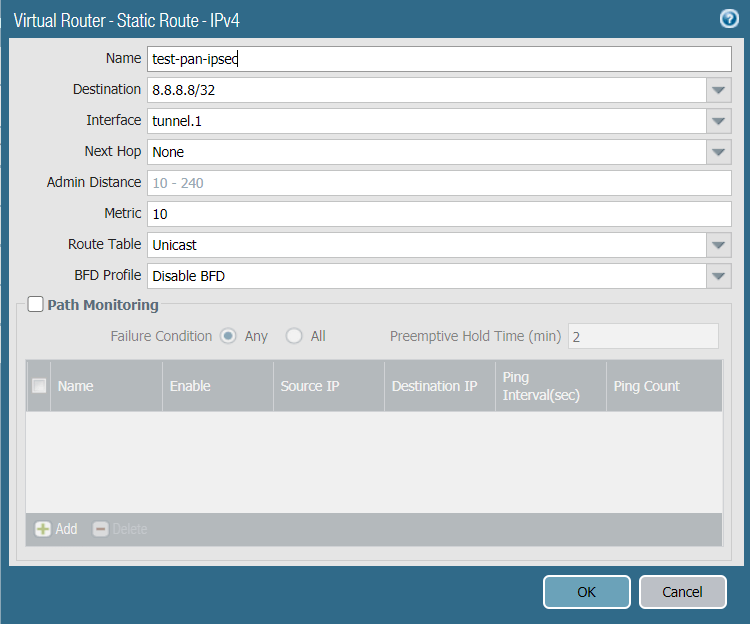
- Click Add to add a new route.
- Configure the route fields according to the details below:
- Name: test-ipsec-pan.
- Destination: 8.8.8.8/32.
- Interface: tunnel.1.
- Next Hop: None.
- Admin Distance:
- Metric: 10.
- Route Table: Unicast.
- BFD Profile: Disable BFD.
- Path Monitoring: Deselect.
- Reference configurations of this route are described in the image below:
- Click OK to save the configurations.
- Click Commit to apply the configurations.
Task 13: Verifying the Connectivity
In this section, the connectivity between PAN and Acreto gateway will be
verified.
-
SSH to the PAN device.
-
Run the following command below:
ping source <tunnel.1 IP address> host 8.8.8.8
-
The ping should work with a sample output like below:
PING 8.8.8.8 (8.8.8.8) from 10.1.203.93 : 56(84) bytes of data.
64 bytes from 8.8.8.8: icmp\_seq=1 ttl=116 time=7.98 ms
64 bytes from 8.8.8.8: icmp\_seq=2 ttl=116 time=4.76 ms
64 bytes from 8.8.8.8: icmp\_seq=3 ttl=116 time=4.24 ms
64 bytes from 8.8.8.8: icmp\_seq=4 ttl=116 time=4.90 ms
64 bytes from 8.8.8.8: icmp\_seq=5 ttl=116 time=4.99 ms
-
You should be able to see these traffic logs in the Acreto Reports dashboard. Navigate to the Ecosystem and from the left panel, select
Reports. Below is a sample of the reports from the Acreto Web Portal:
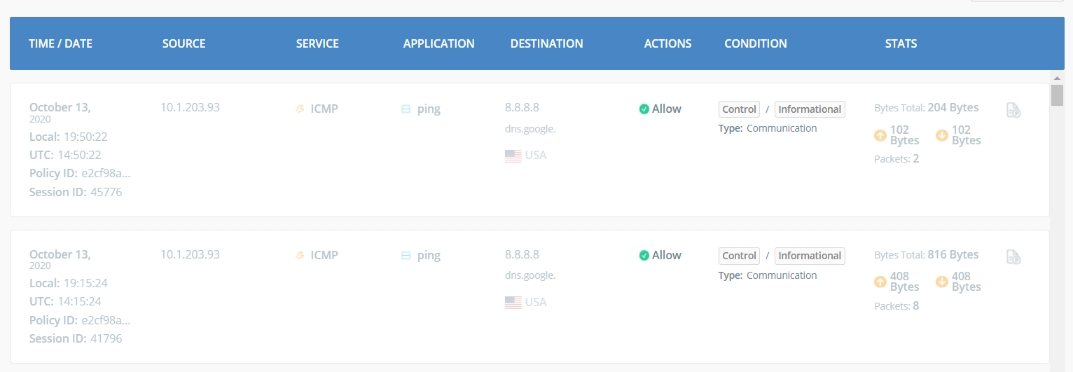

Pfsense Ipsec with Acreto
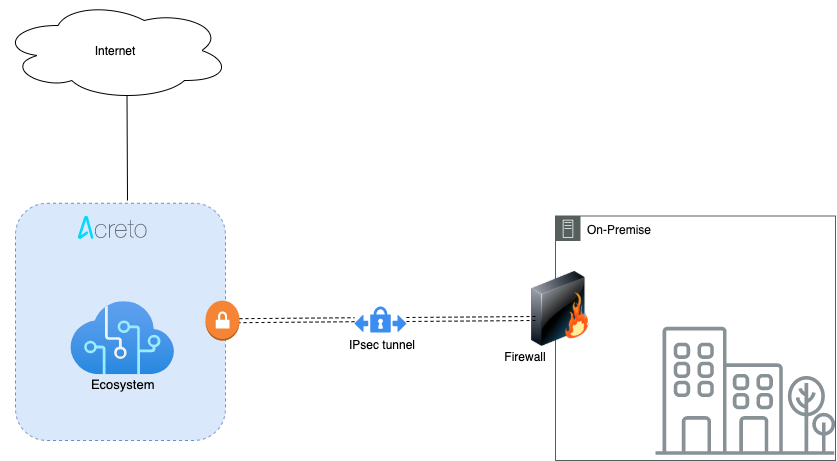
Overview
This article will help you connect and secure your pfSense installation with Acreto Ecosystem.

Prerequisites
- pfSense installation.
- Ecosystem set up with proper security policies.
Create Gateway for IPsec
Firstly, you will need to create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
- Name: IPsec connection name must meet the exact requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed through this gateway.


Info
To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow you to test connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
How-To
Task 1: Read IPsec Gateway Values Required for IPsec Configuration
To proceed with the pfSense configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All of these may be found within the Gateway details panel - view the below animation for further instruction.
-
Log in to your pfSense panel.
-
Go to VPN > IPsec. Click on Add P1 to configure the Phase 1 settings.
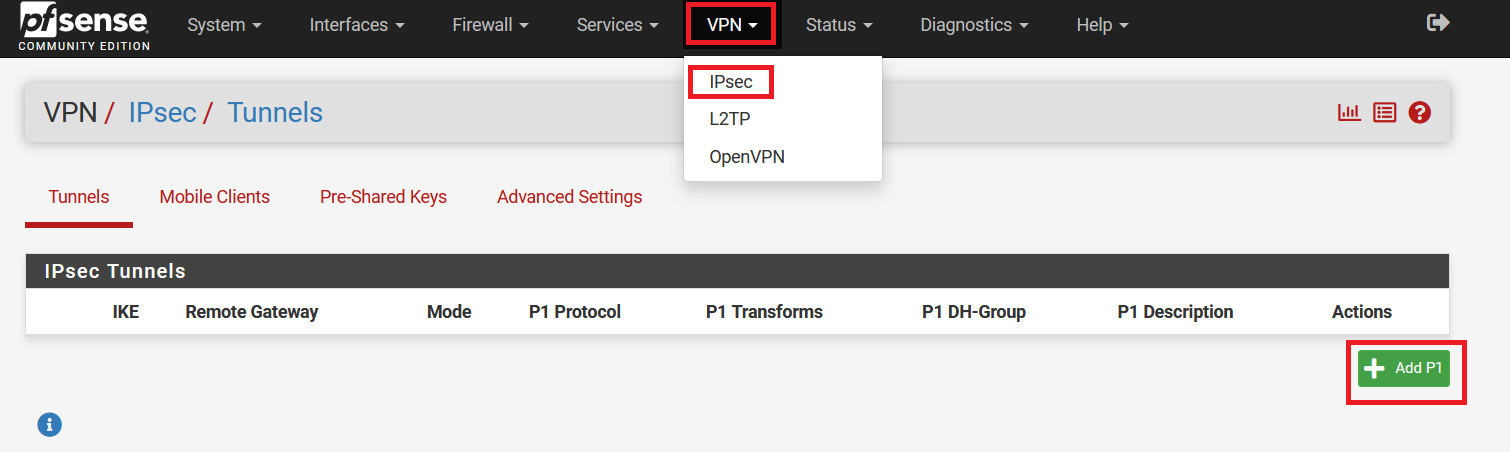

-
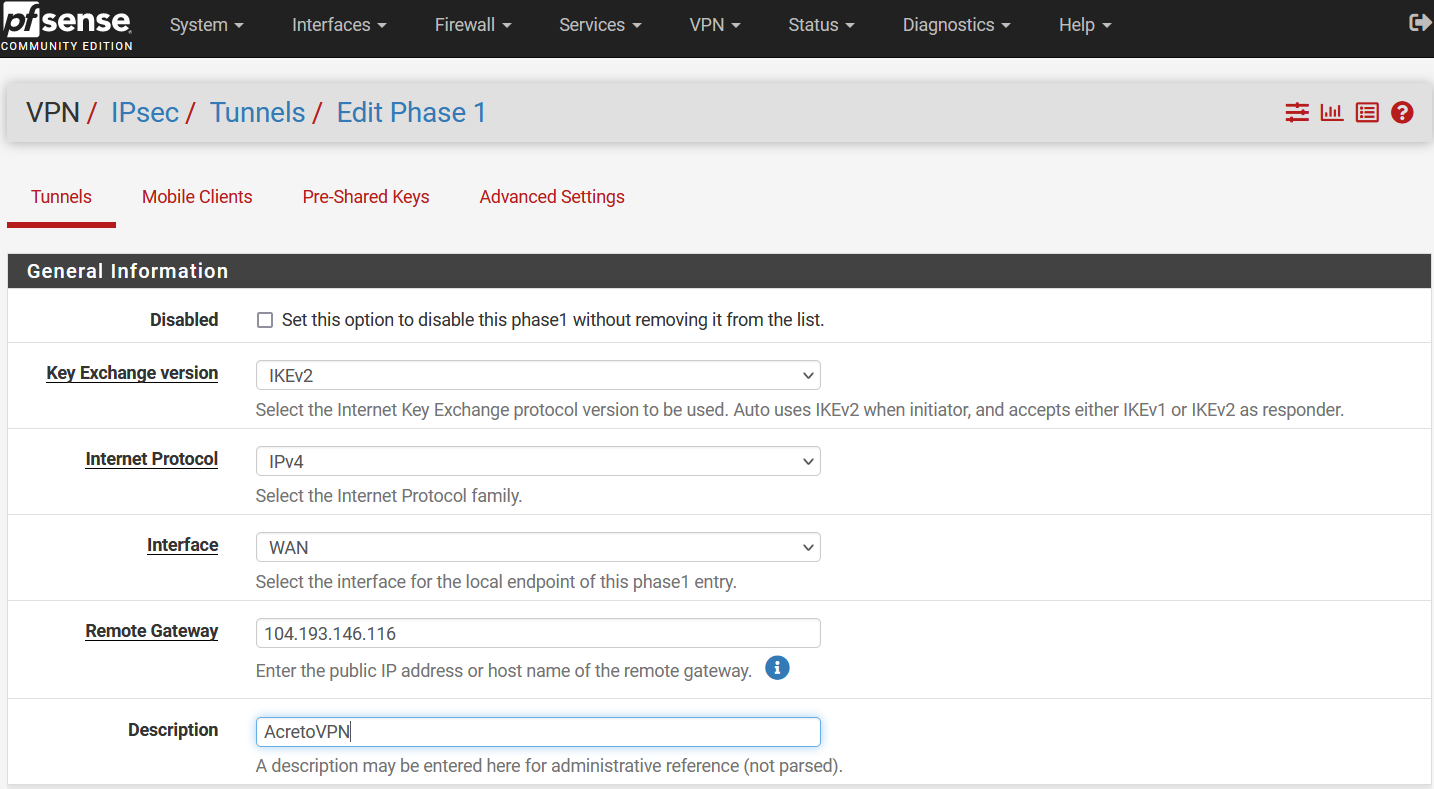
In the following window, configure VPN Phase1 settings as below:
- General Information:
- IKE Exchange Version: IKEV2
- Internet Protocol: IPv4
- Interface: WAN
- Remote Gateway: Acreto Peer IP
- Description: AcretoVPN

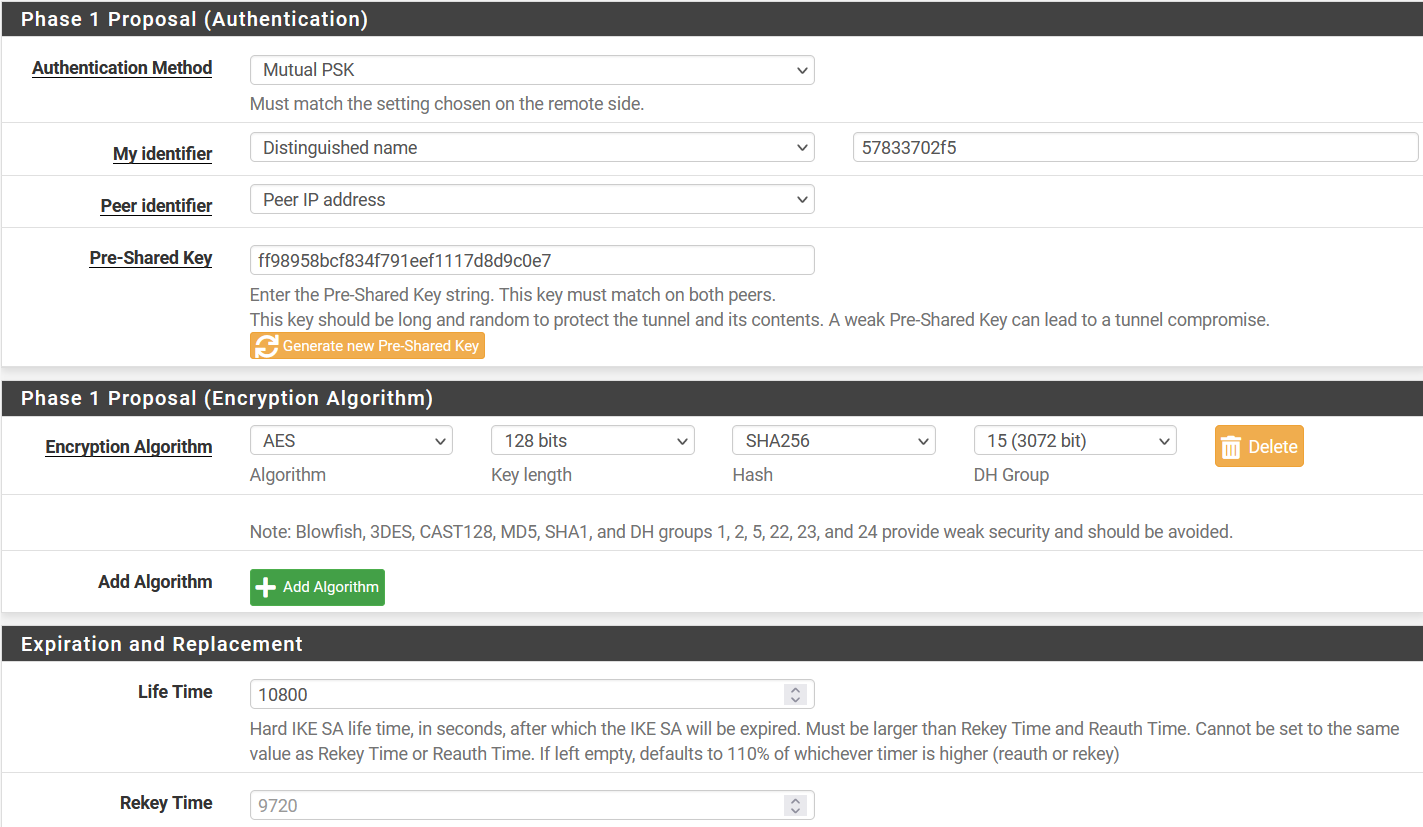
- Phase 1 Proposal (Authentication)
- Authentication Method: Mutual PSK
- My Identifier: select Distinguished Name and use Peer ID in the value field.
- Pre-Shared Key: PSK
- Phase 1 Proposal (Encryption Algorithm)
- Encryption Algorithm: AES 128 SHA256 15(3072)
- Expiration and Replacement
- Lifetime: 10800

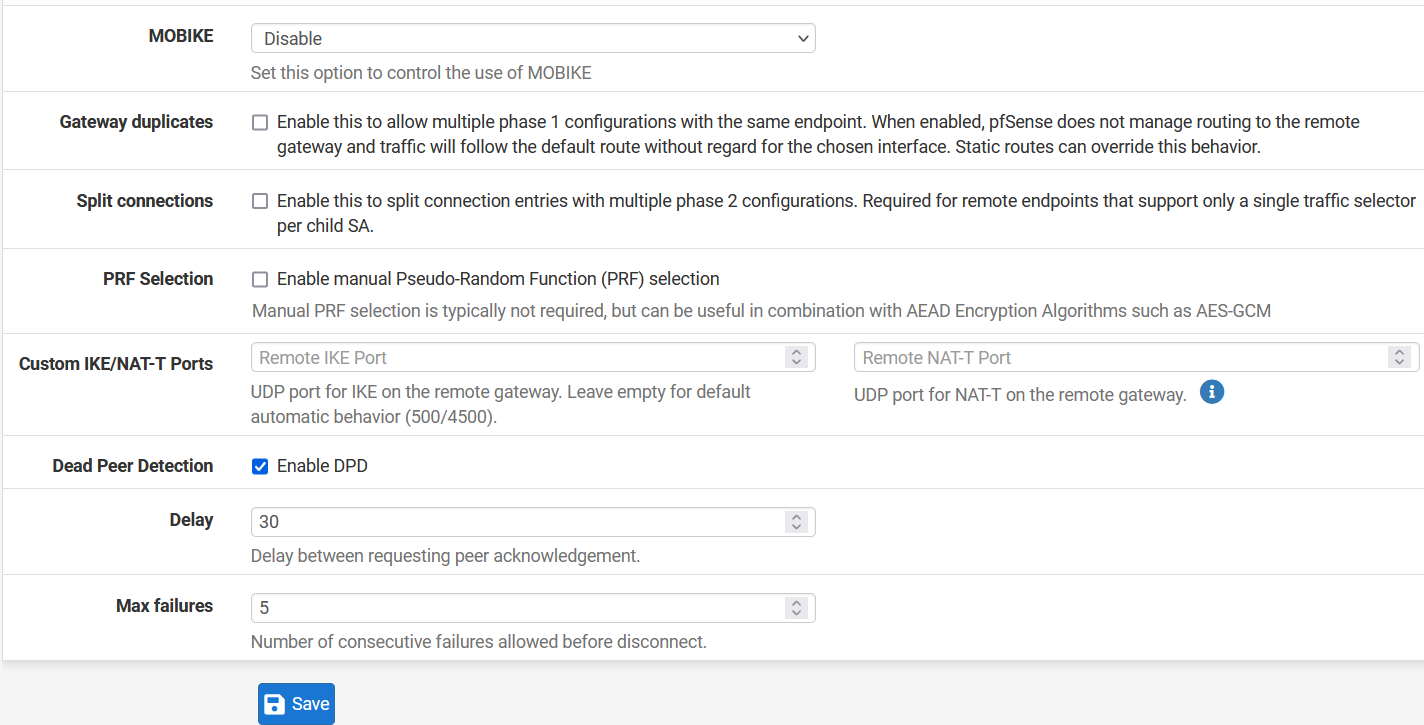
- Advanced Options
- Dead Peer Detection: Enable
- Delay: 30
- Max Failures: 5
-
Click Save to save the configuration.

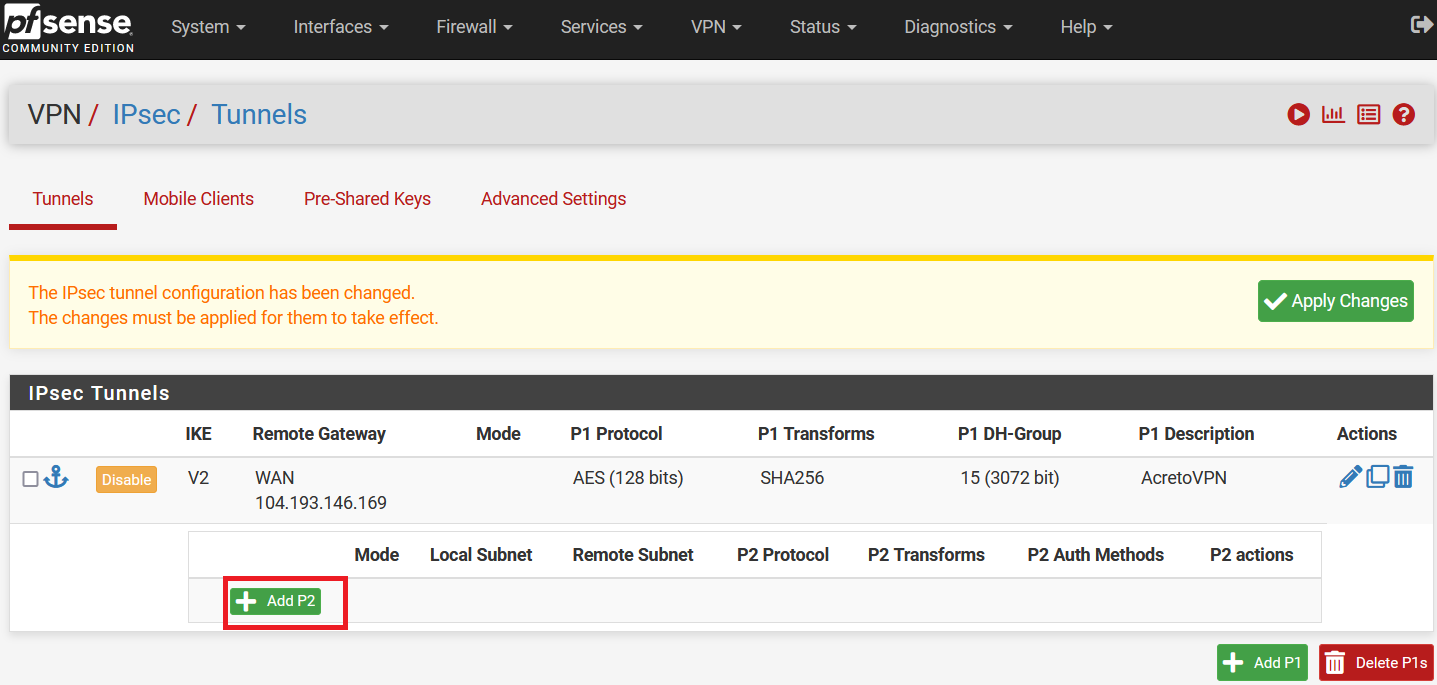
-
Click on Show Phase 2 Entries and Click on Add P2.

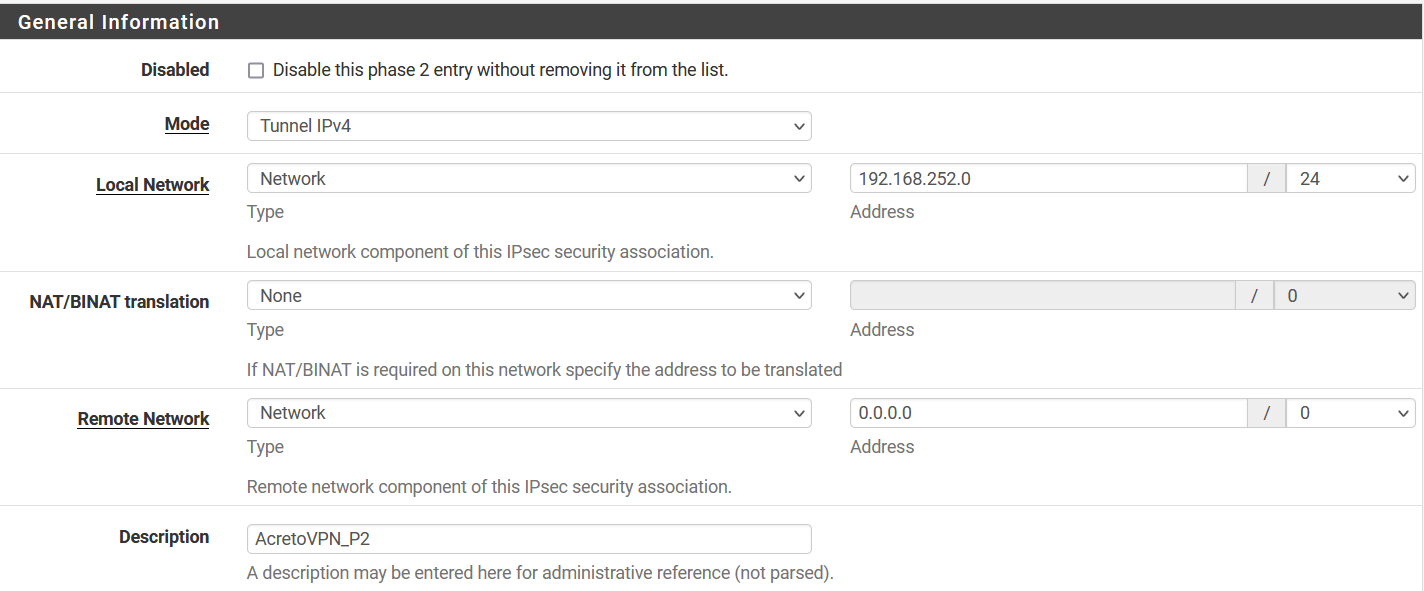
-
In the next window, configure the Phase 2 setting as below:
- General Information:
- Mode: Tunnel IPv4
- Local Network: Select Network and enter local network address 192.168.252.0/24
- Remote Network: Select Network and enter 0.0.0.0/0
- Description: AcretoVPN_P2

- Phase 2 Proposal (SA/Key Exchange)
- Protocol: ESP
- Encryption Algorithm: AES 128
- Hash Algorithm: SHA256
- PFS key group: 15 (3072)
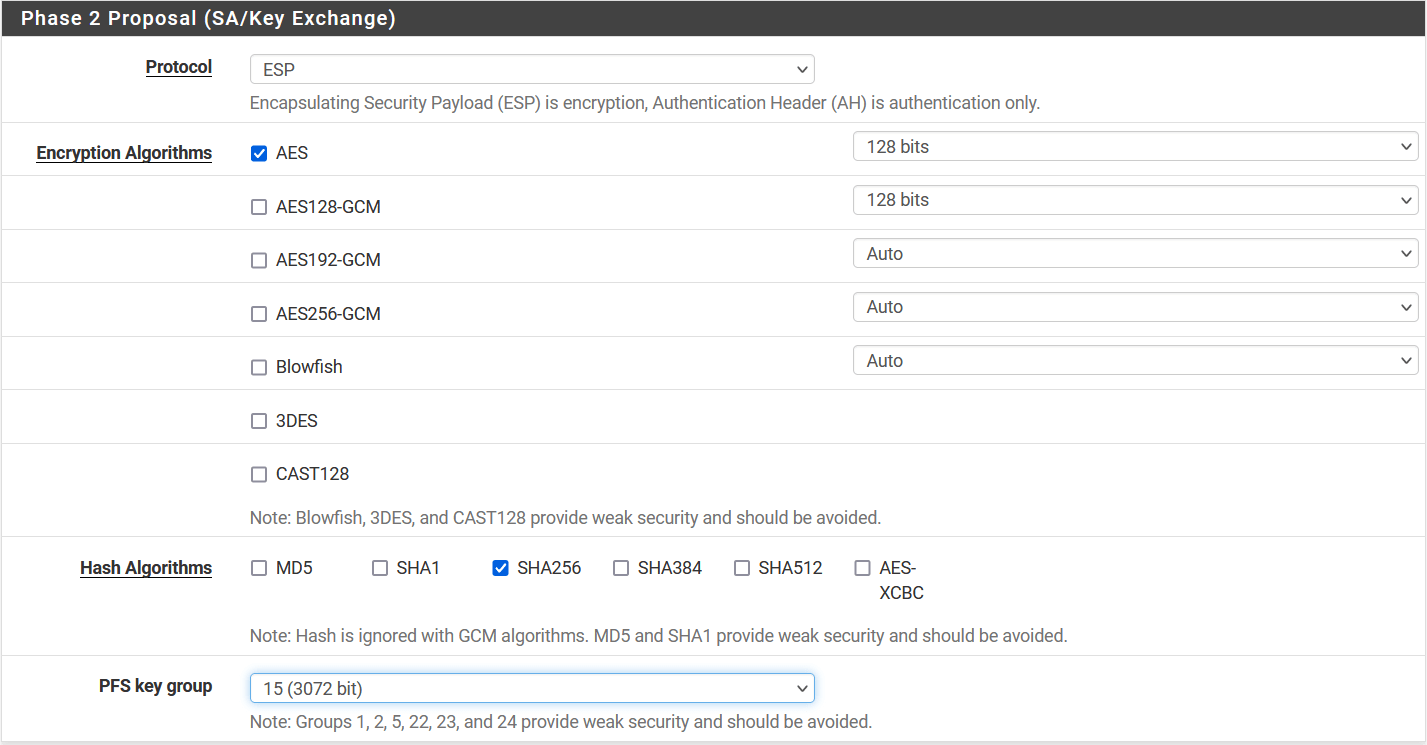

- Expiration and Replacement
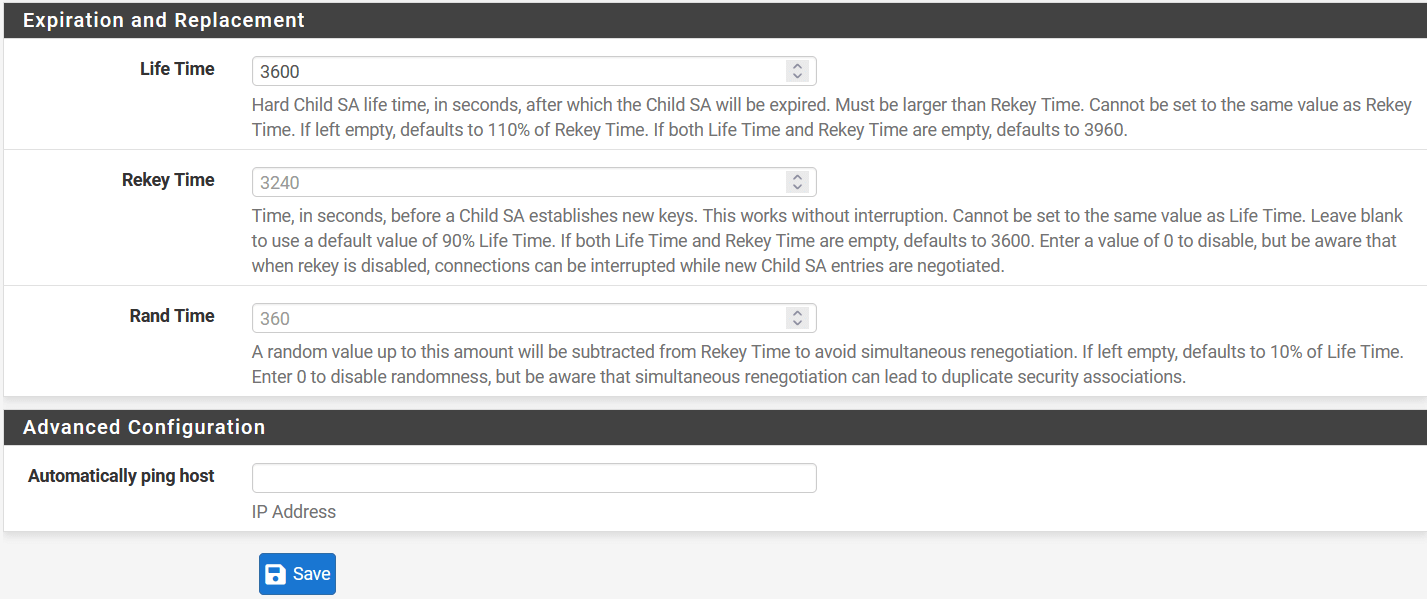
- Lifetime: 3600 `
-
Click on Save.

-
Click on Apply Changes to save the configuration.

-
Go to Firewall > Rules and select LAN

-
Click on Add button to add a new rule.
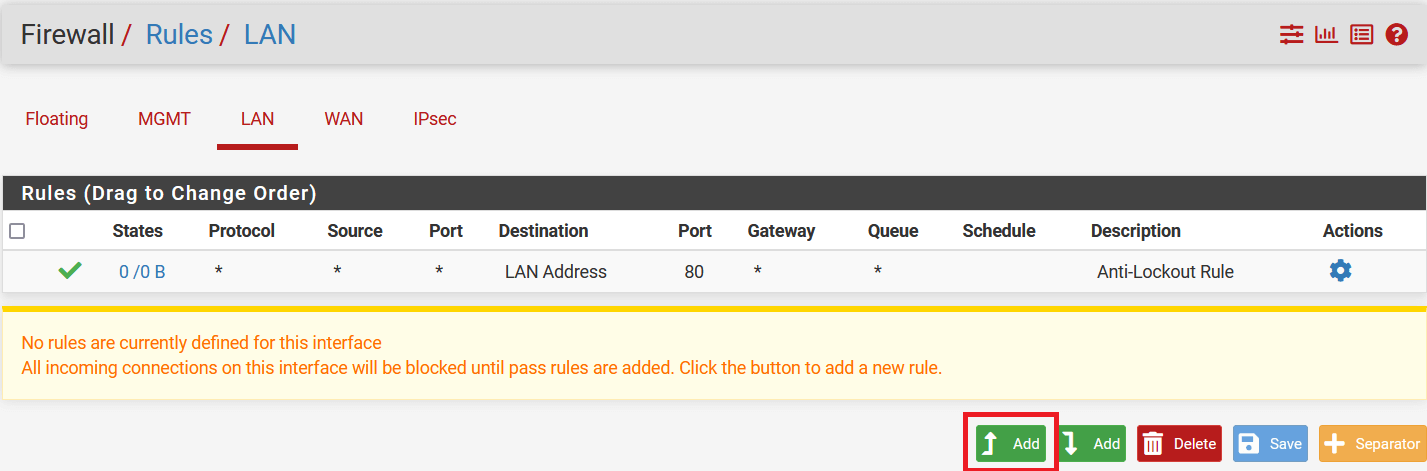

-
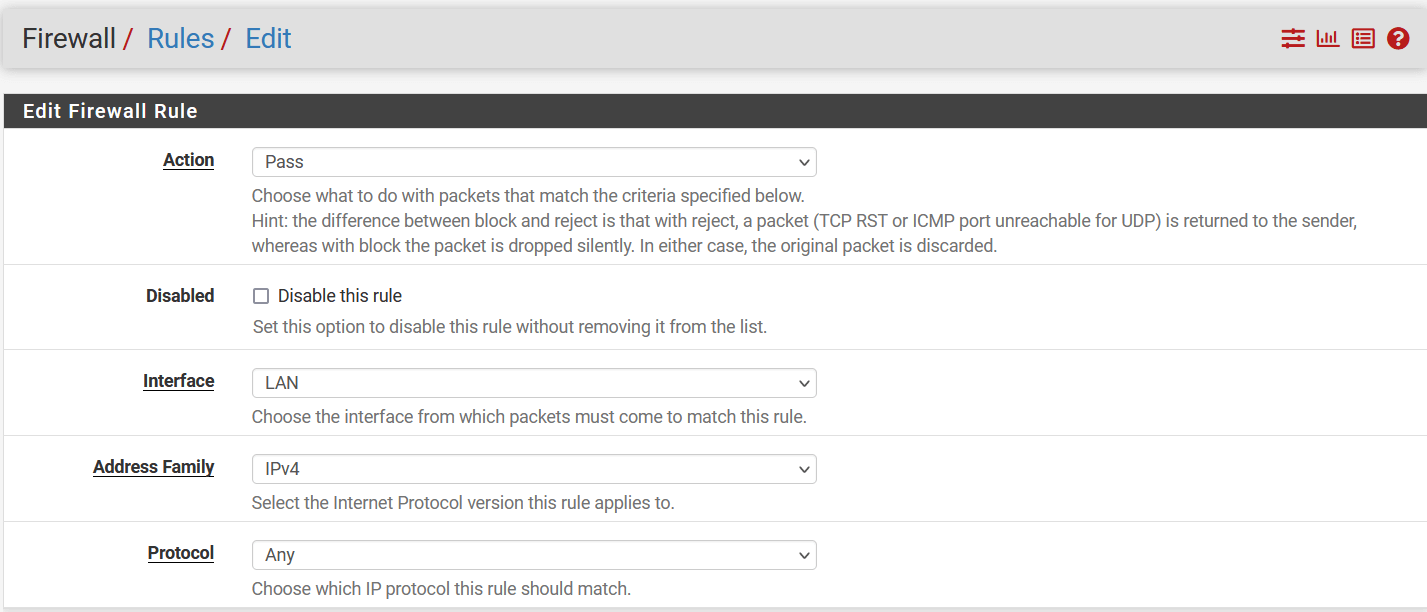
In the next window, configure policy as below:
- Edit Firewall Rules
- Action: Pass
- Interface: LAN
- Address Family: IPv4
- Protocol: Any

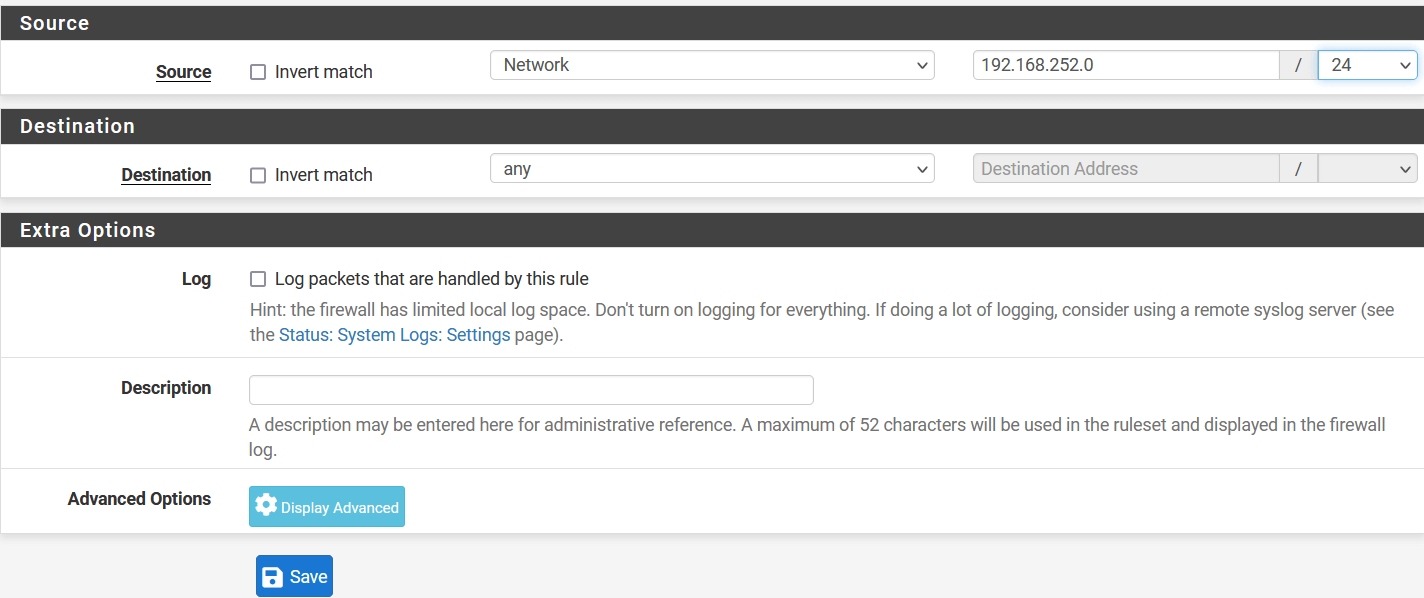
- Source
- Source: Select Network and enter local lan address i.e., 192.168.252.0/24
- Destination
- Destination: Any
- Click on Save

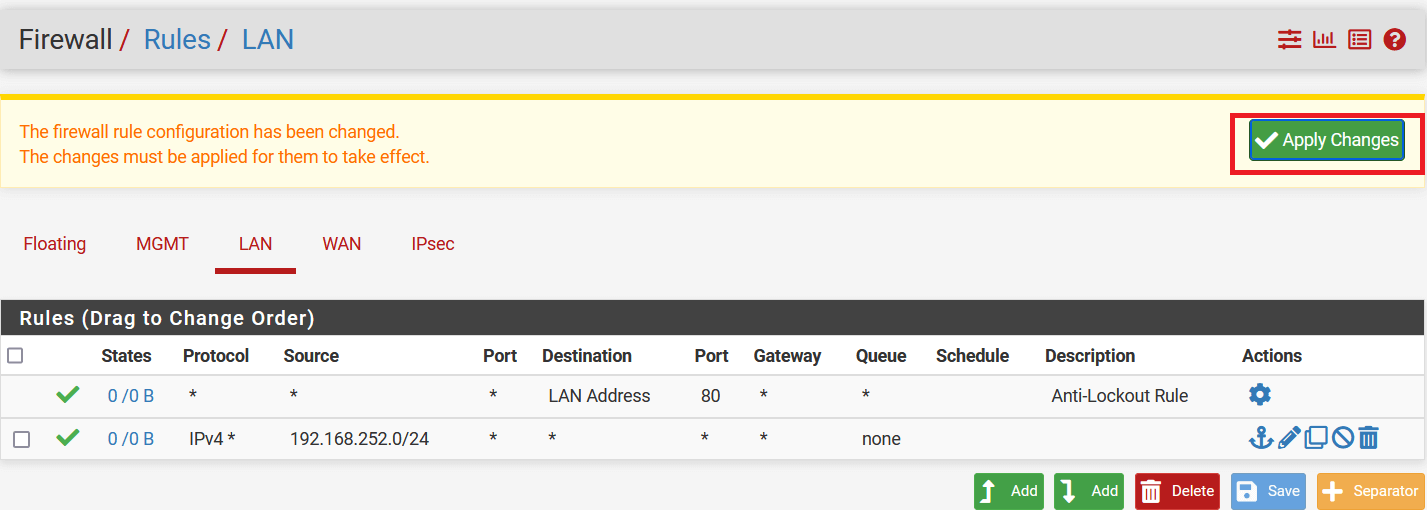
- Click on Apply Changes to save the configuration.

Task 4. Disable NAT for traffic over VPN
-
Go to Firewall > NAT.
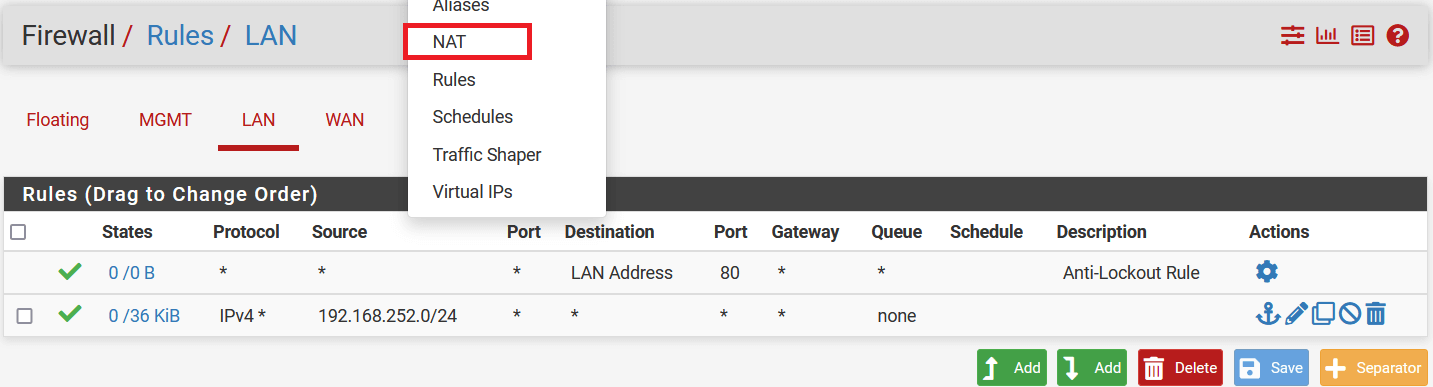

-
Select Outbound, and in the Mapping section click on the Add button.
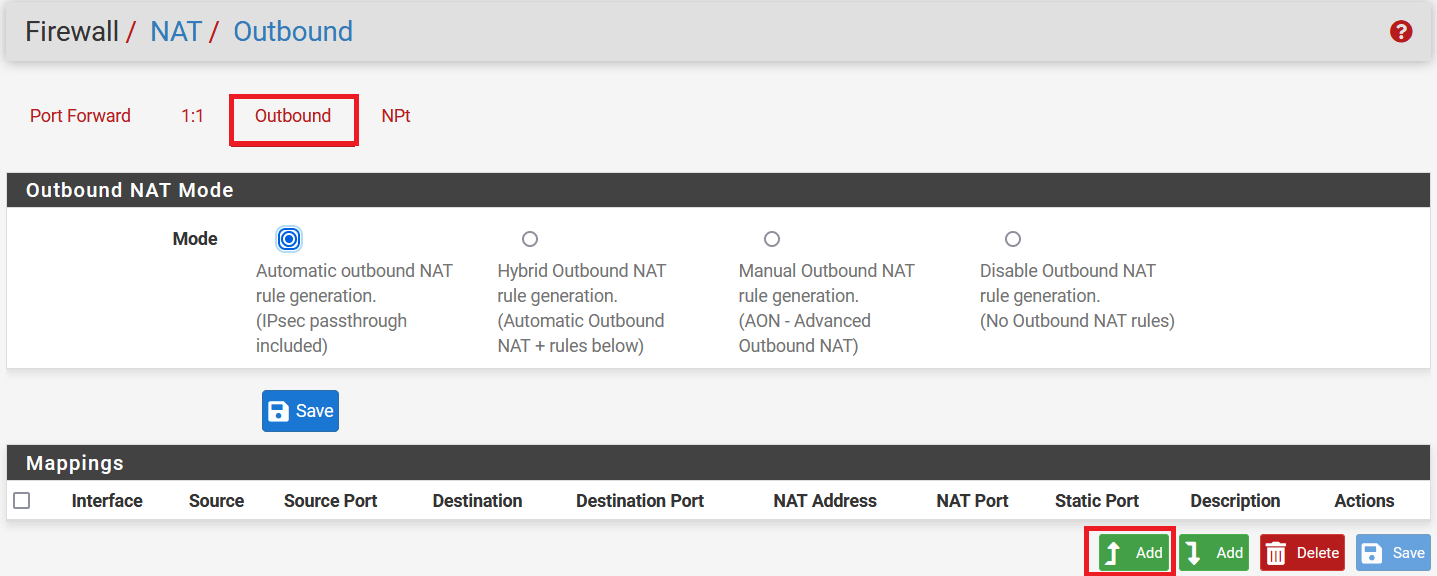

-
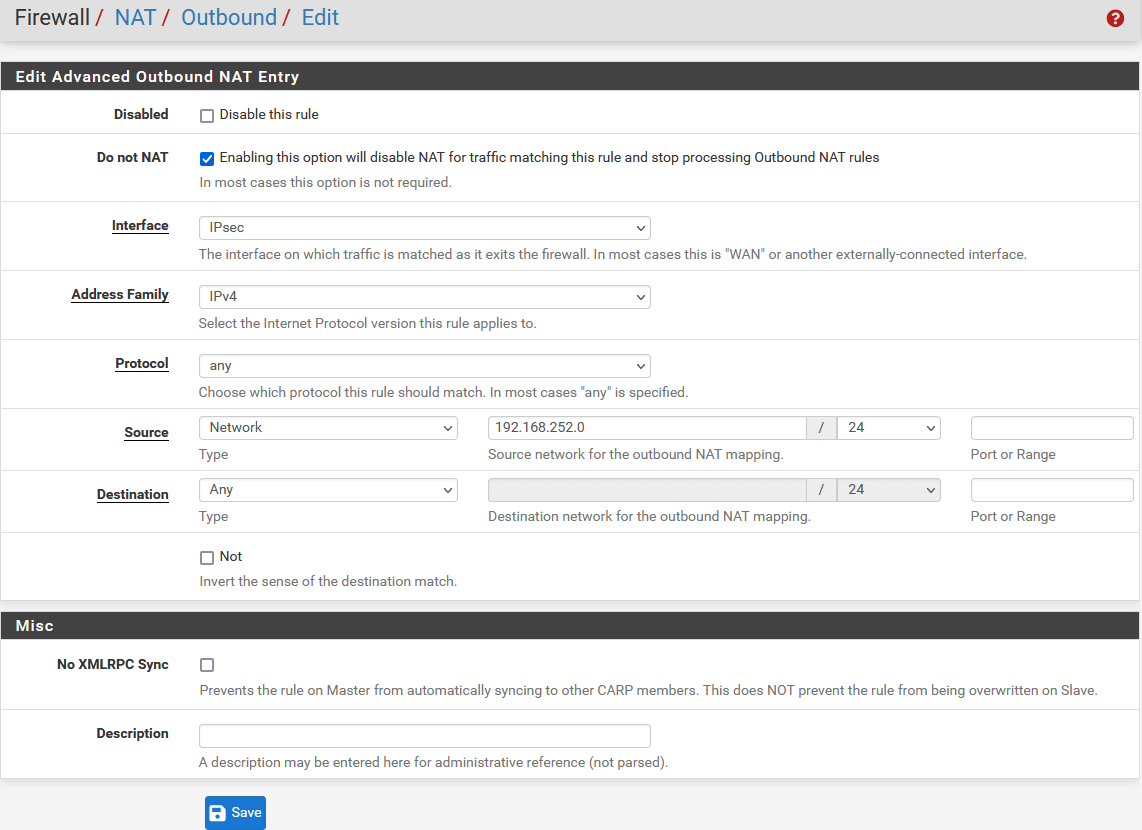
In the next window, configure the rule as below:
- Edit Advanced Outbound NAT Entry
- Do not NAT: Enable
- Interface: IPsec
- Address Family: IPv4
- Protocol: Any
- Source: Select Network and enter local lan address i.e., 192.168.252.0/24
- Destination: Any
-
Click on Save

-
Click on Apply Changes to save the NAT rule.
-
In the same window, select mode Hybrid Outbound NAT rule generation. (Automatic Outbound NAT + rules below) in Outbound NAT Mode.
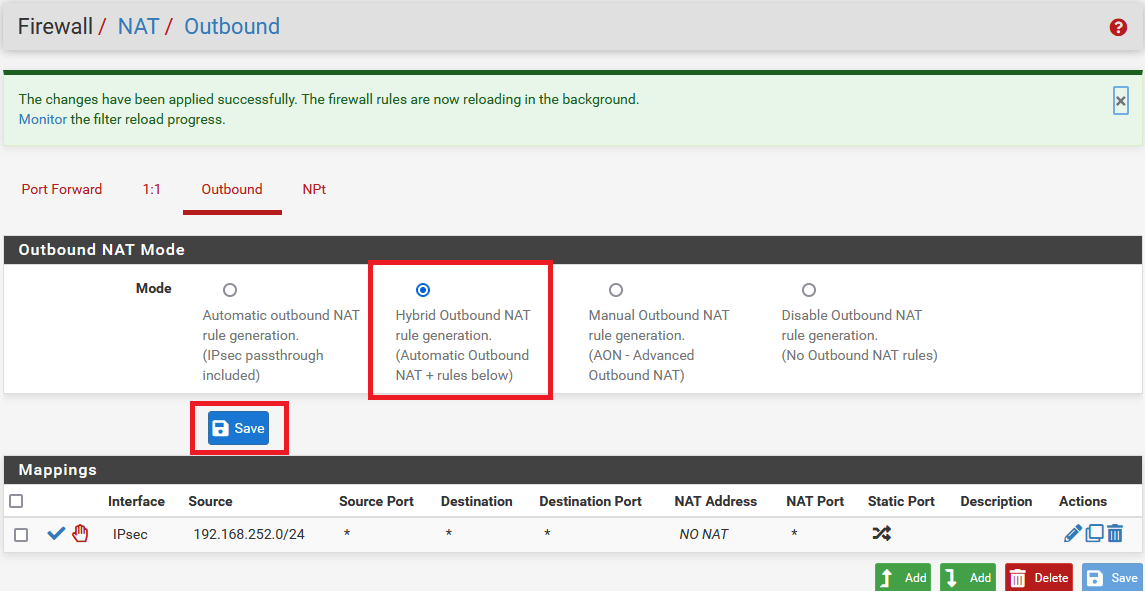

-
Click on Apply Changes to save settings.
Task 5. Verify Tunnel Status
-
Go to Status > IPsec.

-
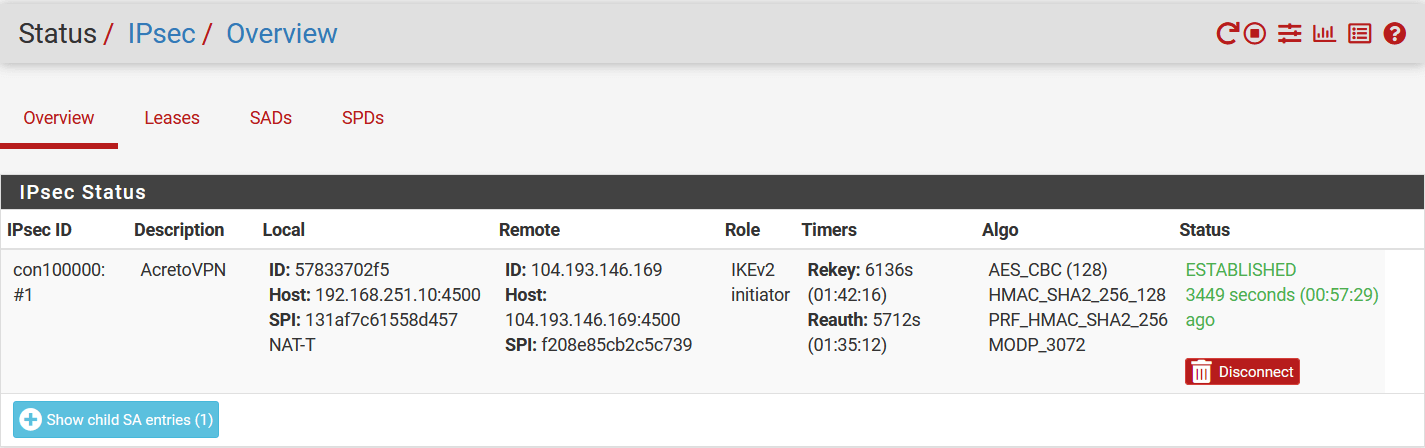
The following window will show the status of the VPN as below. Click on Connect VPN if the tunnel is down.

Task 6. Check the connectivity using the LAN interface
-
Go to Diagnostics » Ping.

-
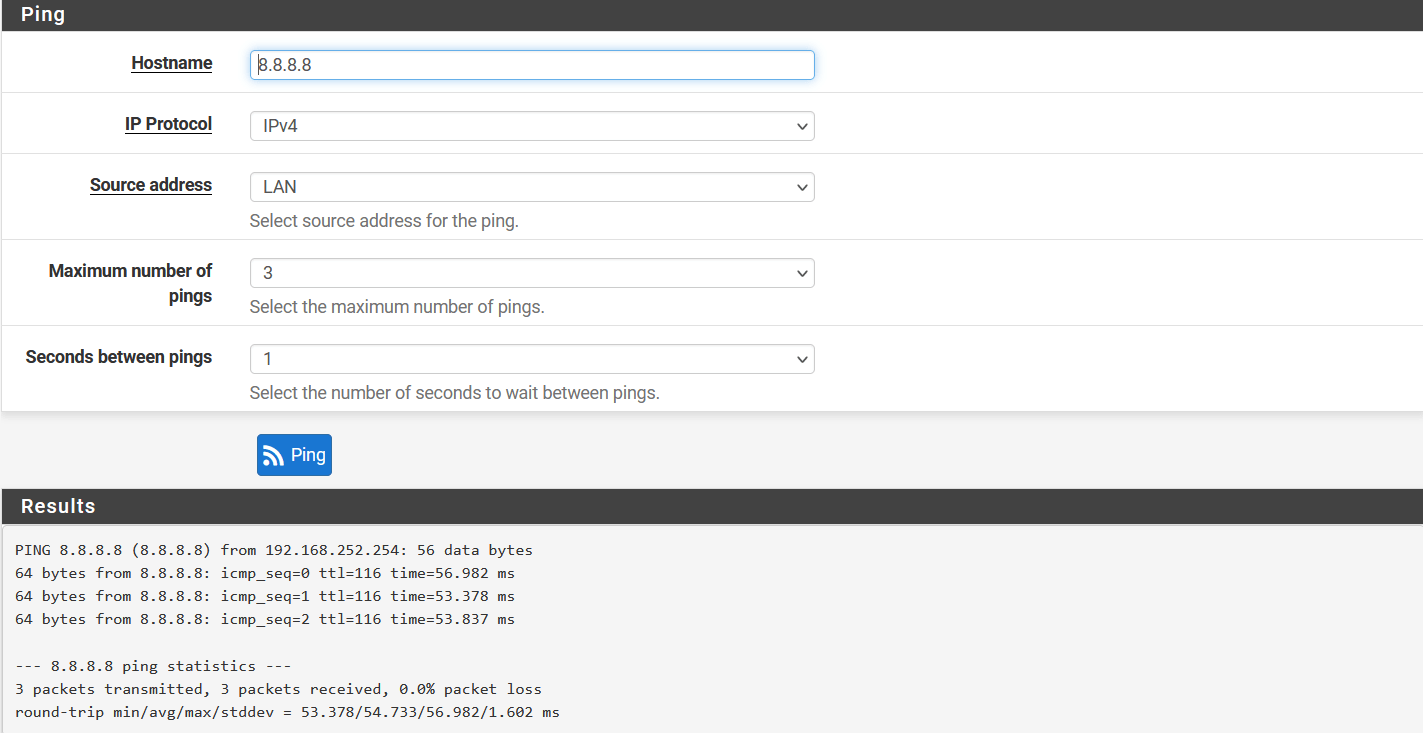
In the next windows, check ping as below:
- Hostname: 8.8.8.8
- Source address: LAN
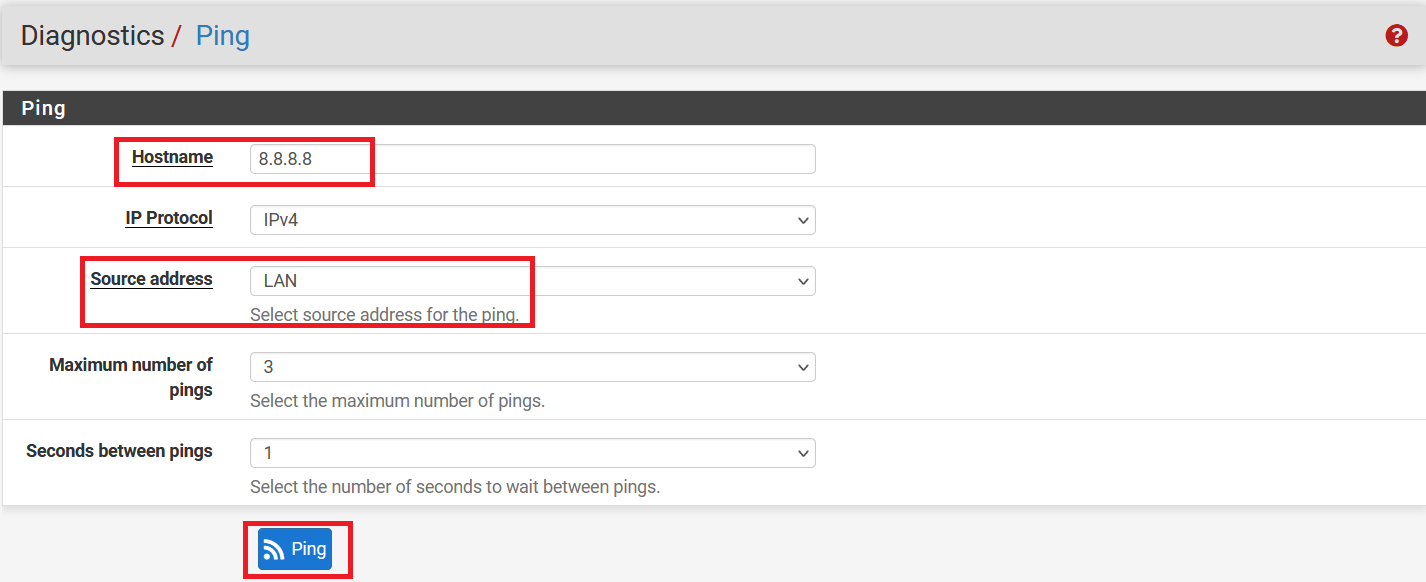


-
Ping should be successful, and logs on the Wedge dashboard should show the same record.
-
Go to VPN > IPsec and click on Advanced Setting.

-
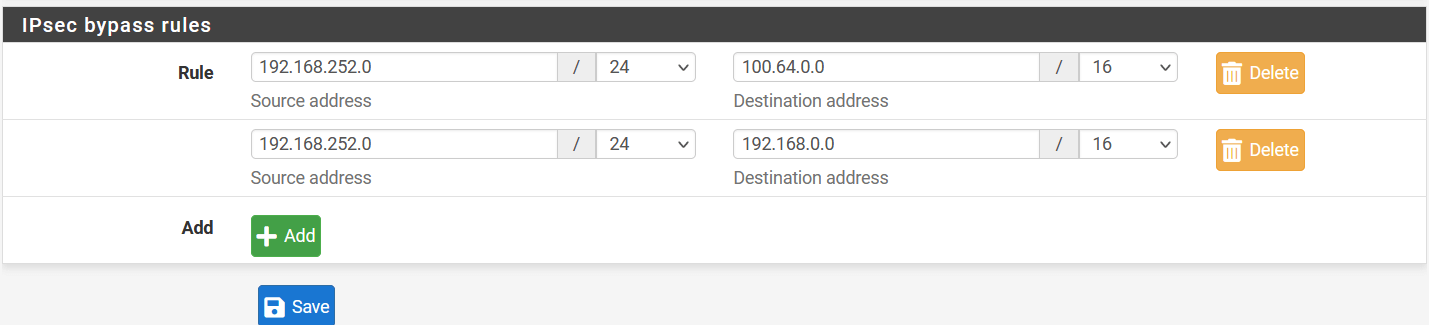
In IPsec bypass rules, enter the source and destinations of your local traffic, which doesn’t need to go through Acreto VPN.

Summary
Once the VPN connection is successfully established, all the internet traffic will be routed through the Acreto.
Sonicwall 6.5 IPsec Configuration
Overview
In this article, you will learn how to connect your Sonicwall to the Acreto Ecosystem. To make it possible and secure, we will use the IPSec VPN connection.

Prerequisites
- Sonicwall 6.5 installation
- Ecosystem set up with proper security policies
Create Gateway for IPsec
Create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
- Type: IPsec
- Category: Data Center
- Model: AWS site-to-site VPN
- Connections from: Public IP
- Local network: local_network
- Save and Commit the changes
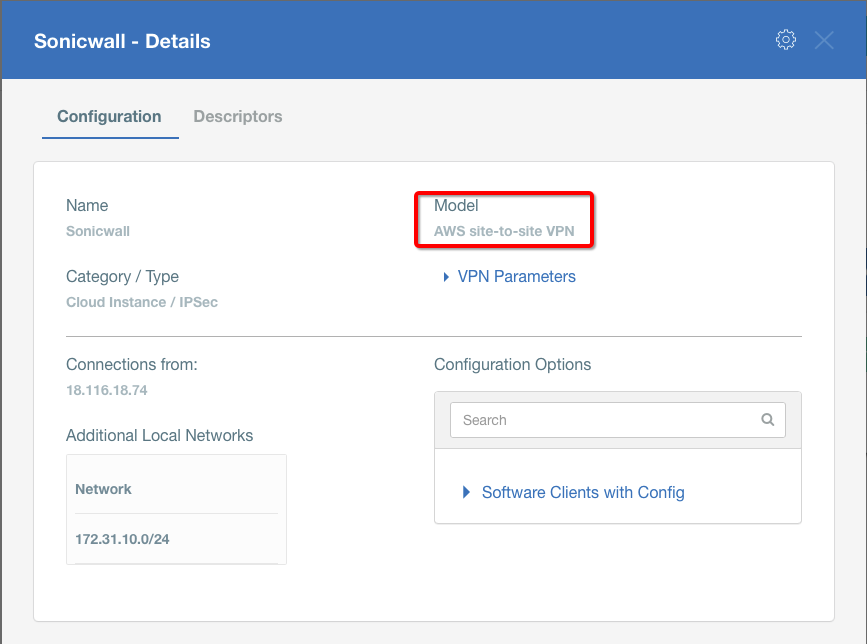

Info
To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (use /32 prefix for public interface). This allows testing connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
How-To
Task 1: Read IPsec Gateway Values Required for IPsec Configuration
To proceed with the Sonicwall configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All the details may be found within the Gateway details panel - please check the video below for further instructions.
To configure the IPsec VPN using tunnel interface, proceed with the following steps:
-
Goto MANAGE » VPN » Base Settings.
-
Under the VPN Policies click the ADD button
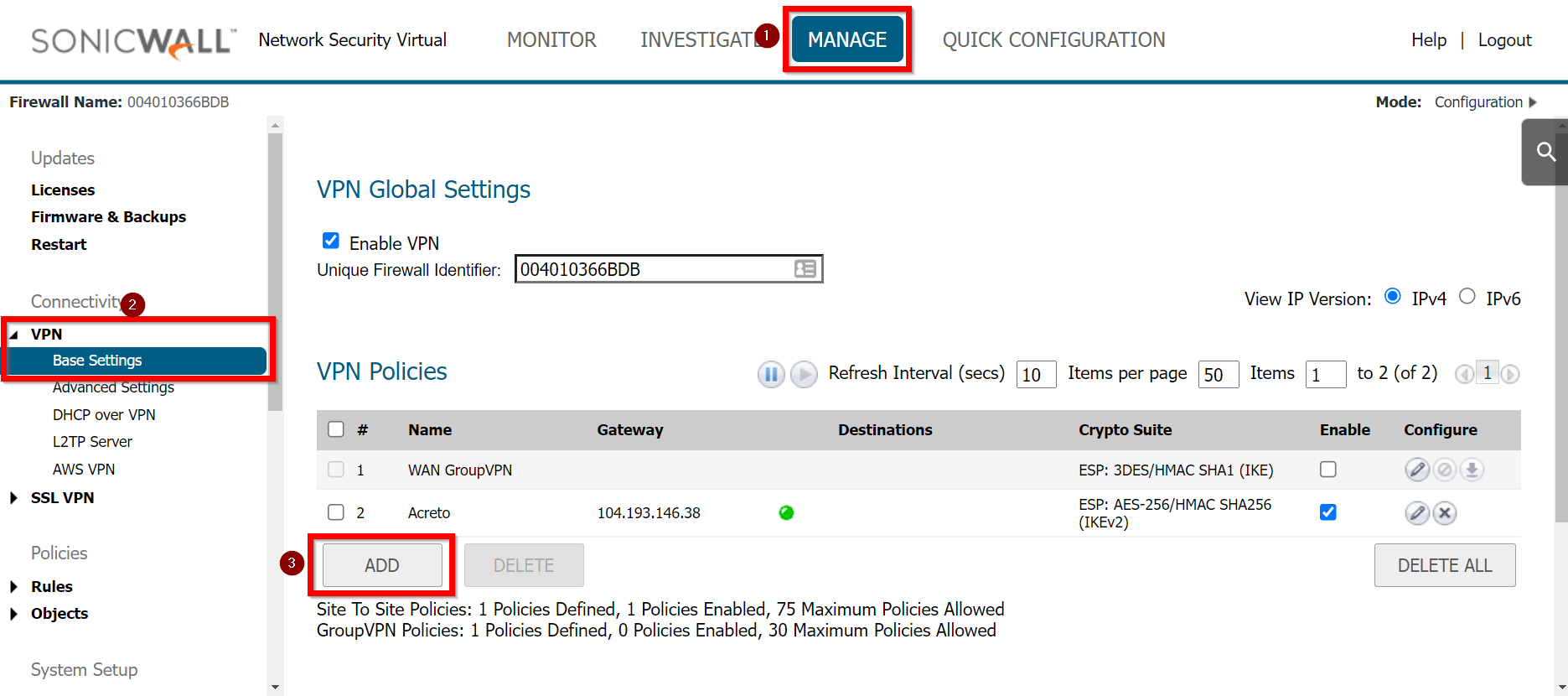

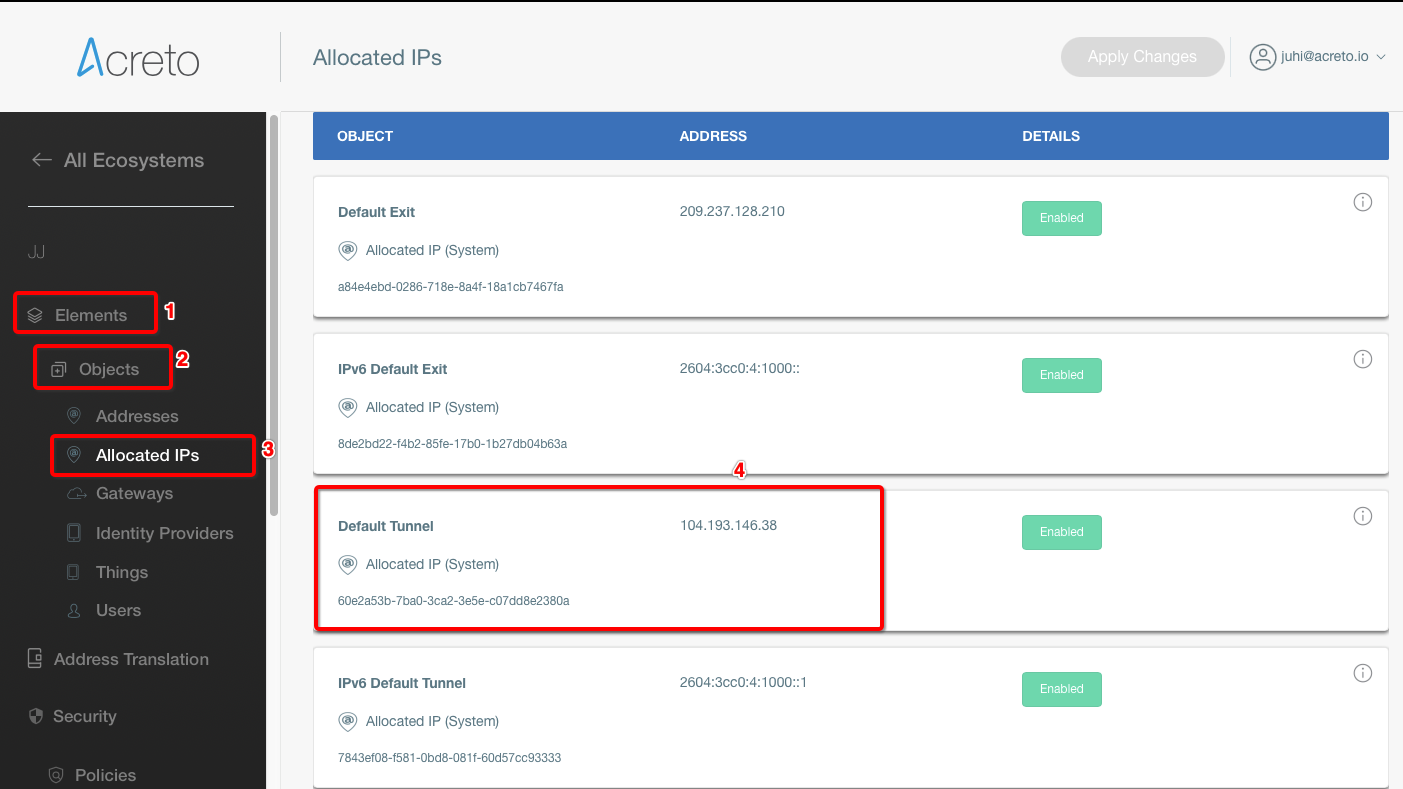
-
Under the General tab, enter the following values:
- Security Policy
- Policy Type: Tunnel Interface
- Authentication Method: IKE using Preshared Secret
- Name: Acreto
- IPsec Primary Gateway Name or Address: <Wedge_Tunnel_IP>
- IKE Authentication
- Shared Secret:
- Confirm Shared Secret:
- Local IKE ID: IPv4 Address: wedge_tunnel_IP

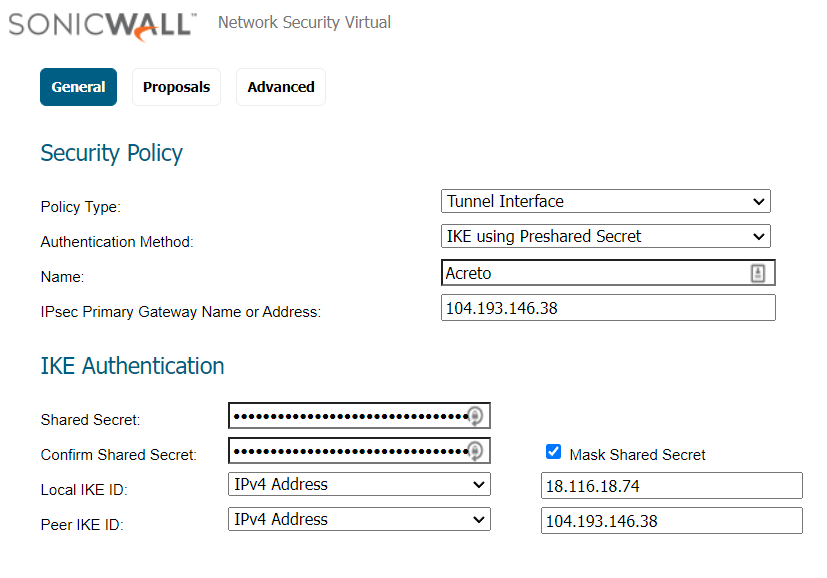
- Peer IKE ID: IPv4 Address: Local Public IP

-
Goto Proposals
- IKE (Phase 1) Proposal
- Exchange: IKEv2 Mode
- DH Group: Group 2
- Encryption: AES-256
- Authentication: SHA256
- Life Time (seconds): 10800
- IPsec (Phase 2) Proposal
- Protocol: ESP
- Encryption: AES-256
- Authentication: SHA256
- Enable Perfect Forward Secrecy: Yes
- DH Group: Group 14
- Life Time (seconds): 3600
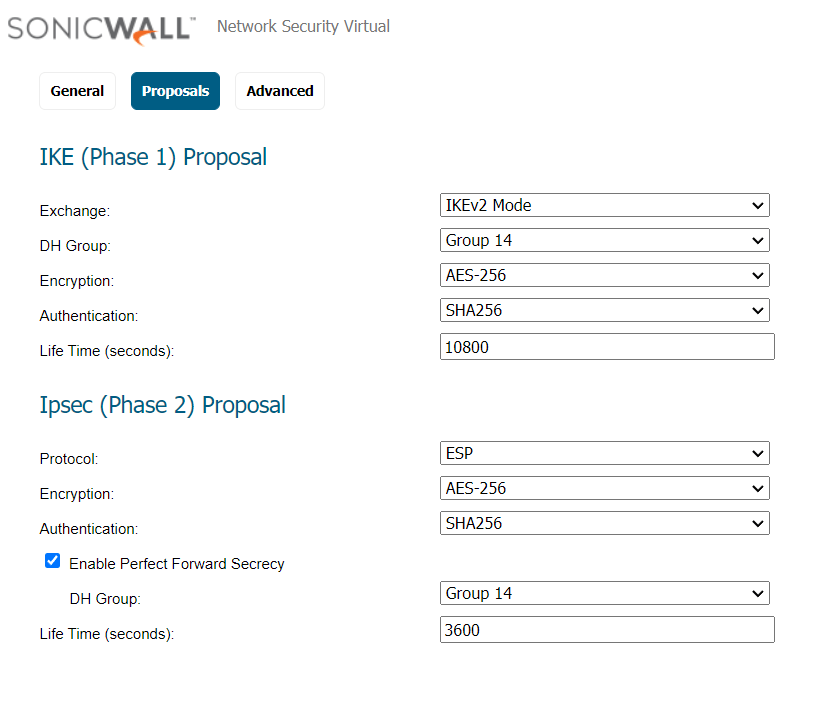

-
Advanced Settings
- Enable Keep Alive: Enable

-
Click the OK button.
Task 3: Create a new tunnel interface
Next, we will create the tunnel interface that will be used to route the traffic.
-
Goto MANAGE » Network » Interfaces
-
In the middle of the screen, for the field Add Interface, select VPN Tunnel Interface.
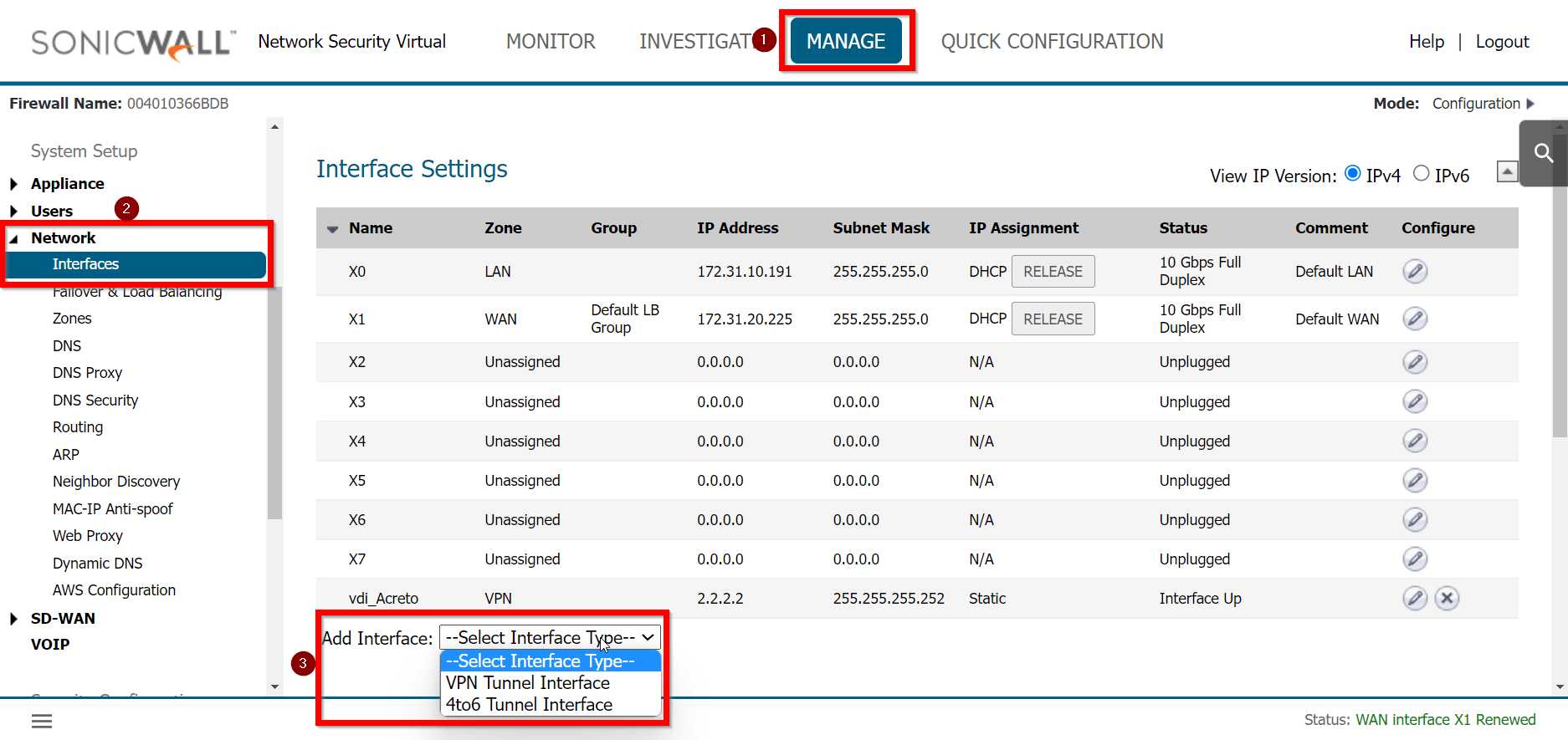

-
Create a new interface with the following values:
- VPN Policy: Acreto
- Name: vdi_Acreto
- IP Address: <any random IP as 2.2.2.2>
- Subnet Mask: 255.255.255.255
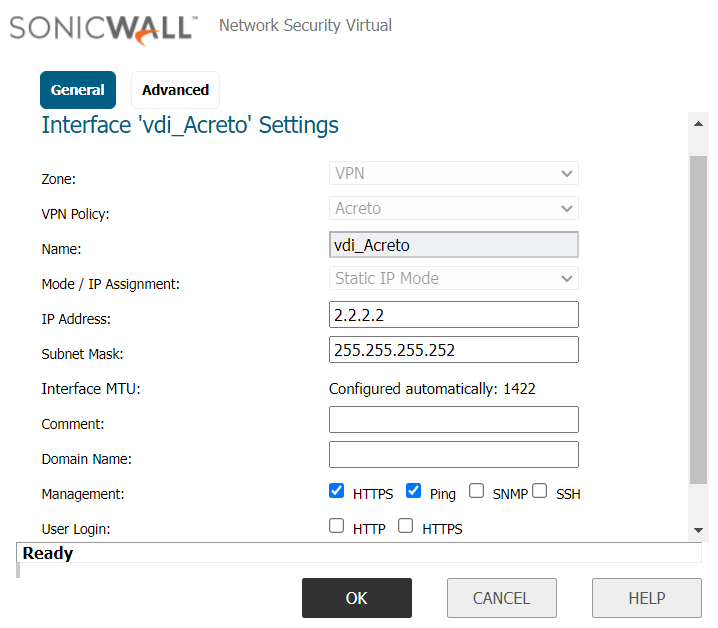

-
Click the OK button.
To allow the traffic from the LAN subnet to route through the tunnel interface, perform the following steps:
-
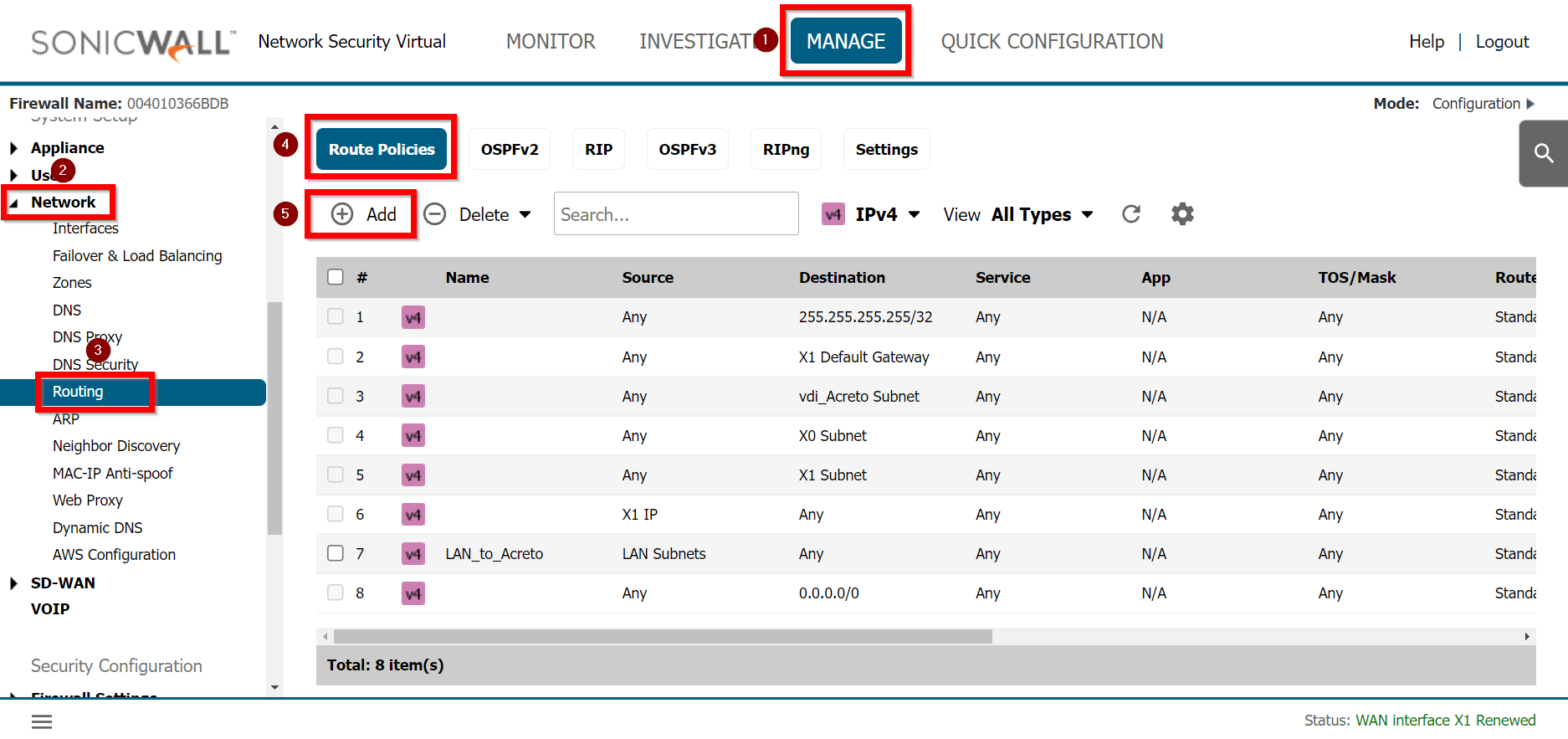
Goto MANAGE » Network » Routing
-
Under the tab Route Policies, click the Add button

-
Create a new rule with the following values under General:
- Route Policy Settings
- Name: Lan_to_Acreto
- Source: <lan_subnets>
- Destination: Any
- Service: Any
- Interface: <tunnel_interface>
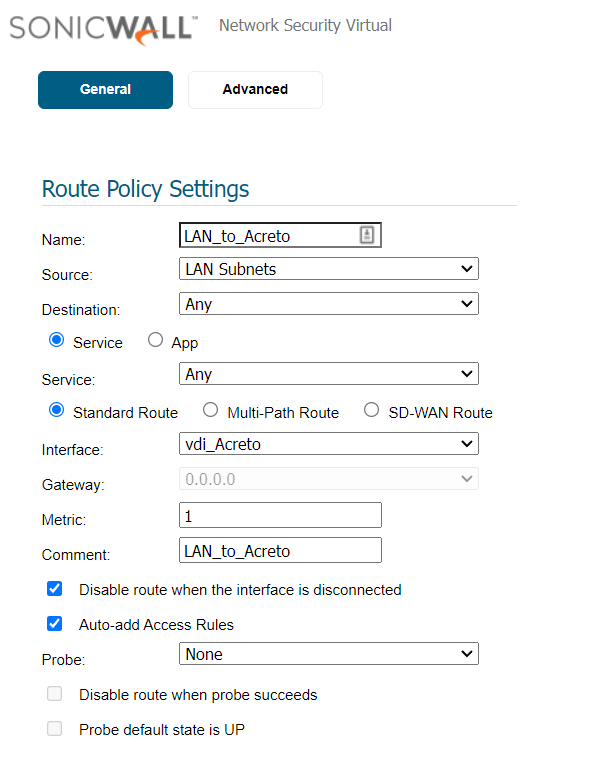

-
Click the OK button
Verify existing or create a new access rule to allow the desired traffic
-
Goto MANAGE » Rules » Access Rules
-
Click the Add button
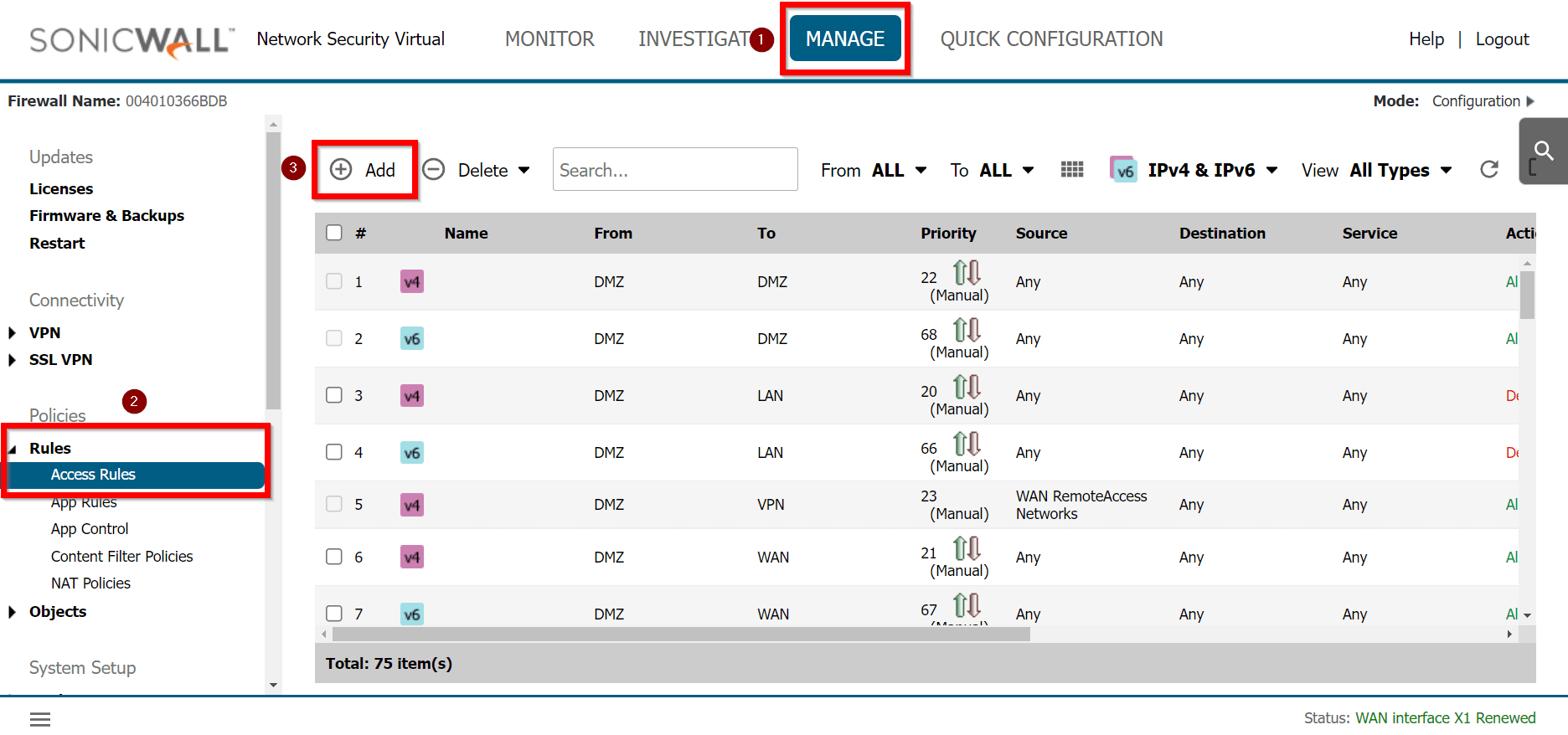

-
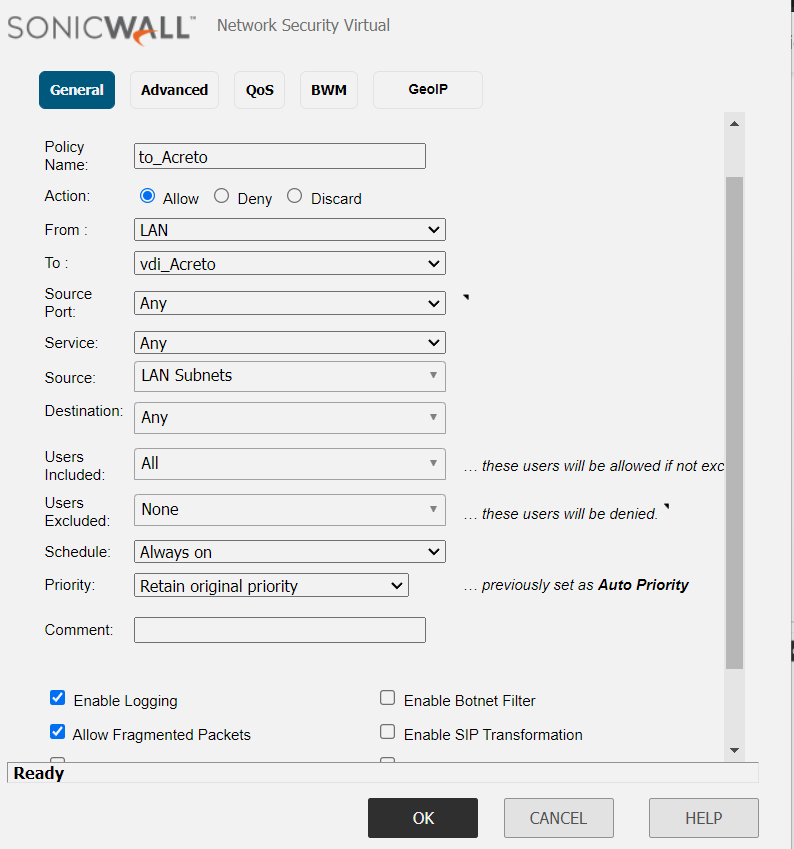
Under General, provide the following values:
- Name: To_Acreto
- Action: Allow
- From: <Lan_interface>
- To: <tunnel_interface>
- Source Port: Any
- Service: Any
- Source: <lan_subnet>
- Destination: Any

-
Click the OK button
Task 6: Verify the connection
Once the tunnel connection is successfully established, its status will change to UP.
-
To verify the status on Sonicwall, navigate to goto MANAGE » VPN » Base Settings
The status of the VPN policy should be Green.
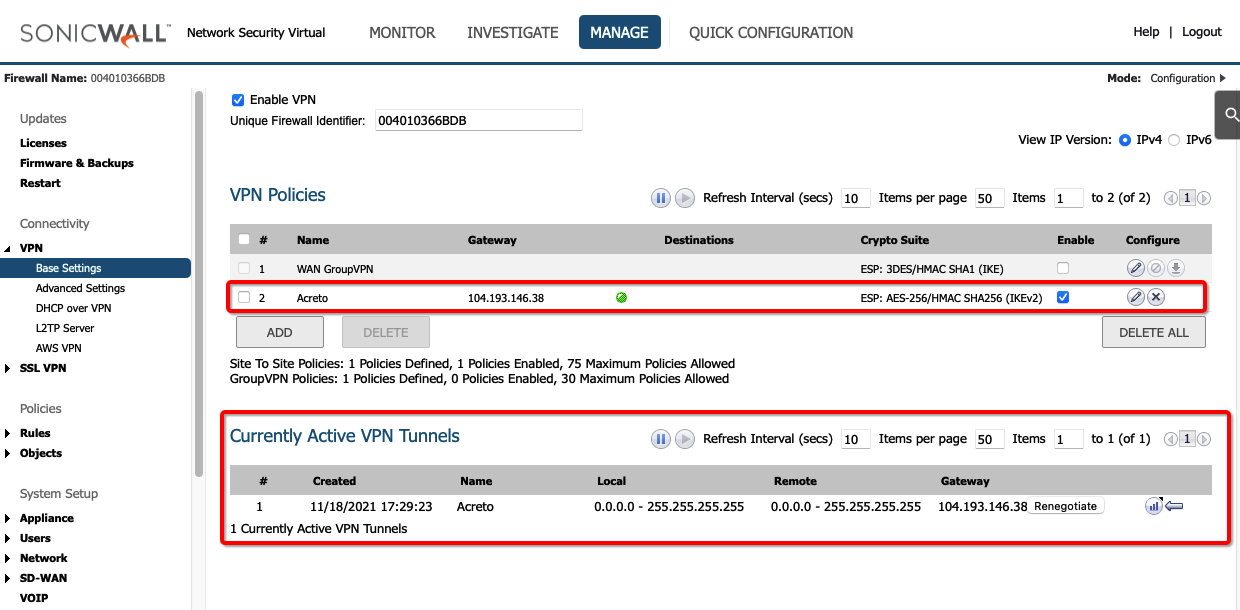

- Currently Active VPN Tunnels
The active VPN tunnel will be shown in the list.
-
Execute tracert 1.1.1.1 (or traceroute 1.1.1.1) on internal server check the route to external host 1.1.1.1. It should show Acreto’s IP in the path.
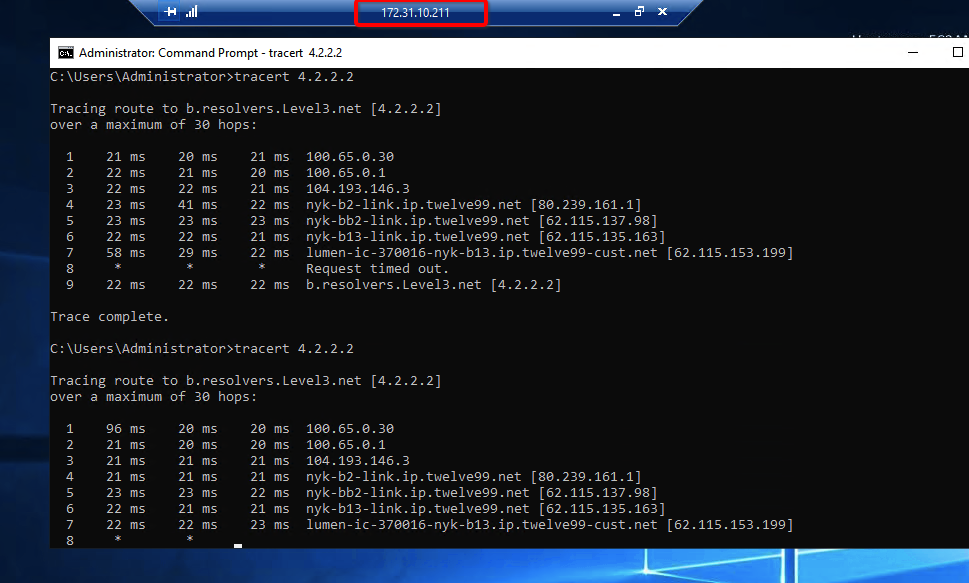

Summary
Once the VPN connection is successfully established, all the internal traffic to the internet will be routed through Acreto.
Sonicwall 7.0 IPsec Configuration
Overview
In this article, you will learn how to connect your Sonicwall to the Acreto Ecosystem. To make it possible and secure, we will use the IPSec VPN connection.
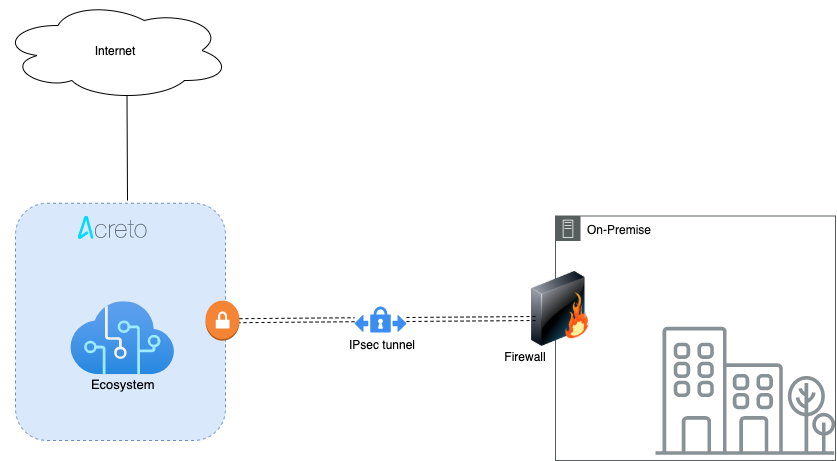

Prerequisites
- Sonicwall 7.0 installation
- Ecosystem set up with proper security policies
Create Gateway for IPsec
Create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
- Type: IPsec
- Category: Data Center
- Model: AWS site-to-site VPN
- Connections from: Public IP
- Local network: local_network
- Save and Commit the changes
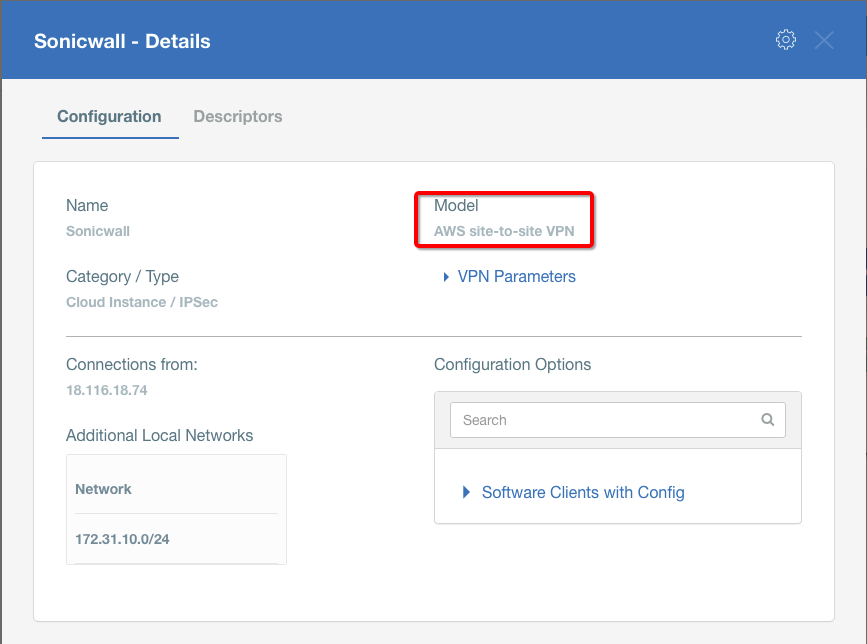

Info
To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (use /32 prefix for public interface). This allows testing connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
How-To
Task 1: Read IPsec Gateway Values Required for IPsec Configuration
To proceed with the Sonicwall configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All the details may be found within the Gateway details panel - please check the video below for further instructions.
To configure the IPsec VPN using tunnel interface, proceed with the following steps:
-
Goto NETWORK » IPsec VPN » Rules and Settings.
-
Click the ADD button.
-
Under the General tab, enter the following values:
- Security Policy
- Policy Type: Tunnel Interface
- Authentication Method: IKE using Preshared Secret
- Name: Acreto
- IPsec Primary Gateway Name or Address: <Wedge_Tunnel_IP>
- IKE Authentication
- Shared Secret: PSK
- Confirm Shared Secret: PSK
- Local IKE ID: IPv4 Address: Wedge_tunnel_IP
- Peer IKE ID: IPv4 Address: Local Public IP
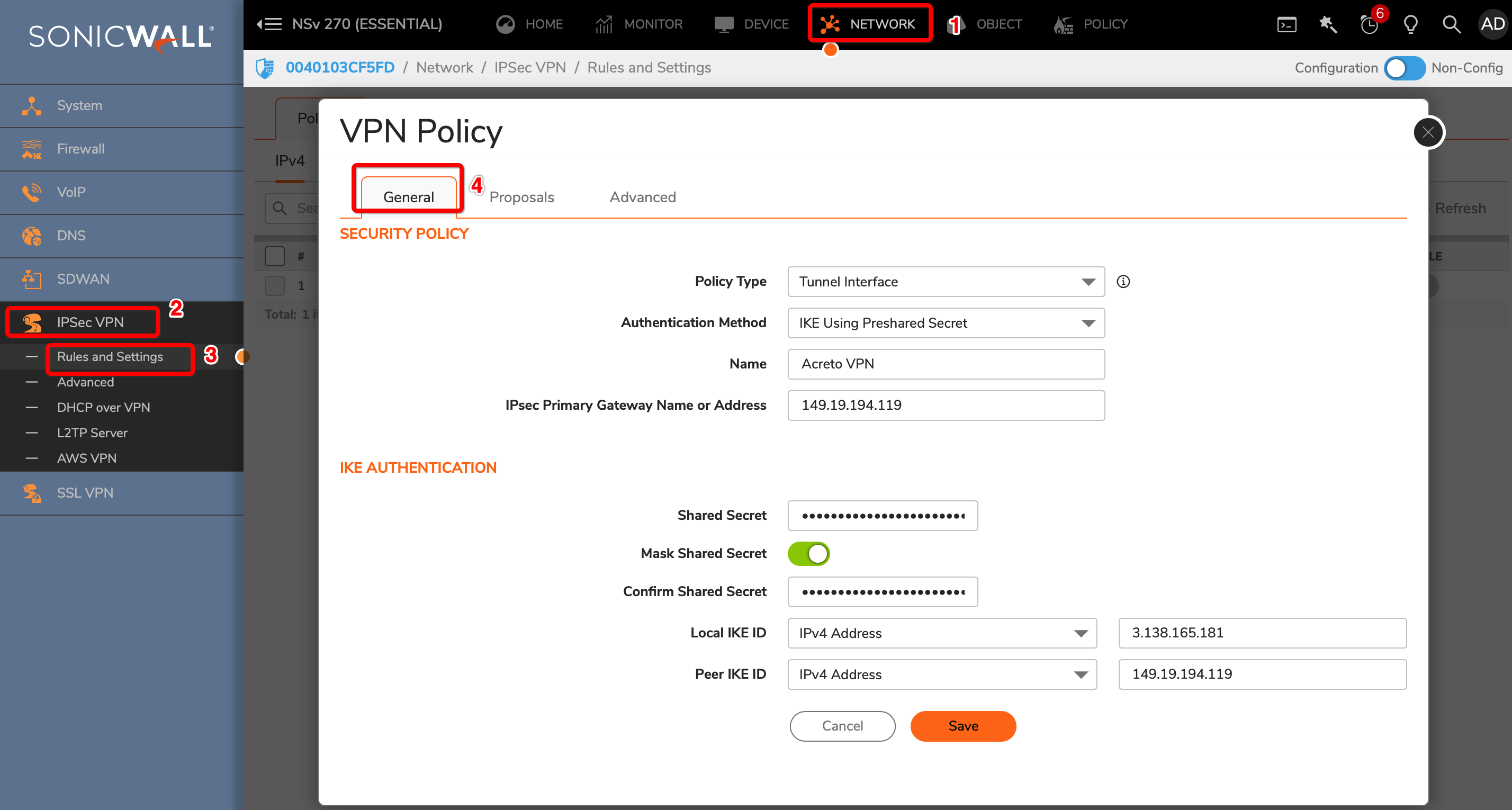

-
Goto Proposals
- IKE (Phase 1) Proposal
- Exchange: IKEv2 Mode
- DH Group: Group 2
- Encryption: AES-256
- Authentication: SHA256
- Life Time (seconds): 10800
- IPsec (Phase 2) Proposal
- Protocol: ESP
- Encryption: AES-256
- Authentication: SHA256
- Enable Perfect Forward Secrecy: Yes
- DH Group: Group 14
- Life Time (seconds): 3600
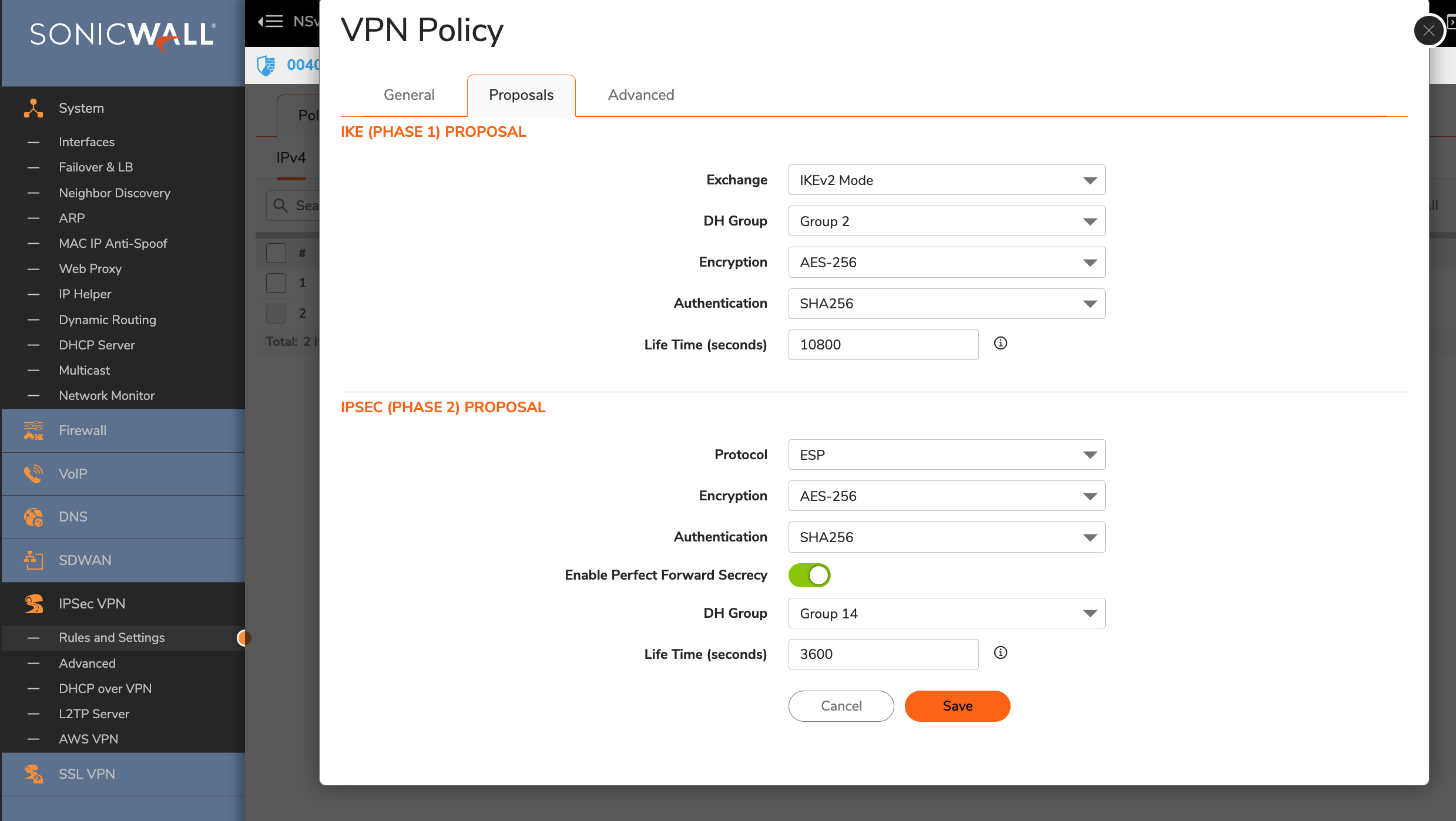

-
Advanced Settings
- Enable Keep Alive: Enable
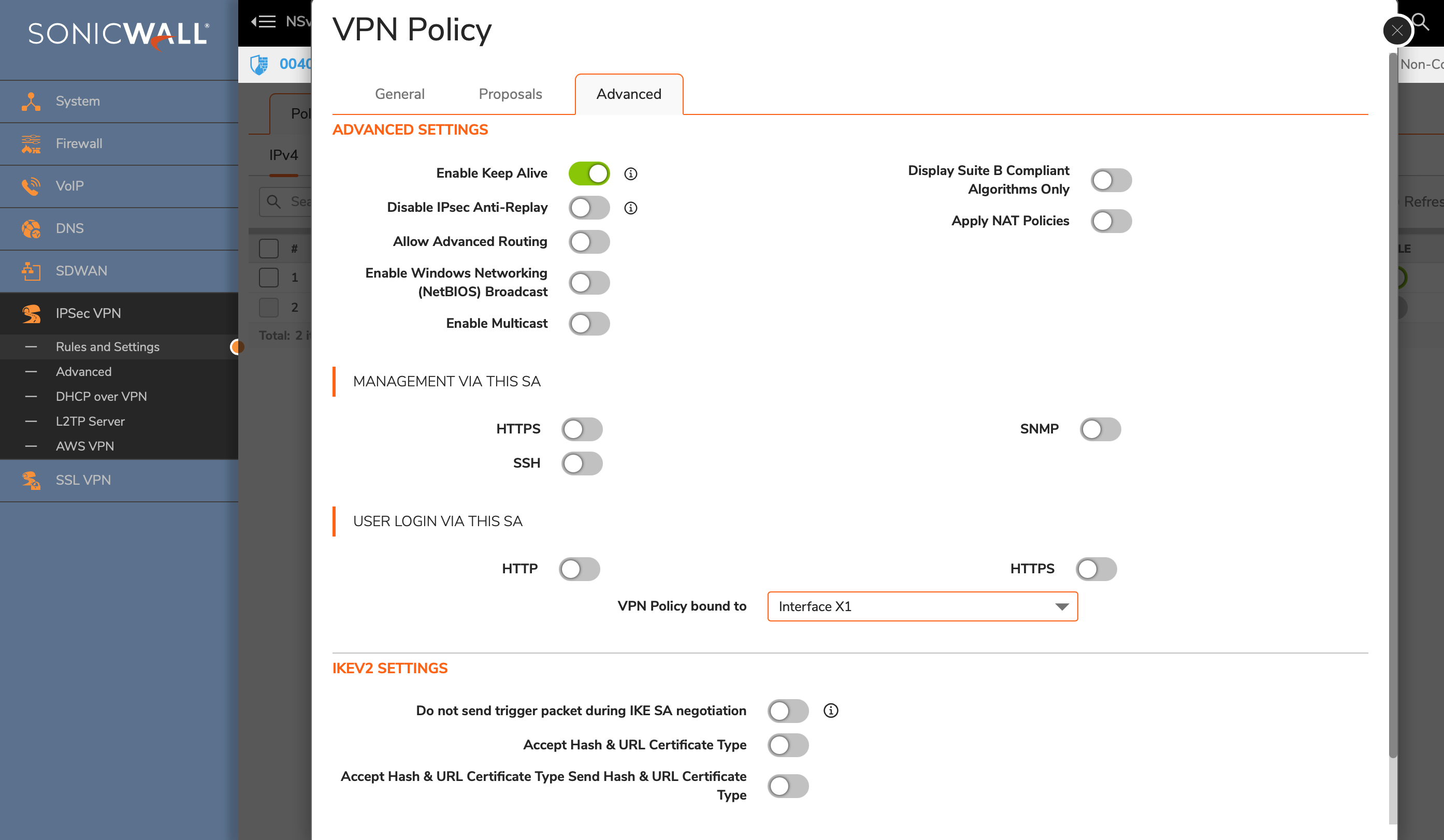

-
Click the OK button.
Task 3: Create a new tunnel interface
Next, we will create the tunnel interface that will be used to route the traffic.
-
Goto NETWORK » System » Interfaces.
-
Click the Add Interface button and select VPN Tunnel Interface
-
Create a new interface with the following values:
- VPN Policy: Acreto
- Name: vti_Acreto
- IP Address: <any random IP as 2.2.2.2>
- Subnet Mask: 255.255.255.254
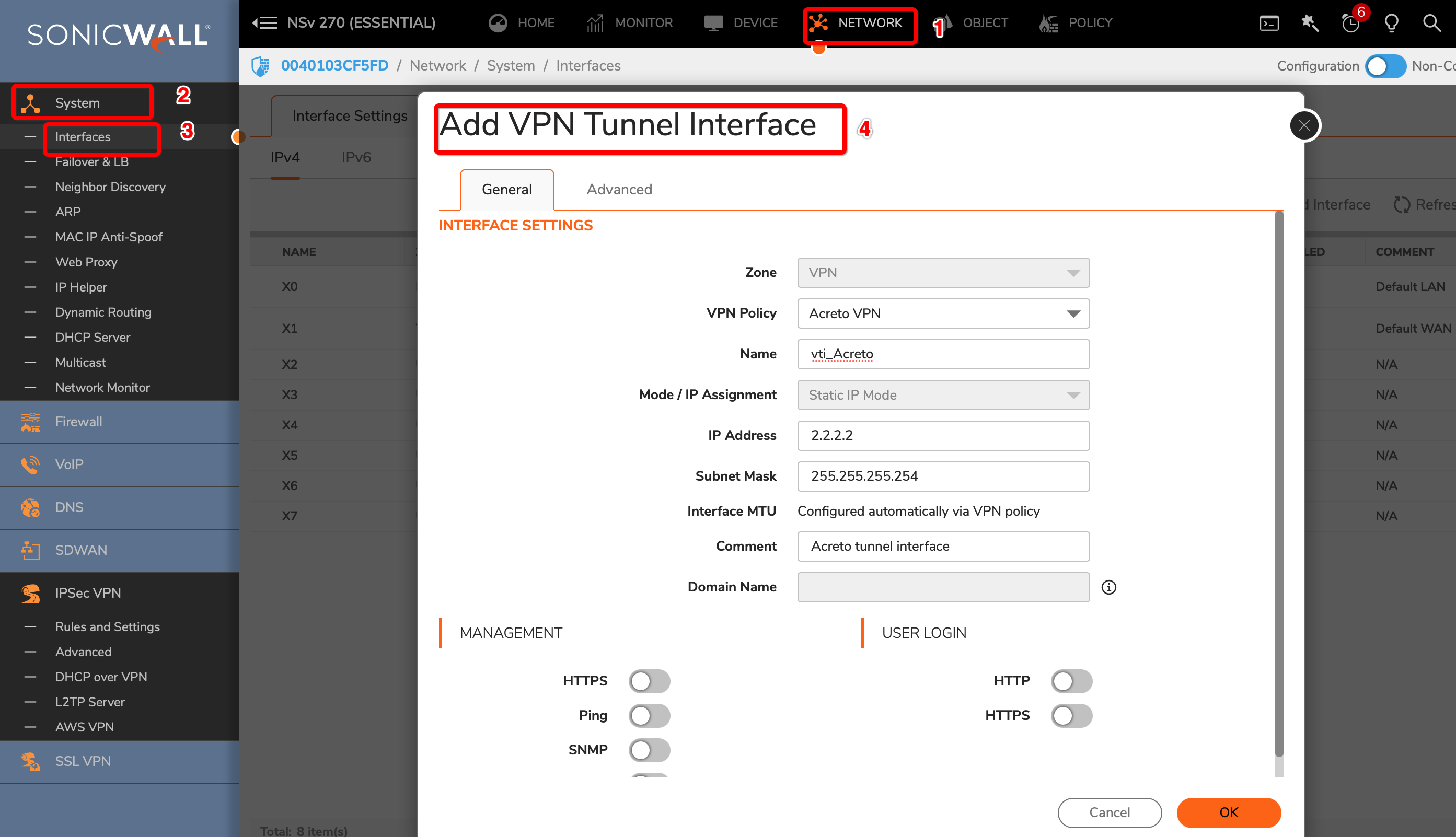

-
Click the OK button.
To allow the traffic from the LAN subnet to route through the tunnel interface, perform the following steps:
-
Goto POLICY » Rules and Policies » Route Policy
-
Create a new rule with the following values under General tab:
- Name: Lan_to_Acreto
- Source: <lan_subnets>
- Destination: Any
- Select Service radio button
- Service: Any
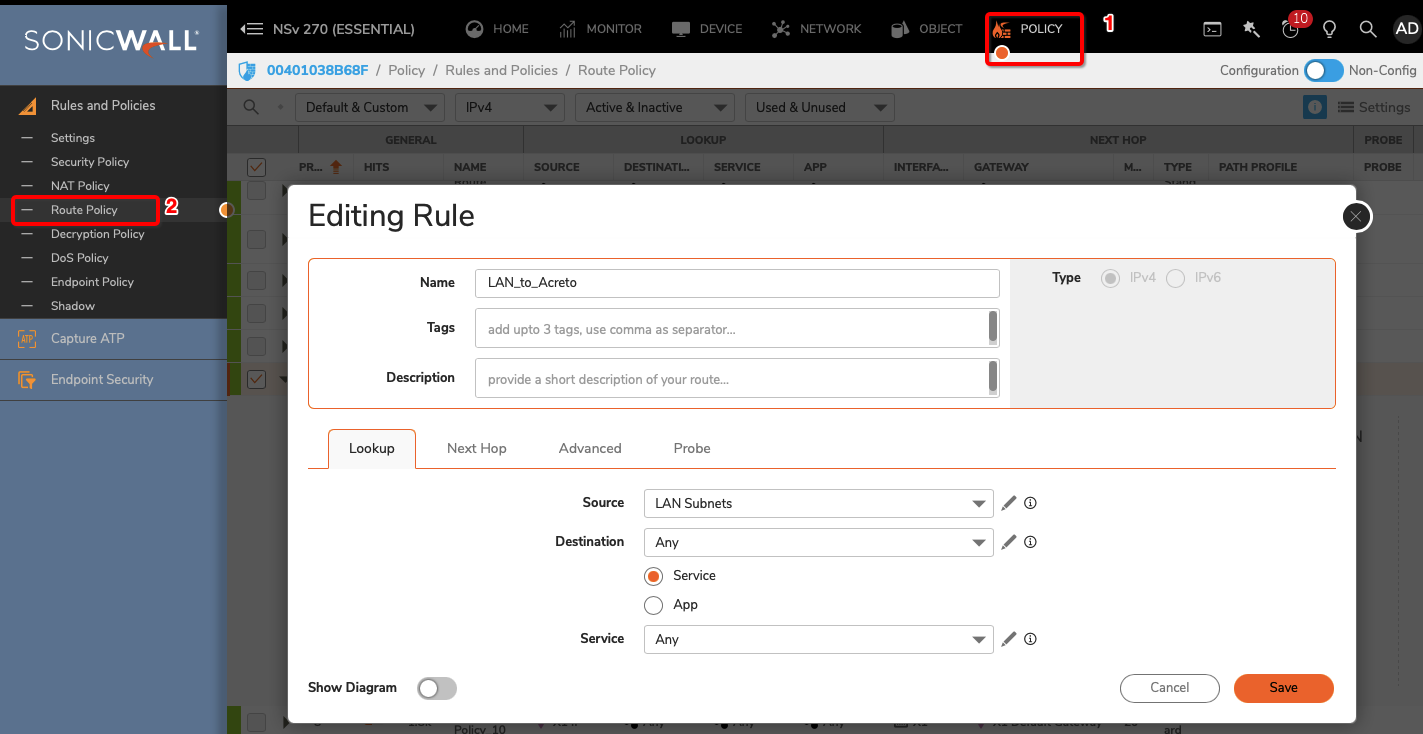

-
Click Next Hop tab and give the following values :
- Select Standard Route radio button
- Interface: <tunnel_interface>
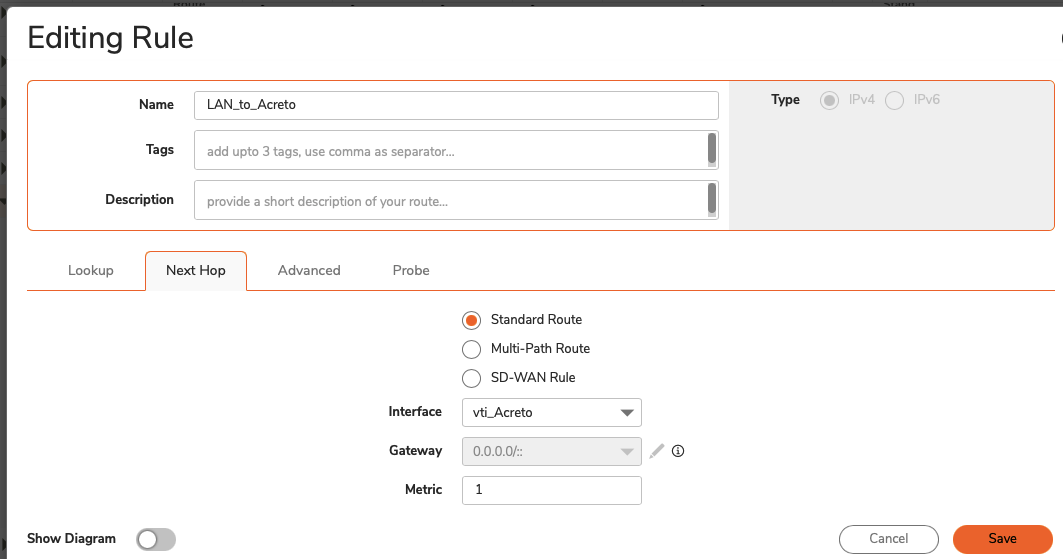

- Click the SAVE button
Verify existing or create a new access rule to allow the desired traffic
-
Goto POLICY » Rules and Policies » Security Policy
-
Click the Add button
-
Under General, provide the following values:
- Name: To_Acreto
- Action: Allow
- From: <Lan_interface>
- To: <tunnel_interface>
- Source Port: Any
- Service: Any
- Source: <lan_subnet>
- Destination: Any
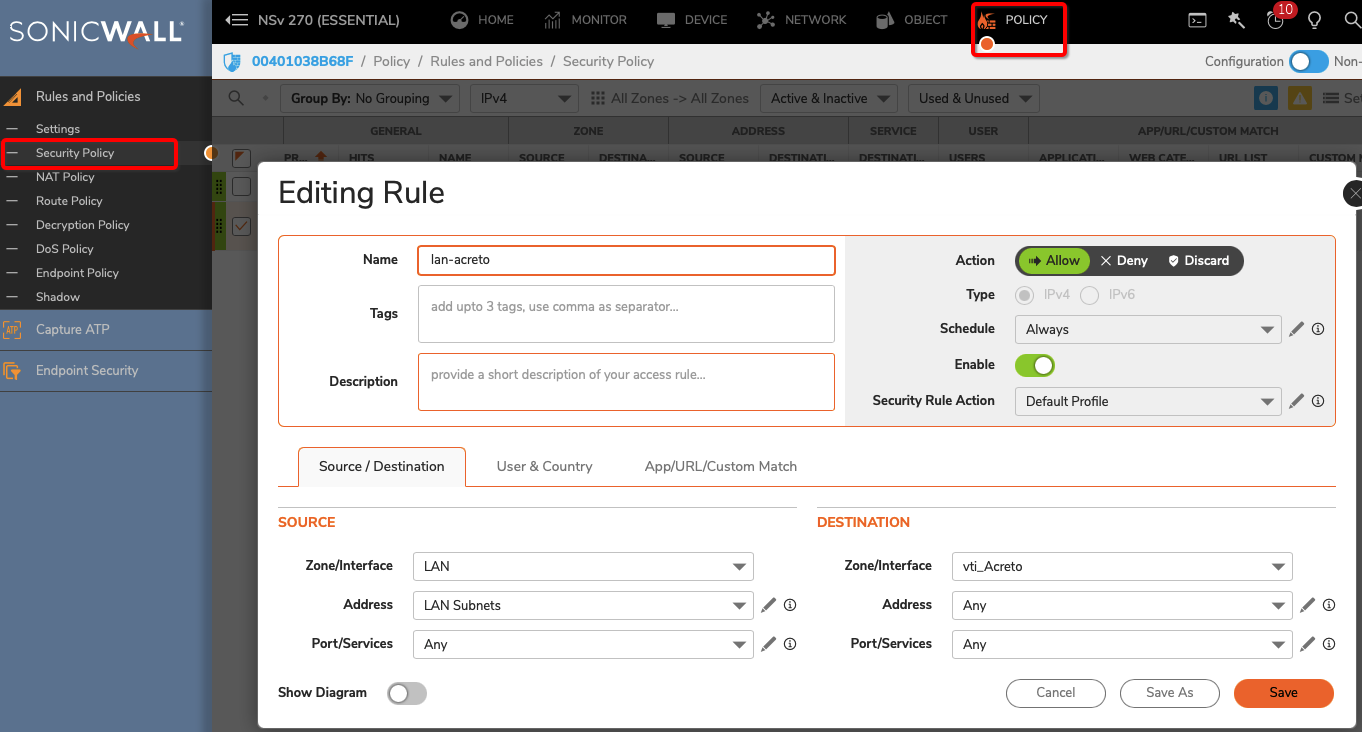

- Click the OK button
Task 6: Verify the connection
Once the tunnel connection is successfully established, its status will change to UP.
-
To verify the status on Sonicwall, navigate to goto NETWORK » IPsec VPN » Rules and Settings » Active Tunnels tab.
- The status of the VPN policy should be Green.
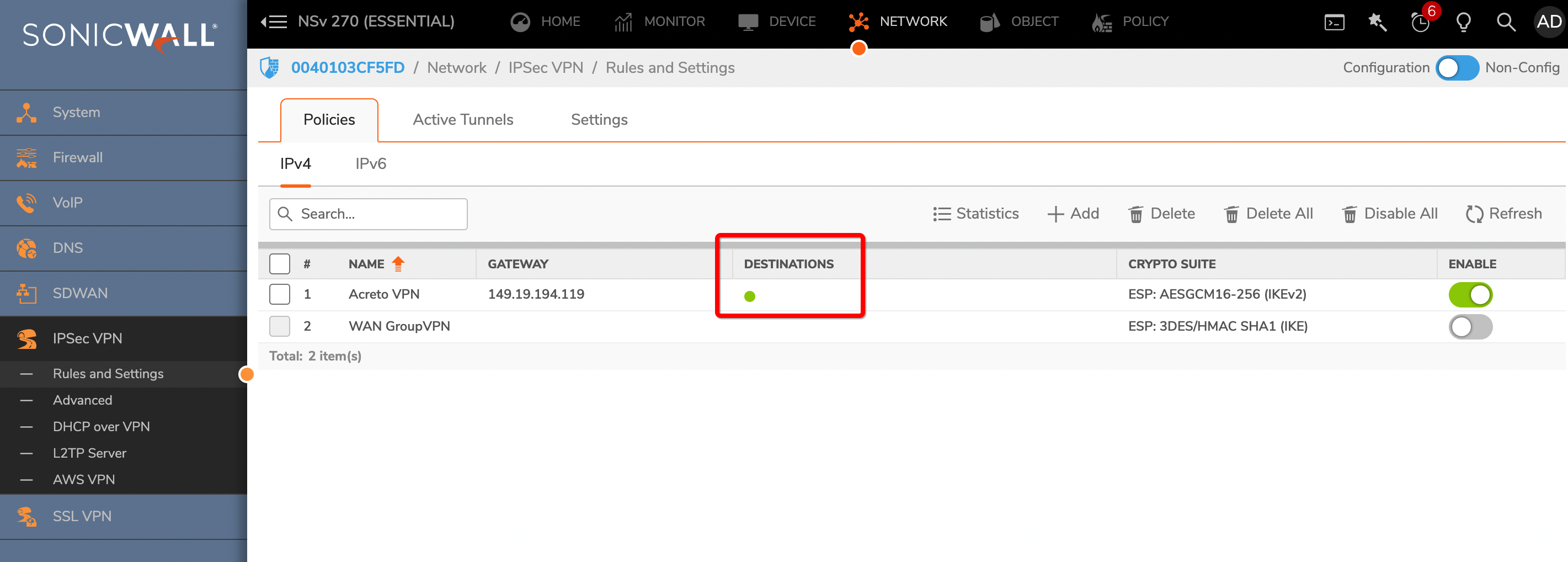

- Currently Active VPN Tunnels
The active VPN tunnel will be shown in the list.
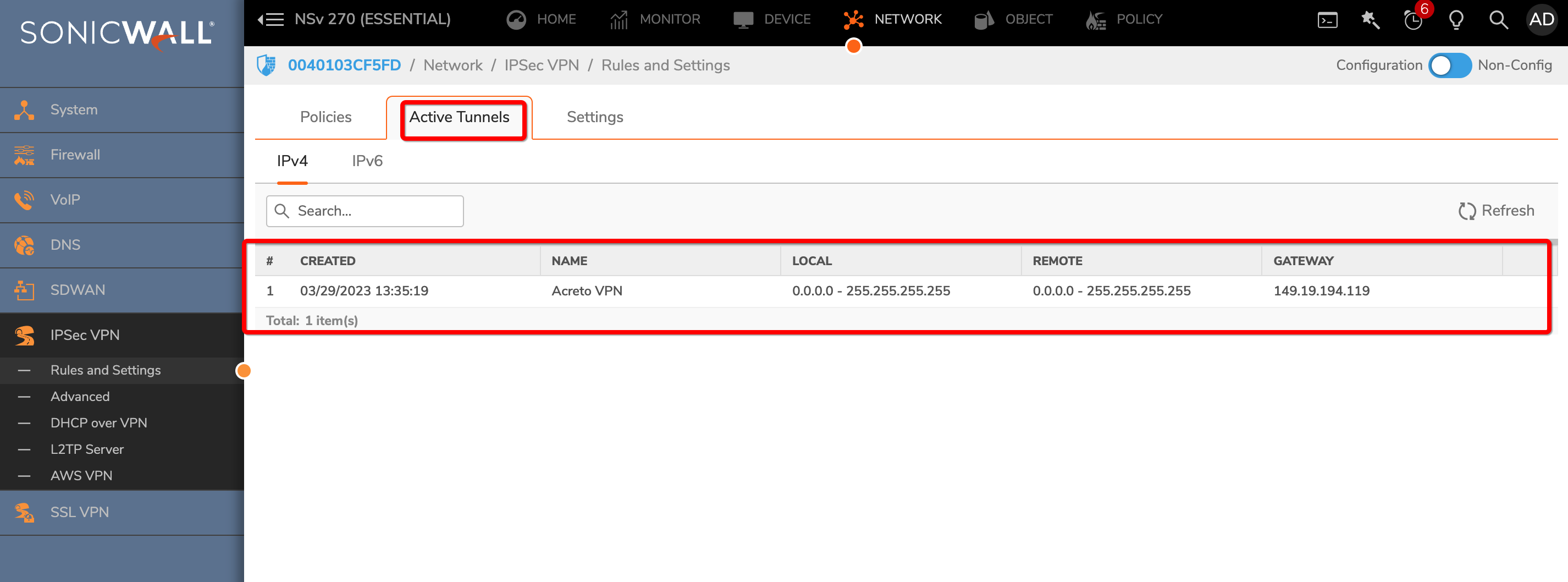

-
Execute tracert 1.1.1.1 (or traceroute 1.1.1.1) on internal server check the route to external host 1.1.1.1. It should show Acreto’s IP in the path.
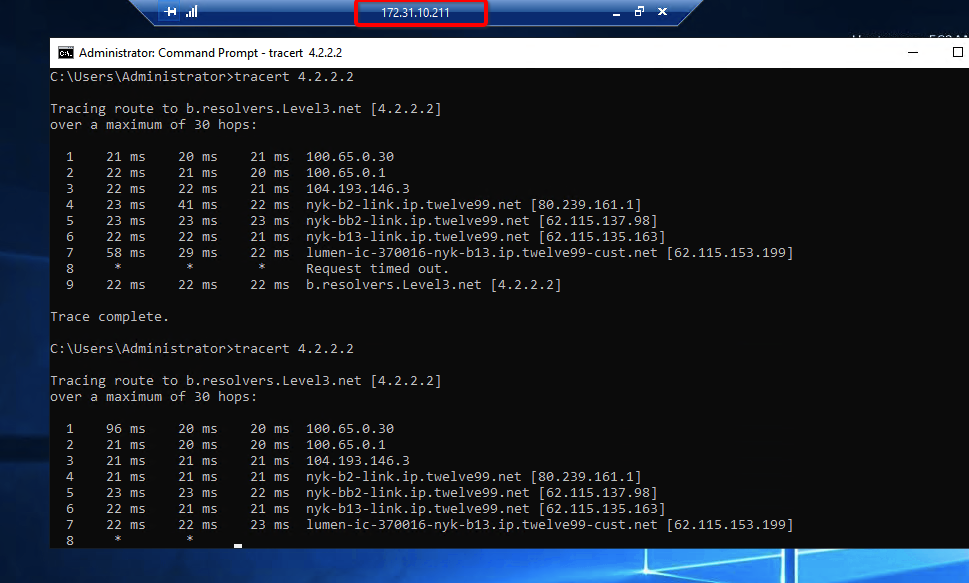

Summary
Once the VPN connection is successfully established, all the internal traffic to the internet will be routed through Acreto.
Sophos Ipsec with Acreto
Overview
This article will help you connect your Sophos XG with Acreto Ecosystem through the IPsec tunnel.
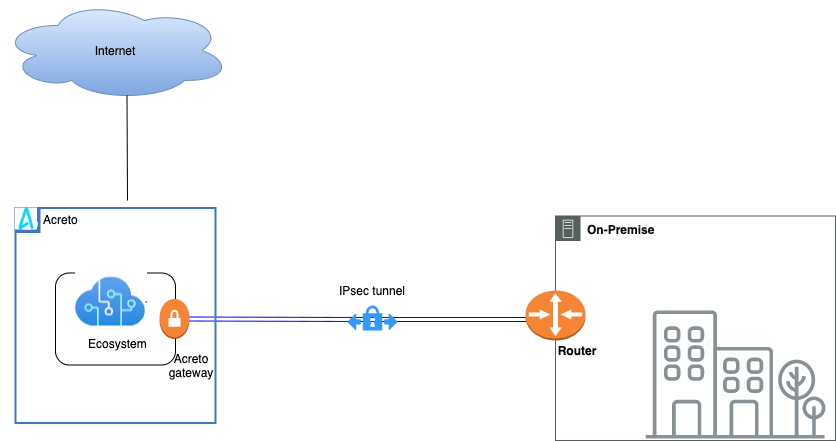

Prerequisites
- Sophos XG installation
- Ecosystem set up with proper security policies
Create Gateway for IPsec
Firstly, you will need to create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
- Name: IPsec connection name must meet the same requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed through this gateway.


Info
To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32 prefix for public interface). This will allow you to test connectivity from the gateway through Acreto by using Ping, Traceroute, or similar tools.
How-To
Task 1: Read IPsec Gateway Values Required for IPsec Configuration
To proceed with the Sophos configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
All of these may be found within the Gateway details panel - view the below animation for further instruction.
-
Log in to the Sophos Firewall panel as a user with an administrator role.
-
From the left side navigation, choose Configure > VPN (1).
-
Move to the IPsec policies tab (2) and click on the Add button (3) to create a new policy.

-
Fill the creation form with the following values:
-
General Settings
- Name: Acreto_ipsec
- Key exchange: ikev2
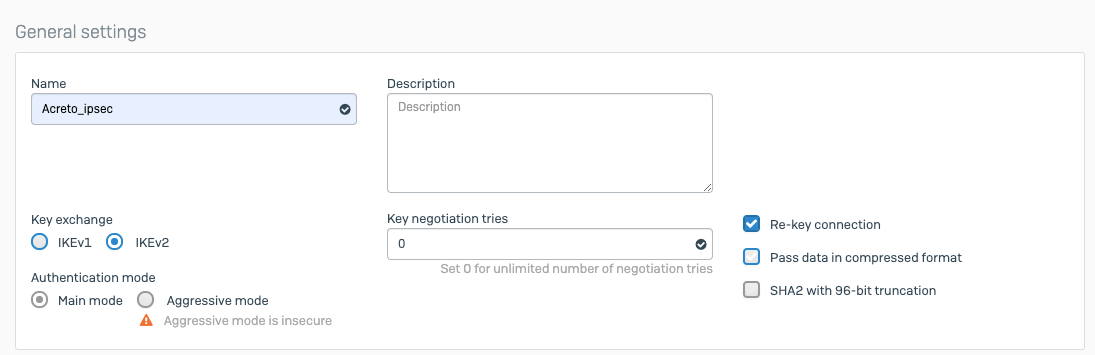

-
Phase1
- Key life: 10800
- DH group (key group): 14,16,20
- Encryption - Authentication:
- AES256 -SHA2 256
- AES128 - SHA2 256
- AES256 - SHA2 512
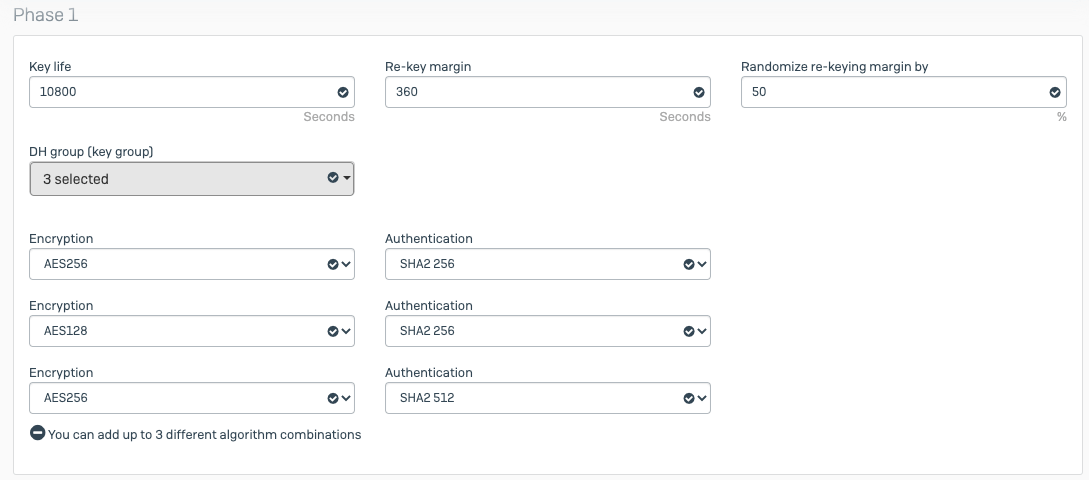

- Phase2
- PFS group (DH group): Same as phase1
- Key life: 3600
- Encryption - Authentication:
- AES256 -SHA2 256
- AES128 - SHA2 256
- AES256 - SHA2 512
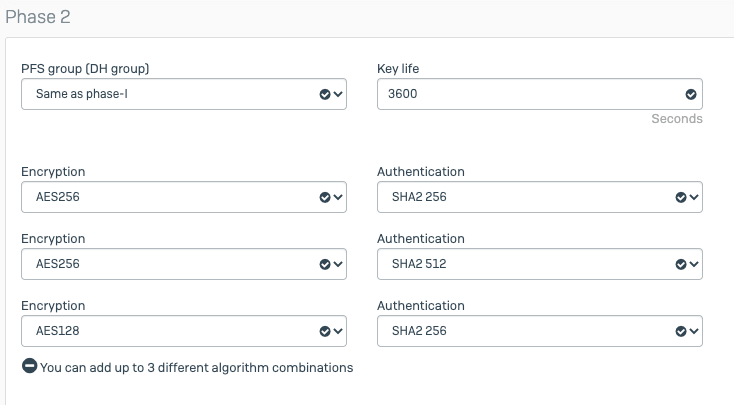

- Dead Peer Detection
- Dead Peer Detection: enable
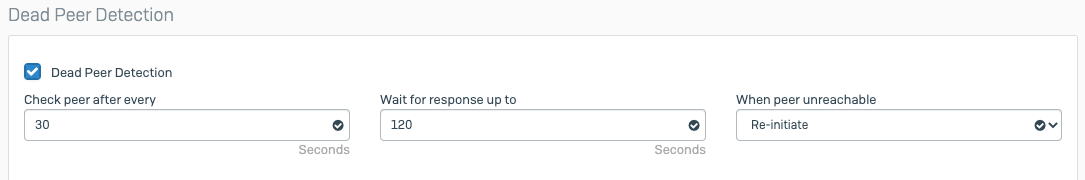

-
Click on the Save button to create the policy.
-
Goto VPN from left side navigator
-
Select tab IPsec connections and click Add button
-
Configure VPN with the following setting:
-
General Settings
- Name: Acreto
- IP version: IPv4
- Connection type: Tunnel interface
- Gateway type: Initiate the connection
- Activate on Save: enable
-
Encryption
- Policy: Acreto_ipsec
- Authentication type: Preshared key
- Preshared key: key (copied from Wedge)
- Repeat preshared key: key (copied from Wedge).
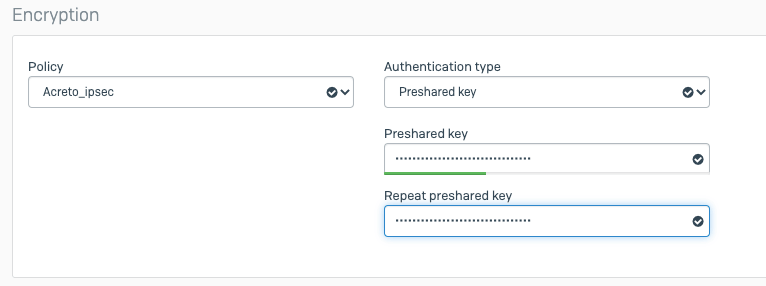

Gateway settings
-
Local gateway
- Listening interface: wan_ip
- Local ID type: DNS
- Local ID: peer_id (copied from Wedge)
-
Remote gateway
- Gateway address: acreto_gateway (copied from Wedge)
- Remote ID type: IP address
- Remote ID: acreto_gateway (copied from Wedge)
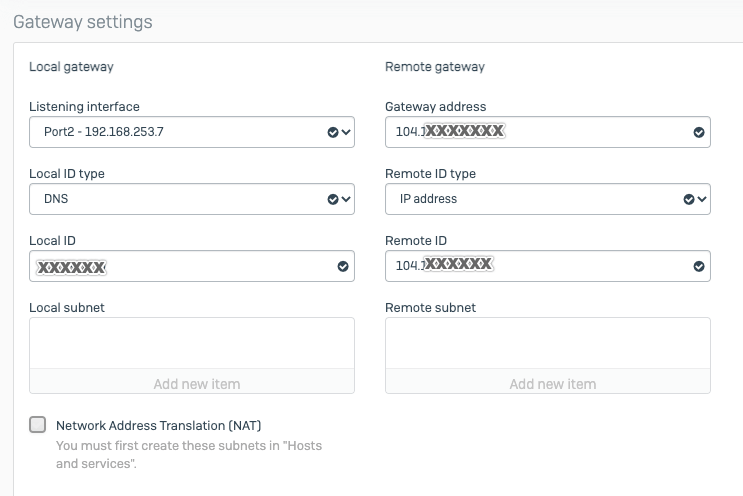

- Click Save.
Upon saving, the tunnel will try to establish a connection with Acreto, and upon successful connection, the tunnel will come up.


-
Goto Network from left side navigator
-
Select tab Network
-
Click the blue bar on the wan interface. It will unfold the new VPN tunnel interface formed
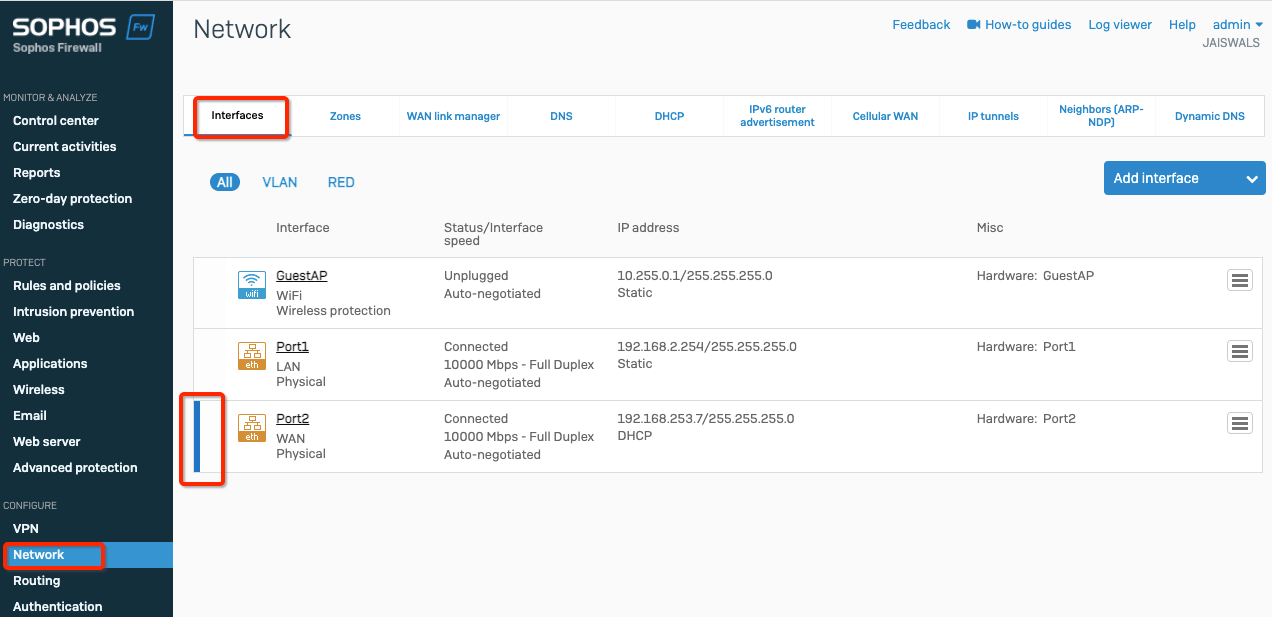

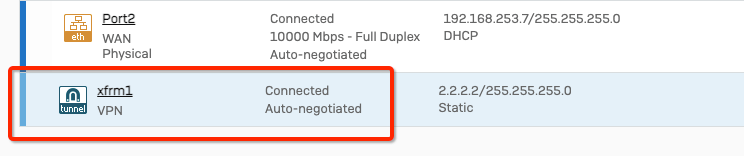

-
Click the tunnel interface and add some random IP
- IPv4/netmask - 2.2.2.2 /32
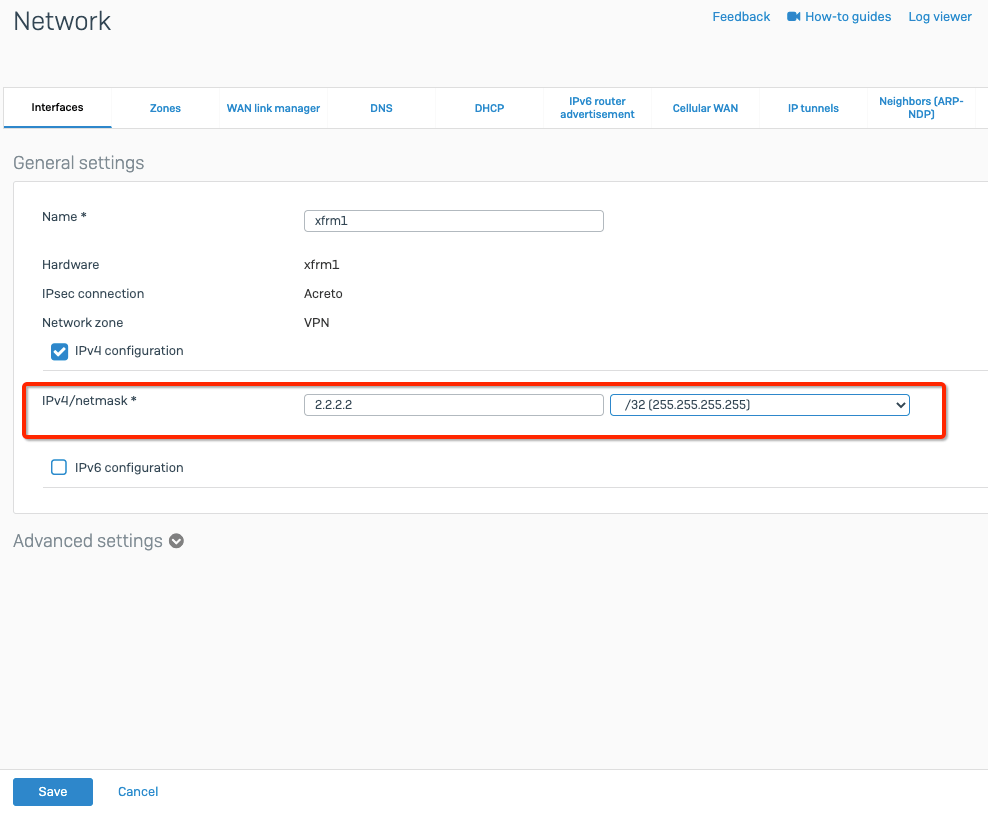

-
Click Save.
- Goto Routing from the left side navigator
- Select tab Static Routing
- Click Add button to configure the following routes
Direct route to Acreto gateway to establish the connection
- Destination IP/Netmask : acreto_gateway_ip /32 (copied from wedge)
- Gateway: ISP_gateway
- Interface: wan
- Distance: 0
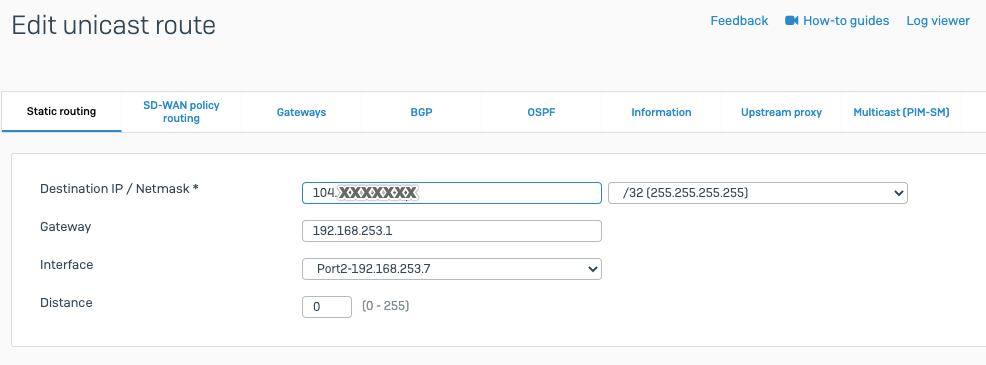

Default route to through the tunnel
- Destination IP/Netamsk: 0.0.0.0 /0
- Gateway: blank
- Interface: tunnel_inetrface
- Distance: 10
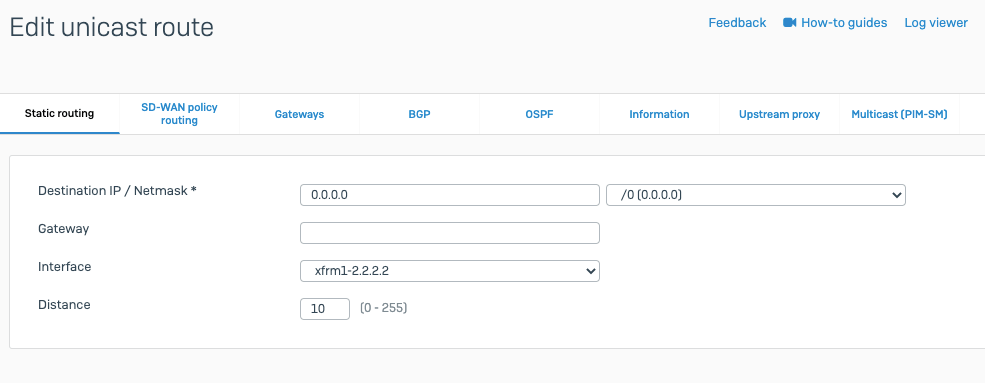

-
Goto Rules and policies from left side navigator
-
Select tab Firewall rules and click Add firewall rule to add a new firewall rule
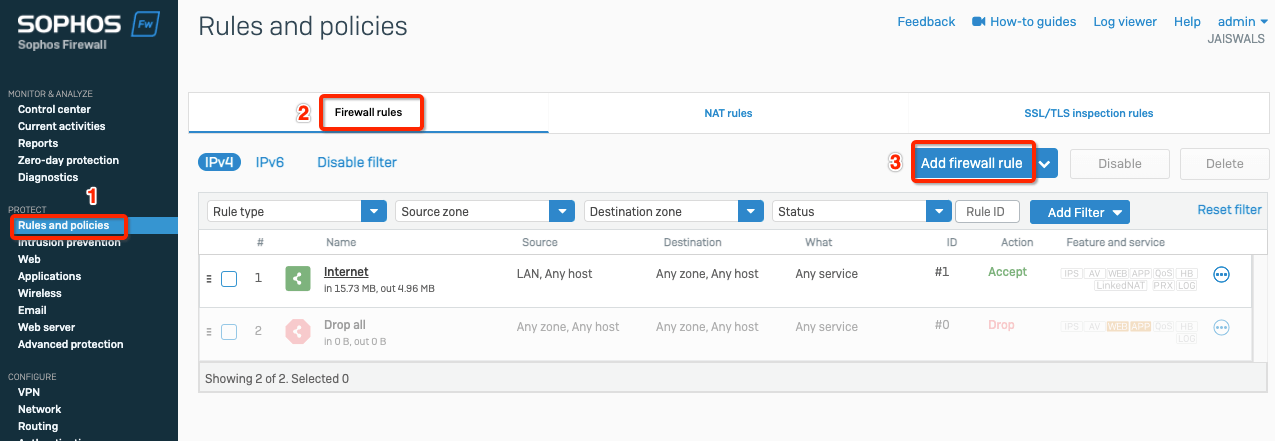

-
Create the firewall rule with values as below
Task 6: Verify the connection
Verify the connection is going through Acreto.
From any server in the internal subnet, do traceroute or mtr and verify if traffic is going through Acreto.
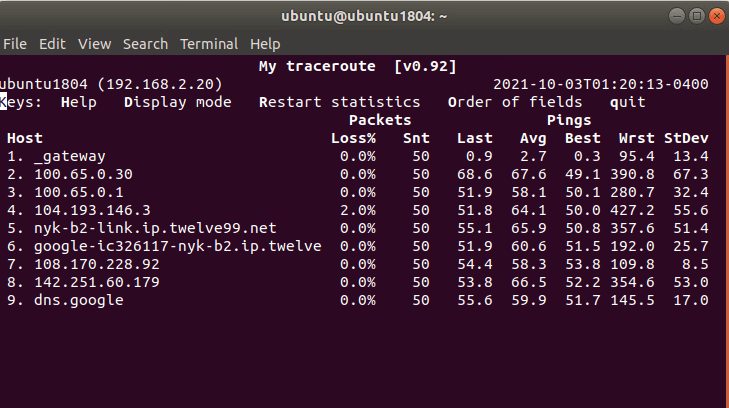

Summary
Once the VPN connection is successfully established, all the internal traffic to the internet will be routed through Acreto.
Troubleshooting - FortiGate Cloud Management issue
Issue
Forticloud management connection was lost after connecting to Acreto.
Description
When FortiGate is set up to route all traffic through Acreto, it may lose connection with FortiGuard/FortiCloud management servers.
Reason
When the default route is set towards Acreto, FortiGate sends all the FortiCloud connections through Acreto. However, while sending these requests, FortiGate uses its WAN IP as the source of the connection, which may not be allowed in Acreto EcoSystem.
To fix the issue, apply the solutions listed below:
Solution: Changes in FortiGate ( from the Customer side)
Alternatively, this issue can be resolved at the Customer location by setting Fortigate’s LAN IP as the source address for Fortiguard by following the steps below :
-
Login to Fortigate Dashboard
-
Goto Network > Interfaces > select the LAN interface
-
Copy the IP address of the LAN interface of FortiGate (Gateway IP for the LAN network)

-
Login to CLI of FortiGate.
-
Run the following commands:
config system fortiguard
set source-ip <ip_address_lan_interface>
end
Any one of the above solutions will restore the connection with FortiCloud.
Ubiquiti Unifi IPsec Configuration
Overview
In this article, you will learn how to connect to the Acreto ecosystem with your Unifi USG/Edgerouter using IPSec VPN.
Prerequisites
- Ubiquiti USG/EdgeRouter installation
- Ecosystem set up with proper
security policies
How-To
Step1: Create Gateway for IPsec
Firstly, you will need to create a new Gateway device in the Acreto platform. Instructions on how to create a new Gateway are available here.
If you already have one, make sure that it’s IPsec type and jump to How-to.
- Name: IPsec connection name must meet the same requirements as the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed through this gateway.


Info
To simplify testing, add the IP addresses of all interfaces connected to your gateway as Local Networks (you can use /32
prefix for public interface). This will allow you to test connectivity from the gateway through Acreto by using Ping, Traceroute, or similar
tools.
Step 2: Read the IPsec Gateway Values Required for Ubiquiti Configuration from Acreto Ecosystem
To proceed with the Ubiquiti configuration, you will need a few values from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Recommended Ciphers
- Peer ID
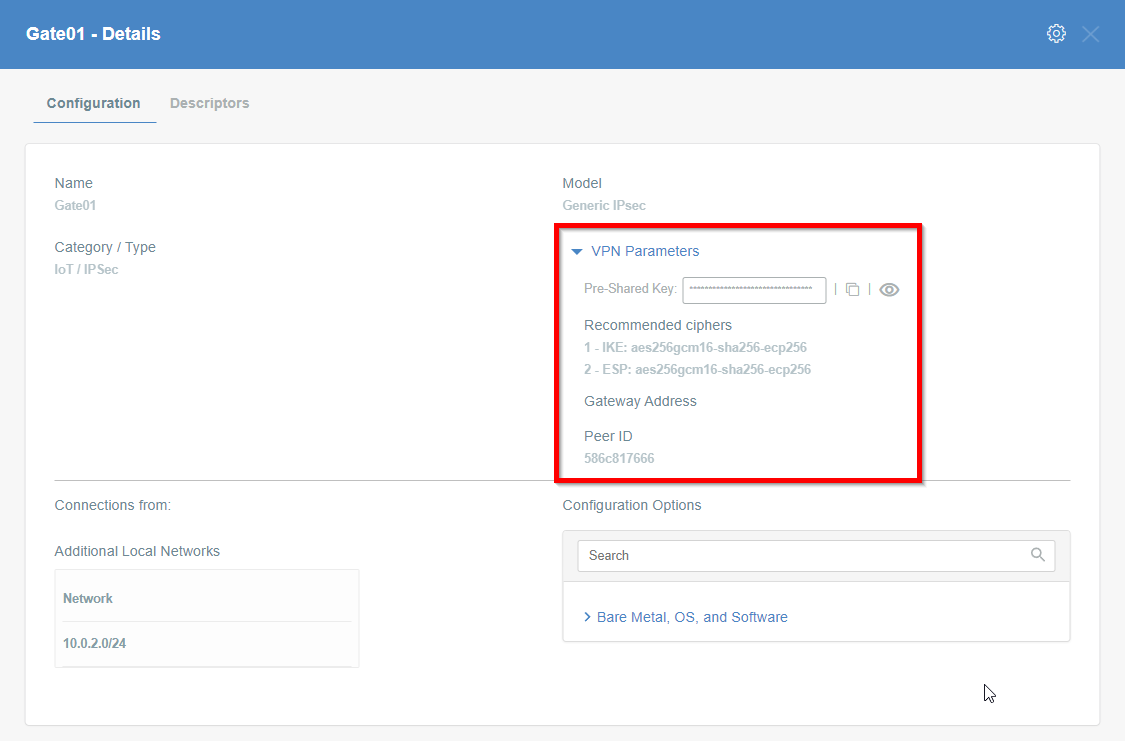

All of these may be found within the Gateway details panel - view the below animation for further instruction.
-
Login into Ubiquiti and enter Configuration mode
-
Enable the auto-firewall-nat-exclude feature which automatically creates the IPsec firewall/NAT policies in the iptables firewall.
set vpn ipsec auto-firewall-nat-exclude enable.
-
Create the IKE / Phase 1 (P1) Security Associations (SAs) by providing the following values
set vpn ipsec ike-group AcretoGate key-exchange ikev2
set vpn ipsec ike-group AcretoGate lifetime 10800
set vpn ipsec ike-group AcretoGate proposal 1 dh-group 16
set vpn ipsec ike-group AcretoGate proposal 1 encryption aes256
set vpn ipsec ike-group AcretoGate proposal 1 hash sha256
-
Create the ESP / Phase 2 (P2) SAs.
set vpn ipsec esp-group AcretoGate lifetime 3600
set vpn ipsec esp-group AcretoGate proposal 1 encryption aes256
set vpn ipsec esp-group AcretoGate proposal 1 hash sha256
set vpn ipsec esp-group AcretoGate compression disable
-
Execute the below command using values from previous steps:
Configure the below steps with values for Gateway address, Preshared key and Peer Id collected in Step 1.
- GATEWAY_ADDRESS - available in step 1, number 1 on screen.
- PRE-SHARED KEY - available in step 1, number 2 on screen.
- PEER ID - available in step 1, number 4 on screen.
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS authentication mode pre-shared-secret
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS authentication pre-shared-secret PRE-SHARED_KEY
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS description ipsec
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS authentication id PEER_ID
-
Copy the WAN IP and router address from the Ubiquiti gateway device

-
Use the above WAN IP and conFigure the Peer with the below commands
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS local-address LOCAL_WAN_INTERFACE
-
Link the SAs created in the above steps to the remote peer and bind the VPN to a virtual tunnel interface (vti0).
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS ike-group AcretoGate
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS vti bind vti0
set vpn ipsec site-to-site peer GATEWAY_IP_ADDRESS vti esp-group AcretoGate
-
Configure a static route to route gateway address to the internet directly. Use router address copied from step 6.
set protocols static route GATEWAY_IP_ADDRESS next-hop ROUTER_IP_ADDRESS
-
Configure default static route to send all traffic to Acreto VPN.
set protocols static interface-route 0.0.0.0/0 next-hop-interface vti0
-
Commit the changes and save the configuration.
Summary
Once the VPN connection is successfully established, all the internet traffic will be routed through Acreto.
Watchguard IPsec Configuration
Overview
This article will show you how to configure the Watchguard to connect to the Acreto Ecosystem. This configuration will be made by using IPsec VPN.
Prerequisites
- Watchguard installation
- Ecosystem set up with proper
security policies
How-To
Step 1: Create Gateway for IPsec
Firstly, you will need to create a new Gateway device in the Acreto
platform. Instructions on how to create a new Gateway are available
here.
- Name: IPsec connection name must meet the same requirements as
the Strongswan connection name (letters and numbers only).
- Category: IoT
- Type: IPsec
- Allow connection from: Empty (describes the source IP address
where the IPsec connection will be permitted).
- Local Networks: any local network addresses that will be routed
through this gateway.


Info
To simplify testing, add the IP addresses of all
interfaces connected to your gateway as Local Networks (you can use /32
prefix for public interface). This will allow you to test connectivity
from the gateway, or similar
tools.
Step 2: Read the Values from Acreto Gateway
To proceed with the Watchguard configuration, you will need a few values
from an existing committed Acreto Gateway:
- Gateway Address
- Pre-Shared Key
- Peer ID
- Recommended Ciphers


All of these may be found within the Gateway details panel - view the
below animation for further instruction.
-
Create Phase 2 proposal - Navigate to VPN > Phase 2 Proposals and click ADD button

-
Create Phase 2 with the following values and SAVE
- Name: Acreto
- Description: Acreto phase2 selectors
- Type: ESP
- Authentication: SHA-512
- Encryption: AES(128-bit)
- Time: 1 hour

-
To set up IPsec VPN navigate to VPN > BOVPN Virtual Interfaces and click ADD from the right pane
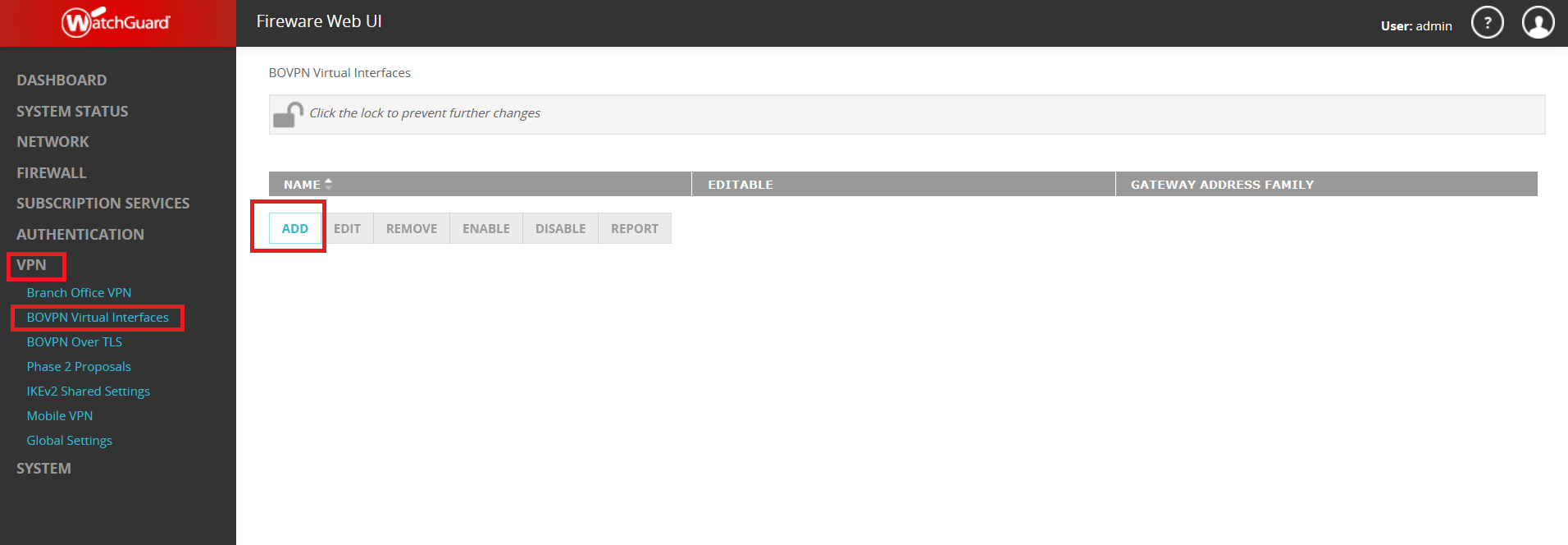

-
Select Remote Endpoint Type as Cloud VPN or Third-Party Gateway
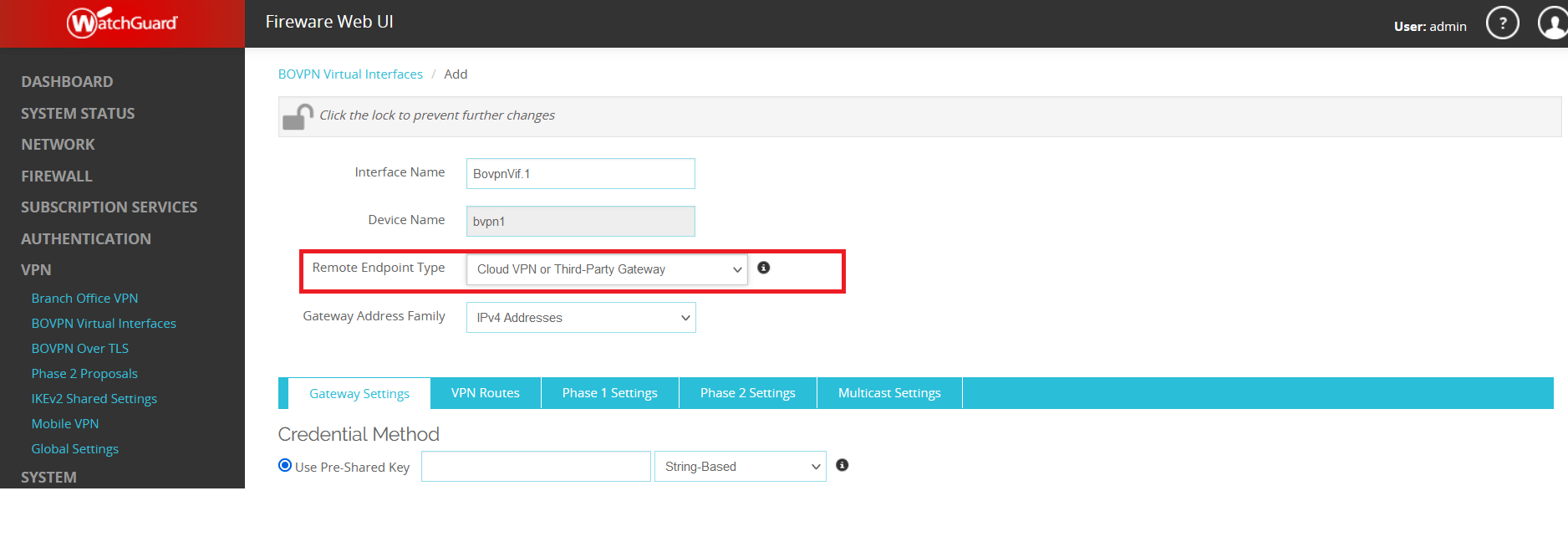

-
Provide the Preshared key copied from the Wedge dashboard in Step 1 and click ADD button to configure Gateway Endpoint
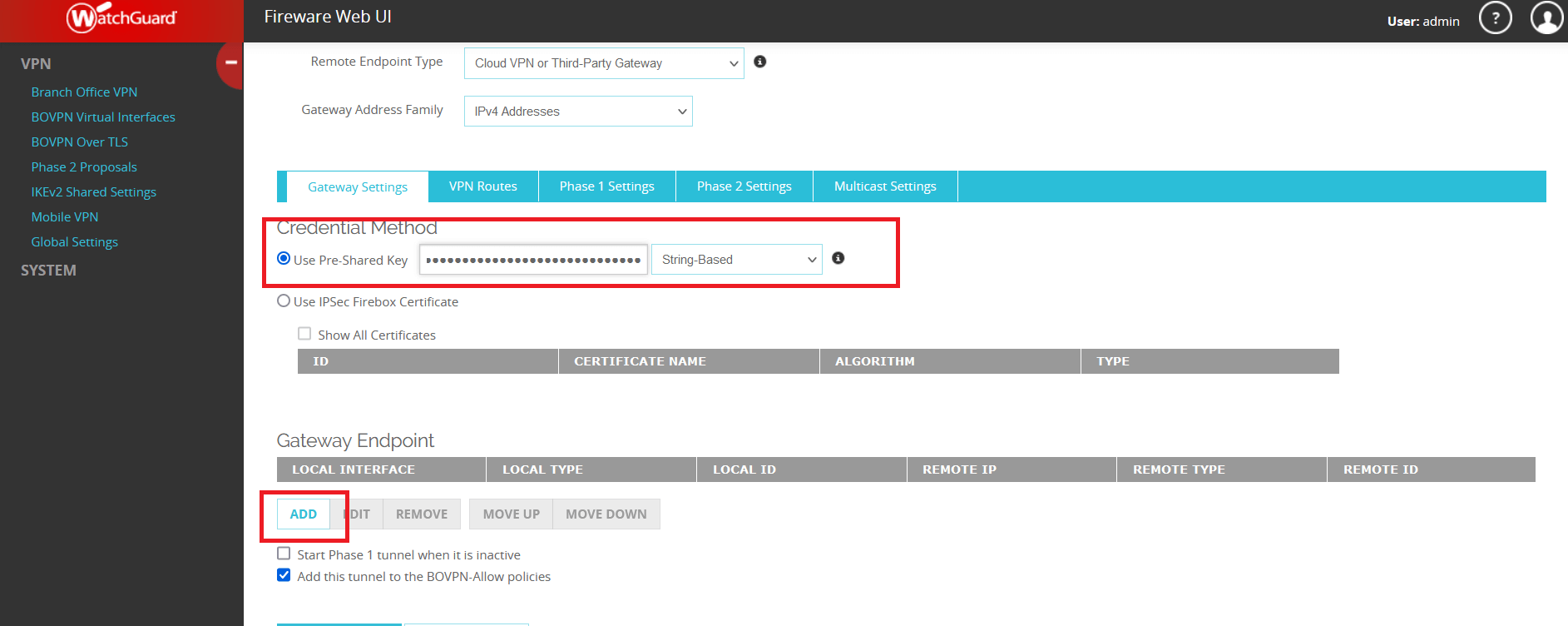

-
Configure Local gateway - Select Interface By Domain Name and provide the Peer ID copied from Wedge dashboard in Step 1.
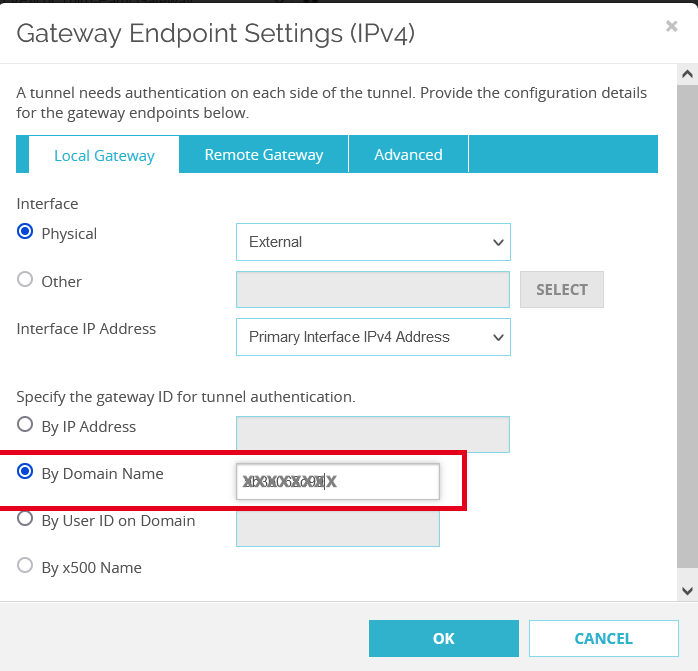

-
Configure Remote gateway with values copied in Step 1 and click OK
- Static IP Address : Wedge_gateway
- By IP Address: Wedge_gateway
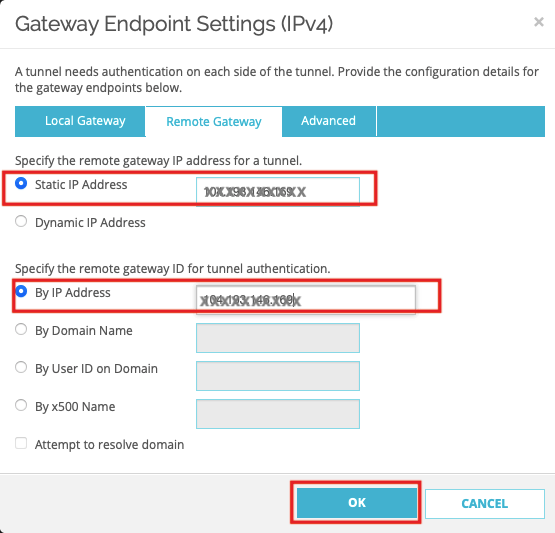

-
Click Phase 1 Settings tab

-
the following values
- Version: IKEv2
- Keep-alive interval: 540 seconds
- Traffic-idle timeout: 30 seconds

- Select the Phase 1 Transform set in Transform Settings and click EDIT. Set the following values and click OK.
- Authentication: SHA2-512
- Encryption: AES(28-bit)
- SA Life: 3 hours
- Key Group: Diffie-Hellman Group 15

- Click Phase 2 Settings and configure Phase 2 with values as below
- Enable Perfect Forward Secrecy: Diffie-Hellman Group 15
Select Acreto from Phase 2 proposal and ADD and SAVE.
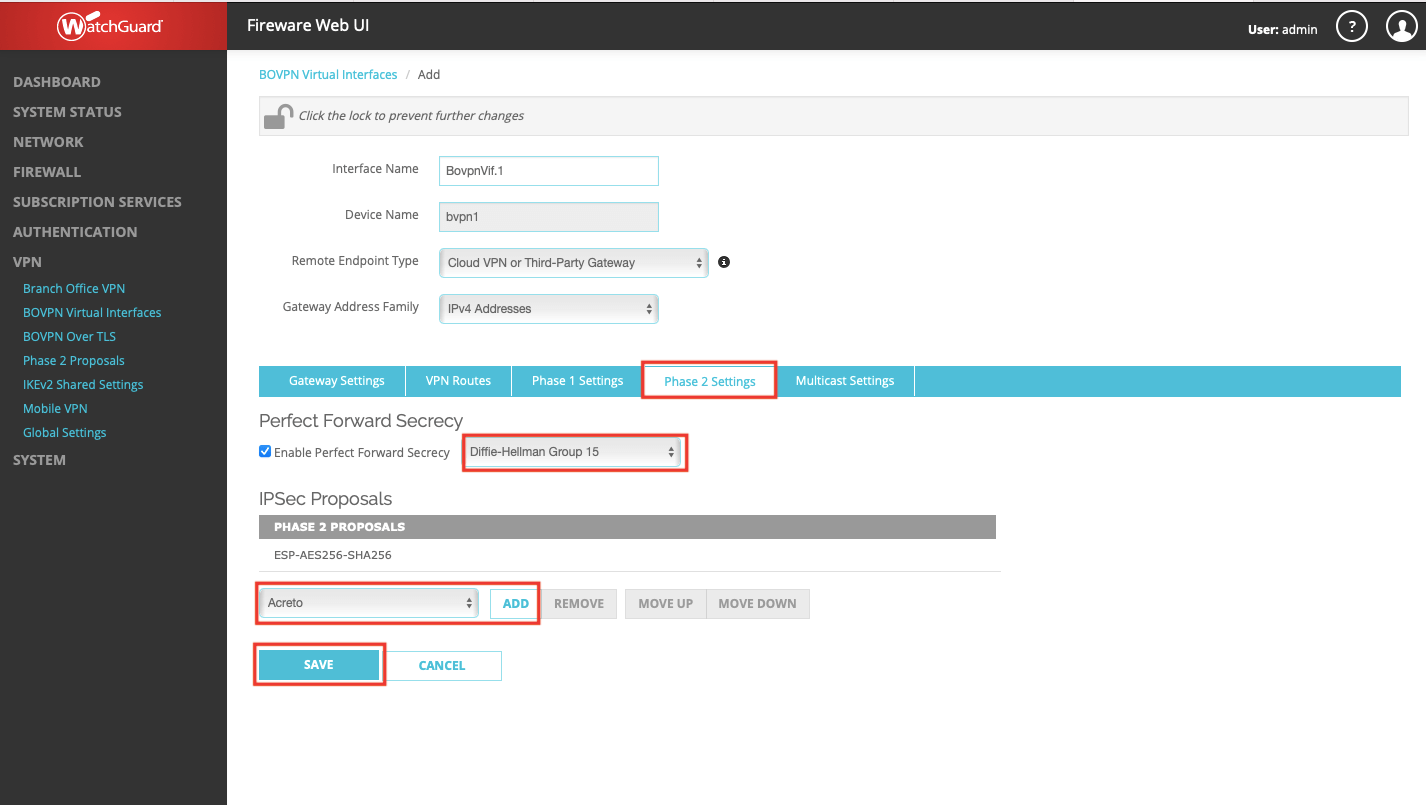

- Verify the tunnel status - Navigate to SYSTEM STATUS > VPN Statistics > Branch Office VPN and click IKEv2 Virtual Interface. If the VPN is successfully established, the statistics related to VPN will be displayed.

Summary
Once the VPN connection is successfully established, all the internet traffic will be routed through Acreto.