Multifactor Authentication
What is Multifactor Authentication, and why should you use it?
Two-Factor Authentication (2FA or MFA) - 2FA is an extra layer of security to ensure that people trying to access an online account are who they say they are. First, a user will enter their username and password. Then, instead of immediately gaining access, they must provide other information. For example, this second factor could come from one of the following categories:
- Something you know: This could be a password
- Something you have: Typically, a user would have something in their possession, like a smartphone, or a small hardware token
- Something you are: This might include a biometric pattern of a fingerprint, an iris scan, or a voice print
Acreto supports the most popular form of two-factor authentication - which uses a software-generated time-based, one-time passcode (also called TOTP, or “soft-token”) and also auth-code sent to the user’s email.
First, users must download and install a free 2FA app on their smartphone or desktop. They can then use the app with any site supporting this authentication type. At sign-in, the user first enters a username and password, and then, when prompted, they enter the code shown on the app. Like hardware tokens, the soft token is typically valid for less than a minute. And because the code is generated and displayed on the same device, soft tokens remove the chance of hacker interception. That’s a big concern with SMS or voice delivery methods.
Since app-based 2FA solutions are available for mobile, wearables, or desktop platforms — and even work offline — user authentication is possible almost everywhere.
Prerequisities
To start using MFA, you must own an application that will be your second-factor code generator.
Several popular MFA (Multi-Factor Authentication) applications are available in the market:
- Google Authenticator: Google Authenticator is a free MFA app for Android and iOS devices. It generates time-based one-time passwords (TOTP) to provide an additional layer of security for Google accounts and third-party accounts that support the TOTP protocol.
- Microsoft Authenticator: Microsoft Authenticator is a free MFA app that generates TOTP codes and pushes notifications for Microsoft and third-party accounts supporting the TOTP or OpenID Connect protocols.
- Authy: Authy is a free MFA app that generates TOTP codes, push notifications, and SMS-based codes. It supports various third-party accounts and the Authy OneTouch feature for fast and easy authentication.
- Duo Mobile: Duo Mobile is a free MFA app that generates push notifications, SMS-based and TOTP codes. It supports various third-party accounts and the Duo Push feature for fast and easy authentication.
All mentioned application uses starts supported by Acreto - choose the best tool for you and install it on your device.
How Acreto uses MFA to provide security?
Acreto uses Multifactor Authentication in two scenarios:
- Secure Ecosystem Access - Ecosystem Administrator can activate the MFA to secure access to Acreto Portal.
- MFA Based Profiles for users - this future allows to force all users connecting to Ecosystem to use MFA in the defined period. For example, each person connected to MFA must confirm the connection with the MFA token once a day.
Both of these options are optional and can be enabled or disabled any time.
Summary
In an increasingly interconnected and threat-prone digital landscape, Multi-Factor Authentication has emerged as a “must-have” feature for organizations and individuals. By mitigating password vulnerabilities, enhancing security, complying with regulations, and offering user convenience, MFA significantly strengthens access control and protects against unauthorized access and data breaches. Implementing MFA is a proactive step towards bolstering overall cybersecurity posture and safeguarding sensitive information.
Subsections of Multifactor Authentication
MFA for Acreto Connect Client - How To Enable
Before You Start
What is Multifactor Authentication and why should you use it?
Two-Factor Authentication (2FA or MFA) - 2FA is an extra layer of security to ensure that people trying to access an online account are who they say they are. First, a user will enter their username and password. Then, instead of immediately gaining access, they must provide other information.
Read more about why you should enable MFA in Acreto Ecosystem in this article.
Prerequisites
To enable MFA for Ecosystem users, there are some steps required:
- Make sure that all users know what the MFA is and why you enable it.
- You need to be Ecosystem Administrator to enable this option.
- Ecosystem users need to be imported to Ecosystem by Identity Provider
How To
Step 1: Enable the MFA for Users
To activate Multi-Factor Authentication for the Ecosystem users, login into Acreto Portal and choose your Ecosystem from the Ecosystem list.
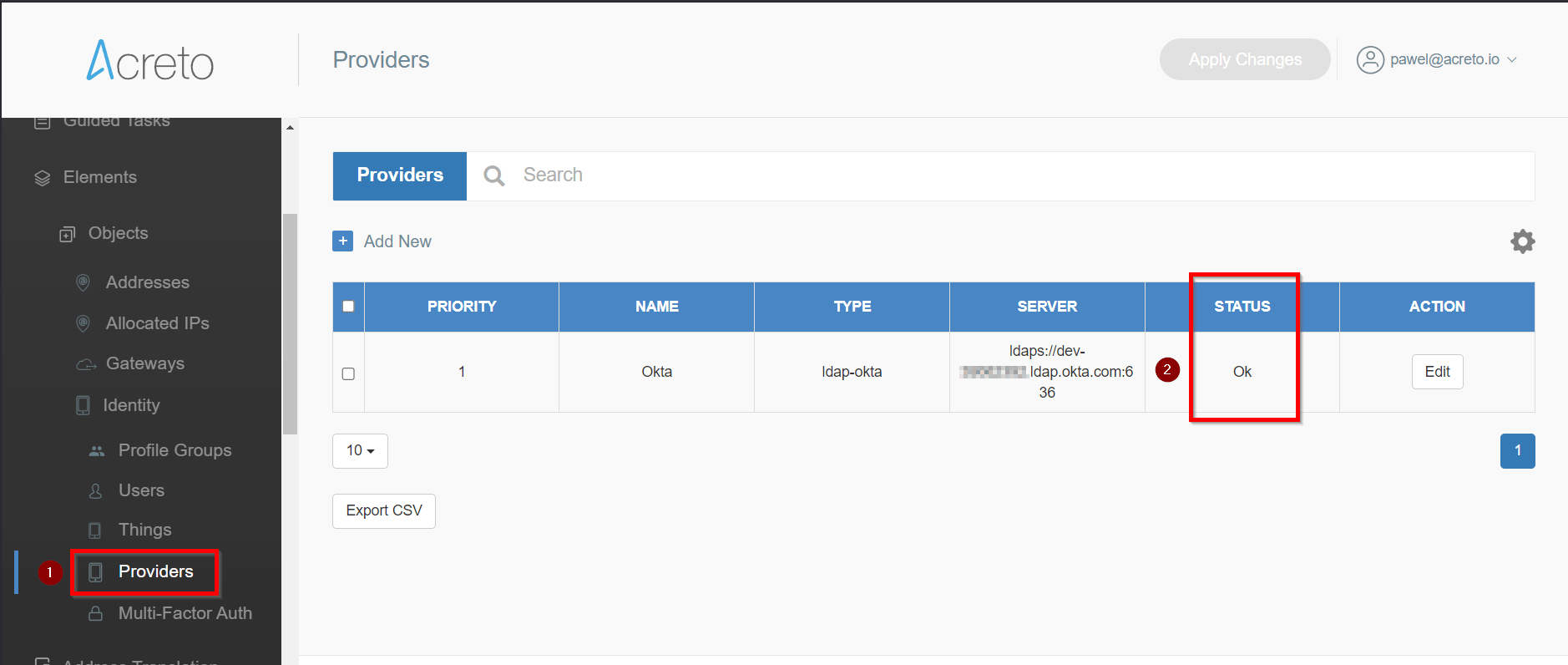

Move to Multi-Factor Auth (1) and enable the MFA option (2). When enabled, you may change the available source of the second factor (3).
You may enable a One-time password generator like Google Auth or/and email address. In the second case, the user will receive an email message with a code on each authentication. You may find more details about the second factor in an article for users.
This setting only enables the configurable option for the user, which may choose from available methods when configuring MFA for his account.
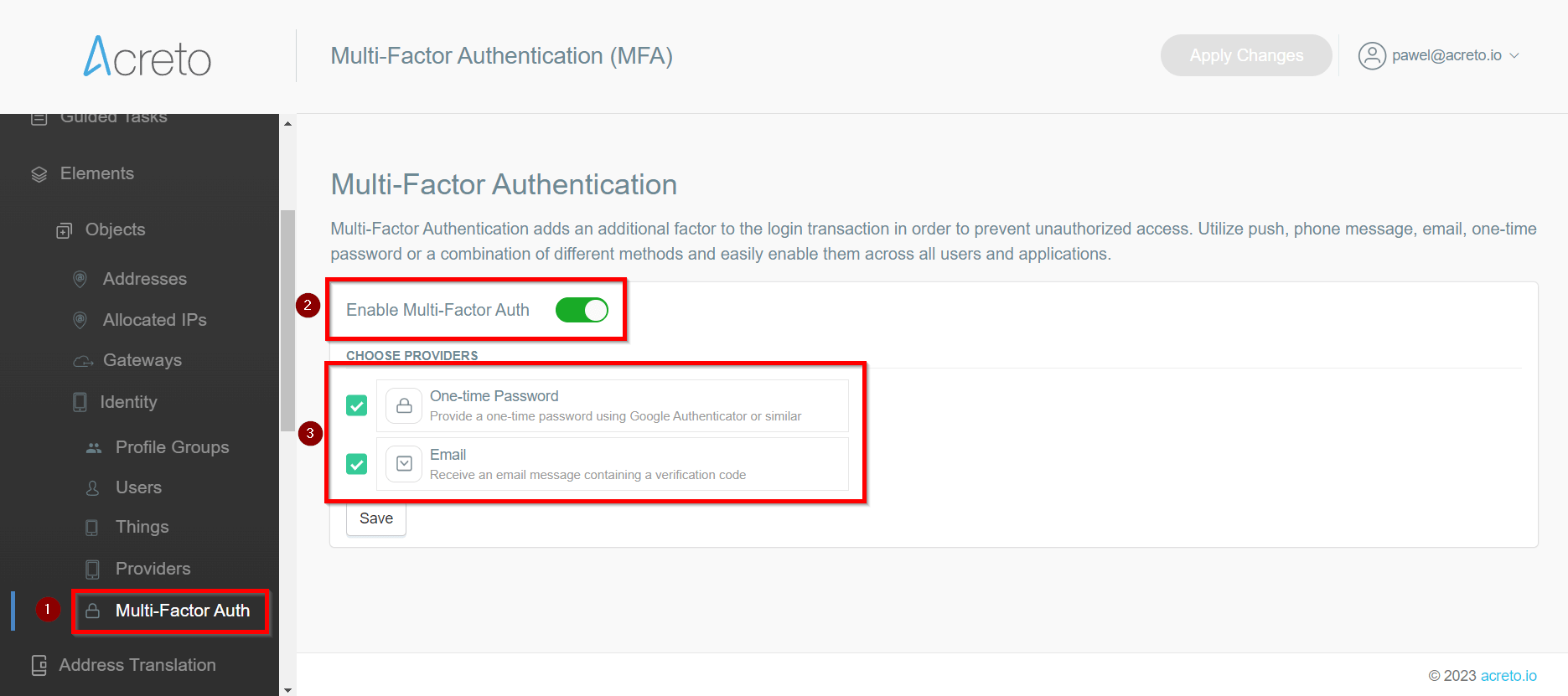

Save and commit the settings.
Step 2:
When the MFA is enabled, go to the Users section and invite all users again - this will generate a special type of Acreto Connect Client profile with MFA support.
This part of the procedure is mandatory - this invitation allows users to set up their Multi-Factor access.
Choose the users from the list and send the invitation.
Reset MFA
Working with users, you may expect many potential issues with the second factor - lost devices, forgotten passwords, etc.
The best solution for all potential issues with locked access is a reset of the MFA. However, this action is available only to Ecosystem Administrator for security reasons.
If the users need to reset the MFA, they should ask Administrator to reset MFA.
Ecosystem Administrator can then go to the Users list in Acreto Portal, choose a user, and perform Reset MFA or Reset and Logoff action.
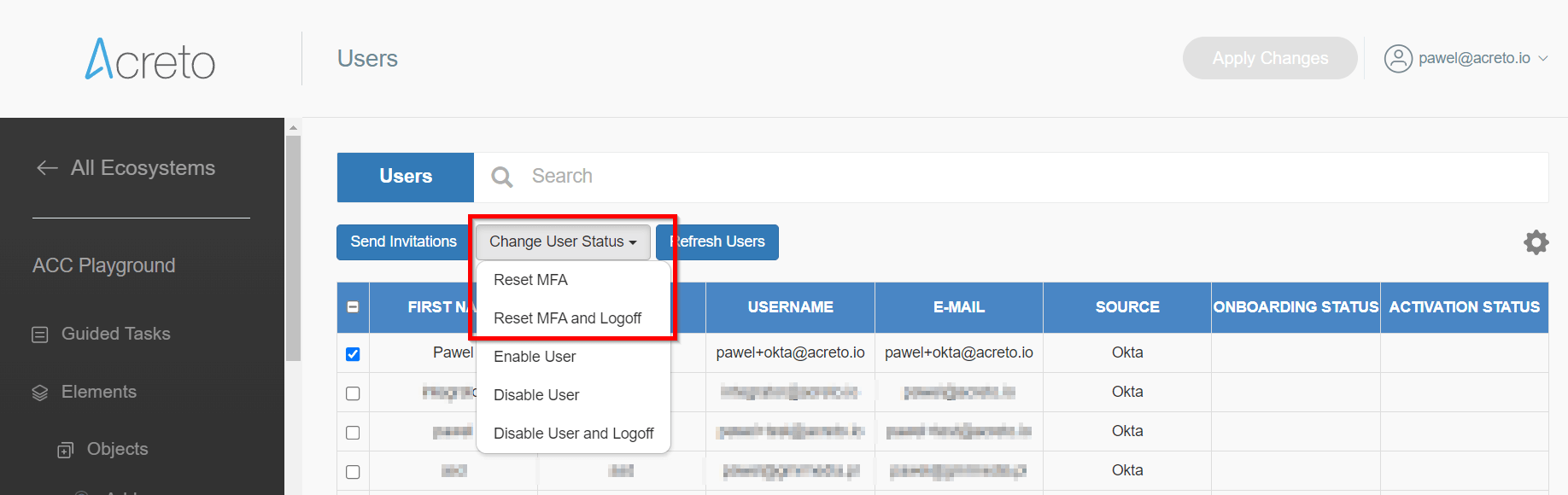

The reset option is dedicated to users who " forgot " the MFA device/source credentials. In case of the situation when the device was stolen, the best practice is to use Reset MFA and Logoff - this will automatically close all existing Acreto sessions related to this device.
Summary
MFA is an easy-to-enable and managed feature that increases security to another level.
MFA for Acreto Connect Client - User Guide
Before You Start
What is Multifactor Authentication, and why should you use it?
Two-Factor Authentication (2FA or MFA) - 2FA is an extra layer of security to ensure that people trying to access an online account are who they say they are. First, a user will enter their username and password. Then, instead of immediately gaining access, they must provide other information.
This article explains why you should enable MFA in Acreto.
Prerequisites
The Administrator of your Ecosystem should Enable the MFA for you.
To get the best User Experience with Acreto MFA, you need to download and install Acreto Connect Client
How To
Step 1: Start the Onboarding Procedure
If MFA is enabled in your Ecosystem, you should receive an Invitation email that allows you to set up the MFA for your account.
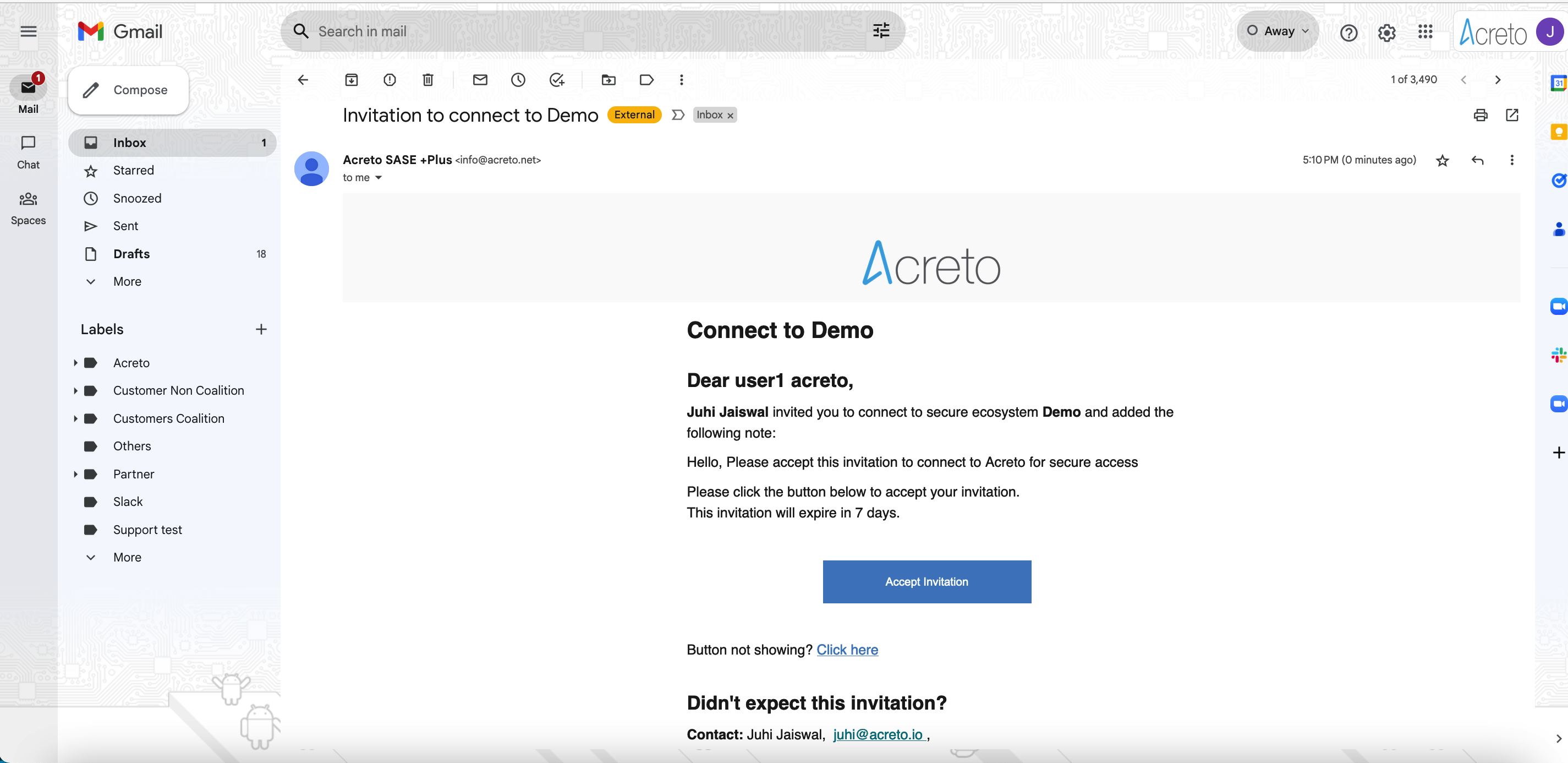

Click the Button Accept Invitation to start the onboarding process. Next, you see an MFA setup page - provide your username and password registered on Identity Provider ( Generic LDAP, Azure Active Directory, Windows Server AD, Google Workspace, etc.) and select one of the Multi-Factor Providers to register their Multi-factor device.
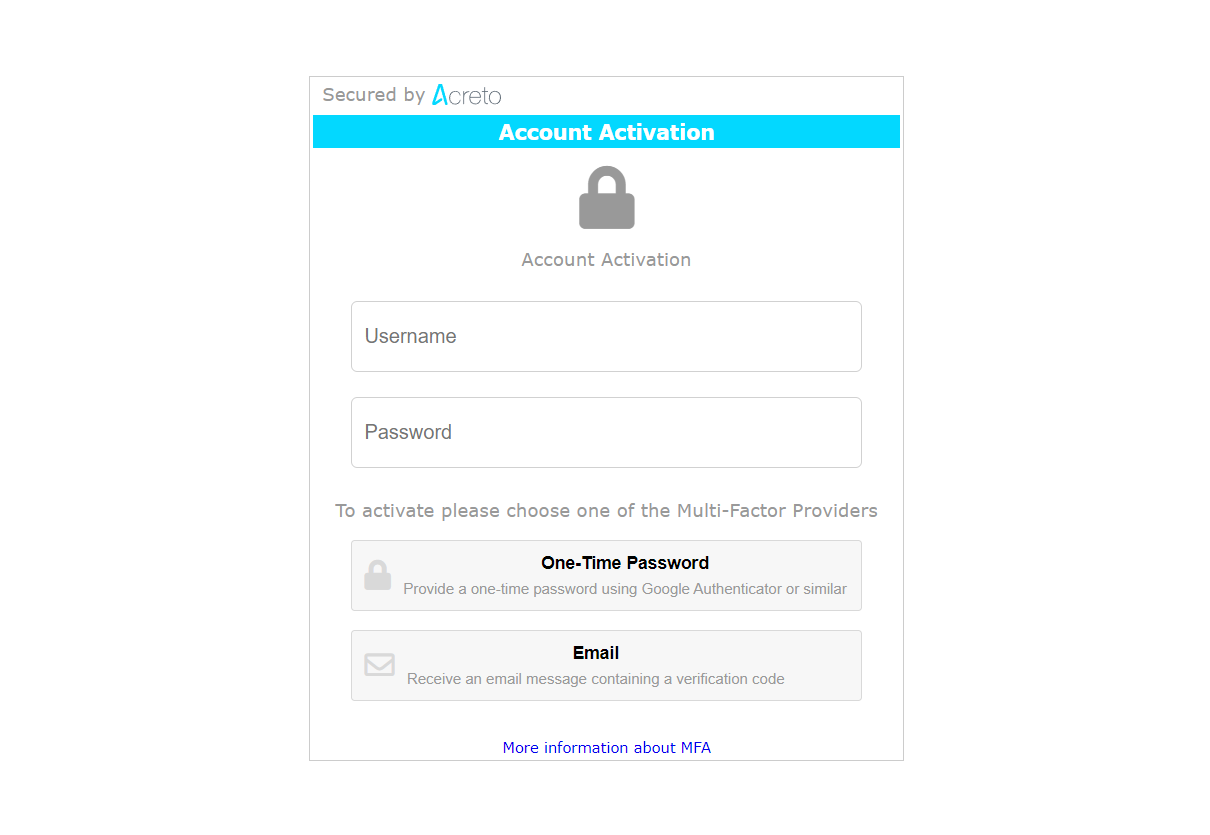

On this screen, you may also choose the second-factor method: Email or Authentication Application - more details about them in next the step.
Step 2: Choose the Second Factor
There are two ways of receiving the second factor of authentication - Email and Authentication Application.
Email
- If you choose Email as the Multi-factor provider, you receive the auth code as an email message whenever you try to log in.
- Provide the token received on the email on the Acreto auth page.
- Whenever the token expires(generally 24 hours), Acreto will prompt for reconnection, and the user will have to provide the username/password and new token sent via email to reconnect.
- Proceed to the next step for finishing the Onboarding process to Acreto VPN.
One-Time Password
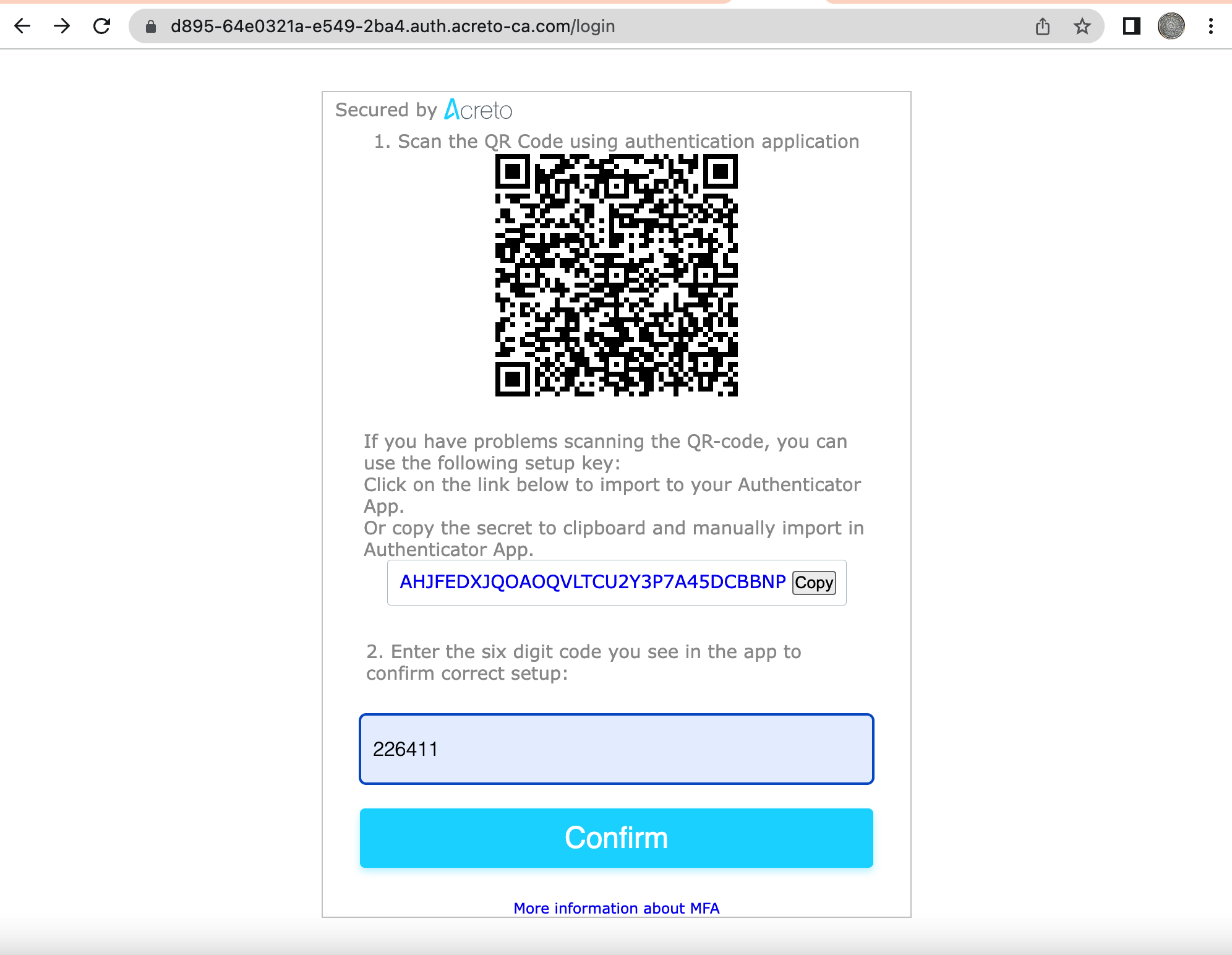
- If you choose One-Time Password as the Multi-factor provider, you need to scan the QR code screen to register the authenticating device which can receive the token.
- Download Google Authenticator or an equivalent app from the App Store on your mobile device.
- Scan the QR code on the Acreto page to add the account on the Authenticator app.
- The Authenticator app will generate the token after adding the account. Use the token on the Authenticator app and provide it on the token box on the Acreto page.
- Whenever the token expires(generally 24 hours), Acreto will prompt for reconnection, and the user will have to provide the username/password and token generated on the Authenticator app to reconnect.
- PProceed to the next step for finishing the Onboarding process to Acreto VPN.

Step 3: Complete the onboarding process
- After successful authentication, the user will be provided the link to download the VPN configuration.
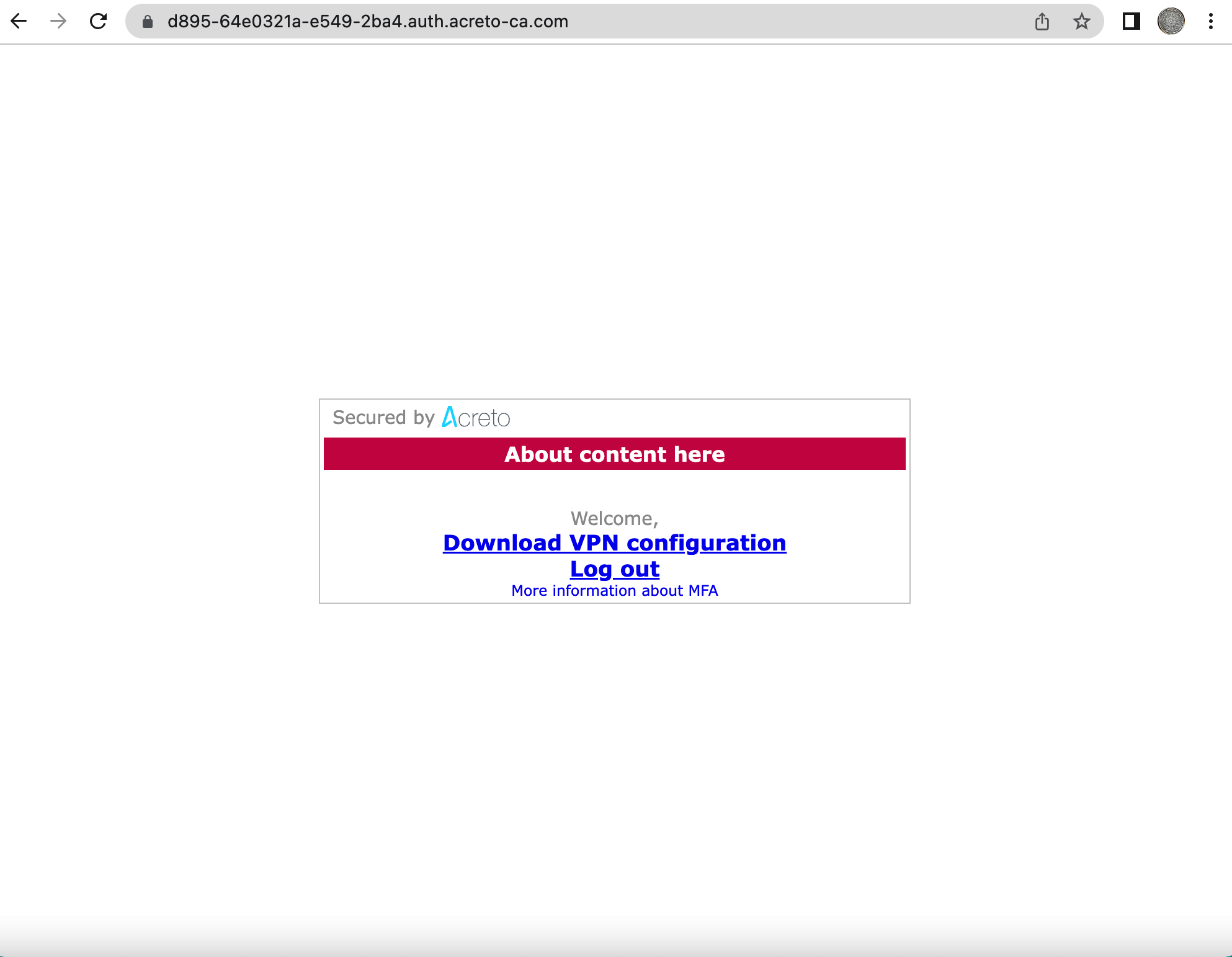

- Click the link to download the VPN configuration.
- Import the downloaded VPN configuration on the Acreto Connect Client
- Upon successful import, the Acreto VPN will be auto-connected.
- Verify your connection by checking Acreto’s ISP.
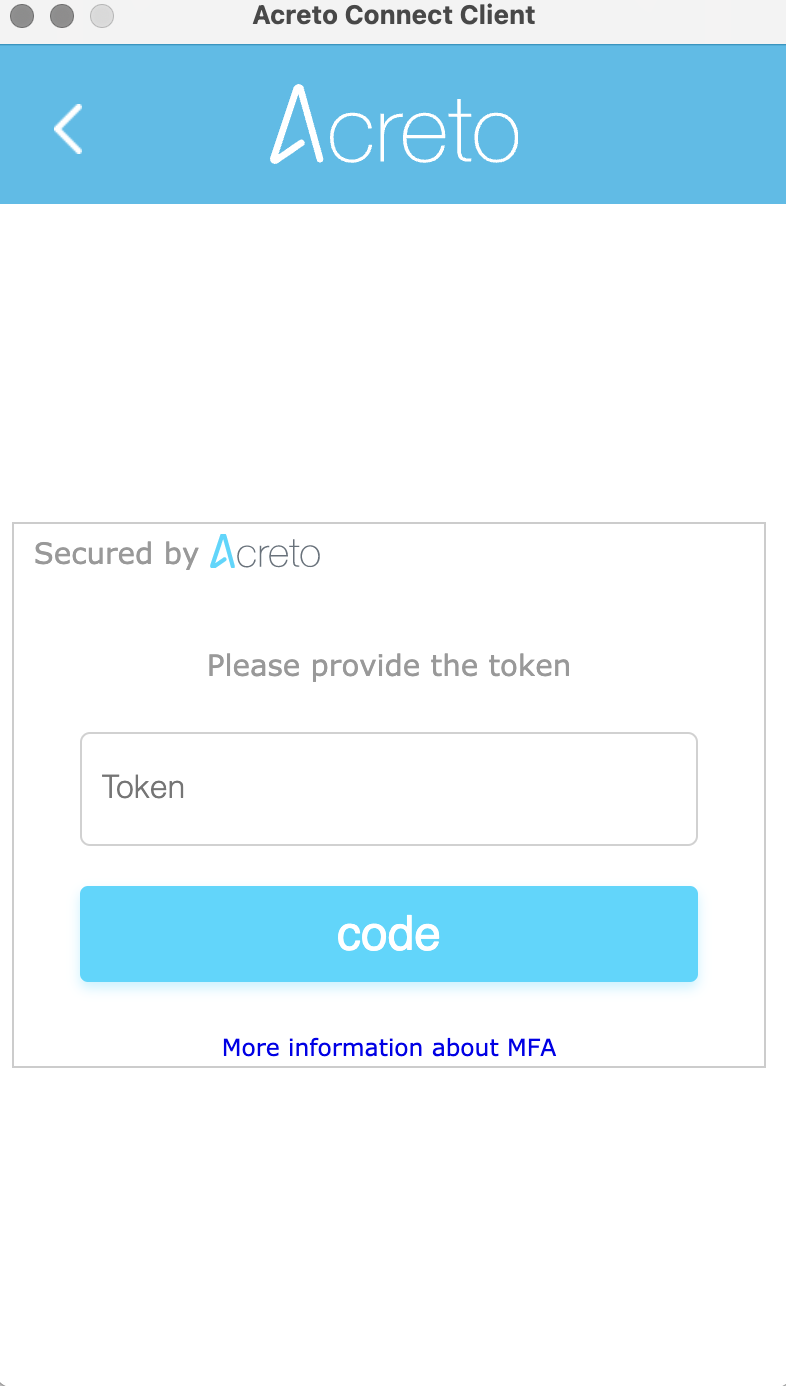
ACC Connection
From now on, periodically (usually once for 24h), Acreto Connect Client will ask you about the second factor.
You must provide the token to keep the connection or establish a new one. Acreto Connect CLient will inform you about the need to authenticate with the proper window.

Summary
In an increasingly interconnected and threat-prone digital landscape, Multi-Factor Authentication has emerged as a “must-have” feature for organizations and individuals. By mitigating password vulnerabilities, enhancing security, complying with regulations, and offering user convenience, MFA significantly strengthens access control and protects against unauthorized access and data breaches. Implementing MFA is a proactive step towards bolstering overall cybersecurity posture and safeguarding sensitive information.
Multifactor Authentication - MFA for Ecosystem
Before You Start
What is Multifactor Authentication and why should you use it?
Two-Factor Authentication (2FA or MFA) - 2FA is an extra layer of security to ensure that people trying to access an online account are who they say they are. First, a user will enter their username and password. Then, instead of immediately gaining access, they must provide another information.
Read more about why you should enable MFA in Acreto Ecosystem in this article.
Prerequisities
To start using MFA, you must own an application that will be your second-factor code generator.
Several popular MFA (Multi-Factor Authentication) applications are available in the market:
- Google Authenticator: Google Authenticator is a free MFA app for Android and iOS devices. It generates time-based one-time passwords (TOTP) to provide an additional layer of security for Google accounts and third-party accounts that support the TOTP protocol.
- Microsoft Authenticator: Microsoft Authenticator is a free MFA app that generates TOTP codes and pushes notifications for Microsoft and third-party accounts supporting the TOTP or OpenID Connect protocols.
- Authy: Authy is a free MFA app that generates TOTP codes, push notifications, and SMS-based codes. It supports various third-party accounts and the Authy OneTouch feature for fast and easy authentication.
- Duo Mobile: Duo Mobile is a free MFA app that generates push notifications, SMS-based and TOTP codes. It supports various third-party accounts and the Duo Push feature for fast and easy authentication.
All mentioned application uses starts supported by Acreto - choose the best tool for you and install it on your device.
How To
Two-Factor Authentication (2FA) and Timeout
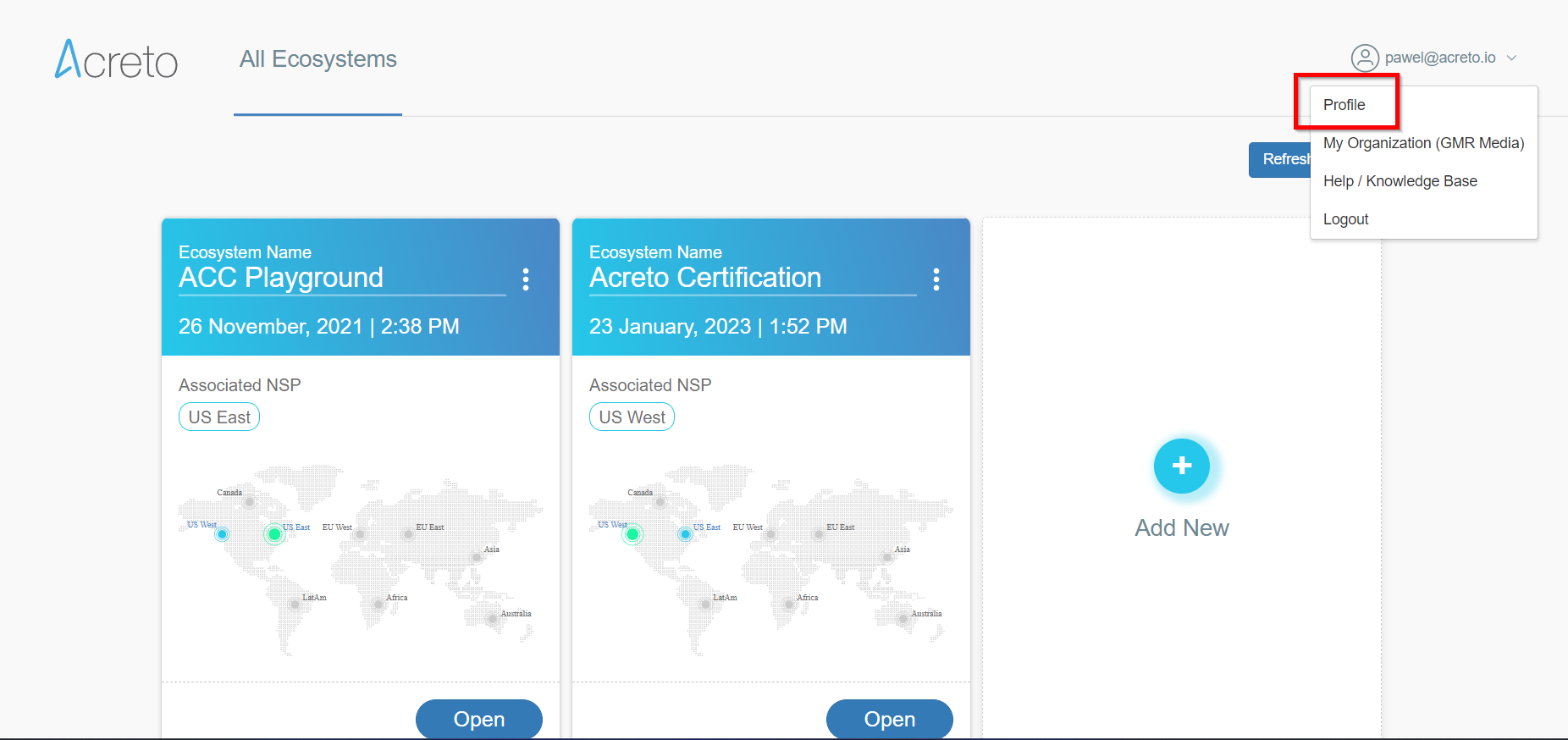
Log in to your Acreto account, and clock on your email address in the top right corner; next, choose the Profile option.

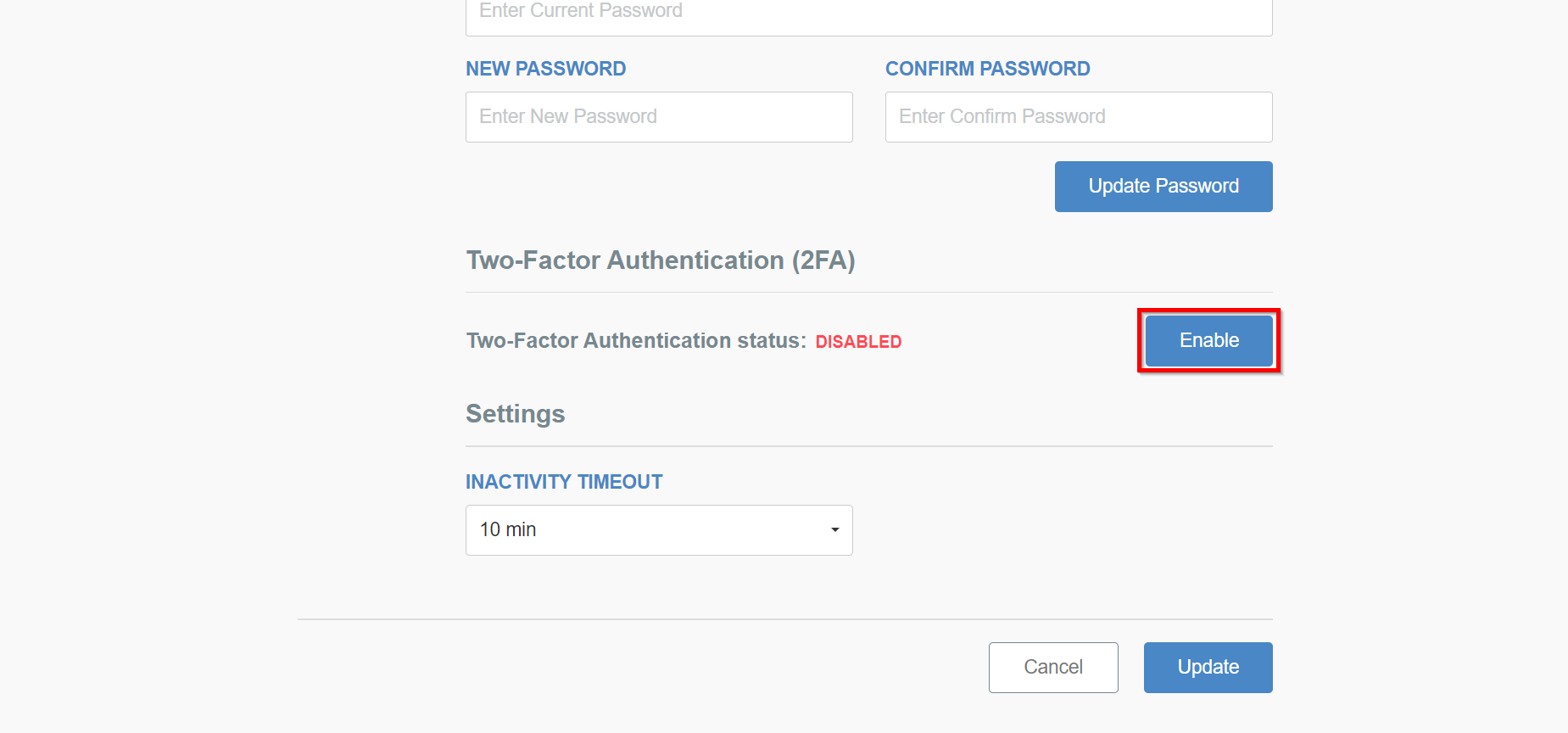
Scroll down to the bottom of the panel, and click the Enable button in Two-Factor Authentication (2FA) to enable this feature.

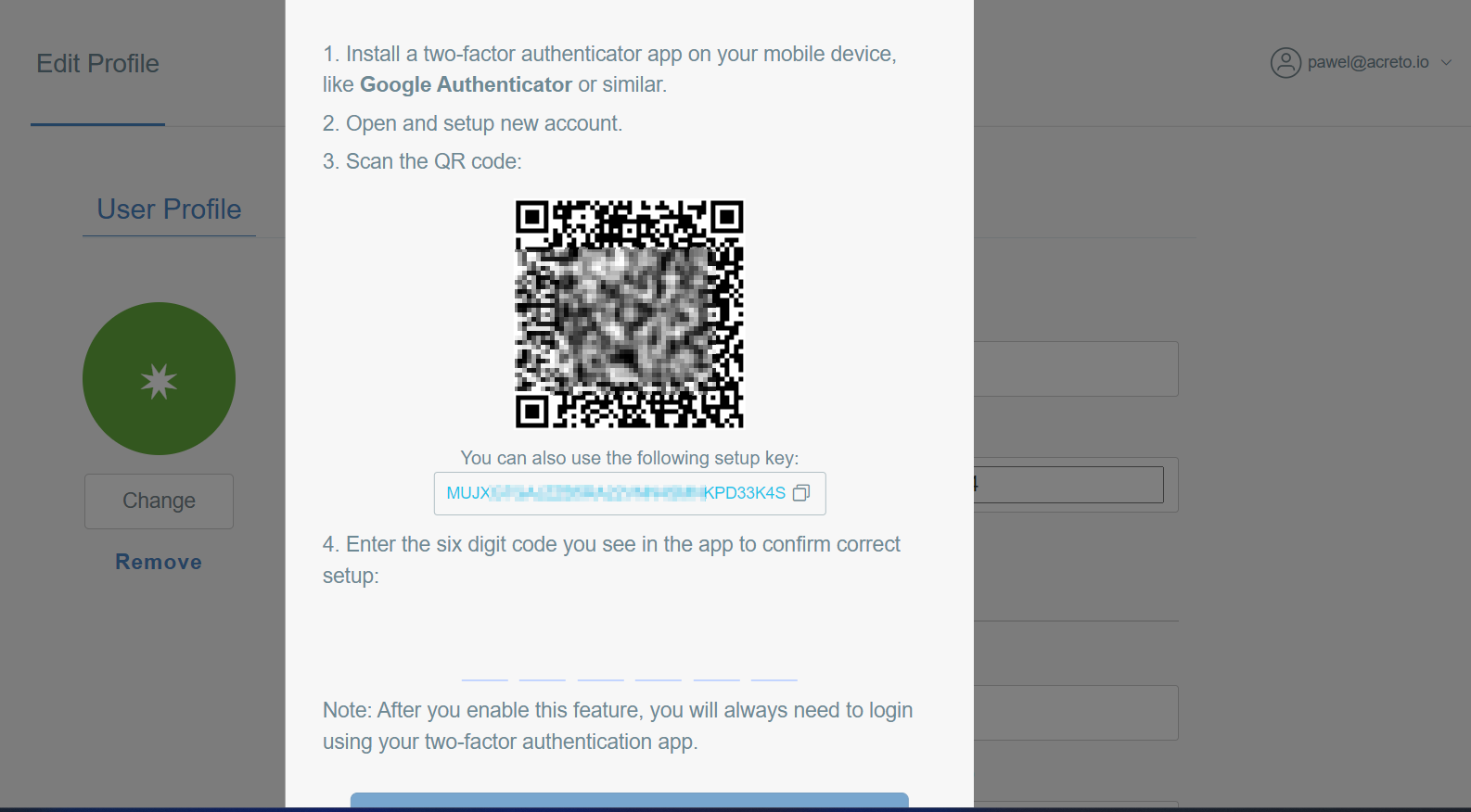
The new window will show a QR code you should scan using Google Authenticator or a similar tool. Scan it, and in step #4 place the first authentication code from this app, to confirm that the setup is correct; click on Enable button.

From now on, every login to Wedge will ask you about the second factor.
On the same panel, you can also define the inactivity timeout when logged out - you can choose between 5min, 10min, and 30min.
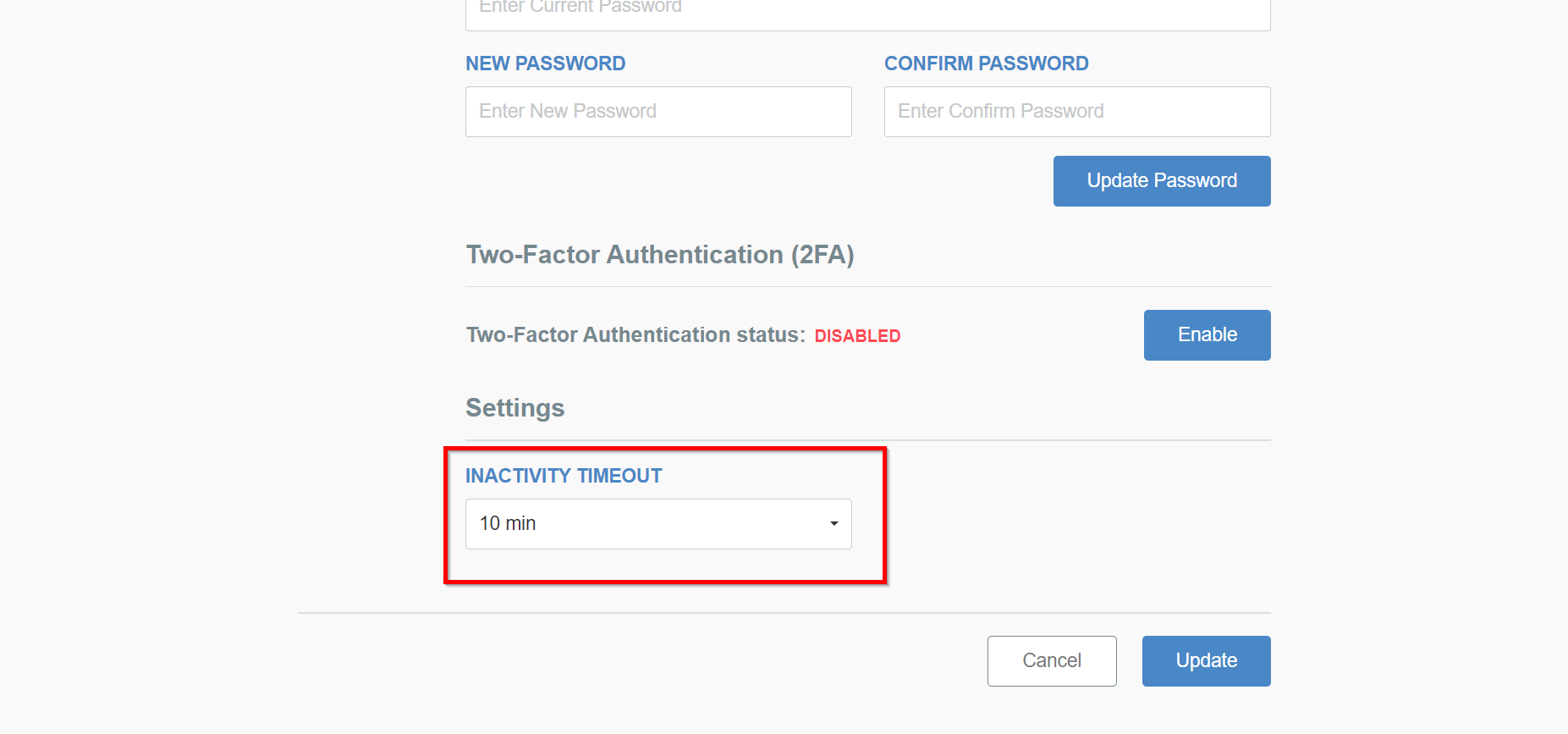

Remember to save the setting using the Update button.
What next?
When MFA for an account is activated on every login to the Ecosystem, you will need to use the second factor to confirm your credentials.
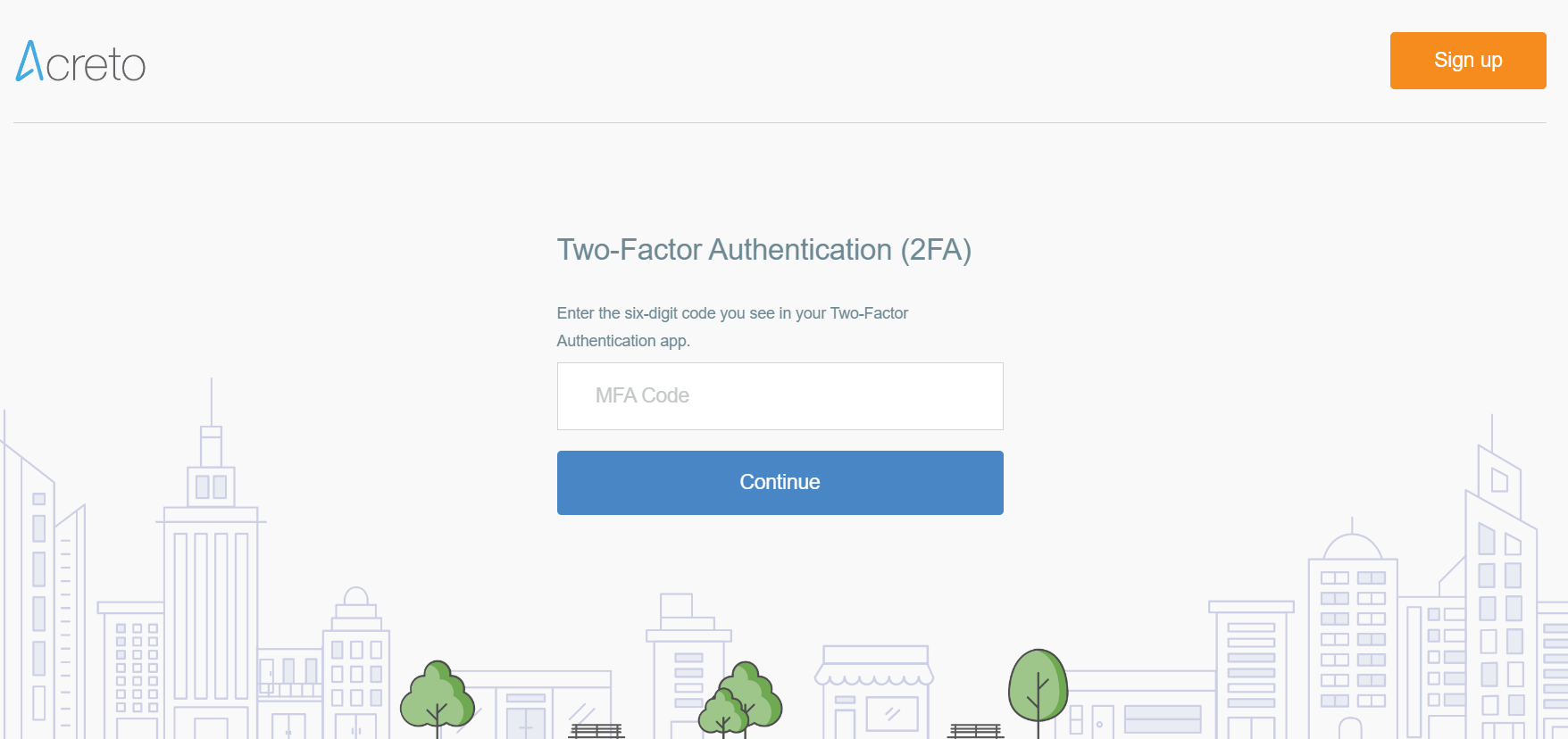

Summary
In an increasingly interconnected and threat-prone digital landscape, Multi-Factor Authentication has emerged as a “must-have” feature for organizations and individuals. By mitigating password vulnerabilities, enhancing security, complying with regulations, and offering user convenience, MFA significantly strengthens access control and protects against unauthorized access and data breaches. Implementing MFA is a proactive step towards bolstering overall cybersecurity posture and safeguarding sensitive information.












